Kullanıcı1233
Kıdemli Üye
- 19 Tem 2011
- 4,371
- 12
What is Cewl?
Word list files may be needed when you are performing a password attack in penetration tests. It aims to increase the relevance of the words by examining the given web page. Cewl examines the site and creates words.
Let's create a word list.
1) Type "cewl" in terminal.
We can get to the help menu by typing "cewl -h"
3-)cewl -d 2 -m 8 https://hacklang.org/ -w /root/desktop/Wordlist_Hacklang
4-)You can see "Wordlist_Hacklang.txt" file in Desktop.
Note:
-d 2 ; depth of revieweing the web page.
-m 8; means at least 8 characters.
-w; creates the word list file
What is Crunch?
You can create a word list with Crunch
Let's create a word list
1) Type "crunch" on the terminal.
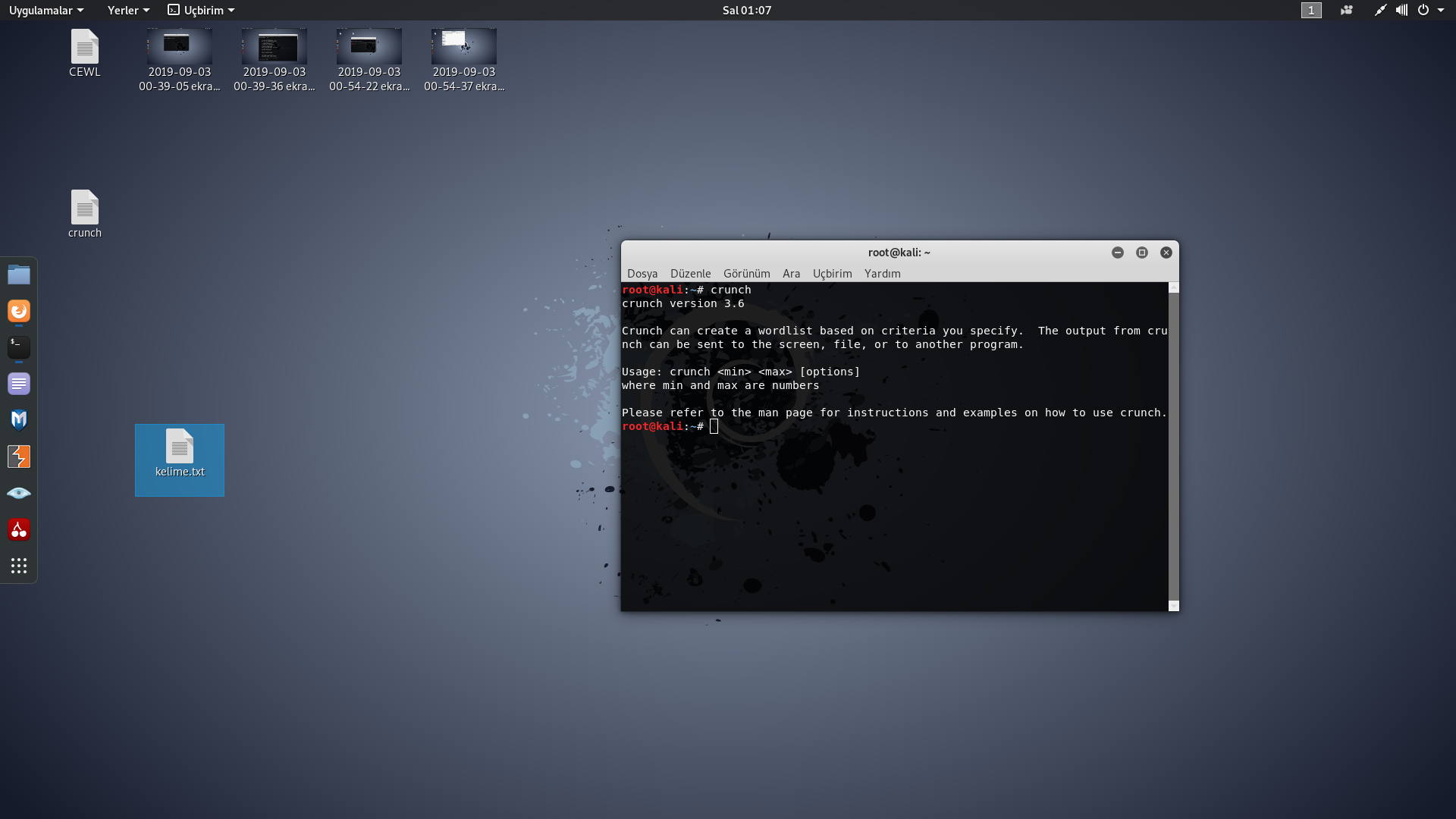
2) Crunch 2 5 er123 -o /root/desktop/wordlist.txt
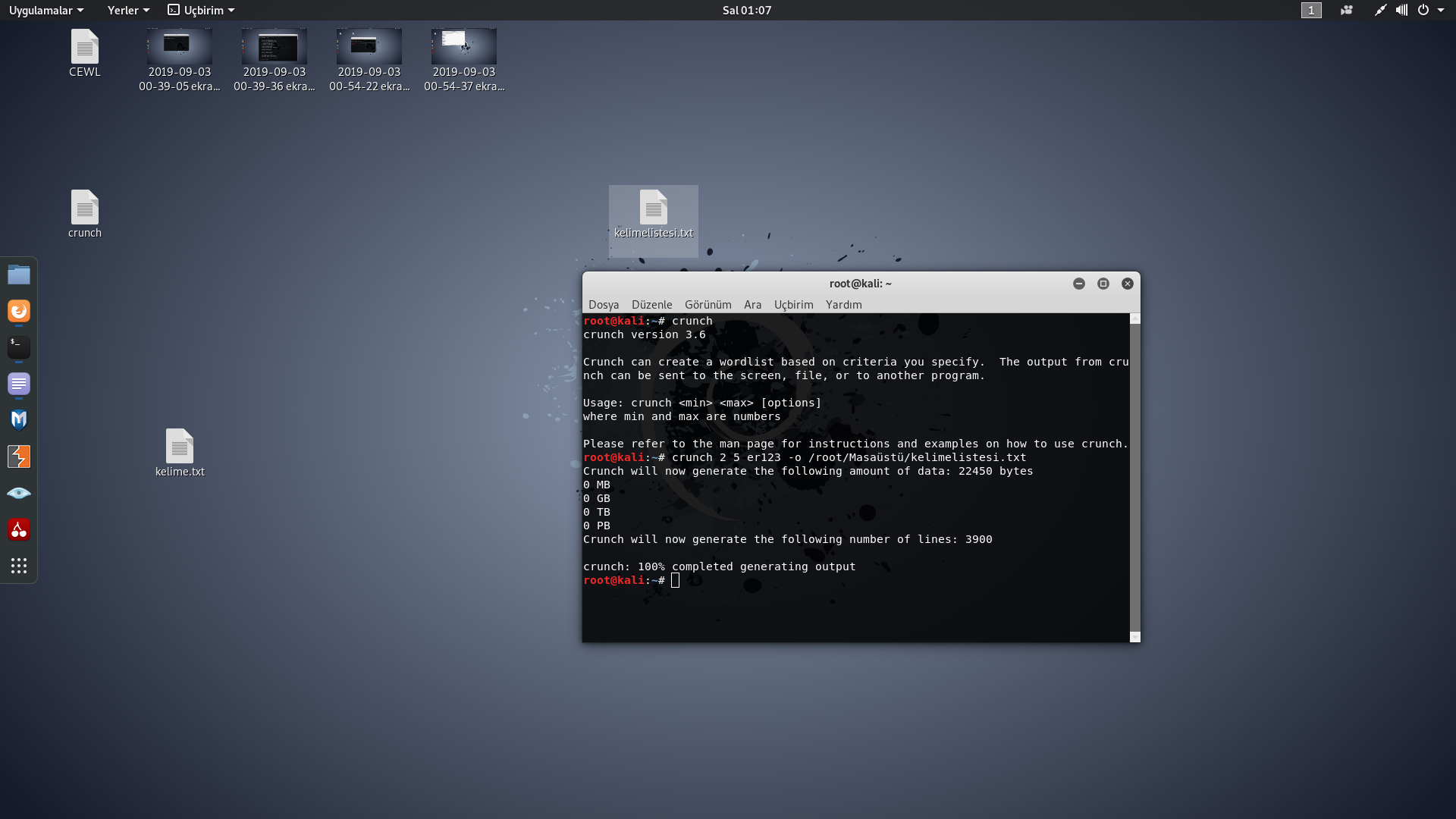
Note: we determined how many characters it should be by typing 2 5, It doesn't write anything after 5 characters, it writes all combinations from a to z.
