

CVE-2024-27280: Buffer Overread Vulnerability In StringIO
We have released the StringIO gem version 3.0.1.1 and 3.0.1.2 that have a security fix for a buffer overread vulnerability.
This vulnerability has been assigned the CVE identifier CVE-2024-27280.
This vulnerability has been assigned the CVE identifier CVE-2024-27280.
Details

An issue was discovered in StringIO 3.0.1, as distributed in Ruby 3.0.x through 3.0.6 and 3.1.x through 3.1.4.
The ungetbyte and ungetc methods on a StringIO can read past the end of a string, and a subsequent call to StringIO.gets may return the memory value.
This vulnerability is not affected StringIO 3.0.3 and later, and Ruby 3.2.x and later.
Recommended Action

We recommend to update the StringIO gem to version 3.0.3 or later. In order to ensure compatibility with bundled version in older Ruby series, you may update as follows instead:
- For Ruby 3.0 users: Update to stringio 3.0.1.1
- For Ruby 3.1 users: Update to stringio 3.0.1.2
Note: that StringIO 3.0.1.2 contains not only the fix for this vulnerability but also a bugfix for [Bug #19389].
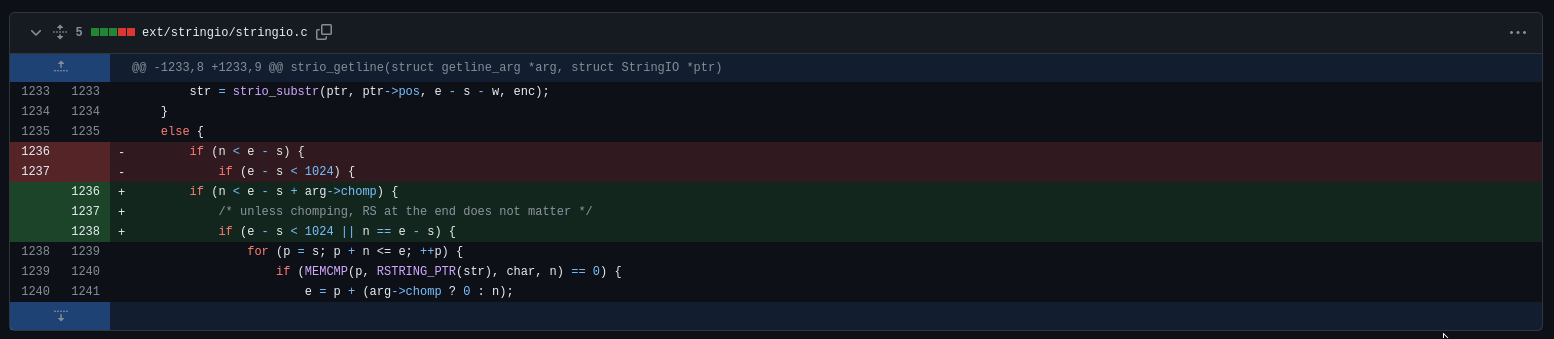
C:
str = strio_substr(ptr, ptr->pos, e - s - w, enc);
}
else {
if (n < e - s) {
if (e - s < 1024) {
if (n < e - s + arg->chomp) {
/* unless chomping, RS at the end does not matter */
if (e - s < 1024 || n == e - s) {
for (p = s; p + n <= e; ++p) {
if (MEMCMP(p, RSTRING_PTR(str), char, n) == 0) {
e = p + (arg->chomp ? 0 : n);
C:
assert_equal("def", stringio.gets("", chomp: true))
assert_string("", Encoding::UTF_8, StringIO.new("\n").gets(chomp: true))
assert_equal("", StringIO.new("ab").gets("ab", chomp: true))
end
def test_gets_chomp_eol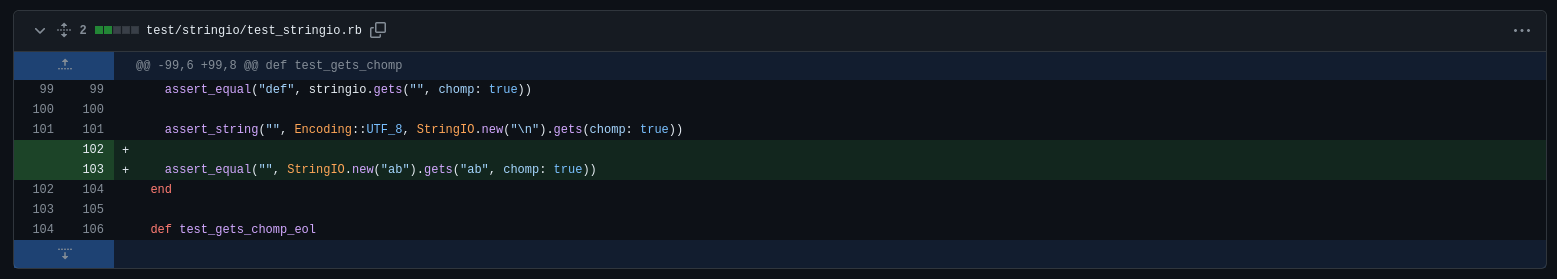
C:
# define RUBY_VERSION_MINOR RUBY_API_VERSION_MINOR
#define RUBY_VERSION_TEENY 4
#define RUBY_RELEASE_DATE RUBY_RELEASE_YEAR_STR"-"RUBY_RELEASE_MONTH_STR"-"RUBY_RELEASE_DAY_STR
#define RUBY_PATCHLEVEL 199
#define RUBY_PATCHLEVEL 200
#define RUBY_RELEASE_YEAR 2023
#define RUBY_RELEASE_MONTH 3
You can use gem update stringio to update it. If you are using bundler, please add gem "stringio", ">= 3.0.1.2" to your Gemfile.
Affected Versions
- Ruby 3.0.6 or lower
- Ruby 3.1.4 or lower
- StringIO gem 3.0.1 or lower
Son düzenleme:






