

CVE-2023-21554: What is MSMQ? (Comprehensive)
On April 12, 2023, Microsoft released a series of new patches for the Windows operating system. One of these patches was intended to fix CVE-2023-21554. This security vulnerability was a remotely exploitable weakness found in the rarely used Windows Message Queuing (MSMQ) service. This vulnerability could potentially result in remote code execution (RCE). Initial analysis came from researchers Wayne Low at Fortinet and Haifei Li at Check Point. These researchers shared some details about the vulnerability and general mitigation information.
Although this service is not enabled by default on Windows servers, Check Point noted that some enterprise applications (such as Microsoft Exchange Server) could start automatically and continue to run in the background. This means that such a service could be running on a system without the administrator being aware of it.
The good news is that there were no known publicly available attacks for this vulnerability. The bad news, however, is that according to the advisory report, no authentication would be required to exploit this service, and it could be triggered with just a single TCP packet (which suggests that exploiting it might be a matter of time and fuzz testing). In other words, there are currently no known public attacks for this vulnerability... YET!
"...an attacker could take control of the process with just a single packet sent to port 1801/tcp." - Check Point If the news, advisory reports, and CVSS score are accurate, especially considering the high-value target that could potentially be exploited with relatively low complexity, it's only a matter of time before we see something. If an exploit emerges, there's no doubt threat actors will race to compromise these devices.
Regardless of whether the service is protected by a firewall or exposed publicly for a legitimate reason, individuals and organizations should check if this service is running on their servers. Administrators should ensure that the latest Microsoft patches have been applied if the service is enabled as intended.
This service listens on TCP port 1801 and uses a proprietary binary communication protocol. Fortunately, Microsoft's documentation includes sample MSMQ connection request and MSMQ connection response. Using this information, an analyst can quickly check if a valid MSMQ service is listening on the remote side using the following command with "netcat":
Kod:
$ echo H4sIAAAAAAACAxM4wM3g4+kfZMPEwPAfCBgYmBguRhSHBkycOtVz+rZngq/UjrF3nnX2sRTsd3GdUDFh3oI/fqfuyQowM4yCEQ4AzGv6OzwCAAA= \
|base64 -d|zcat -|\
netcat $IP_ADDRESS 1801 |\
hexdump -CIf the output looks like the hexadecimal dump below, then it means the server is running MSMQ:
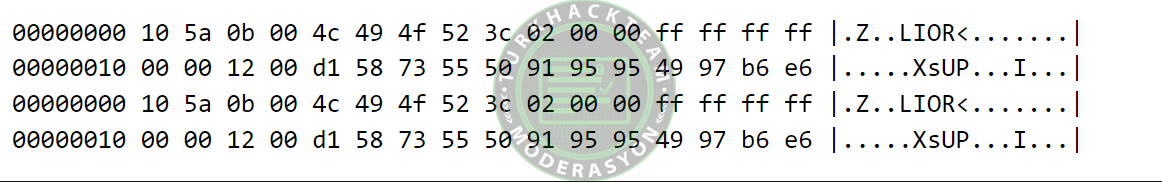
Instead, a user should determine if the service is running by going to the Start Menu, then opening the Control Panel and clicking on the "Programs and Features" section. There should be an option called "Turn Windows features on or off." From this window, we can scroll down to find an entry labeled "Microsoft Message Queue (MSMQ) Server." If these checkboxes are enabled, it means the service is running.
MSMQ Observations


Instead, a user should determine if the service is running by going to the Start Menu, then opening the Control Panel and clicking on the "Programs and Features" section. There should be an option called "Turn Windows features on or off." From this window, we can scroll down to find an entry labeled "Microsoft Message Queue (MSMQ) Server." If these checkboxes are enabled, it means the service is running.
MSMQ Observations

