Greetings, in our C secure coding series, we will discuss the format string vulnerability, which is one of the known vulnerabilities in the exploit development community, and examine the vulnerability through sample applications. First of all, let's understand the concept of format string through examples.
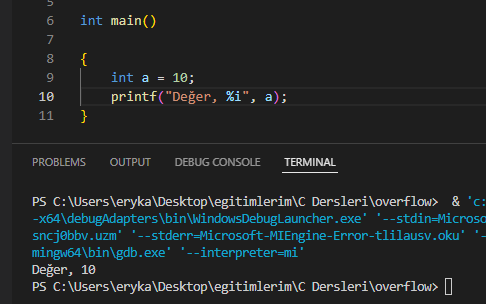
Now what is going on in this code? Variable A holds an integer value. We will print this value to the screen with the printf method, and we print this value by specifying its format, and we do this with the value %i, which is the format specifier here. In other words, we ensure that the format of the value to be presented as output is integer. In other words, our style specifiers here provide the desired interpretation of the binary data in the memory. We can understand this more clearly with the following example.
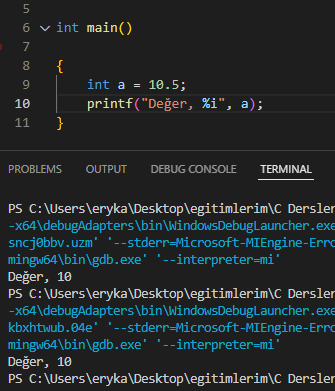
Look, our variable catches the value 10.5, but we print it in integer format and it prints the full part of the number.
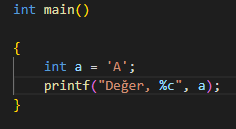
Now I changed the code like this, what do you think it will output? We have a variable of type Int and it holds a character in it. Then we format the variable with a character and print it on the screen.
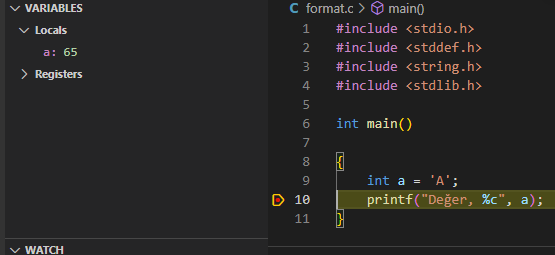
Now I stop the value with breakpoint without printing it to the screen and see its value in memory. There is an integer variable holding the string 'A' and the value it holds is the decimal equivalent of the letter A. Then I format it with %c, so I say I want to see it in character format.
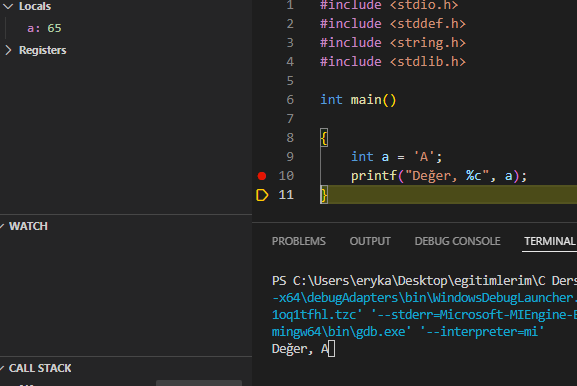
I say step over and process the next line, and as a result, I can see the character formatted version of the relevant decimal value. You can query such examples by applying them yourself. I wanted to exemplify the format string event without mentioning the format string weakness. Finally, let's examine the printf method here.
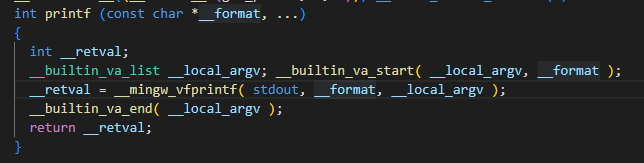
Our printf function under the stdio.h library takes the string to be sent to stdout in its first parameter, and then takes the optionally formatted values.
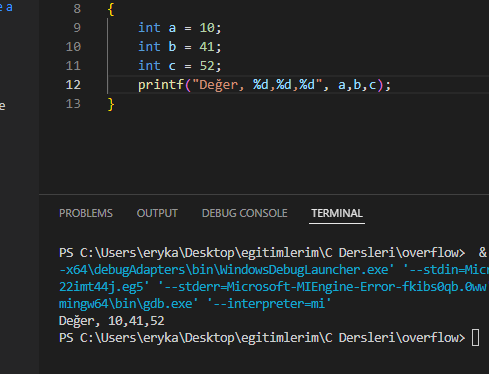
So we can see it this way.
Abusing Format Strings
In fact, at the end of the day, we come to the subject that we will talk about as weakness. We will see how this format specifier, which we call format specifiers, can be used as an exploitation technique in a possible vulnerability. Let's just get into the basics.
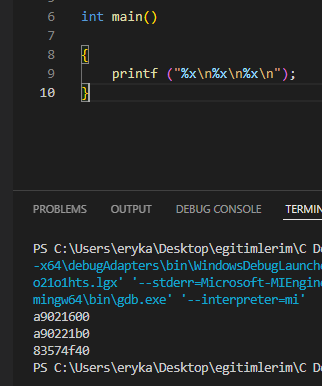
Now I gave a very simple example. Look, there is no variable, there is no value to be output, but I print the %x token three times with printf and I see three addresses on the screen. Here, %x gives us hexadecimal values. So it read and wrote three values from the stack. So, something popped up in your mind? Well, since we can read the value, in case of a possible vulnerability, let's squeeze this token in and take advantage of it, it would be nice, right?
