
Greetings TurkHackTeam family in this position I will tell you about the "DOM" structure and what we can do using Dom, if you are ready, I wish you good reading.

- What is DOM? -
Document Object Model (DOM): Also known as the Document Object Model, the browsers we use define each website as a document. All documents contained in these documents are also considered objects. Tools such as text, images, forms used in these sites are included in the object definition. The DOM is used to access objects in the document and change their content, style, structure (IDs, classes, attributes, elements, etc.)
- DOM Structure -
We can consider the DOM structure as follows,
At the very beginning <html> is the label, and below it are other labels written inside. As an example, let's examine the page structure from the point of view of DOM.

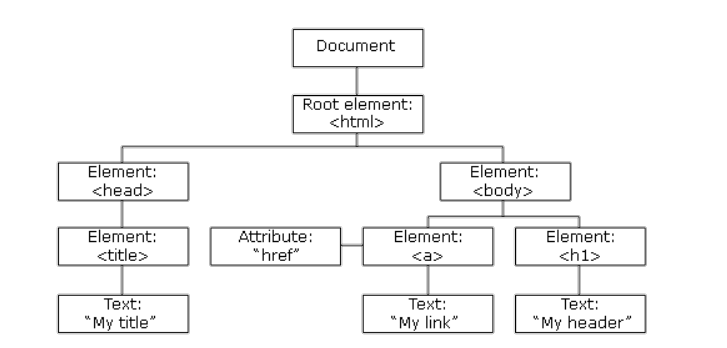
<html> It covers all tags to be written into the html tag. Other tags make no sense without using an html tag.
<head> This tag represents the area where the page is introduced to the browser and search engines (with Meta tags), CSS and Javascript files are included. The page does not cause any change in appearance.
<title> This tag specifies the page name. That is, it covers the name that represents the browser tab.
<body> All the tags that we will write between this tag are reflected on the screen. In general, <body> we work between labels when designing. So the <body> tag is the most important part of an html file.
<a> Used to create link text, links are used to transition to other pages. The most important feature of this tag is the href property. With this feature, the URL of the page we want to link to is indicated.
<h1> It is usually the first title tag that appears at the beginning of the page. The H tags within the page are located at the top of the hierarchy.

Let's contact a programming language as an example;
I'm going to use PHP
, let's create a document called form.html
HTML:
<html>
<head>
<title>PHP & DOM | THT</title>
</head>
<body>
<form method=”POST” action=”post.php”>
<input type="text" name="name">
<input type="text" name="surname">
<input type="submit" value="Gönder">
</form>
</body>
</html>
post.php
<?php
if(isset($_POST))
{
$name = $_POST[‘name’];
$surname = $_POST[‘surname’];
echo “Adınız : ”.$name.“ Soyadınız : ”.$surname;
}In the example above, we assigned some tags to an HTML document. We have two inputs in the form label. We send these inputs to a php file called post.php with the action post.php statement. In the post.php file, we capture the expressions from the inputs with the name property, throw them into the variable and press the screen.

Speaking of what a DOM is, let's give an example of the harm it can create.
- DOM Based XSS -
Its Turkish equivalent is referred to as DOM-based XSS. Unlike HTML code, XSS is a type of vulnerability that occurs on the DOM.
While it is possible to see the results of Stored and Reflected XSS attacks, in Dom-based attacks, the HTML source and the response returned will be the same.
The DOM-based XSS vulnerability is often user-accessible.
And it's a common type of XSS vulnerability today.

Now let's create a sample DOM-based XSS vulnerability,
get a site with the following codes
Kod:
<script>[/SIZE][/COLOR][/I][/B][/CENTER]
[B][I][COLOR=rgb(255, 255, 255)][SIZE=5][CENTER] document.write("<b>Geçerli URL</b> : " + document.baseURI);
</script>
Kod:
http://dom-deneme.com/dom.html#<script>alert(1)</script>When you send an HTTP request, it will be enough for the JavaScript code to work.
Because whatever you type to the Url address with the document.write function reflects it on the screen exactly on the page. When you look at the source of the page, you won't see the <script>alert(1)</script> code.
This is because everything that happens happens in the DOM and is run by JavaScript code.
After the malicious JavaScript code is executed by the page, it is possible to exploit the DOM-based XSS vulnerability in a simple way to steal the user's cookies or change the page behavior as desired.
One of the biggest differences between this vulnerability, Reflected, Stored XSS, which still exists even in popular companies today, is that DOM XSS cannot be prevented in any way on the server side. So why can't it be prevented?
The answer is that nothing written after the "#" character is sent to the server, meaning it does not appear in HTTP traffic.

"The section, also known as hashing, was introduced in the past with the goal of scrolling the HTML page toward a specific element. But in the later periods, in pages where AJAX was used by JavaScript developers, it was mostly used as a hash-bang "#!" to keep page records and things like that."
Therefore, nothing written after "#" is sent to the server. This shows that in DOM XSS attacks, no server-side security method applied in code will work.
I thank you if you have read so far. Hope to see you on the next issues...


Translator: @ByFelez
Subject Author: @Mascar
Subject: https://www.turkhackteam.org/konular/dom-yapisi-ve-hacklenmesi.2016242/







