What Is Cyber Intelligence?
Collecting information from electronic media
Gathering information from OsInt engines/tools
Analyzing/using the information collected
Monitoring and analyzing digital security threats
and the initiation of the resistance process with the information obtained after this analysis process.
Importance Of Cyber Intelligence
States' Fear of Cyber Terrorism
Deciphering Commercial Company Information (Financial information, competitor, etc.)
Personal Information
Hackers
Privacy
Today, as a result of the state of technology, great importance is attached to cyber intelligence. Countries and institutions are attacking the information systems of competitors in order to gain superiority to each other, and aim to harm economically by disabling their cyber systems. Besides, the data stored in cyberspace was captured and thus future plans, technologies used and some other confidential information could be obtained.
As a result of a cyber attack, it is possible to interrupt all electricity services of a country at once. With attacks on SCADA systems, not only economic but also physical attacks can be carried out to the target country. As a result of an attack that can last for days, the systems of all banks and financial institutions of the country can be collapsed and rendered inoperable. It is now stated by various experts that the era of fighting with tanks and rifles is over and that wars will take place in cyberspace. The US officials stated in a statement that any cyber attack against them would be a reason for conventional warfare.
This official statement made by the USA emphasizes the importance of cyber security and cyber intelligence elements. Cyber intelligence can be on hacking, which is also defined as HACKINT, or can be obtained by using social media and various internet broadcasts, as we have stated before. In addition, cyber throttle operations, which are frequently used in Middle Eastern countries such as Syria and Iran, can also cause material and moral damage.
Determining The Target
Government agency
Staff at the establishment(Social Engineering)
Software/Product (Software theft)
Data (data theft)
Prestige (Intelligence organizations)
Banks/E-Business Systems
Personal Data (Picture, Video, privacy, blackmail)
Social Media Accounts (Curiosity, ambition etc.)
Mail (Getting information, curiosity, etc.)
OsInt
Open Source Intelligence
Public Data
OsInt, First defined by the US Department of Defense in 2005
Information Gathering Techniques & Tools
Privacy
Bitcoin * Fake Name Generator
Tor Browser Bundle * Ghostery
Cryptocat * HTTPS Everywhere
DoNotTrackMe * Hushmail alternative
Enigmail * Burn Note
Search Engines
Google Dorks * Duck Duck Go
Baidu * PunkSpider
binsearch.info * Google
Bing * Shodan
Searchenginecolossus
Google Hacking
Technique primarily used by hacker groups
Fast and multiple results
Specific results with advanced operators
Passwords user IDs, pdfs important files Dropbox sensitive datas, ip ranges
important db dumping with single dork, excel, pdf, xls scans for target.
<Dork sharing is forbidden on forum.> =)
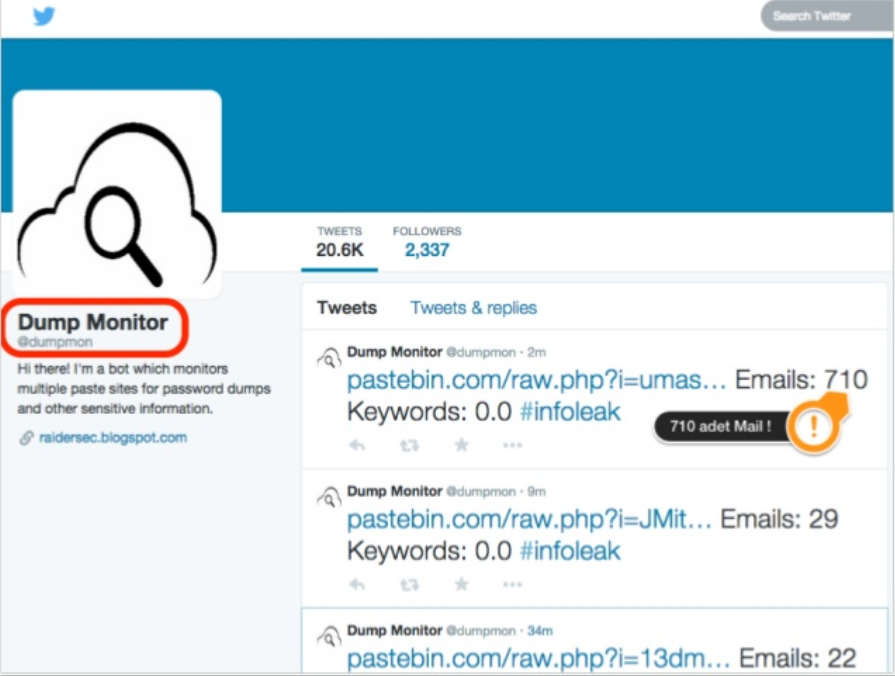
Pastebin
Twitter Pastebin
Open Source
Other Sources