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
+What is Medusa?
- Medusa is based on Brute Force. implements brute force attempts on the target address, target host or server. Medusa is used a lot because it is simple to use. The fact that the medusa supports a lot of modules and protocols allows us to easily to perform brute force attacks to many servers and hosts. Let's get start:
How to Install Medusa
2) Type "medusa" on terminal.
Now, let's learn how to use these parameters. First, the basic parameters you need to know are 5 as -h / -H, -u / -U, -p / -P, -M and -f / -F. Without these paramteres the medusa tool won't work.
Let's start learning the parameters from the -h and -H parameters. -h parameter allows us to perform brute force only through the IP address of a server or host, -H parameter allows us to perform brute force experiments over the IP address of more than one host or server. For example, If you are going to use -H parameter, after saving all the IP addresses in a text file on the Desktop; you should add as ""-H /root/Desktop/host.txt". You can examine the commands that I wrote below for both parameters. If you run the codes that I wrote below, Medusa will give you an error.
Our next parameter, -u and -U parameters; used to specify the user name that you want to try during brute force. Of course, there is a small difference between -u and -U parameters. During the brute force, we must add the -u parameter if we want the try a single username, or the -U parameter if we want to try more than one. If we will use the -U parameter, you need to create a text file on the Desktop, write and save the usernames that we want to try. The examples that below will help you to understand better.
Now the -p and -P parameters that we will examine, work with the same logic as the -u and -U parameters. The only difference in this parameter is that we only specify the passwords. I hope you understand that the 2 parameters I have already explained and this parameter works with the same logic. If you want to try a single password during brute force -which won't be healthy- you need to use the -p parameter, and If you want to try more than one password you must use the -P parameter.
7) We learned 3 parameters and now we need to use the -M parameter to determine which protocol will work with these parameters. Generally, ftp and ssh protocols are used mostly in -M parameter. But, it is also possible to use it with protocols such as snm, smtp. You can use this parameter as in the example below.
8) When using the Medusa, the -f parameter -which is the last of the basic 5 parameters- is a very important parameter that prevents loss of time but I think its very underrated. For example, we attack the xxx.xx.xx.xxxx ip and there are 3 usernames and 3 passwords as admin, user, root. When we attack with Medusa, no problem If it found the user and password on the first try and we don't forget the -F parameter, there is no problem. If you don't use it, medusa will keep trying all usernames and passwords after finding it.
We just learned the 5 basic parameters when using the Medusa tool. But If you want to specify a port in addition, the -n parameter will help you. If you don't use the -n parameter normally, the default tcp port will be activated. Generally, the -n parameter is used in line with the analysis and acquired information on a single target. So If you will use the -n parameter then I recommend you to use -h parameter. But of course this is your choice.
9) If you want to view the available modules in the Medusa, you can use the -d parameter. As you can see in the image below, you will see the list when we enter the command "medusa -d"
10) We learned how to display the information line about the Medusa version with the -b parameter when using the command. If you want to learn Medusa's version, you can use "medusa -V" command.
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
What is Hydra?
We can attack mails with the wordlist that we have created with Hydra.
1) Type "hydra" on the terminal. (You can use the other options above)
2) Let's create wordlist.txt on the desktop
Note :
gmail port: 465
hotmail port :587
yahoo port : 587
4-) If it matches, we will see the results.
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
+What is John the Ripper?
You can crack passwords when you are offline. For example you can decrypt md5 files with john the ripper.
How to Use John the Ripper:
1-)Open the Terminal
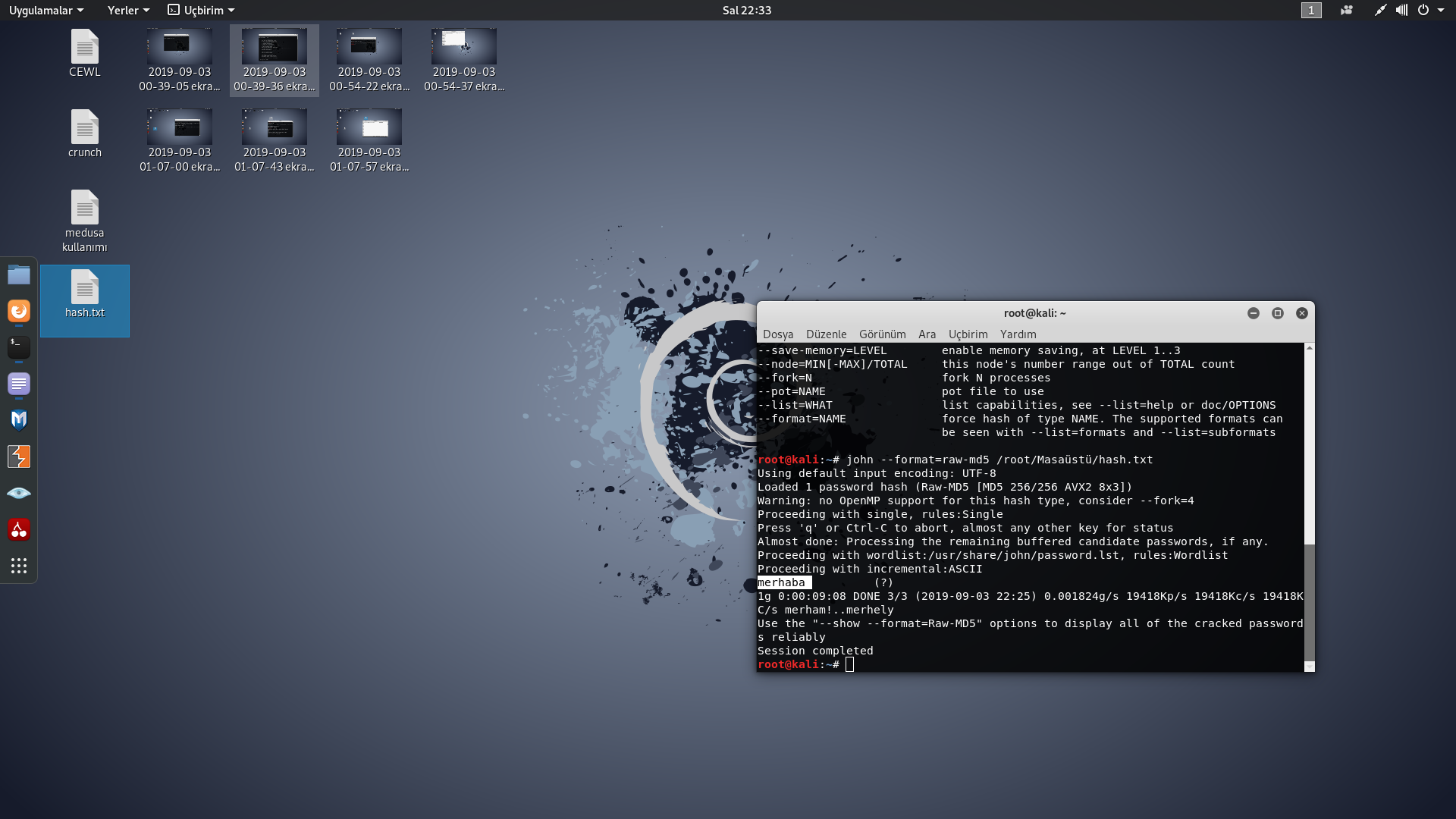
2-)We can see the instructions with this command: "john"
Note: You can add multiple hashes to "root/Desktop/password.txt" I created a md5, write "hello" and tried it.
