Hello, Today we will review with you the topic of "Windows Internals".
So what is it?
Let's call it a kernel in short, there is no need to confuse you at all.
So what will we learn?
virtual memory, kernel mode and user mode, win32 api and more.
Of course, while explaining these, I will tell you how to analyze malware in a cursory way. Otherwise, we need to write a book for this.
Our first title is "Virtual Memory"
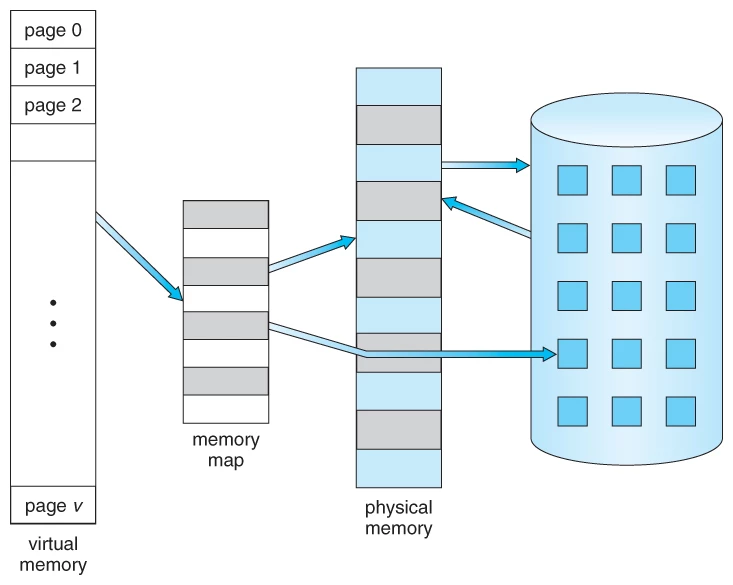
Our friend, which we call virtual memory, creates an invisible space between the CPU and the operating system instead of sending it directly to the physical memory. In other words, an imaginary environment is created by the operating system.
Our operating system creates a table for the transaction called by the CPU, which is called a "page table".
This is how virtual memory works.
Next up is "Kernel and User Mode"
To briefly explain without confusing you, applications running in kernel mode have full authority in the system and can access without any limitations (the type of virus we call rootkit works on kernel mode). In user mode, they cannot directly access the hardware. Through the APIs of operating systems, they can access resources such as CPUs and RAM. that is, they can only work on their own resources.

Let's examine kernel32.dll in simple terms. In such a situation, we can see what we can come across.
Our list of requirements is: cff explorer and C:WindowsSystem32Kernel32.dll
Let's open our cff explorer application and select the kernel32.dll file from the system32 folder and open it. Then let's make a small click on the "Export directory" section and the section that appears -
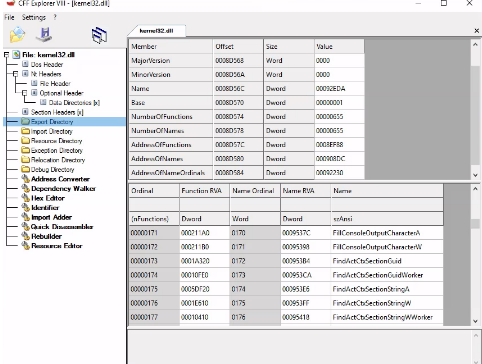
Through this kernel32.dll we can easily see what kind of powers our friend has, what he has accessed, what he can change. You can observe this again on any virus.
Yes, let's talk about the Win32 API next.
There are too many APIs in the Windows operating system. However, we can say that the most popular is Win32 Api. This api works fine on both 32-bit and 64-bit. We actively use winapi when making a program/software and, as you can imagine, use this API in malware.
When doing the malicious analysis, you will encounter plenty of APIs. However, this does not mean that the software is harmful, many programs that we use in our daily lives use it. To understand that this is malware, it is better to examine the way the API is used.
So how do we understand that this is malware?

We will solve this problem with Obtaining API Logs
;
When performing the analysis with the PE file on the exe, we may encounter API names. However, looking at APIs statically is not very useful as we mentioned above. At this point, what we need is dynamic analysis, or we will have to deal with reverse engineering by debugging.
APIMiner comes to our rescue while looking at API Logs. Thanks to APIMiner, we can access the logs of APIs while performing dynamic analysis. APIMiner Github: GitHub - poona/APIMiner: API Logger for Windows Executables
Well, the year 2022 has been hundreds of
WIN32 Api
available from the Windows operating system and SDKs. Now let's examine where and how we can access these APIs and the uses of these friends.

Win32 DLLs
We can find the Win32 APIs in the folder "C:WindowsSystem32". So in short, system32. As we showed above, you can examine the kernel32.dll file again with CFF explorer.
The .DLL files I mentioned below are both necessary for Windows to work and dll files that our viruses frequently use:
NTDLL.DLL
KERNEL32.DLL
KERNELBASE.DLL
USER32.DLL
NETAPI32.DLL
And it goes on and on...
These are the DLLs that come by the SDKs (I'll show you an example of the DLLs that come with Visual Studio). Located at the end 60, 120, 20... The numbers found such as refer to the versions of the SDKs.
MSVCRT.DLL
MSVCP100.dll
MSVBVM60.DLL
VCRUNTIME140.DLL
Programs written in languages such as C# VB.NET use the .NET framework's own DLLs. An The dlls we mentioned above will generally come up all the time. Now we will use MSDN to collect information about Win32 APIs, such as what features DLLs can do.