I took this example directly from Format One :: Andrew Griffiths' Exploit Education here. It's an example that you can basically understand.
You know, I just said %x, a style specifier for reading data from memory, which in this example points out exactly that.
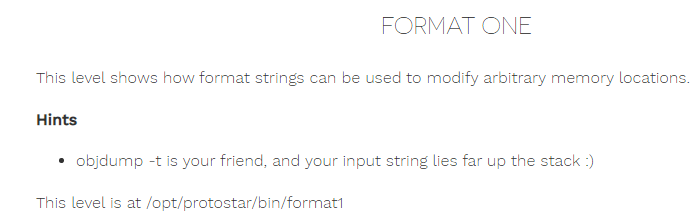
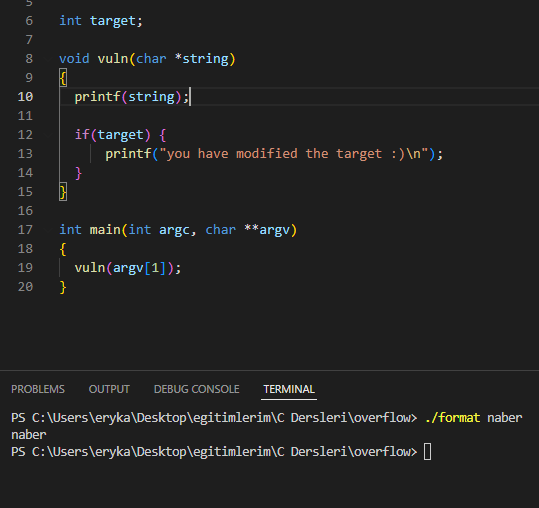
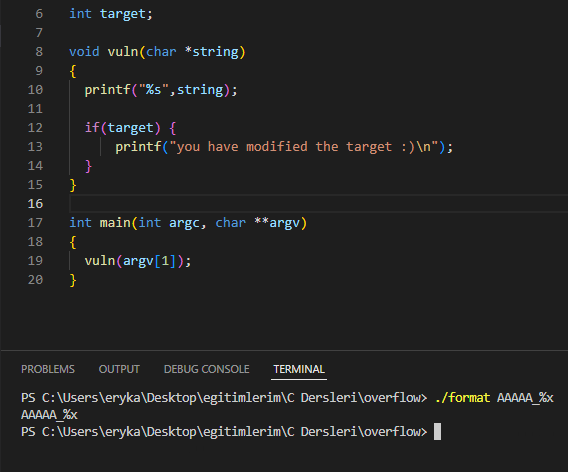
Here you read the description and hint part. The explanation is different from what I said above. In the hint part, it says objdump is your aide. Here, let me first explain the source code to you and find the point of vulnerability. A variable called int target takes up space in the defined stack, but it doesn't work, it takes up space. Then the vuln function is a function that does not return a void value and expects a char value as an argument. It also prints the argument that comes to it with printf. Then it checks the value of the target variable and gives a message that you have modified it. In the main function, the vuln function is called and an argument is given. In short, when you run the program by giving an argument, the vuln function in main will be triggered and it will execute the printf method and perform the task of printing to the screen.
Now, if you pay attention here, printf prints the incoming argument directly and a format specifier is not used in any way. At this point, we are in a situation where we can perform operations by adding a specifier. Because it will take it as an argument and process it. At this point, the format string vulnerability occurs.
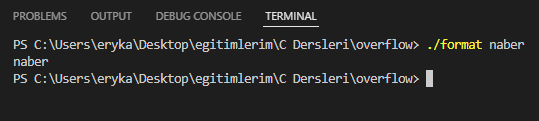
It properly takes the argument and prints it to the screen.
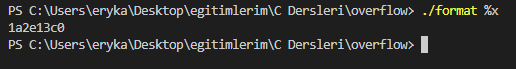
But it prints this too. So, at this point, we have identified the vulnerability. So we abuse it by taking advantage of the format specifier.
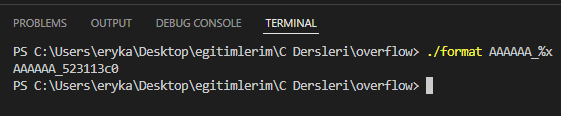
We can exemplify like this. So what happened, we're back to the printf(%x) example I mentioned in abuse. This program is currently doing just that.
After that, if we obtain the value of the relevant target variable in memory with objdump and write the value we want to this value with the %n token, we will have modified the target variable and exploited the vulnerability.
In this way, we specify the type of our output as a string with printf and we write safe code.
The point is to trust and control input from the user. Sounds like an XSS vulnerability, right? Output encoding or something? Thanks you for reading.
Thanks you for reading.
Original Article: https://www.turkhackteam.org/konular/c-guvenli-kod-gelistirme-format-string-zafiyeti.2015852/
Translator and editor: @Dolyetyus
Down below is a video of this article but the language is Turkish, unfortunately there is no English subtitles but you can still watch it.