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
1.What is Hashcat?
Hashcat is a password recovery tool. It had a proprietary code base until 2015, but is now released as open source software. Hashcat is already comes installed on Kali Linux. If you have a solid wordlist it will easily break the hash.
How to Use Hashcat?
We need a list of passwords and the hash that we will crack.
1.1 we create a new file and put it in the hash that we will crack.
2.1 let's create our password list, open a file and write the words. For example brute.txt
3.1 and type the following command to the terminal
4) Well, scanning completed. Let's see the results
The tasks of our parameters are -m 0 parameter can be used to select our hash type.
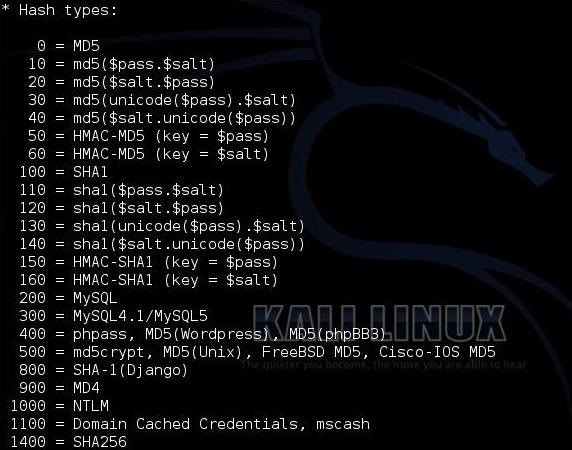
parameter -a 0 determines our attack type, If you want to see the attack types just type "help"
source: https://www.turkhackteam.org/kripto...1-parola-kirma-saldirilari-linux-aquiell.html
Translator: dRose98
Word list files may be needed when you are performing a password attack in penetration tests. It aims to increase the relevance of the words by examining the given web page. Cewl examines the site and creates words.
Let's create a word list.
1) Type "cewl" in terminal.

We can get to the help menu by typing "cewl -h"

3-)cewl -d 2 -m 8 https://hacklang.org/ -w /root/desktop/Wordlist_Hacklang

4-)You can see "Wordlist_Hacklang.txt" file in Desktop.

Note:
-d 2 ; depth of revieweing the web page.
-m 8; means at least 8 characters.
-w; creates the word list file
What is Crunch?
You can create a word list with Crunch
Let's create a word list
1) Type "crunch" on the terminal.

2) Crunch 2 5 er123 -o /root/desktop/wordlist.txt

Note: we determined how many characters it should be by typing 2 5, It doesn't write anything after 5 characters, it writes all combinations from a to z.

++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
+What is Medusa?
- Medusa is based on Brute Force. implements brute force attempts on the target address, target host or server. Medusa is used a lot because it is simple to use. The fact that the medusa supports a lot of modules and protocols allows us to easily to perform brute force attacks to many servers and hosts. Let's get start:
How to Install Medusa
Kod:
apt-get install medusa2) Type "medusa" on terminal.
Now, let's learn how to use these parameters. First, the basic parameters you need to know are 5 as -h / -H, -u / -U, -p / -P, -M and -f / -F. Without these paramteres the medusa tool won't work.
Let's start learning the parameters from the -h and -H parameters. -h parameter allows us to perform brute force only through the IP address of a server or host, -H parameter allows us to perform brute force experiments over the IP address of more than one host or server. For example, If you are going to use -H parameter, after saving all the IP addresses in a text file on the Desktop; you should add as ""-H /root/Desktop/host.txt". You can examine the commands that I wrote below for both parameters. If you run the codes that I wrote below, Medusa will give you an error.
Kod:
medusa -h 70.32.68.120
medusa -H /root/Desktop/host_ip.txtOur next parameter, -u and -U parameters; used to specify the user name that you want to try during brute force. Of course, there is a small difference between -u and -U parameters. During the brute force, we must add the -u parameter if we want the try a single username, or the -U parameter if we want to try more than one. If we will use the -U parameter, you need to create a text file on the Desktop, write and save the usernames that we want to try. The examples that below will help you to understand better.