Shodan
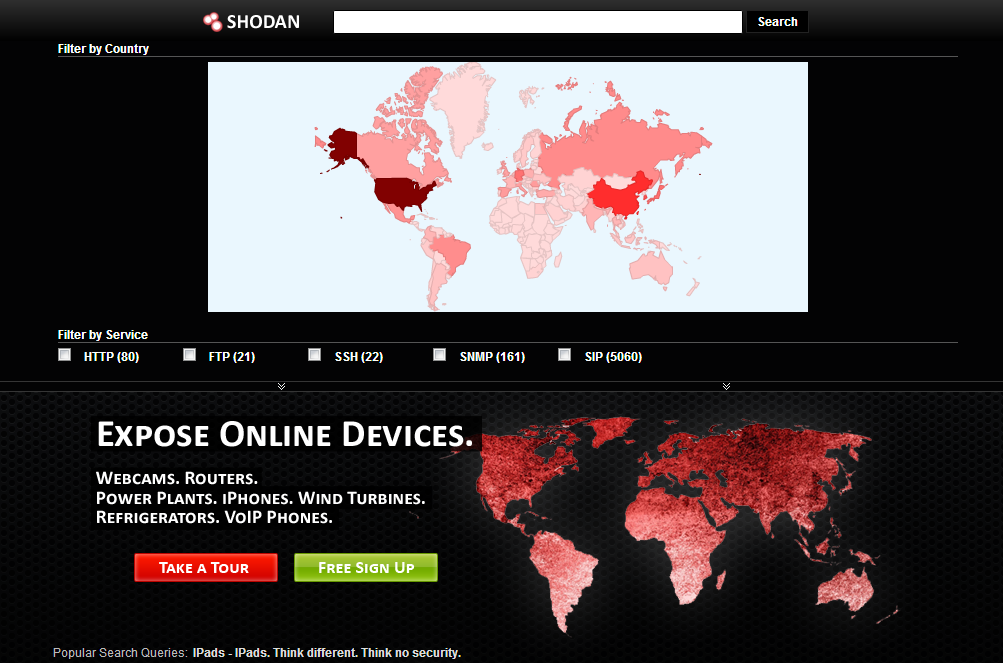
SHODAN is a searching engine that enables to find various computer-based systems (desktop, switch, router, servers, etc.) using filters. Although it is a search engine, it is very different from search engines like Google, Yahoo or Bing.
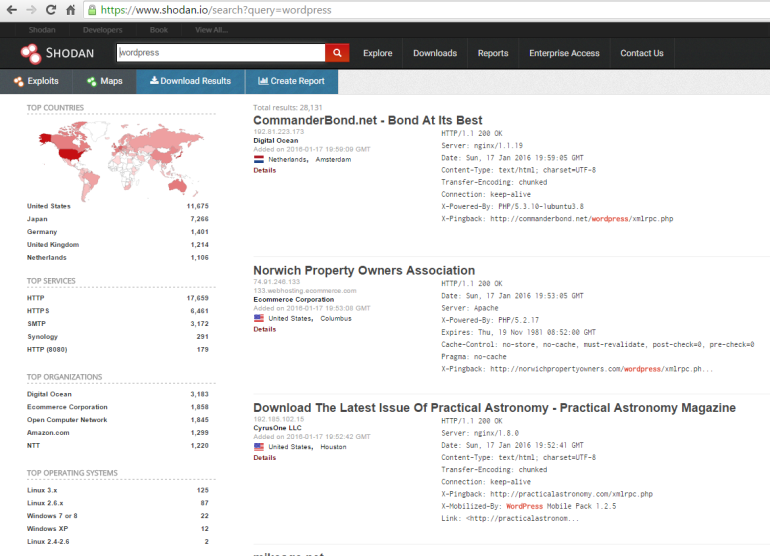
Search engines such as Google, yahoo can produce excellent results for you according to the phrase you search, but do not answer the following questions; We want to find web servers running Apache? Or what is the most popular Microsoft