As of April 14, 2023, no exploit has been released for this vulnerability. However, it is important to know what potential issues could arise and to what extent if such an exploit is released in the near future.
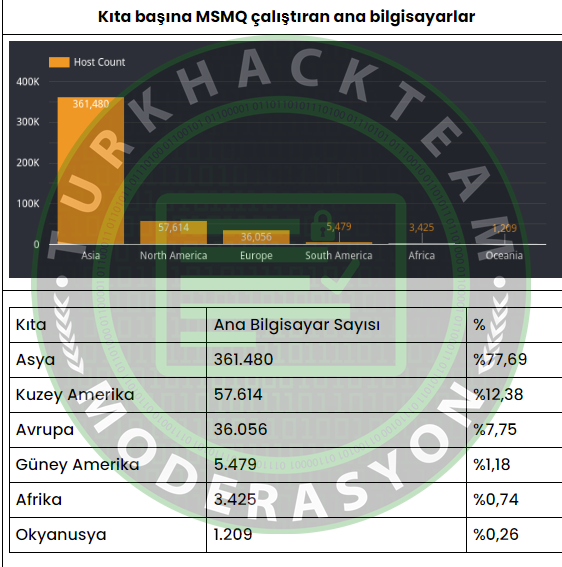
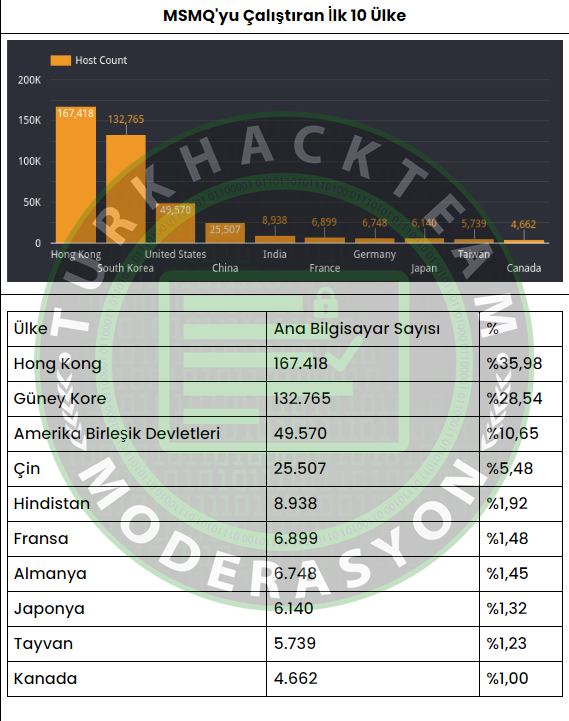
Since Censys distributed the MSMQ scanner on the evening of February 12, it has detected the presence of over 465,000 hosts running the MSMQ service. Below are the continents where this service has been observed, along with the top ten countries. Results are still coming in, but we have observed that Hong Kong is the largest user running this service, with over 35% of the total MSMQ hosts on the internet (167,418 hosts).
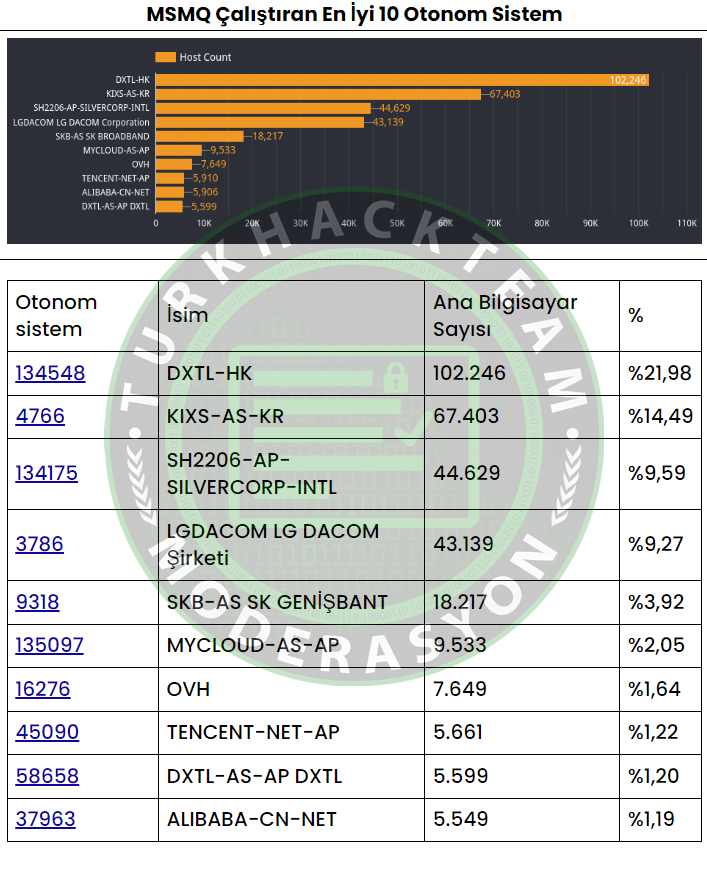
When it comes to the types of networks where this service is running, we observe a mix of businesses, cloud hosting providers, and public broadband internet service providers. Here are the top ten independent systems and networks where MSMQ services are being observed:
(Note: This does not imply that these systems are vulnerable, only that they indicate the presence of the MSMQ service.)
