Kullanıcı1233
Kıdemli Üye
- 19 Tem 2011
- 4,371
- 12

Hello everyone. In this post, i'm gonna explain malware analysis. New malwares increasing day by day. Malware attacks that targeted to companies, institutions and organizations can damage financially. We have to analyse it to a**** these malware attacks. I'll try to explain how to do that. But first of all, what is malware?
What is Malware?
Malware is a malicious software that used for leaking datas or infos out upon its developer's request by infecting into systems. Malware stands for malicious software.
What are Intended Uses of Malware?
Malware that infected into system can leak so many infos out. For example, a malware that infected into your phone can see your calls and messages. It can even call or send message to someone. And also it can see your files or pictures, too.
A malware that infected into your computer can listen, see, and follow your computer, leak something out of your computer and make your computer a zombie that used in ddos attacks. A malware can these examples and much more.
How Does a Malware Infect?
There a lot of methods of infecting into system. Such as:
- By using browser vulnerabilities.
- By using something like USB, DVD, CD, Autorun, etc.
- By social engineering methods (e-mail, message, etc.).
What are Methods of Developing a Malware?
There are 2 types of that:
- Developing by using software that can be found in all over the Internet.
- Developing by coding it yourself, not with softwares.
What are Extensions of Malwares?
Most of people think that malwares only have .exe extensions. But that's just wrong. You can check it out: https://sensorstechforum.com/popular-windows-file-types-used-malware-2018/
What are Methods of Malware Analysis?
There are a couple of methods of malware analysis such as: behavioral, code (static and dynamic), and memory.
What is Behavioral Malware Analysis?
Malware's behavior on network, registry, file systems are examined. These behaviors are analyzed.
Some programs that you can use: Process Monitor, Process Explorer, Regshot, Wireshark, CaptureBat, Cuckoo Sandbox.
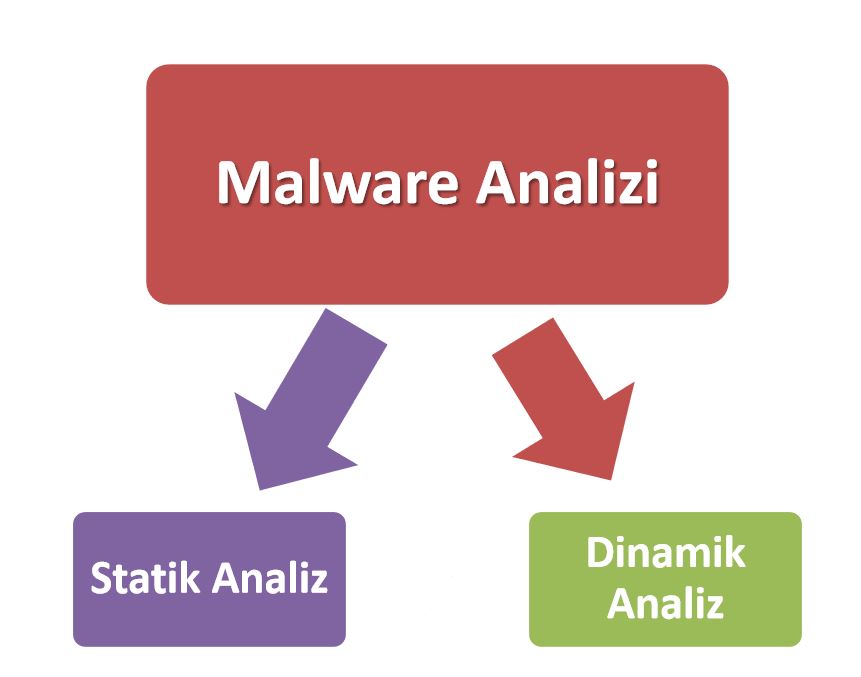
What is Code Analysis?
Code analysis is examined under two general headings: static and dynamic analysis.
What is Static (Binary) Analysis?
Static analysis is the examination of malware by looking at its code without running it on the system. It's the easiest method. There are some signature-based detection. It's easy to bypass static examination.
There is a method about making examination harder, to use methods like crypter and fud.
Some programs that you can use: Strings, IDA, Dependency Walker, PEiD, JAD, Reflector, dnSpy.
What is Dynamic Analysis?
Dynamic analysis is the examination of malware's behaviours with various tools by running it on the system with debugger of malware. It's all about analysing how does effect the system by running it on Sandbox.
Unlike static analysis, it's a lil bit dicier. When it's run on the system, it can give some damage, or delete something, etc. This is why it has to be in isolated environment such as Sandbox, VMware, or VirtualBox.
Some programs that you can use: IDA, Ollydbg, Immunity Debugger, Windbg.
What is Memory Analysis?
It is the examination of the infected computer with various tools by taking the current ram image.
Some programs that you can use: Volatility, Memoryze, Redline.

How to Make Malware Analysis Difficult?
There are some methods to make it difficult. Thanks to these methods, we can bypass antivirus or firewall and infect our virus into system.
But these methods are for disguiding optimized systems. It wouldn't be so hard to detect this precautions for an experienced malware analyst.
- Anti Debugging: It makes debugging difficult.
- Anti WM: It detects if malware runs on virtual machine.
- Obfuscation: It makes codes converting into source codes and analysing it difficult.
- Packing: It packs malware in order to make static analysis difficult.
- Anti Disassemling: It makes analysis difficult by exploiting the vulnerabilities in disassembler algorithm.
Online Malware Analysis Websites
https://www.hybrid-analysis.com/
https://www.virustotal.com/
https://www.joesandbox.com/
Original: https://www.turkhackteam.org/zararli-yazilim-analizi/1793326-malware-analizi-nedir-senzero.html
Translator: R4V3N




