What is Cyber Espionage?
Cyber spying is the act of engaging in an attack or series of attacks that let an unauthorized user or users view classified material. These attacks are often subtle, amounting to nothing more than an unnoticed bit of code or process running in the background of a mainframe or personal workstation, and the target is usually a corporate or government entity.
The goal is typically to acquire intellectual property or government secrets. Attacks can be motivated by greed or profit, and can be used in conjunction with a military operation or as an act of terrorism. Consequences can range from loss of competitive advantage to loss of materials, data, infrastructure, or loss of life.


Popular Spying Tactics
For years, corporations have attempted to seek advantages by prying into the business plans of their competitors. One tactic is to send in faux employees who attempt to gain access to data or projects where new technology is being developed. Technology provided an evolutionary path for this activity, and resulted in the birth of cyber spying.
The faux employee is still a useful tactic, but now an unsecured workstation is far more attractive. An individual can use a USB stick to upload a worm or virus in a matter of seconds. The goal might be to identify and open a security portal or find an exploit that can be targeted at a later date.
Business websites can offer the same type of openings, and experienced hackers can use a vulnerable website to execute an attack. Emails that appear to be official may be sent to specific individuals with higher network privileges who could be lured into clicking a link that downloads code to enable later attacks. This type of attack is called spear phishing.
Modern browser software is comprised of thousands of lines of code. New lines of code add new features as the software evolves. Sometimes new code, by chance or oversight (or lack thereof) breaks little-known features or works at-odds with security patches that have previously been effective. When a new feature or a new piece of software hits the market, its analyzed, dissected, and backward-engineered by countless individuals and interested parties around the world.

What is Spyware?
Spyware is a term used to describe a program designed to gather information about a user's activity secretly. Spyware programs are often used to track users' habits to target them with advertisements better. Spyware is usually installed on a user's machine without their knowledge after clicking a link (intentionally or unintentionally) that redirects the user to a malicious website.
How Spyware Works?
Once the spyware is installed on the user's computer, it monitors all the user's activities, collects all relevant information such as the user's surfing habits, and transmits it to a third party over the Internet. It's often seen that spyware changes important system settings to remain undetected for as long as possible. Also, the browser's settings are adjusted so often that each time the browser is opened the user is redirected to a specific website. Other possibilities of spyware are display of banner ads, analysis of mail traffic and much more. Because the spyware runs constantly in the background, it uses up valuable system resources of the infected computer.
How do I protect myself from spyware?
The best defense against spyware, as with most malware, starts with your behavior. Follow these basics of good cyber self-defense.
- Dont open emails from unknown senders.
- Dont download files unless they come from a trusted source.
- Mouse-over links before clicking on them and make sure youre being sent to the right webpage.
- Use a reputable cybersecurity program to counter advanced spyware. In particular, look for cybersecurity that includes real-time protection.
How do I know if I have spyware?
Unless something is noticeably different, the only method of detecting spyware on a computer, phone, or tablet would be to have an anti-spyware or anti-malware detection tool.


Malwarebytes Usage
First, download it from this link:
Download
You'll see this. Clicking on 'Agree and Install' will be enough to continue.
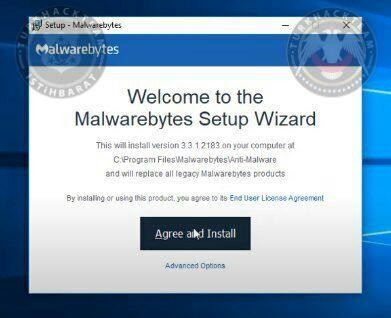
Then we need to wait a lil bit to install it.
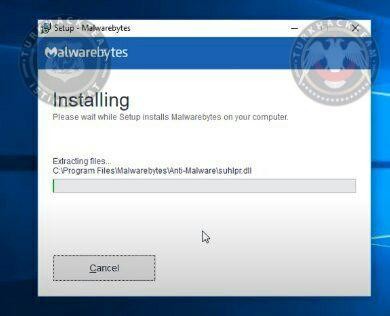
Click 'Scan Now' after it's done.
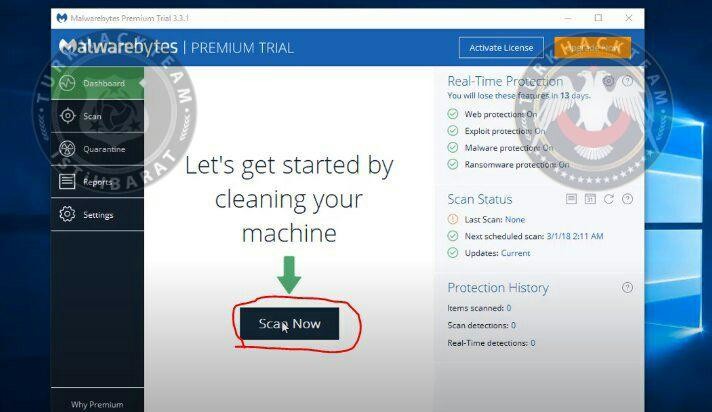
Wait till it's done as well.
You can remove all malicious softwares from your computer after scanning is done.