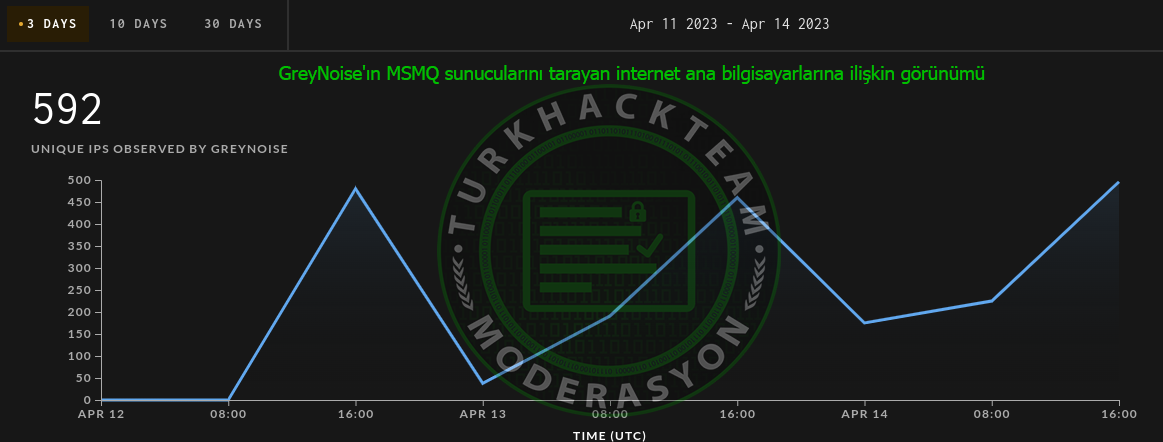
GreyNoise, an organization that collects and analyzes data on hosts attempting to scan or exploit vulnerabilities on the internet, has recently observed an increase in scanning and reconnaissance activities around the MSMQ service. In the last three days, GreyNoise has identified 592 unique IP addresses attempting to find MSMQ services (some of which are probably owned by Censys  ).
).
Solution
If a quick patch cannot be applied to MSMQ on the server or it cannot be disabled, configure a firewall to block untrusted connections to TCP port 1801.
Patch Link: [Security Update Guide - Microsoft Security Response Center]

Source : https://www.turkhackteam.org/konular/cve-2023-21554-msmq-nedir-genis-kapsamli.2046430/
Solution
If a quick patch cannot be applied to MSMQ on the server or it cannot be disabled, configure a firewall to block untrusted connections to TCP port 1801.
Patch Link: [Security Update Guide - Microsoft Security Response Center]

Source : https://www.turkhackteam.org/konular/cve-2023-21554-msmq-nedir-genis-kapsamli.2046430/