Now what is going on in this code? Variable A holds an integer value. We will print this value to the screen with the printf method, and we print this value by specifying its format, and we do this with the value %i, which is the format specifier here. In other words, we ensure that the format of the value to be presented as output is integer. In other words, our style specifiers here provide the desired interpretation of the binary data in the memory. We can understand this more clearly with the following example.

Look, our variable catches the value 10.5, but we print it in integer format and it prints the full part of the number.

Now I changed the code like this, what do you think it will output? We have a variable of type Int and it holds a character in it. Then we format the variable with a character and print it on the screen.

Now I stop the value with breakpoint without printing it to the screen and see its value in memory. There is an integer variable holding the string 'A' and the value it holds is the decimal equivalent of the letter A. Then I format it with %c, so I say I want to see it in character format.

I say step over and process the next line, and as a result, I can see the character formatted version of the relevant decimal value. You can query such examples by applying them yourself. I wanted to exemplify the format string event without mentioning the format string weakness. Finally, let's examine the printf method here.

Our printf function under the stdio.h library takes the string to be sent to stdout in its first parameter, and then takes the optionally formatted values.

So we can see it this way.
Abusing Format Strings
In fact, at the end of the day, we come to the subject that we will talk about as weakness. We will see how this format specifier, which we call format specifiers, can be used as an exploitation technique in a possible vulnerability. Let's just get into the basics.

Now I gave a very simple example. Look, there is no variable, there is no value to be output, but I print the %x token three times with printf and I see three addresses on the screen. Here, %x gives us hexadecimal values. So it read and wrote three values from the stack. So, something popped up in your mind? Well, since we can read the value, in case of a possible vulnerability, let's squeeze this token in and take advantage of it, it would be nice, right?

I took this example directly from Format One :: Andrew Griffiths' Exploit Education here. It's an example that you can basically understand.
You know, I just said %x, a style specifier for reading data from memory, which in this example points out exactly that.

Here you read the description and hint part. The explanation is different from what I said above. In the hint part, it says objdump is your aide. Here, let me first explain the source code to you and find the point of vulnerability. A variable called int target takes up space in the defined stack, but it doesn't work, it takes up space. Then the vuln function is a function that does not return a void value and expects a char value as an argument. It also prints the argument that comes to it with printf. Then it checks the value of the target variable and gives a message that you have modified it. In the main function, the vuln function is called and an argument is given. In short, when you run the program by giving an argument, the vuln function in main will be triggered and it will execute the printf method and perform the task of printing to the screen.
Now, if you pay attention here, printf prints the incoming argument directly and a format specifier is not used in any way. At this point, we are in a situation where we can perform operations by adding a specifier. Because it will take it as an argument and process it. At this point, the format string vulnerability occurs.

It properly takes the argument and prints it to the screen.

But it prints this too. So, at this point, we have identified the vulnerability. So we abuse it by taking advantage of the format specifier.

We can exemplify like this. So what happened, we're back to the printf(%x) example I mentioned in abuse. This program is currently doing just that.
After that, if we obtain the value of the relevant target variable in memory with objdump and write the value we want to this value with the %n token, we will have modified the target variable and exploited the vulnerability.

In this way, we specify the type of our output as a string with printf and we write safe code.
The point is to trust and control input from the user. Sounds like an XSS vulnerability, right? Output encoding or something?
Original Article: https://www.turkhackteam.org/konular/c-guvenli-kod-gelistirme-format-string-zafiyeti.2015852/
Translator and editor: @Dolyetyus
Down below is a video of this article but the language is Turkish, unfortunately there is no English subtitles but you can still watch it.
Moderatör tarafında düzenlendi:







