Welcome back, my tenderfoot hackers!
Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last!

Of course, global financial markets crashed as well, but that's another story.
Although there were many elements that made the hack successful, such as Darlene developing a zero-day exploit (I'll showing you how to do that in a future article) that none of the intrusion detection systems, firewalls, or antivirus softwares detected, Elliot also made certain that the hack could not be traced back to him by using proxies.
Early in the last episode, Lenny, the former boyfriend of Elliot's therapist, Krista, reveals to Krista that he had been hacked by Elliot. He points out that Elliot is nearly untraceable as he uses a proxy from Estonia. In this tutorial, I will show how Elliot bounced his attack off an Estonian (or other) proxy in order to make his hacks untraceable.
How Proxies Work
As you know, whenever you visit (or hack) a website or server over the Internet, your unique Interpret Protocol (IP) address travels with you. It would then be very easy to trace the source of an attack by simply tracing the source IP address.
Hackers, though, often use proxies to hide or obscure their IP address. In this way, they send their traffic to an intermediary proxy, who then sends the traffic on to the destination, replacing the source IP address with its own. In this way, the malicious traffic appears to be coming from the proxy and not the original sender.
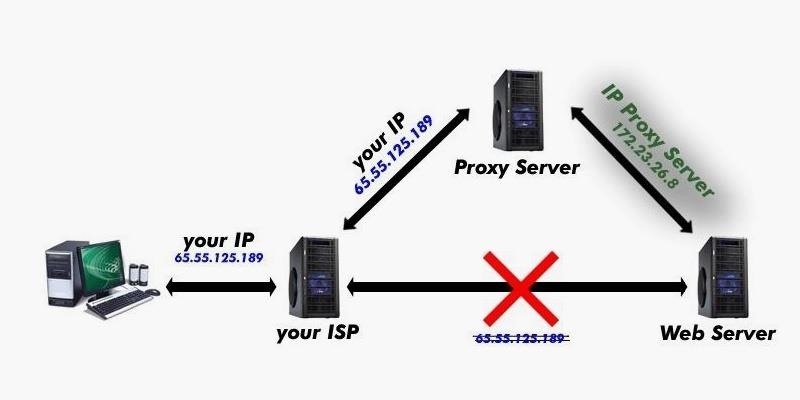
Before I start, I want to point out that there are multiple types of proxies. One of the more popular, anonymous proxies is Tor. Although Tor is effective in anonymizing your traffic from Google and other commercial tracking, it is not effective in anonymizing your traffic from law enforcement, especially the NSA.
As Elliot points out in the pilot episode, when he is explaining to the coffee shop owner who is also a child *****grapher, "Whoever's in control of the exit nodes is also in control of the traffic, which makes me the one in control." He owns the exit node, owns the traffic, and hence, the identity of the users.

Step 1Fire Up Kali
To get started, fire up Kali Linux. If don't already have Kali, you can download it here.
Step 2Go to Proxychains
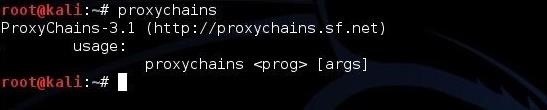
Next, let's go to proxychains. Type:
kali > proxychains
When you do so, it shows you the simple proxychains syntax. Basically, after setting up proxychains, all you need to do is precede the command you want to run with the command "proxychains" and all of your Internet traffic will go through your chosen proxy. As we will see later in this tutorial, if we want to browse the Web with our browser, we can simply start our browser by preceding it with proxychains, such as:
Search for Proxies
In order to set up proxychains to hide our IP address, we will need to select a proxy. There are many sites on the Web with lists of free and paid proxies. Some of these include, but are not limited to:
http://www.hidemyass.com/
http://www.samair.ru/
http://www.hide.me/
Free Proxy Servers - Protect Your Online Privacy with Our Proxy List
Let's try using SamAir Security. When we navigate there, we can see their list of free proxies.
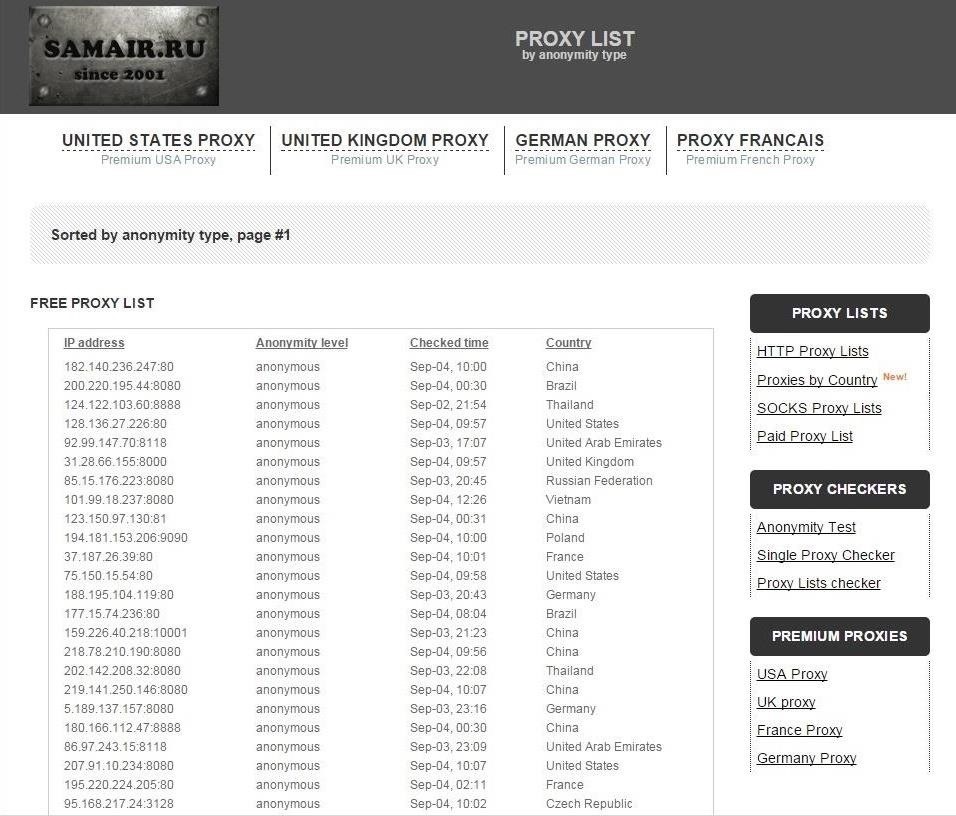
Near the bottom of the page, we can see that they have sorted the proxies by country. Remember, Elliot was using a proxy in Estonia. This list has one proxy listed in Estonia.
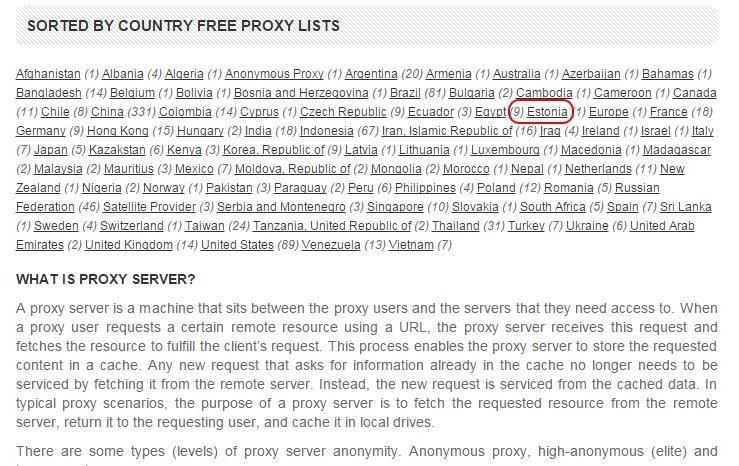
When click on it, we can see that this one proxy in Estonia is a transparent proxy. This means it won't hide our IP. That won't work!
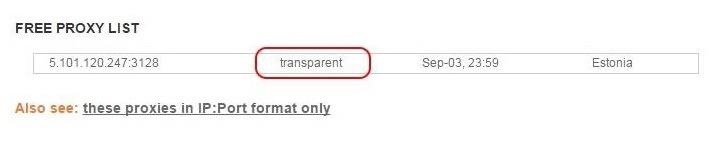
Instead, let's try the list of Russian proxies. Many hackers use Russian proxies as EU and U.S. law enforcement do not have jurisdiction in Russia. This means there is little or no chance of tracing their identity.
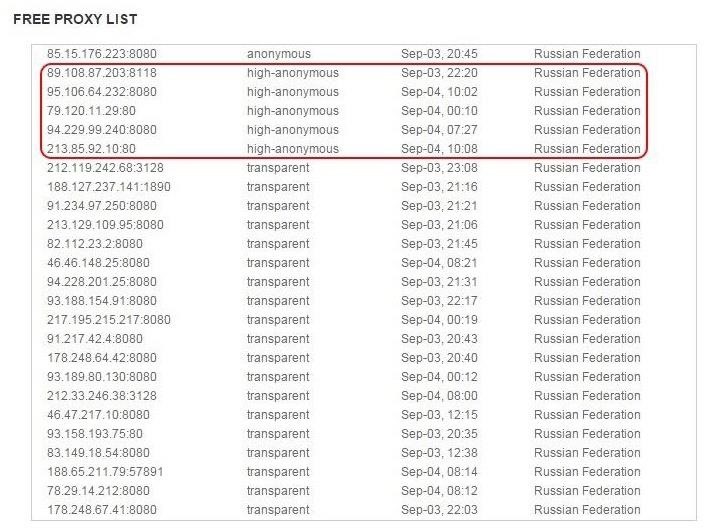
We can see that there are five "high-anonymous" proxies in Russia on this list. Let's us one of those.
Step 4Configure Proxychains
Now that we have a list of potential anonymous proxies, we have to configure proxychains to use it. Like nearly all Linux/Unix applications, configuration is done by a plain text file. These files are generally found in the /etc directory. In this case, the configuration file for proxychains is found at:
We can open it with any text editor, but I will use Leafpad here.
This opens the configuration file for proxychains as seen below. Near the bottom of the file is the critical part. Here is where we tell proxychains which proxy to use.
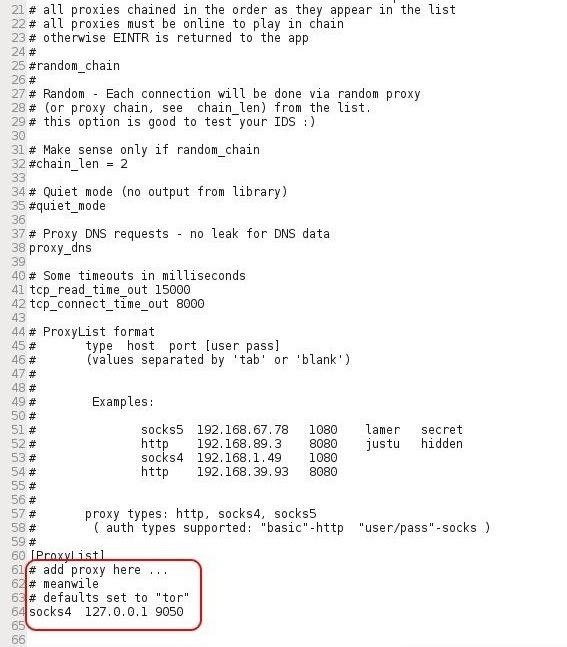
By default, proxychains is setup to use Tor. As Elliot expressed in episode one, he who controls the exit node of Tor controls the traffic. Elliot is certainly aware that the NSA and law enforcement know this as well and would not want to use Tor. To disable Tor, simply put a comment mark (#) before line #64.

