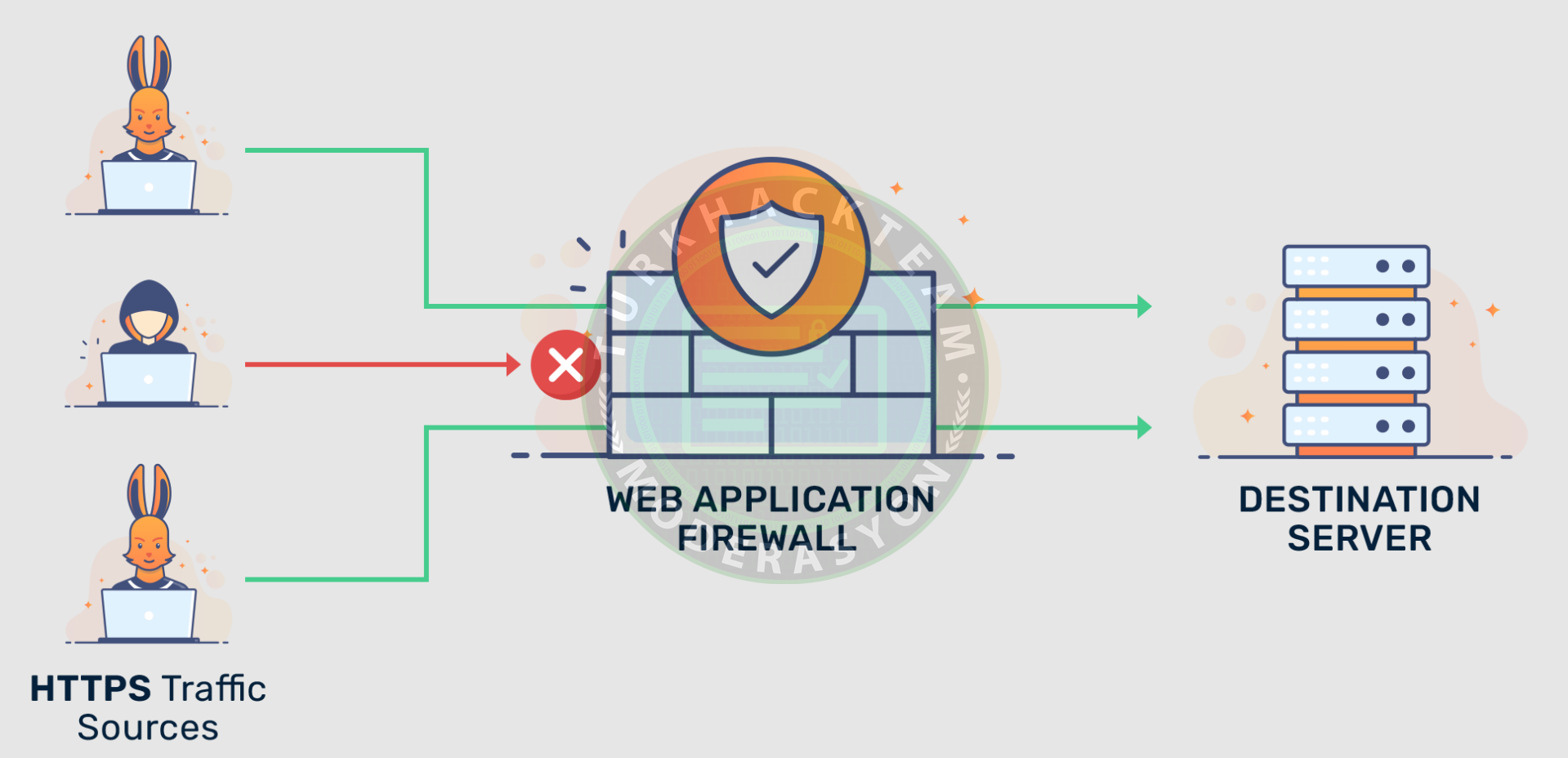

How to Bypass WAF in Burp Suite - Installation Guide?
WAF stands for Web Application Firewall. It is a popular defense tool against web application attacks. WAF protects web applications against various application layer attacks, such as cross-site scripting (XSS), SQL injection, and cookie poisoning, by examining and filtering traffic between each web application and the internet. Therefore, using WAF helps safeguard the company's web applications by analyzing and filtering traffic between each web application and the internet.