Collect information about the Win32 API by Using MSDN
The most useful place to learn about an API is on MSDN. (Microsoft software developer network) When we search on google (or other search engines), it comes out first.
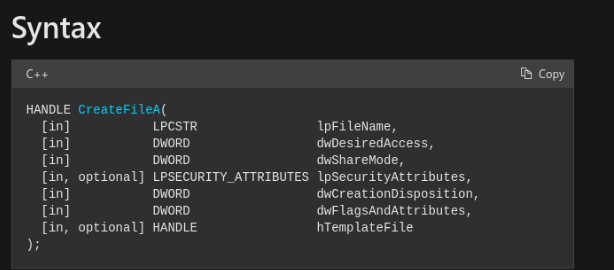
MSDN documentation for the CreateFile() Win32 API
Thank you for reading enough of this day and I wish you all a good day.


Translator: @ByFelez
Subject Author: @0xd2
Subject: https://www.turkhackteam.org/konular/windows-internals-nedir.2017262/
So what is it?
Let's call it a kernel in short, there is no need to confuse you at all.
So what will we learn?
virtual memory, kernel mode and user mode, win32 api and more.
Of course, while explaining these, I will tell you how to analyze malware in a cursory way. Otherwise, we need to write a book for this.
Our first title is "Virtual Memory"
Our friend, which we call virtual memory, creates an invisible space between the CPU and the operating system instead of sending it directly to the physical memory. In other words, an imaginary environment is created by the operating system.
Our operating system creates a table for the transaction called by the CPU, which is called a "page table".
This is how virtual memory works.

Next up is "Kernel and User Mode"
To briefly explain without confusing you, applications running in kernel mode have full authority in the system and can access without any limitations (the type of virus we call rootkit works on kernel mode). In user mode, they cannot directly access the hardware. Through the APIs of operating systems, they can access resources such as CPUs and RAM. that is, they can only work on their own resources.

Let's examine kernel32.dll in simple terms. In such a situation, we can see what we can come across.
Our list of requirements is: cff explorer and C:WindowsSystem32Kernel32.dll
Let's open our cff explorer application and select the kernel32.dll file from the system32 folder and open it. Then let's make a small click on the "Export directory" section and the section that appears -

Through this kernel32.dll we can easily see what kind of powers our friend has, what he has accessed, what he can change. You can observe this again on any virus.
Yes, let's talk about the Win32 API next.
There are too many APIs in the Windows operating system. However, we can say that the most popular is Win32 Api. This api works fine on both 32-bit and 64-bit. We actively use winapi when making a program/software and, as you can imagine, use this API in malware.
When doing the malicious analysis, you will encounter plenty of APIs. However, this does not mean that the software is harmful, many programs that we use in our daily lives use it. To understand that this is malware, it is better to examine the way the API is used.
So how do we understand that this is malware?

We will solve this problem with Obtaining API Logs
;
When performing the analysis with the PE file on the exe, we may encounter API names. However, looking at APIs statically is not very useful as we mentioned above. At this point, what we need is dynamic analysis, or we will have to deal with reverse engineering by debugging.
APIMiner comes to our rescue while looking at API Logs. Thanks to APIMiner, we can access the logs of APIs while performing dynamic analysis. APIMiner Github: GitHub - poona/APIMiner: API Logger for Windows Executables
Well, the year 2022 has been hundreds of
WIN32 Api
available from the Windows operating system and SDKs. Now let's examine where and how we can access these APIs and the uses of these friends.

Win32 DLLs
We can find the Win32 APIs in the folder "C:WindowsSystem32". So in short, system32. As we showed above, you can examine the kernel32.dll file again with CFF explorer.

The .DLL files I mentioned below are both necessary for Windows to work and dll files that our viruses frequently use:
NTDLL.DLL
KERNEL32.DLL
KERNELBASE.DLL
USER32.DLL
NETAPI32.DLL
And it goes on and on...
These are the DLLs that come by the SDKs (I'll show you an example of the DLLs that come with Visual Studio). Located at the end 60, 120, 20... The numbers found such as refer to the versions of the SDKs.
MSVCRT.DLL
MSVCP100.dll
MSVBVM60.DLL
VCRUNTIME140.DLL
Programs written in languages such as C# VB.NET use the .NET framework's own DLLs. An The dlls we mentioned above will generally come up all the time. Now we will use MSDN to collect information about Win32 APIs, such as what features DLLs can do.

Collect information about the Win32 API by Using MSDN
The most useful place to learn about an API is on MSDN. (Microsoft software developer network) When we search on google (or other search engines), it comes out first.

MSDN documentation for the CreateFile() Win32 API

Thank you for reading enough of this day and I wish you all a good day.


Translator: @ByFelez
Subject Author: @0xd2
Subject: https://www.turkhackteam.org/konular/windows-internals-nedir.2017262/








