Hello friends, in this regard, I will try to create a clear perspective in your mind about the concept of the 0day exploit.

As you know, the concept of an exploit refers to the exploitation of a system's vulnerability, and there are various types of exploits. We categorize exploits into three groups: 0day, Remote, and Local.
Remote exploits are exploitations that can be carried out from a distance.
Local exploits are exploits that increase your privileges within the system.
0day exploits, on the other hand, occur when a vulnerability is uploaded to the internet, allowing many attackers to exploit that vulnerability.

We can explain it step by step as follows:
First, a vulnerability is identified in the system or application.
After the vulnerability is identified, an appropriate exploit is developed.
The exploit is then uploaded to the internet, either for a fee or free of charge.
The administrator of the application or system becomes aware of the damage caused by this exploit and proceeds to patch the vulnerability by adding an update package to the system or application. In this way, the exploit becomes ineffective.

As you know, the concept of an exploit refers to the exploitation of a system's vulnerability, and there are various types of exploits. We categorize exploits into three groups: 0day, Remote, and Local.
Remote exploits are exploitations that can be carried out from a distance.
Local exploits are exploits that increase your privileges within the system.
0day exploits, on the other hand, occur when a vulnerability is uploaded to the internet, allowing many attackers to exploit that vulnerability.

We can explain it step by step as follows:
First, a vulnerability is identified in the system or application.
After the vulnerability is identified, an appropriate exploit is developed.
The exploit is then uploaded to the internet, either for a fee or free of charge.
The administrator of the application or system becomes aware of the damage caused by this exploit and proceeds to patch the vulnerability by adding an update package to the system or application. In this way, the exploit becomes ineffective.
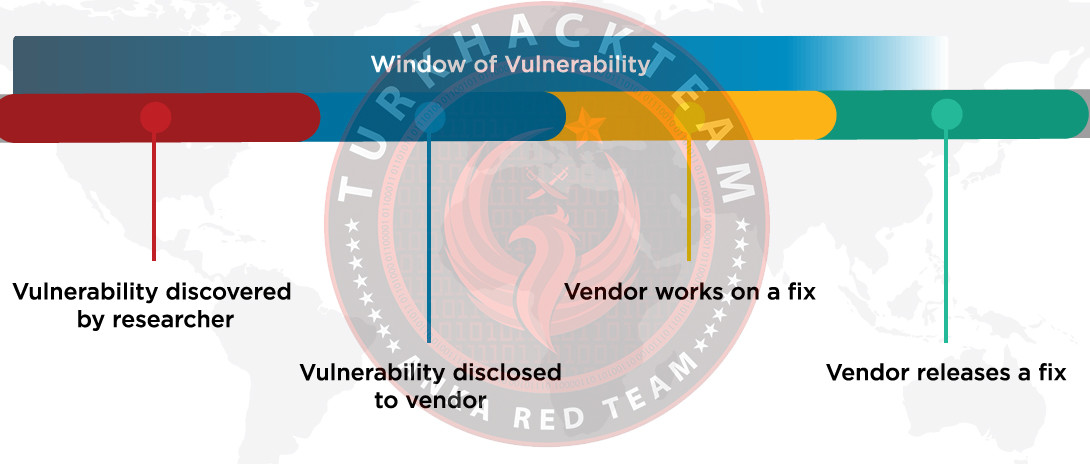

The steps work as described above. When a vulnerability is found, an individual can monetize it depending on its severity and offer it for sale to other hackers. To avoid confusion, it's worth noting that the term "0day" has become synonymous with a popular site where numerous fraudulent activities have occurred. The concept of "0day" should be distinguished from that site.
Exploits that are not put up for sale are commonly shared on shared platforms where people publish their exploits, such as exploit-db and cxsecurity. These vulnerabilities are quickly exploited by many individuals.

The importance of 0day exploits is significant in today's world. For example, in 2017, a content injection exploit was published for WordPress versions 4.7.0 and 4.7.1, revealing a vulnerability that allowed individuals to input content on WordPress websites without admin privileges. The outcome of this example exploit was as follows.
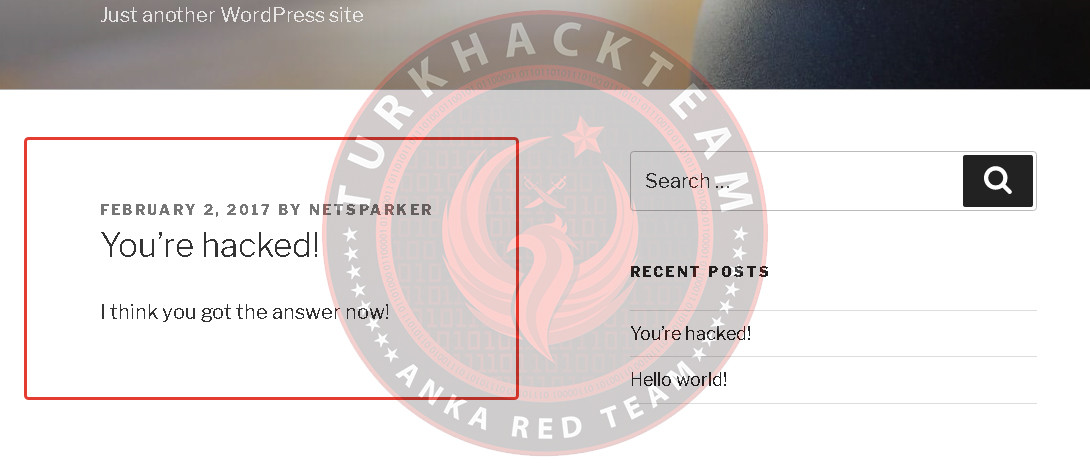

67,000 websites were hacked solely by the person who created the exploit, and the exploit was quickly released, developed by others, and turned into an automated tool. Of course, we had our share of it at the time
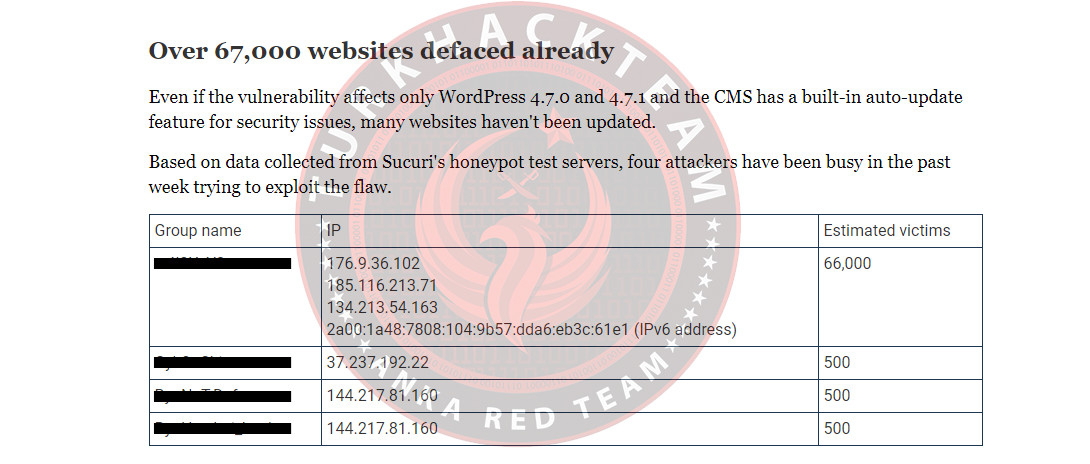

Another reason for the high impact of 0day exploits is that the published exploits are highly adaptable and modifiable because they do not work with complex and dense module structures. In the example given above, the content injection exploit was initially shared just to hack a specific target website. However, hours later, many tools were developed that could perform this task en masse, scanning and exploiting websites on your target list. As a result, the numbers, which initially started at 67,000, grew rapidly to the point where zone-h couldn't even handle the bandwidth due to a heavy influx of notifications, leading to its temporary shutdown.

It is important to keep track of these exploits while they are still up-to-date. An outdated exploit will lose its effectiveness over time. Research has shown that on average, once an exploit becomes 0day, it takes about 28 days for the vulnerability to be patched. Of course, this timeframe can vary depending on how long the person responsible for patching the vulnerability delays the process. However, there is a situation where even when a new patch is released to fix the vulnerability, many users may not have downloaded it. Therefore, even old 0day exploits can still be valuable in today's context.

0day exploit sales take place on the dark web or underground forums. The individuals who upload these exploits are typically either a group that specializes in such sales or individuals looking to sell their own exploits in the environment where these sales occur.
In the first scenario, groups sell these exploits to individuals without providing any trust or security, which can lead to numerous instances of fraud. For example, let's say I have an Instagram password reset exploit, and I release it on my website for people to purchase with cryptocurrency for $10,000. In this case, the buyers have no assurance or guarantee regarding the exploit and payment, which can lead to actual cases of fraud.
In the second sales method, an escrow or intermediary is involved, holding the payment in escrow until the exploit is delivered and verified to work. Once it's confirmed to be functional, the payment is then released to the seller.
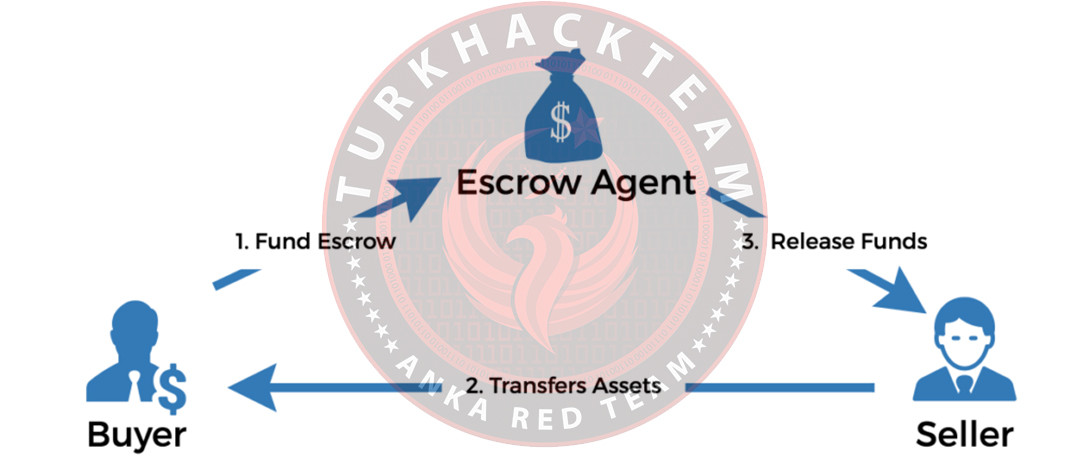

So, is it advisable to buy 0day exploits?
Environments where 0day exploits are bought and sold are not trustworthy. What you should do instead of buying exploits is to discover them. In fact, you can develop and utilize exploits that are already freely available. I've never bought any, and I don't recommend it. I've seen people waste $4,000 on purchases that didn't pan out. Public, meaning freely accessible 0day exploits, will also serve your purpose.

In many public 0day exploits, there isn't a predefined "dork." Do we have to create it ourselves? Having a dork is not a requirement in the concept of exploits. Even an exploit that targets a single system can be published on websites without having a dork.
For instance, let's say we come across an exploit for a common platform like Joomla, but we notice that it doesn't come with a pre-defined dork. In this case, we would derive the dork based on how the exploit exploits the vulnerability.
For example:
"/index.php?option=com_gmapfp&controller=editlieux&tmpl=component&task=edit_upload"
This exploit is a simple HTML upload exploit that works on Joomla's Component GMapFP J3.5/J3.5F versions. Assuming there is no predefined dork, when we analyze the exploit, we notice the "com_gmapfp" content in the URL. This implies that we can exploit this vulnerability on websites that contain this URL. By using "inurl:com_gmapfp," we obtain the dork for our 0day exploit. I can explain it in a simple way like this. Scenarios can vary depending on the exploit.


There's a fact in this field that not every 0day exploit is perfect. Even vulnerabilities like SQL injection or reflected XSS in rarely used scripts can be published on these websites. Vulnerabilities of all sizes and significance are continuously uploaded. You need to find which exploit suits your needs by conducting searches that are relevant to the exploit. As I explained above, you may need to determine the breadth of your target range.

For those who want to follow 0day exploits in more detail and evaluate them, my recommendation is to participate in the training provided by the Cyber Star League project. Our training on this subject will include plenty of examples.
I've tried to share what I know about 0day exploits from a different perspective. Have a great forum, everyone
Source : @GECEGEZEN https://www.turkhackteam.org/konular/0day-exploit-nedir-hackerlarin-gelir-kapisi.1954227/