

What is CVE-2023-32784 Vulnerability? (KeePass Software)
"CVE-2023-32784, allows the retrieval of a plaintext master password from a memory dump. The memory dump can be from a KeePass process, a swap file (pagefile.sys), a hibernation file (hiberfil.sys), or a RAM dump on the entire system.
KeePass 2.X uses a specialized text box for password entry called SecureTextBoxEx. The vulnerability used in this CVE is the creation of a residue string in memory for every character entered. Due to the nature of how .NET works, it is nearly impossible to dispose of it once created. For example, when typing "Password," it will result in residue strings like •a, ••s, •••s, ••••w, •••••o, ••••••r, •••••••D. The first character cannot be recovered.
Let's Examine the Vulnerability Scenario for KeePass CVE-2023-32784
Note:
To recreate the scenario, we are using KeePass version 2.38 for Linux with Ubuntu 18.04.1. The Proof of Concept (PoC) is also based on this Github repository, which is part of the original PoC.
The PoC we are using follows these steps to extract the KeePass secret key:
Firstly, scan all files in /proc/<pid>/cmdline and store the pids of those associated with the KeePass keyword.
Next, obtain the addresses of memory maps that are not directly related to a library.
Finally, parse the memory of all these maps in /proc/<pid>/mem. Attempt to find the remaining strings that look like •a, ••s, •••s, and so on, as the user enters the master password."
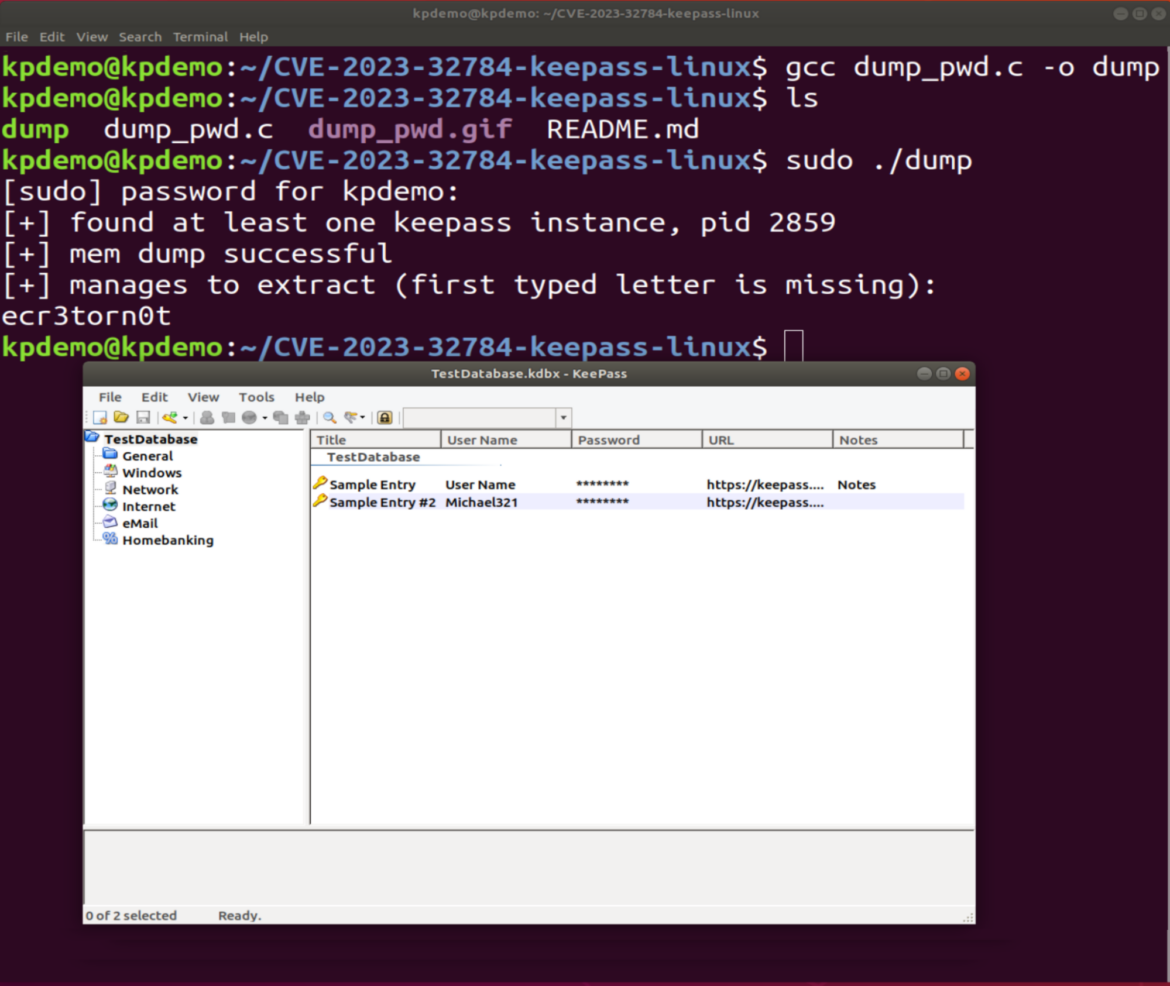
"As seen in the image above, the master key is revealed without the initial character.
