

CVE-2023-25690 What is the Security Vulnerability in Apache HTTP Server?
Specific mod_proxy configurations between versions 2.4.0 and 2.4.55 of the Apache HTTP Server can be exploited for an HTTP Request Smuggling attack.
HTTP Request Smuggling is a sophisticated attack method that exploits inconsistencies in the processing of HTTP requests by various web infrastructure components. Attackers using this technique manipulate the interpretation of requests, leading to bypassing security measures, unauthorized injection of malicious payloads, potential access to sensitive data, or even remote code execution.
This vulnerability arises when mod_proxy is enabled with RewriteRule or ProxyPassMatch, where a specific pattern provided by the user matches a portion of the request target (URL) data and is then added to the proxied request target using variable substitution. An example could be:
Kod:
RewriteEngine on
RewriteRule "^/here/(.*)" "http://example.com:8080/elsewhere?param=$1"; [P]As a result, request splitting or smuggling may occur, potentially bypassing access controls on the proxy server, unintentional proxying of URLs to existing origin servers, and leading to cache poisoning.
The Apache HTTP Server vulnerability gained attention when it was publicly disclosed as proof by a researcher named dhmosfunk. The proof demonstrated how this vulnerability could be exploited for header injection and request smuggling attacks, but several conditions must be met to be affected by this vulnerability:
The configuration of the Apache server must include a RewriteRule that copies data to the query string of a proxy URL.
The application must consider the proxy as a significant security boundary.
The application must operate on a vulnerable Apache HTTP Server version (2.4.55 or earlier).
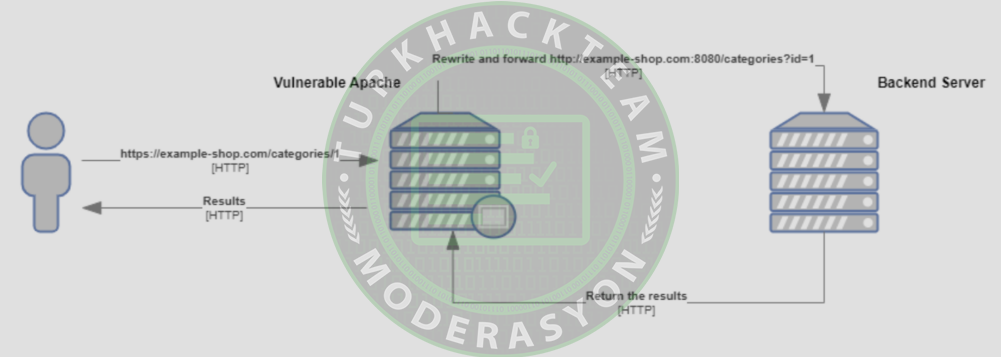
Proof of Concept attack data flow (Source: GitHub)
According to Shodan's data, more than 6 million servers may be vulnerable to this exploit.
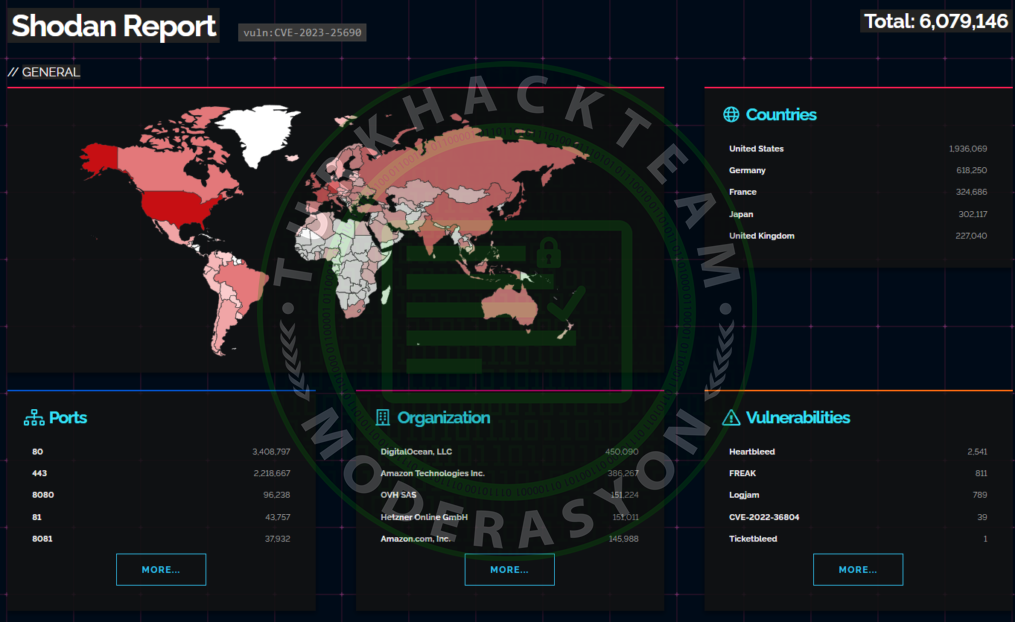
