
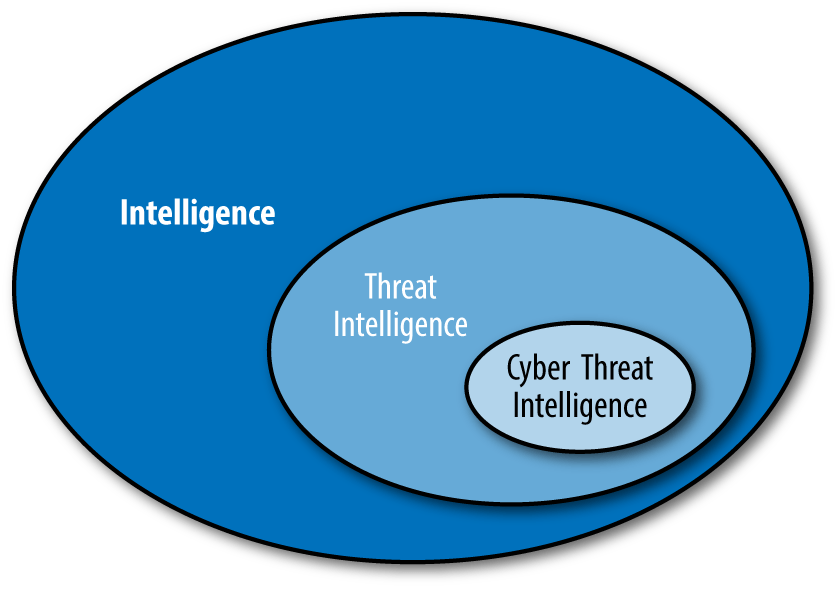
Cyber intelligence is defined as the information that the IT department needs to detect existing and potential threats on its network and to respond effectively to the incident. In today's technology world, the most important issue in the defense against attacks on the internet is cyber intelligence. Cyber Intelligence is critical to organizations in terms of improving and enhancing their capabilities in specific areas, such as threat detection, prioritization, or emergency response.
Cyber intelligence is an important information acquisition activity that is revealed by the threat research and analysis processes of organizations. When it comes to cyber intelligence, organizations focus on the most current threats in their networks and take precautions by detecting the threats that may come with intelligence in advance and provide a great advantage against cyber attacks.
What is Cyber Intelligence?
When we look at the data breaches that have arisen, we see that the measures taken during or after cyber attacks do not always work. Because every day, almost every moment, we are witnessing new threats. For this reason, it is not easy to follow cybercriminals and their techniques that target the critical systems of organizations, and they are processes that require large budgets. At this point, cyber intelligence or cyber threat intelligence plays a very important role against attacks. Cyber intelligence has been one of an organization's most powerful weapons in the fight against cybercriminals.

What is a Cyber Threat?
Cyber Threat is defined as the possibility of attempting unauthorized access to a control system device and/or network using a data communication pathway, or disrupting or disrupting a computer network. Threats to institutions and organizations can come from a multitude of sources, including hostile governments, hacktivist groups, terrorist groups, disgruntled employees, and malicious intruders. You can't describe a war without mentioning the strategy and tactics of the enemies, the weapons they use, the logistics and communication and control systems that provide information about the battlefield. The same is true for cyber threats. The only thing that makes it difficult to understand is that their effects are often less obvious. However, the goals, motivations, and techniques of attacks are often the same.

What Is Cyber Threat Intelligence?
Cyber threat intelligence is to determine the "motivations", "intentions" and "methods" of the attackers as a result of the analysis of identified, collected and enriched data about the threats that may harm the business elements and security of the institutions and organizations at any level.
What is the Purpose of Cyber Threat Intelligence?
The main purpose of cyber threat intelligence is to help institutions and organizations understand the most common and dangerous threat risks from the outside (external). These attacks can be for example 0-day attacks, enhanced persistent threat APT (Advanced Persistent Threat) and exploits. However, the threat threats can also be internal (internal) attacks. Such attacks cause very serious damage to the structure of institutions and organizations. Threat intelligence needs extensive and in-depth data to help organizations protect themselves from such attacks. Until 10 years ago, the IT industry was most afraid of mass attacks; however, although it is now very difficult to detect targeted attacks, they are seen as almost only a "parasite" within the corporate network and it is very difficult to detect. Cybersecurity companies now detect and share IOC (indicator of compromise) data such as malware signatures and IP addresses, md5 hash summaries and URL addresses, botnet command center domain names with the first examples taken from any attack. After the attacks occur for the first time, it is easier to detect the first samples with the necessary software and architecture within the corporate networks after some of the institutions and organizations are damaged.


Cyber Threat is defined as the possibility of attempting unauthorized access to a control system device and/or network using a data communication pathway, or disrupting or disrupting a computer network. Threats to institutions and organizations can come from a multitude of sources, including hostile governments, hacktivist groups, terrorist groups, disgruntled employees, and malicious intruders. You can't describe a war without mentioning the strategy and tactics of the enemies, the weapons they use, the logistics and communication and control systems that provide information about the battlefield. The same is true for cyber threats. The only thing that makes it difficult to understand is that their effects are often less obvious. However, the goals, motivations, and techniques of attacks are often the same.

What Is Cyber Threat Intelligence?
Cyber threat intelligence is to determine the "motivations", "intentions" and "methods" of the attackers as a result of the analysis of identified, collected and enriched data about the threats that may harm the business elements and security of the institutions and organizations at any level.

What is the Purpose of Cyber Threat Intelligence?
The main purpose of cyber threat intelligence is to help institutions and organizations understand the most common and dangerous threat risks from the outside (external). These attacks can be for example 0-day attacks, enhanced persistent threat APT (Advanced Persistent Threat) and exploits. However, the threat threats can also be internal (internal) attacks. Such attacks cause very serious damage to the structure of institutions and organizations. Threat intelligence needs extensive and in-depth data to help organizations protect themselves from such attacks. Until 10 years ago, the IT industry was most afraid of mass attacks; however, although it is now very difficult to detect targeted attacks, they are seen as almost only a "parasite" within the corporate network and it is very difficult to detect. Cybersecurity companies now detect and share IOC (indicator of compromise) data such as malware signatures and IP addresses, md5 hash summaries and URL addresses, botnet command center domain names with the first examples taken from any attack. After the attacks occur for the first time, it is easier to detect the first samples with the necessary software and architecture within the corporate networks after some of the institutions and organizations are damaged.