How to Detect the KeePass CVE-2023-32784 Vulnerability?
/proc
To detect such an attack, we should be able to monitor access to the folder by an unknown process. This triggers an alert, and further investigation can be conducted.
If we attempt to detect this with an open-source project within the CNCF scope using
Falco
, it provides real-time detection of unusual activities in cloud-native environments by sending alerts. In this scenario, we need to set or create the Read environment variable from /proc files.
To trigger this rule correctly, we should modify the condition to capture the reading of /proc/<pid>/cmdline, /proc/<pid>/maps, or ./proc/<pid>/mem, which were used in the PoC to obtain the KeePass master password."
Kod:
- rule: Dump memory detection
desc: An attempt to read process environment variables from /proc files
condition: >
open_read and container and (fd.name glob "/proc/*/mem" or fd.name glob "/proc/*/maps")
output: >
Detected process memory dump to search for credentials (proc.name=%proc.name proc.pname=%proc.pname fd.name=%fd.name container=%container.info evt.type=%evt.type evt.arg.request=%evt.arg.request proc.pid=%proc.pid proc.cwd=%proc.cwd proc.ppid=%proc.ppid proc.cmdline=%proc.cmdline proc.pcmdline=%proc.pcmdline)With this new rule, we can detect the exploitation of CVE-2023-32784.
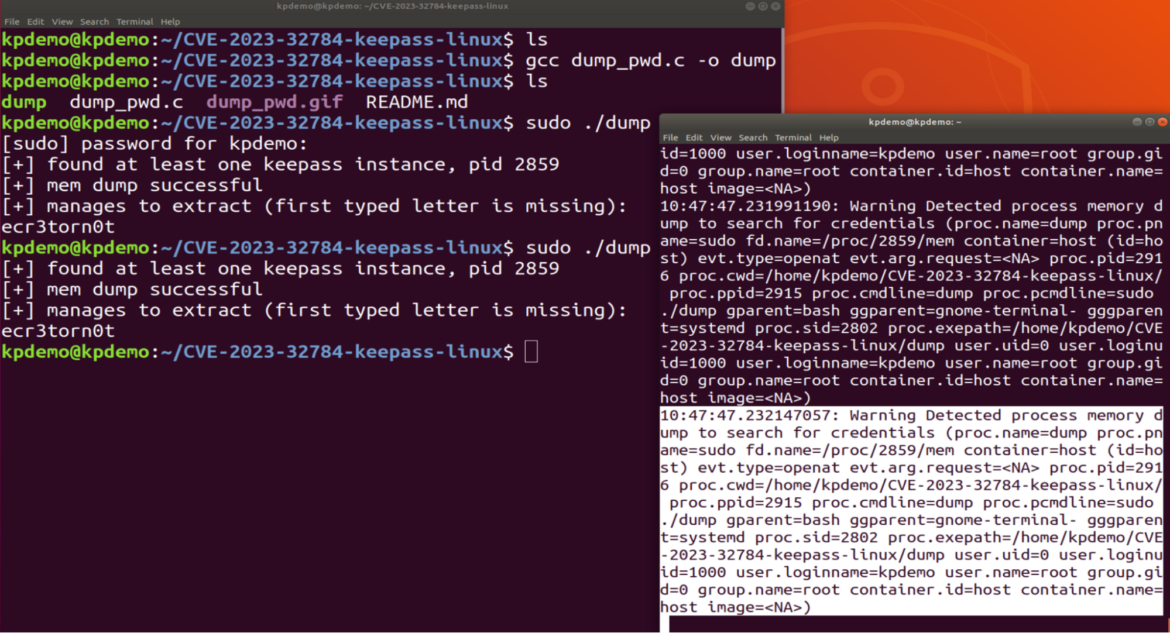
The alert contains all the information we need to continue investigating the threat.
Kod:
10:47:47.232147057: Warning Detected process memory dump to search for credentials (proc.name=dump proc.pname=sudo fd.name=/proc/2859/mem container=host (id=host) evt.type=openat evt.arg.request=<NA> proc.pid=2916 proc.cwd=/home/kpdemo/CVE-2023-32784-keepass-linux/ proc.ppid=2915 proc.cmdline=dump proc.pcmdline=sudo ./dump gparent=bash ggparent=gnome-terminal- gggparent=systemd proc.sid=2802 proc.exepath=/home/kpdemo/CVE-2023-32784-keepass-linux/dump user.uid=0 user.loginuid=1000 user.loginname=kpdemo user.name=root group.gid=0 group.name=root container.id=host container.name=host image=<NA>)[/SIZE][/B][/CENTER]
[B][SIZE=5][CENTER]If the attacker has the necessary permissions and capabilities on your machine, as mentioned in the exploitation, they can carry out various malicious actions. However, this rule can provide us with an indicator of whether our credentials have been compromised and allow us to act accordingly.
How to Dump Process Memory?
If we delve a bit further into this technique, we'll find other tools that perform similar actions. Let's take a look at a couple of them and how we can detect them in the same way.
Using the Mimipenguin Tool
Mimipenguin 2.0 is a tool for dumping the login password of the current Linux desktop user. It is adapted from the concept behind the popular Windows credential theft tool, mimikatz.
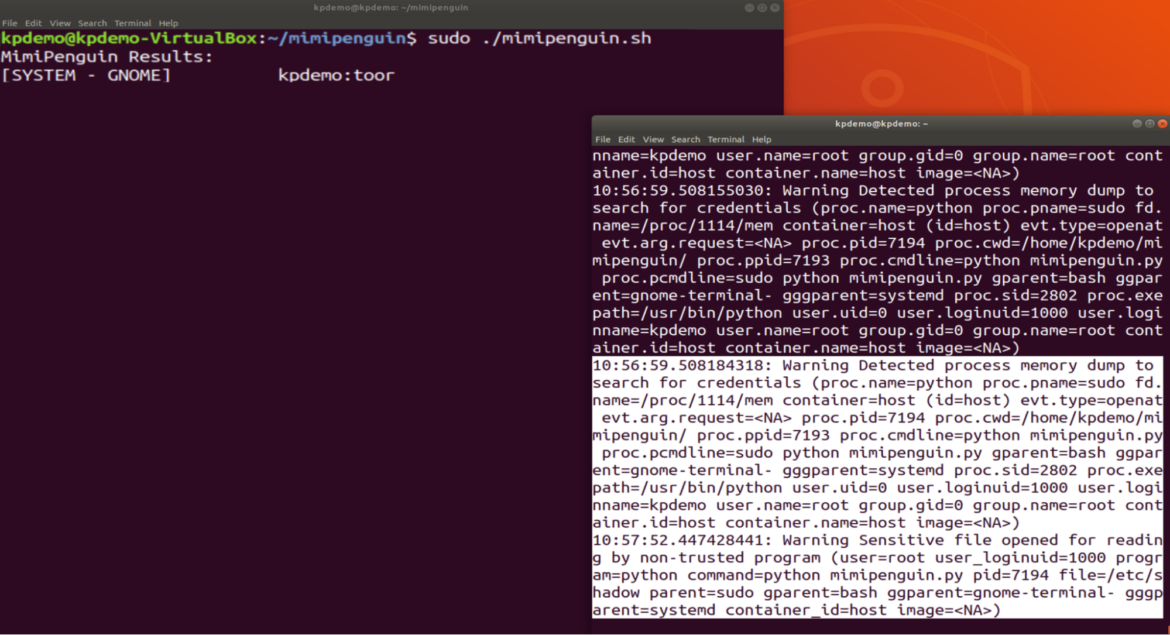
The tool attempts to do something similar to the KeePass PoC but, in this case, it cannot find the key (because CVE has not been applied). However, it can obtain system credentials. In the image above, we can see both alerts;
the first one relates to /proc/<pid>/mem.
