- 7 Tem 2013
- 8,198
- 672
What is Social Engineering?
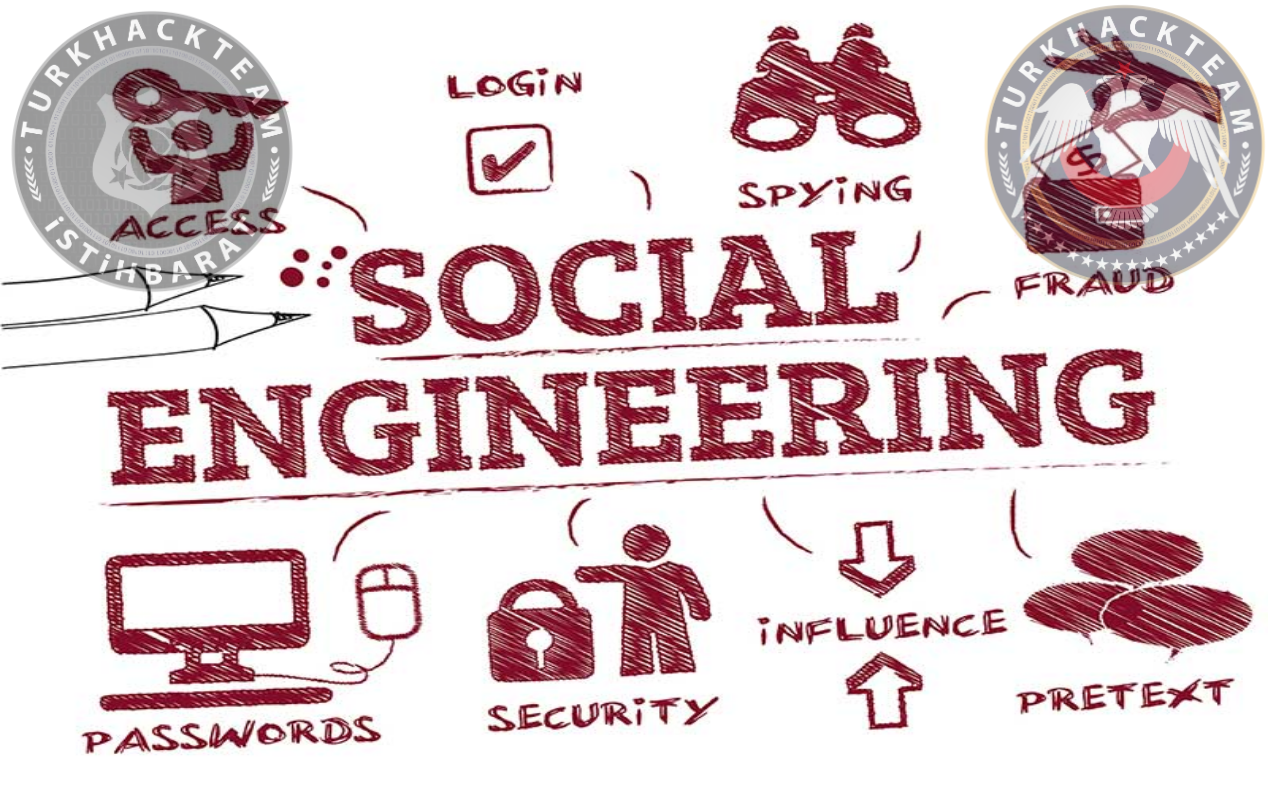
Social engineering is the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious softwarethat will give them access to your passwords and bank information as well as giving them control over your computer.

Social Engineering in IT
The fraudster's primary purpose is using psychological manipulation to gain more access to an IT system, using IT technologies to support psychological manipulation techniques to achieve the goal, for example to capture banking credentials through phishing attacks to steal the target's money.

Social Engineering Techniques
This entry will cover some of the most common techniques such as: pretexting, baiting, quid pro quo, tailgating, and phishing. Phishing attacks depend on social engineering.

Attack Technique: Pretexting
Pretexting is a method of inventing a scenario to convince victims to divulge information they should not divulge. Pretexting is often used against corporations that retain client data, such as banks, credit card companies, utilities, and the transportation industry. This is more than just a lie, in some cases it can create a completely new identity and then use it to manipulate information retrieval.
+ Example: the attacker claims to work for IT support and requests the target's password for maintenance.
There must be appropriate identification and authentication processes to survive these attacks.

Attack Technique: Baiting
Baiting is in many ways similar to phishing attacks. However, what distinguishes them from other types of social engineering is the promise of an item or good that malicious actors use to entice victims. Baiters may leverage the offer of free music or movie downloads, for example, to trick users into handing their login credentials.
Baiting attacks are not restricted to online schemes, either. Attackers can also focus on exploiting human curiosity via physical media.
Example: a USB flash drive with a keylogger but it seems like "My private pictures"


Attack Technique: Tailgating
known as tailgating or piggybacking. In these types of attacks, someone without the proper authentication follows an authenticated employee into a restricted area. The attacker might impersonate a delivery driver and wait outside a building to get things started. When an employee gains securitys approval and opens the door, the attacker asks the employee to hold the door, thereby gaining access to the building.
Tailgating does not work in all corporate settings such as large companies whose entrances require the use of a keycard. However, in mid-size enterprises, attackers can strike up conversations with employees and use this show of familiarity to get past the front desk.
Example: The attacker, dressed as an employee, carries a large box and convinces the victim, an authorized employee, at the same time to open the door of the data center using the victim's RFID pass.


