- 7 Tem 2013
- 8,194
- 655

What is Krack Vulnerability and How Does It Work?

Krack (Key Reinstallation Attacks method) In this vulnerability, networks using the WPA2 protocol will be targeted for attack. The biggest feature of this attack is that the attacker can sniff traffic analysis without connecting to the target network system. Creates a fake network that has the same SSID as the wireless network that the attacker wants to attack and runs on a different channel. When the victim wants to connect to the real network, the packets sent by the attacker are connected to the fake network due to the CSA beacon method. After that, the encryption key is changed using the pass vulnerability.
Visual Analysis
Victim Sends Request To Real AP

The attacker performs a CSA Beacon Injection attack

As a result of the CSA Beacon Injection attack, the victim is redirected to the Fake AP.

Target Network Vulnerability Tests

The creator of vulnerability is a programmer named Mathy Vanhoef.
He published it to understand whether the network connection with the published script received an attack or was available for attack.
Script Address: Github
Key Reinstallation Attacks

The test that you'll see is currently tested on the TP-LINK TL-wn722n/Ubuntu 14.04 system.
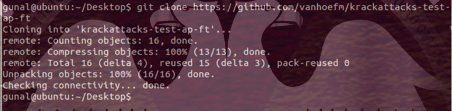
Kod:
git cloneBefore the test, it's necessary to turn off the system's Wi-fi function with a short command.
The script should be able to use this feature.
For this, let's type the command:
Kod:
sudo rfkill unblock wifilater, hardware encryption is disabled with the "disable-hwcrypto.sh" command.

When our system is opened after the restart, we'll prepare a configuration file to connect to the target network using the wpa_supplicant command.

SSID: name of the publication to be tested
Key_Mgmt: this section should be FT-PSK because the Fast Transaction feature will be tested.
PSK: broadcast password
Kod:
sudo wpa_supplicant -D nl80211 -i wlan0 -c network.confwe can select the driver with the -d command. and with the the-i command, we can select the wireless broadcast card. we select the configuration file that is prepared with the -c command.
this is important! if there is an error-free connection here, we can move on to other steps. If there is a connection problem, we'll understand that the network doesn't support the fast transaction.
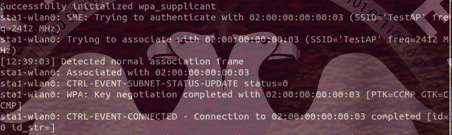
If there is a certain link, "wpa_supplicant -krack-ft-test.py" the command is executed. A virtual monitor is created to observe the test.
Kod:
sudo ./krack-ft-test.py wpa_supplicant -D nl80211 -i wlan0 -c network.conf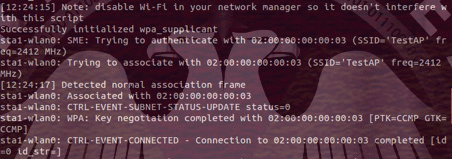
Kod:
sudo wpa_cli -i wlan0After connecting with Wpa_cli, you can switch to a different AP on the same network.
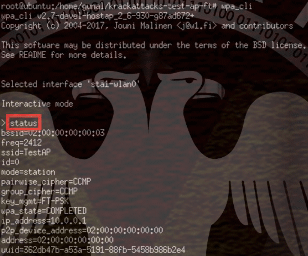
with the the-i command, we can select the network card
Kod:
scan_resultsyou can see if there are any other AP scanned with the scan_results command
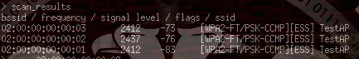
when a successful connection is created, the terminal will list all vulnerabilities in the wireless network.
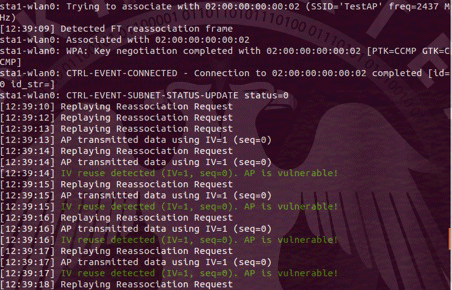
Attack Determination
- By detecting Fake APS.
- If the keys only have a value of 0.
- If nonce values are repeated
Source: https://www.turkhackteam.org/network/1830669-wpa2-protokolune-saldiri-kurulum-inceleme.html
Translator Gauloran