First Steps in Bypassing WAF
WAF protects your online business by securely handling sensitive customer data. Understanding the threats you may encounter is crucial when preparing to establish a company that deals with a trade website, online financial services, or any web-based product. As WAFs provide protection against different types of threats, selecting the right one is important.
WAF can be particularly beneficial for services involving interactions with customers or business partners. It adds certain protections that help maintain your company's reputation and market position. As an administrator, you need WAF for application visibility, aiding in compliance with regulatory standards such as PCI, HIPAA, and GDPR. WAF adds an essential extra defense layer to an already robust application security program. Additionally, as a security professional, you can leverage a web application firewall to monitor a potential attack during an incident and receive alerts for activities violating predefined rules. You can use WAF as a reliable defense line for applications. Here is a list of the most common application security vulnerabilities:
1- Injection attacks
2- Broken Authentication
3- Sensitive data exposure
4- XML External Entities (XXE)
5- Broken Access control
6- Security misconfiguration
7- Cross-Site Scripting (XSS)
8- Insecure Deserialization
Moreover, to bypass some WAF products, you can add headers to all Burp requests. This extension automatically adds the following headers to all requests. Let's take a look at their list:
Kod:
X-Originating-IP: 127.0.0.1
Kod:
X-Forwarded-For: 127.0.0.1
Kod:
X-Remote-IP: 127.0.0.1
Kod:
X-Remote-Addr: 127.0.0.1
Kod:
X-Client-IP: 127.0.0.1Bypassing WAF Techniques
Let's explore WAF bypass techniques using HTTP standards and the behavior of web servers. In this section, you'll learn a creative array of techniques for evading and reshaping HTTP requests by exploiting peculiar behaviors of web servers and features such as request encoding or HTTP pipelining. These methods demonstrate that developers should not rely solely on WAFs as a defense mechanism, but when can you employ these techniques?
1- As a penetration testing expert, you can use this to test a website behind a WAF, avoiding drama and pain.
2- Defense teams can utilize this method to design appropriate measures.
Bypassing Some WAF Devices Using Burp Extension
Download and compile the Python version, Java version, or Java source of the extension. Then, use this extension to add the necessary headers. After installing the extension, follow these steps:
1- Launch Burp.
2- Go to the "Extender >> Extensions" section.
3- Click the "Add" button.
4- Select the extension type as "Java."
Note: If you are using the Java Extension, choose the "Java" extension type. If you are using the Python version, select the "Python" extension type, and then navigate to the extension path.
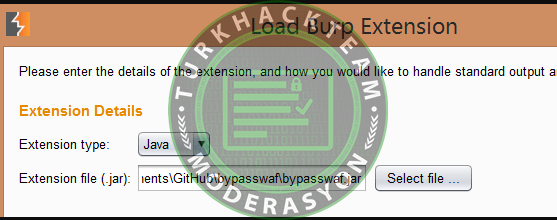
The extension will be added as shown below:

To proceed, follow the steps below:
1- Go to the "Options >> Sessions" section.
2- Click the "Add" button for "Session Handling Rules."
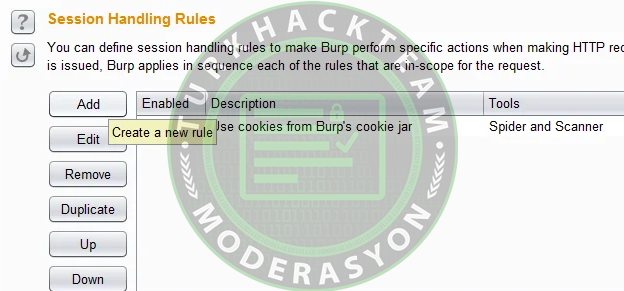
In the next step, you need to give the rule a name. Click the "Add" button in the "Rule Actions" section. Finally, select the option "Invoke a Burp extension."
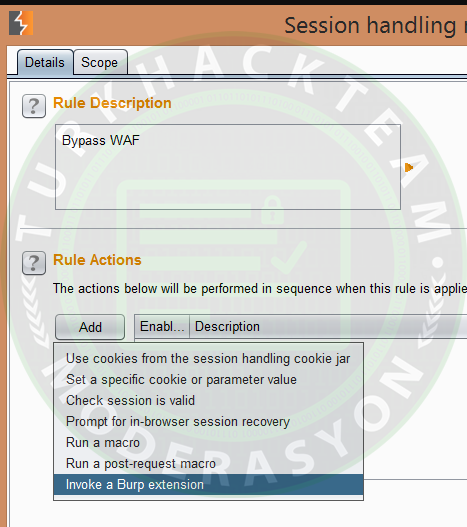
As you can see below, you need to choose the "Bypass WAF" option from the dropdown menu:

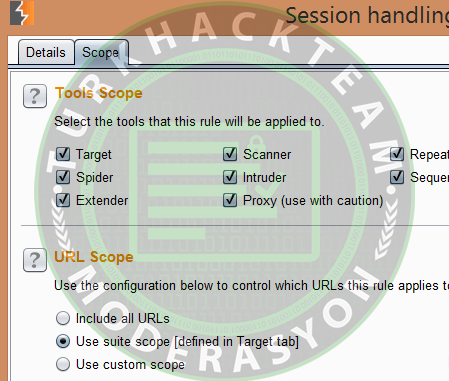
In this step, you need to click the "Ok" button and select the "Scope" tab. Now, you can enable all the tools you want to be in scope for the extension and then adjust the scope. Enable all tools and limit the scope to those added to the suite, as shown below:
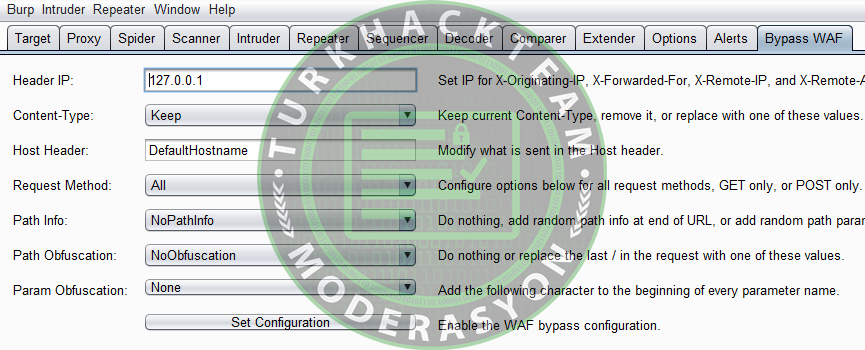
Bypass WAF includes the following features:
Conclusion
In this discussion, Bypass WAF was introduced, and you learned how to install Bypass WAF on Burp Suite.
Thank you for reading this post.
Source : https://www.turkhackteam.org/konular/burp-suitete-wafi-atlamanin-kurulumu-nasil-yapilir.2048865/
Let's explore WAF bypass techniques using HTTP standards and the behavior of web servers. In this section, you'll learn a creative array of techniques for evading and reshaping HTTP requests by exploiting peculiar behaviors of web servers and features such as request encoding or HTTP pipelining. These methods demonstrate that developers should not rely solely on WAFs as a defense mechanism, but when can you employ these techniques?
1- As a penetration testing expert, you can use this to test a website behind a WAF, avoiding drama and pain.
2- Defense teams can utilize this method to design appropriate measures.
Bypassing Some WAF Devices Using Burp Extension
Download and compile the Python version, Java version, or Java source of the extension. Then, use this extension to add the necessary headers. After installing the extension, follow these steps:
1- Launch Burp.
2- Go to the "Extender >> Extensions" section.
3- Click the "Add" button.
4- Select the extension type as "Java."
Note: If you are using the Java Extension, choose the "Java" extension type. If you are using the Python version, select the "Python" extension type, and then navigate to the extension path.

The extension will be added as shown below:

To proceed, follow the steps below:
1- Go to the "Options >> Sessions" section.
2- Click the "Add" button for "Session Handling Rules."

In the next step, you need to give the rule a name. Click the "Add" button in the "Rule Actions" section. Finally, select the option "Invoke a Burp extension."

As you can see below, you need to choose the "Bypass WAF" option from the dropdown menu:

In this step, you need to click the "Ok" button and select the "Scope" tab. Now, you can enable all the tools you want to be in scope for the extension and then adjust the scope. Enable all tools and limit the scope to those added to the suite, as shown below:

Bypass WAF includes the following features:

Conclusion
In this discussion, Bypass WAF was introduced, and you learned how to install Bypass WAF on Burp Suite.
Thank you for reading this post.
Source : https://www.turkhackteam.org/konular/burp-suitete-wafi-atlamanin-kurulumu-nasil-yapilir.2048865/