Attack Technique: Phishing
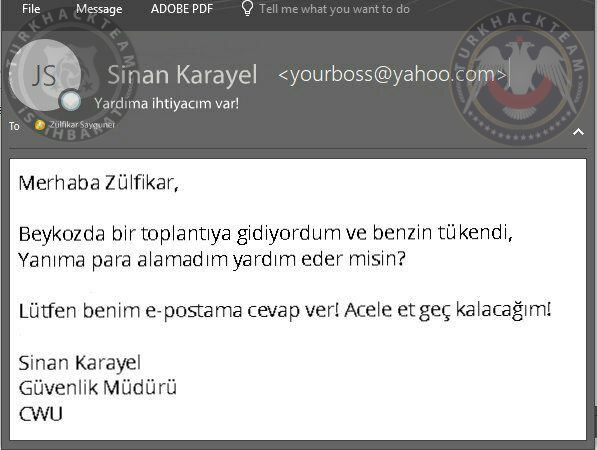
Phishing is the most common type of social engineering attack that occurs today. Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
A sample phishing attack via email;

Useful Tools for Social Engineering
https://www.turkhackteam.org/siber-...er-toolkit-set-kurulumu-ve-kullanimi-qwx.html
https://www.turkhackteam.org/siber-guvenlik/1755603-urlcrazy-kullanimi-darkhawk06.html
https://www.turkhackteam.org/exploi...-android-cihazi-dinlemek-resimli-anlatim.html
https://www.turkhackteam.org/trojan...tograf-pdf-mp3-trojan-yerlestirme-arocks.html
Source: https://www.turkhackteam.org/sosyal-muhendislik/1911640-sosyal-muhendislik-saldirilari.html
Translator Gauloran

Social engineering is the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious softwarethat will give them access to your passwords and bank information as well as giving them control over your computer.

Social Engineering in IT
The fraudster's primary purpose is using psychological manipulation to gain more access to an IT system, using IT technologies to support psychological manipulation techniques to achieve the goal, for example to capture banking credentials through phishing attacks to steal the target's money.

Social Engineering Techniques
This entry will cover some of the most common techniques such as: pretexting, baiting, quid pro quo, tailgating, and phishing. Phishing attacks depend on social engineering.

Attack Technique: Pretexting
Pretexting is a method of inventing a scenario to convince victims to divulge information they should not divulge. Pretexting is often used against corporations that retain client data, such as banks, credit card companies, utilities, and the transportation industry. This is more than just a lie, in some cases it can create a completely new identity and then use it to manipulate information retrieval.
+ Example: the attacker claims to work for IT support and requests the target's password for maintenance.

There must be appropriate identification and authentication processes to survive these attacks.

Attack Technique: Baiting
Baiting is in many ways similar to phishing attacks. However, what distinguishes them from other types of social engineering is the promise of an item or good that malicious actors use to entice victims. Baiters may leverage the offer of free music or movie downloads, for example, to trick users into handing their login credentials.
Baiting attacks are not restricted to online schemes, either. Attackers can also focus on exploiting human curiosity via physical media.
Example: a USB flash drive with a keylogger but it seems like "My private pictures"


Attack Technique: Tailgating
known as tailgating or piggybacking. In these types of attacks, someone without the proper authentication follows an authenticated employee into a restricted area. The attacker might impersonate a delivery driver and wait outside a building to get things started. When an employee gains securitys approval and opens the door, the attacker asks the employee to hold the door, thereby gaining access to the building.
Tailgating does not work in all corporate settings such as large companies whose entrances require the use of a keycard. However, in mid-size enterprises, attackers can strike up conversations with employees and use this show of familiarity to get past the front desk.
Example: The attacker, dressed as an employee, carries a large box and convinces the victim, an authorized employee, at the same time to open the door of the data center using the victim's RFID pass.


Attack Technique: Phishing
Phishing is the most common type of social engineering attack that occurs today. Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
A sample phishing attack via email;

Useful Tools for Social Engineering
https://www.turkhackteam.org/siber-...er-toolkit-set-kurulumu-ve-kullanimi-qwx.html
https://www.turkhackteam.org/siber-guvenlik/1755603-urlcrazy-kullanimi-darkhawk06.html
https://www.turkhackteam.org/exploi...-android-cihazi-dinlemek-resimli-anlatim.html
https://www.turkhackteam.org/trojan...tograf-pdf-mp3-trojan-yerlestirme-arocks.html
Source: https://www.turkhackteam.org/sosyal-muhendislik/1911640-sosyal-muhendislik-saldirilari.html
Translator Gauloran