Now, to use one of our Russian proxies, we simply need to add the type of proxy (http) and the IP address and port for that proxy as I have done above. Then, save the proxychain.conf file and close it.
Step 5Send Traffic Through Proxy
Lastly, if we want to send our HTTP traffic while browsing the Web through that Russian proxy, we simply open our Iceweasel browser by typing:
Now, all of our traffic will go through the proxy and will appear to be coming from that proxy should anyone inspect the traffic.
Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last!

Of course, global financial markets crashed as well, but that's another story.
Although there were many elements that made the hack successful, such as Darlene developing a zero-day exploit (I'll showing you how to do that in a future article) that none of the intrusion detection systems, firewalls, or antivirus softwares detected, Elliot also made certain that the hack could not be traced back to him by using proxies.
Early in the last episode, Lenny, the former boyfriend of Elliot's therapist, Krista, reveals to Krista that he had been hacked by Elliot. He points out that Elliot is nearly untraceable as he uses a proxy from Estonia. In this tutorial, I will show how Elliot bounced his attack off an Estonian (or other) proxy in order to make his hacks untraceable.
How Proxies Work
As you know, whenever you visit (or hack) a website or server over the Internet, your unique Interpret Protocol (IP) address travels with you. It would then be very easy to trace the source of an attack by simply tracing the source IP address.
Hackers, though, often use proxies to hide or obscure their IP address. In this way, they send their traffic to an intermediary proxy, who then sends the traffic on to the destination, replacing the source IP address with its own. In this way, the malicious traffic appears to be coming from the proxy and not the original sender.

Before I start, I want to point out that there are multiple types of proxies. One of the more popular, anonymous proxies is Tor. Although Tor is effective in anonymizing your traffic from Google and other commercial tracking, it is not effective in anonymizing your traffic from law enforcement, especially the NSA.
As Elliot points out in the pilot episode, when he is explaining to the coffee shop owner who is also a child *****grapher, "Whoever's in control of the exit nodes is also in control of the traffic, which makes me the one in control." He owns the exit node, owns the traffic, and hence, the identity of the users.

Step 1Fire Up Kali
To get started, fire up Kali Linux. If don't already have Kali, you can download it here.
Step 2Go to Proxychains
Next, let's go to proxychains. Type:
kali > proxychains
When you do so, it shows you the simple proxychains syntax. Basically, after setting up proxychains, all you need to do is precede the command you want to run with the command "proxychains" and all of your Internet traffic will go through your chosen proxy. As we will see later in this tutorial, if we want to browse the Web with our browser, we can simply start our browser by preceding it with proxychains, such as:
Kod:
kali > proxychains iceweasel
Search for Proxies
In order to set up proxychains to hide our IP address, we will need to select a proxy. There are many sites on the Web with lists of free and paid proxies. Some of these include, but are not limited to:
http://www.hidemyass.com/
http://www.samair.ru/
http://www.hide.me/
Free Proxy Servers - Protect Your Online Privacy with Our Proxy List
Let's try using SamAir Security. When we navigate there, we can see their list of free proxies.

Near the bottom of the page, we can see that they have sorted the proxies by country. Remember, Elliot was using a proxy in Estonia. This list has one proxy listed in Estonia.

When click on it, we can see that this one proxy in Estonia is a transparent proxy. This means it won't hide our IP. That won't work!

Instead, let's try the list of Russian proxies. Many hackers use Russian proxies as EU and U.S. law enforcement do not have jurisdiction in Russia. This means there is little or no chance of tracing their identity.

We can see that there are five "high-anonymous" proxies in Russia on this list. Let's us one of those.
Step 4Configure Proxychains
Now that we have a list of potential anonymous proxies, we have to configure proxychains to use it. Like nearly all Linux/Unix applications, configuration is done by a plain text file. These files are generally found in the /etc directory. In this case, the configuration file for proxychains is found at:
Kod:
/etc/proxychains.confWe can open it with any text editor, but I will use Leafpad here.
Kod:
kali > leafpad /etc/proxychains.conf
This opens the configuration file for proxychains as seen below. Near the bottom of the file is the critical part. Here is where we tell proxychains which proxy to use.

By default, proxychains is setup to use Tor. As Elliot expressed in episode one, he who controls the exit node of Tor controls the traffic. Elliot is certainly aware that the NSA and law enforcement know this as well and would not want to use Tor. To disable Tor, simply put a comment mark (#) before line #64.

Now, to use one of our Russian proxies, we simply need to add the type of proxy (http) and the IP address and port for that proxy as I have done above. Then, save the proxychain.conf file and close it.
Step 5Send Traffic Through Proxy
Lastly, if we want to send our HTTP traffic while browsing the Web through that Russian proxy, we simply open our Iceweasel browser by typing:
Kod:
kali > proxychains iceweaselNow, all of our traffic will go through the proxy and will appear to be coming from that proxy should anyone inspect the traffic.