Kod:
medusa -u admin
medusa -U /root/Desktop/user.txtNow the -p and -P parameters that we will examine, work with the same logic as the -u and -U parameters. The only difference in this parameter is that we only specify the passwords. I hope you understand that the 2 parameters I have already explained and this parameter works with the same logic. If you want to try a single password during brute force -which won't be healthy- you need to use the -p parameter, and If you want to try more than one password you must use the -P parameter.
Kod:
medusa -p password
medusa -P /root/Desktop/password.txt7) We learned 3 parameters and now we need to use the -M parameter to determine which protocol will work with these parameters. Generally, ftp and ssh protocols are used mostly in -M parameter. But, it is also possible to use it with protocols such as snm, smtp. You can use this parameter as in the example below.
Kod:
medusa -M FTP
medusa -M SSH8) When using the Medusa, the -f parameter -which is the last of the basic 5 parameters- is a very important parameter that prevents loss of time but I think its very underrated. For example, we attack the xxx.xx.xx.xxxx ip and there are 3 usernames and 3 passwords as admin, user, root. When we attack with Medusa, no problem If it found the user and password on the first try and we don't forget the -F parameter, there is no problem. If you don't use it, medusa will keep trying all usernames and passwords after finding it.
We just learned the 5 basic parameters when using the Medusa tool. But If you want to specify a port in addition, the -n parameter will help you. If you don't use the -n parameter normally, the default tcp port will be activated. Generally, the -n parameter is used in line with the analysis and acquired information on a single target. So If you will use the -n parameter then I recommend you to use -h parameter. But of course this is your choice.
Kod:
medusa -h 75.213.56.281 -U /root/Desktop/user.txt -P /root/Desktop/password.txt -n 443 -M ftp -F9) If you want to view the available modules in the Medusa, you can use the -d parameter. As you can see in the image below, you will see the list when we enter the command "medusa -d"
10) We learned how to display the information line about the Medusa version with the -b parameter when using the command. If you want to learn Medusa's version, you can use "medusa -V" command.
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
What is Hydra?
We can attack mails with the wordlist that we have created with Hydra.
1) Type "hydra" on the terminal. (You can use the other options above)
2) Let's create wordlist.txt on the desktop
Kod:
"hydra -S ı [email protected] P wordlist.txt v V e ns s 465"Note :
gmail port: 465
hotmail port :587
yahoo port : 587
4-) If it matches, we will see the results.
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
+What is John the Ripper?
You can crack passwords when you are offline. For example you can decrypt md5 files with john the ripper.
How to Use John the Ripper:
1-)Open the Terminal
2-)We can see the instructions with this command: "john"
Note: You can add multiple hashes to "root/Desktop/password.txt" I created a md5, write "hello" and tried it.
Kod:
john --format=raw-md5 /root/Masaüstü/sıfre.txt
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++
1.What is Hashcat?
Hashcat is a password recovery tool. It had a proprietary code base until 2015, but is now released as open source software. Hashcat is already comes installed on Kali Linux. If you have a solid wordlist it will easily break the hash.
How to Use Hashcat?
We need a list of passwords and the hash that we will crack.
1.1 we create a new file and put it in the hash that we will crack.
2.1 let's create our password list, open a file and write the words. For example brute.txt
3.1 and type the following command to the terminal
Kod:
hashcat -m 0 -a 0 thedirectory/thedirectory/thedirectory/thedirectory/hash.txt thedirectory/thedirectory/thedirectory/brute.txt4) Well, scanning completed. Let's see the results
The tasks of our parameters are -m 0 parameter can be used to select our hash type.

parameter -a 0 determines our attack type, If you want to see the attack types just type "help"
Kod:
hashcat --helpsource: https://www.turkhackteam.org/kripto...1-parola-kirma-saldirilari-linux-aquiell.html
Translator: dRose98