CVE-2023-25690 Shodan Search (Source: Shodan)
To address the CVE-2023-25690 vulnerability, especially if your services rely on RewriteRule entries, it is strongly recommended to update the Apache version to 2.4.56 or a newer release.
Enhance Vulnerability Management and Attack Surface Monitoring with SOCRadar
SOCRadar's Vulnerability Intelligence can assist in better managing vulnerability issues and prioritizing patches. You can search for and view detailed information about vulnerabilities on the platform.
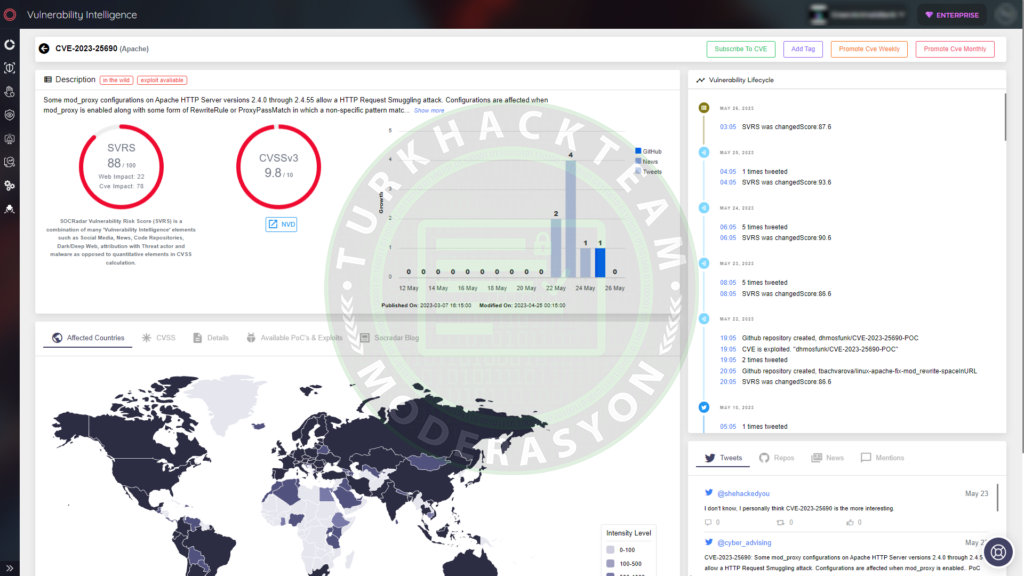
Source : https://www.turkhackteam.org/konula...e-http-sunucusu-guvenlik-acigi-nedir.2048056/
The Apache HTTP Server vulnerability gained attention when it was publicly disclosed as proof by a researcher named dhmosfunk. The proof demonstrated how this vulnerability could be exploited for header injection and request smuggling attacks, but several conditions must be met to be affected by this vulnerability:
The configuration of the Apache server must include a RewriteRule that copies data to the query string of a proxy URL.
The application must consider the proxy as a significant security boundary.
The application must operate on a vulnerable Apache HTTP Server version (2.4.55 or earlier).

Proof of Concept attack data flow (Source: GitHub)
According to Shodan's data, more than 6 million servers may be vulnerable to this exploit.

CVE-2023-25690 Shodan Search (Source: Shodan)
To address the CVE-2023-25690 vulnerability, especially if your services rely on RewriteRule entries, it is strongly recommended to update the Apache version to 2.4.56 or a newer release.
Enhance Vulnerability Management and Attack Surface Monitoring with SOCRadar
SOCRadar's Vulnerability Intelligence can assist in better managing vulnerability issues and prioritizing patches. You can search for and view detailed information about vulnerabilities on the platform.

Source : https://www.turkhackteam.org/konula...e-http-sunucusu-guvenlik-acigi-nedir.2048056/