Kod:
10:56:59.508184318: Warning Detected process memory dump to search for credentials (proc.name=python proc.pname=sudo fd.name=/proc/1114/mem container=host (id=host) evt.type=openat evt.arg.request=<NA> proc.pid=7194 proc.cwd=/home/kpdemo/mimipenguin/ proc.ppid=7193 proc.cmdline=python mimipenguin.py proc.pcmdline=sudo python mimipenguin.py gparent=bash ggparent=gnome-terminal- gggparent=systemd proc.sid=2802 proc.exepath=/usr/bin/python user.uid=0 user.loginuid=1000 user.loginname=kpdemo user.name=root group.gid=0 group.name=root container.id=host container.name=host image=<NA>)The second one is where it gains access to where the user's password is extracted, which is /etc/shadow.
Kod:
10:57:52.447428441: Warning Sensitive file opened for reading by non-trusted program (user=root user_loginuid=1000 program=python command=python mimipenguin.py pid=7194 file=/etc/shadow parent=sudo gparent=bash ggparent=gnome-terminal- gggparent=systemd container_id=host image=<NA>)[/SIZE][/B][/CENTER]
[B][SIZE=5][CENTER]What is LaZagne?
The LaZagne project is an open-source application used to retrieve numerous passwords stored on a local computer. In this case, it not only focuses on memory but also searches for credentials using various techniques (plaintext, API, custom algorithms, databases, etc.).
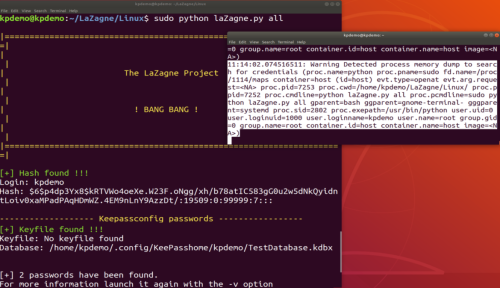
In this example, once again, we have an alert that detects the access, and the tool shows us that it has found both the user's password and the KeePass database we saved.
Kod:
11:14:02.074516511: Warning Detected process memory dump to search for credentials (proc.name=python proc.pname=sudo fd.name=/proc/1114/maps container=host (id=host) evt.type=openat evt.arg.request=<NA> proc.pid=7253 proc.cwd=/home/kpdemo/LaZagne/Linux/ proc.ppid=7252 proc.cmdline=python laZagne.py all proc.pcmdline=sudo python laZagne.py all gparent=bash ggparent=gnome-terminal- gggparent=systemd proc.sid=2802 proc.exepath=/usr/bin/python user.uid=0 user.loginuid=1000 user.loginname=kpdemo user.name=root group.gid=0 group.name=root container.id=host container.name=host image=<NA>)[/SIZE][/B][/CENTER]
[B][SIZE=5][CENTER]What Have We Learned from This Article?
Collecting credentials is a very common technique used by attackers. To detect such actions and prevent lateral movement or disruption of other services, it is essential to have all the necessary tools in place.
Falco provides us with a final layer of security that allows us to monitor access and detect malicious behaviors.
Lastly, we strongly recommend upgrading to the new version, KeePass 2.54.
Source : https://www.turkhackteam.org/konular/cve-2023-32784-acigi-nedir-keepass-yazilimi.2045212/