IIS server? There are many anonymous FTP servers, I want to see? Or a new vulnerability has emerged, to which IP addresses can I infect this vulnerability by region/country? Which backbones are there cisco routers?
Traditional search engines do not provide you with this information, nor they don't allow you to perform a search on these criteria.
TheHarvester
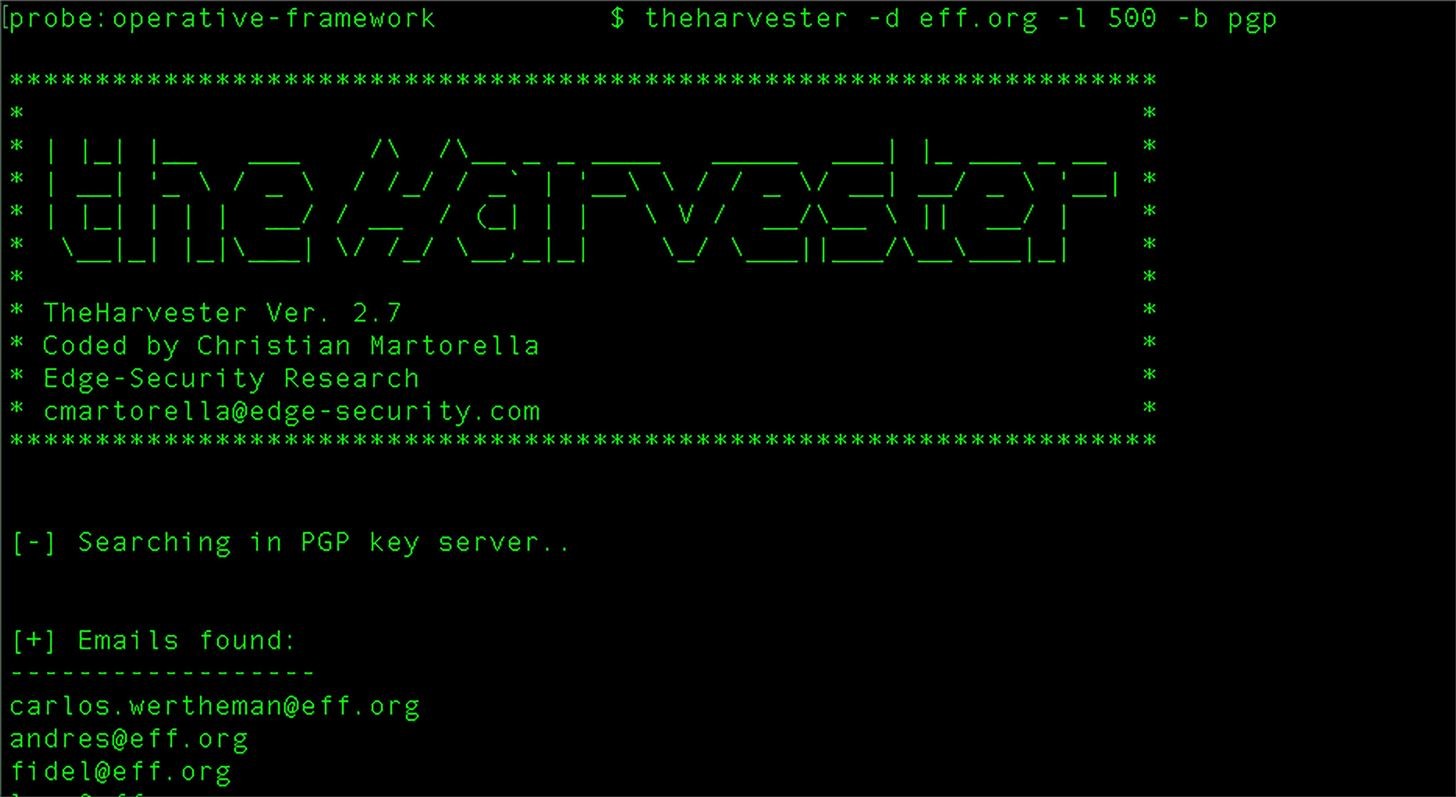
-d: We write the target site next to this parameter.
-l: This parameter specifies how many results in the search engine will extract mail, domain and subdomain information for us.
-b: We specify which search engine to use with this parameter.
For example:
Métagoofil
For example:
SpiderFoot
Domaintools.com
Reverse IP, NS, MX Record search
Detailed Whois infor
Whois History
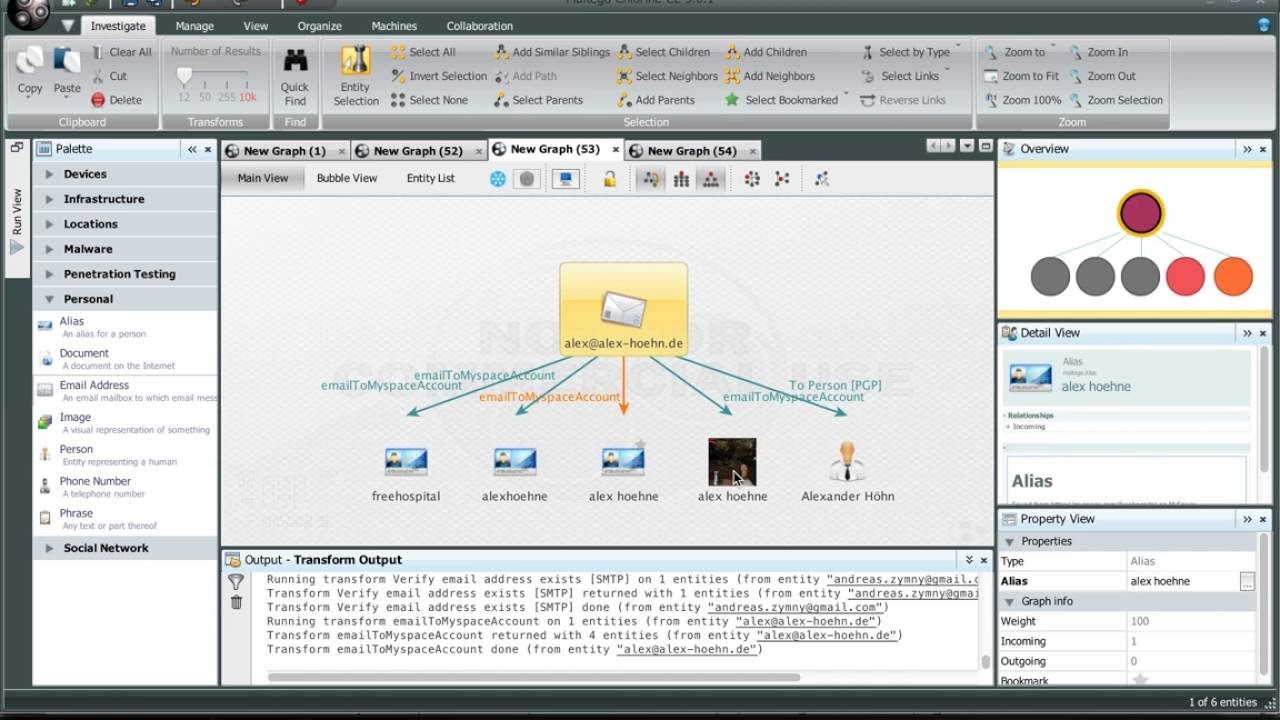
Maltego
One of my favorite OSINT tools.
Collecting information about people, groups, websites, domains and servers
It works on all platforms. (Linux, Mac OS X, Windows)
Quick and easy setup.
Simple practical with graphical user interface.
Social Media Intelligence
People he/she meets most often
Hashtags he/she used
Websites he/she shared
Liked links, content by him/her
Mentionmapp
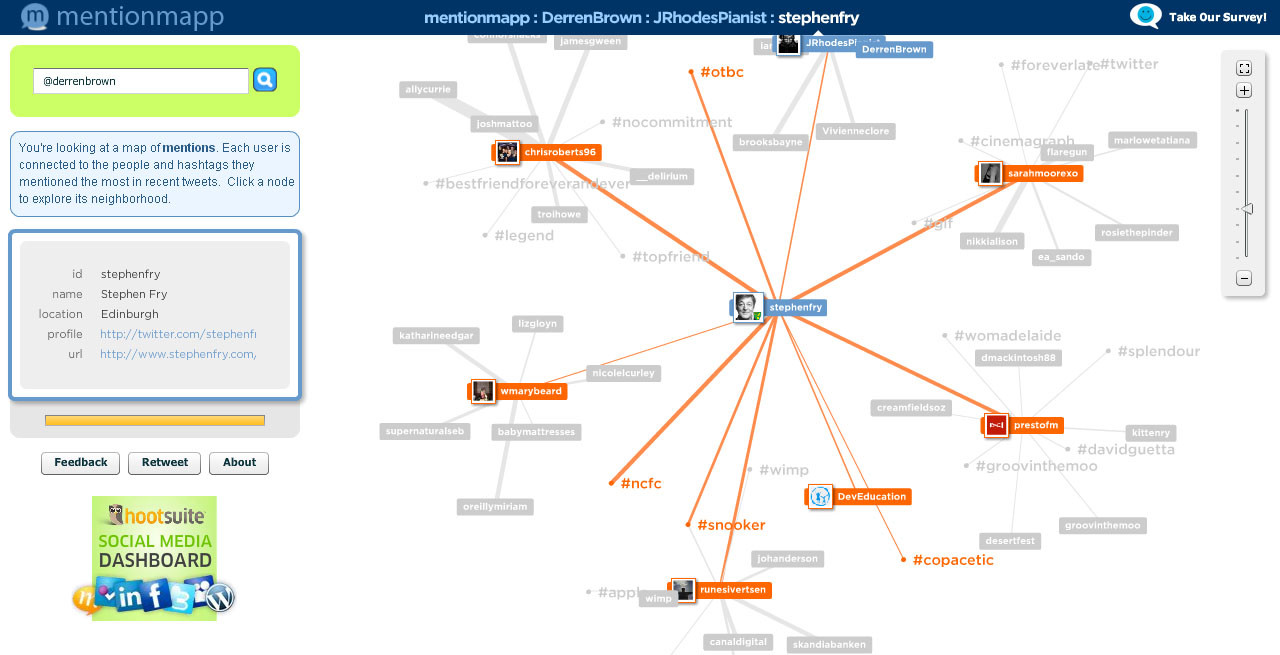
Also, as you know, Facebook, twitter, instagram Linkedin etc. platforms are very useful.
"People have more weaknesses than computers."
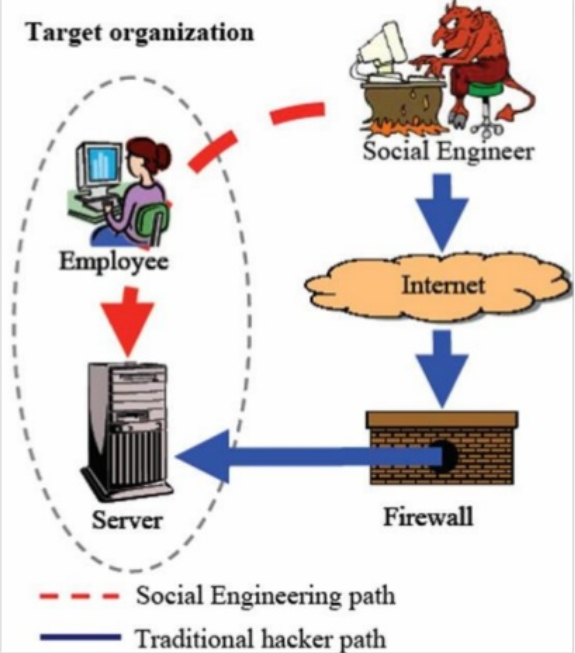
Social Engineering
Errors in human hardware, exploitation the brain.
Who Uses?
Hackers * Countries
Penetrasyon Testers * Employers
Agents * Marketers
ID Thiefs * Everyone=)
Methods
Computer Based
Phishing Attack
Online Fraud
Human Based
Impersonation
Shoulder Surfing
Dumping

Some social engineering methods:
Gathering information, disclosing information, mind games,
thinking styles, micro expressions, Neuro-Linguistic programming (NLP),
interview and questioning, rapid proximity, buffer overflow in the human mind,
persuasion, influence tactics, framing, manipulation: target control etc.
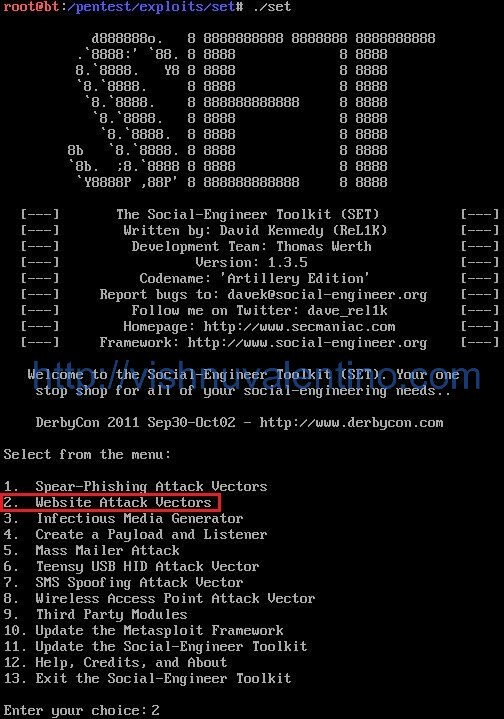
SET(social engineering toolkit)
Open Sourced
Multi phishing and browser exploit.
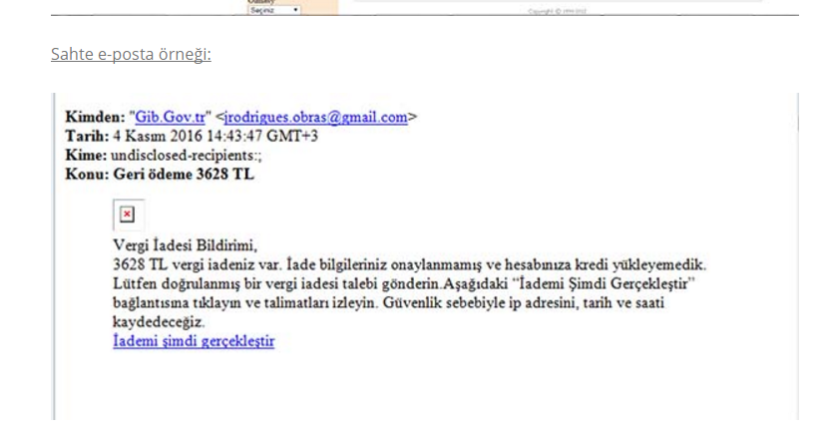
Phising Example:
Flash Disk (Rubber Ducky)

Targeted attack
Twitter > mat
> honan.net
> [email protected]
Forgot my password > m****[email protected]
Forgot my apple password >
1.Bill Addresses
2. The last four digits of credit cards
Address search on Google
The last four digits of credit cards?
1.Amazon customer service > add a new c.c.
2.Name+ e-mail address registered in the system +
Bill Address
3. Adding the fake c.c.
Amazon again
Defining a new e-mail address
1.Name+ Bill Address + c.c. number
Forgot my Amazon password > New-added e-mail address
The last four digits of the other credit card
Mat has became a victim... =)
Ways of Protection
1.Different passwords for each service/website.
2.Use Two Factor Verification
3.set "Security questions?" nonsense answers.
4.Using Virtual Credit Cards
5.Frequently review your personal information and accounts
6.Remove your information from open knowledge databases and there are many more methods ...
When you steal money or property, someone realizes it's lost. Most of the time, when you steal information, no one notices, because the information is still in their hands./ Kevin Mitnick
Source: https://www.turkhackteam.org/sosyal-muhendislik/1736226-sosyal-muhendislik-saldirilari-ve-siber-istihbarat.html
Translator: Dolyetyus

Collecting information from electronic media
Gathering information from OsInt engines/tools
Analyzing/using the information collected
Monitoring and analyzing digital security threats
and the initiation of the resistance process with the information obtained after this analysis process.
Importance Of Cyber Intelligence
States' Fear of Cyber Terrorism
Deciphering Commercial Company Information (Financial information, competitor, etc.)
Personal Information
Hackers
Privacy
Today, as a result of the state of technology, great importance is attached to cyber intelligence. Countries and institutions are attacking the information systems of competitors in order to gain superiority to each other, and aim to harm economically by disabling their cyber systems. Besides, the data stored in cyberspace was captured and thus future plans, technologies used and some other confidential information could be obtained.
As a result of a cyber attack, it is possible to interrupt all electricity services of a country at once. With attacks on SCADA systems, not only economic but also physical attacks can be carried out to the target country. As a result of an attack that can last for days, the systems of all banks and financial institutions of the country can be collapsed and rendered inoperable. It is now stated by various experts that the era of fighting with tanks and rifles is over and that wars will take place in cyberspace. The US officials stated in a statement that any cyber attack against them would be a reason for conventional warfare.
This official statement made by the USA emphasizes the importance of cyber security and cyber intelligence elements. Cyber intelligence can be on hacking, which is also defined as HACKINT, or can be obtained by using social media and various internet broadcasts, as we have stated before. In addition, cyber throttle operations, which are frequently used in Middle Eastern countries such as Syria and Iran, can also cause material and moral damage.
Determining The Target
Government agency
Staff at the establishment(Social Engineering)
Software/Product (Software theft)
Data (data theft)
Prestige (Intelligence organizations)
Banks/E-Business Systems
Personal Data (Picture, Video, privacy, blackmail)
Social Media Accounts (Curiosity, ambition etc.)
Mail (Getting information, curiosity, etc.)
OsInt
Open Source Intelligence
Public Data
OsInt, First defined by the US Department of Defense in 2005
Information Gathering Techniques & Tools
Privacy
Bitcoin * Fake Name Generator
Tor Browser Bundle * Ghostery
Cryptocat * HTTPS Everywhere
DoNotTrackMe * Hushmail alternative
Enigmail * Burn Note
Search Engines
Google Dorks * Duck Duck Go
Baidu * PunkSpider
binsearch.info * Google
Bing * Shodan
Searchenginecolossus

Google Hacking
Technique primarily used by hacker groups
Fast and multiple results
Specific results with advanced operators
Passwords user IDs, pdfs important files Dropbox sensitive datas, ip ranges
important db dumping with single dork, excel, pdf, xls scans for target.
<Dork sharing is forbidden on forum.> =)
Pastebin


Twitter Pastebin

Open Source


Other Sources

Shodan

SHODAN is a searching engine that enables to find various computer-based systems (desktop, switch, router, servers, etc.) using filters. Although it is a search engine, it is very different from search engines like Google, Yahoo or Bing.

Search engines such as Google, yahoo can produce excellent results for you according to the phrase you search, but do not answer the following questions; We want to find web servers running Apache? Or what is the most popular Microsoft IIS server? There are many anonymous FTP servers, I want to see? Or a new vulnerability has emerged, to which IP addresses can I infect this vulnerability by region/country? Which backbones are there cisco routers?
Traditional search engines do not provide you with this information, nor they don't allow you to perform a search on these criteria.
TheHarvester

-d: We write the target site next to this parameter.
-l: This parameter specifies how many results in the search engine will extract mail, domain and subdomain information for us.
-b: We specify which search engine to use with this parameter.
For example:
Kod:
python ./theharvester.py -d tarfet-site.net -l 500 -b googleMétagoofil

For example:
Kod:
Mégoofil.py -d apple.com -t doc,pdf -l 200 -n 50 -o applefiles -f results.html
Métagoofil.py -h yes -o applefiles -f results.html (local dir analysis)SpiderFoot

Domaintools.com
Reverse IP, NS, MX Record search
Detailed Whois infor
Whois History
Maltego
One of my favorite OSINT tools.
Collecting information about people, groups, websites, domains and servers
It works on all platforms. (Linux, Mac OS X, Windows)
Quick and easy setup.
Simple practical with graphical user interface.

Social Media Intelligence
People he/she meets most often
Hashtags he/she used
Websites he/she shared
Liked links, content by him/her
Mentionmapp

Also, as you know, Facebook, twitter, instagram Linkedin etc. platforms are very useful.
"People have more weaknesses than computers."
Social Engineering
Errors in human hardware, exploitation the brain.
Who Uses?
Hackers * Countries
Penetrasyon Testers * Employers
Agents * Marketers
ID Thiefs * Everyone=)
Methods
Computer Based
Phishing Attack
Online Fraud
Human Based
Impersonation
Shoulder Surfing
Dumping

Some social engineering methods:
Gathering information, disclosing information, mind games,
thinking styles, micro expressions, Neuro-Linguistic programming (NLP),
interview and questioning, rapid proximity, buffer overflow in the human mind,
persuasion, influence tactics, framing, manipulation: target control etc.

SET(social engineering toolkit)
Open Sourced
Multi phishing and browser exploit.

Phising Example:

Flash Disk (Rubber Ducky)

Targeted attack
Twitter > mat
> honan.net
> [email protected]
Forgot my password > m****[email protected]
Forgot my apple password >
1.Bill Addresses
2. The last four digits of credit cards
Address search on Google
The last four digits of credit cards?
1.Amazon customer service > add a new c.c.
2.Name+ e-mail address registered in the system +
Bill Address
3. Adding the fake c.c.
Amazon again
Defining a new e-mail address
1.Name+ Bill Address + c.c. number
Forgot my Amazon password > New-added e-mail address
The last four digits of the other credit card
Mat has became a victim... =)
Ways of Protection
1.Different passwords for each service/website.
2.Use Two Factor Verification
3.set "Security questions?" nonsense answers.
4.Using Virtual Credit Cards
5.Frequently review your personal information and accounts
6.Remove your information from open knowledge databases and there are many more methods ...
When you steal money or property, someone realizes it's lost. Most of the time, when you steal information, no one notices, because the information is still in their hands./ Kevin Mitnick
Source: https://www.turkhackteam.org/sosyal-muhendislik/1736226-sosyal-muhendislik-saldirilari-ve-siber-istihbarat.html
Translator: Dolyetyus