Preventing Cyber Espionage
Cyber espionage has no longer been restricted to financial or government institutions, it has deepened its roots in telecommunication industry, companies, hotels etc. The motive of stealing information has changed to damaging the reputation and entire structure of an organization. In case of government and military operations, such cyber-espionage attacks can even result in terrorist attacks endangering the lives of innocent. There are many ways to prevent such attacks, but there is no guarantee that all the attacks would be eliminated. As the saying goes Prevention is better than cure, lets see some of the preventive measures that can be taken in order to a**** cyber espionage attacks:
- Defining security policies and assessing the existing ones enables organizations to be vulnerable against cyber attacks. The organizations should also strive to have a proactive response plan in case such an attack is detected.
- Security measures such as backups and updates should be followed up and audited on a regular basis.
- Knowledge is very important in todays digital era, organizations should educate and train their employees about security policies that minimizes the acts of cyber espionage. Best practices should be followed such as changing passwords at regular intervals, keeping classified information secured and using approved antivirus and malware protection.
As cyber espionage deepens its roots in todays globally connected environment, cybersecurity increases and evolves and the need for automation tools and techniques will become an integral part of an organizations cyber-espionage policies. Organizations should employ automation tools to correlate data, generate policies faster than attacks and implement strategies at a quicker pace to minimize the risk of cyber espionage.


Cyber Espionage Attack Examples
1. Gillette Industrial Espionage
In 1997, a man from Washington, Iowa was charged with wire fraud and theft of trade secrets from Gillette. Steven L. Davis, then 47-years-old, stole information concerning a new shaving system the had been developed by the company. He was a previous employee of Wright Industries Inc. who had been commissioned by Gillette to help design the fabricator equipment for the new shaving system. Davis pleaded guilty and was charged for his part in the espionage and faced a total of 15 years in prison and hundreds of thousands of dollars in fines.
2. GhostNet
Researchers in Canada announced in 2009 that they had been tracking a vast and sustained cyber attack they called Ghostnet for the past 10 months. Ghostnet was one of the largest hacks uncovered in terms of its geographic reach, infiltrating 1,295 computers in 103 countries, targeting computers belonging to foreign ministries and embassies and those linked with the Tibetan spiritual leader, the Dalai Lama.
While they traced Ghostnet mainly to computers in China, the researchers at Information Warfare Monitor made no direct link to the government and Beijing denied involvement.
Cyber spying is the act of engaging in an attack or series of attacks that let an unauthorized user or users view classified material. These attacks are often subtle, amounting to nothing more than an unnoticed bit of code or process running in the background of a mainframe or personal workstation, and the target is usually a corporate or government entity.
The goal is typically to acquire intellectual property or government secrets. Attacks can be motivated by greed or profit, and can be used in conjunction with a military operation or as an act of terrorism. Consequences can range from loss of competitive advantage to loss of materials, data, infrastructure, or loss of life.


Popular Spying Tactics
For years, corporations have attempted to seek advantages by prying into the business plans of their competitors. One tactic is to send in faux employees who attempt to gain access to data or projects where new technology is being developed. Technology provided an evolutionary path for this activity, and resulted in the birth of cyber spying.
The faux employee is still a useful tactic, but now an unsecured workstation is far more attractive. An individual can use a USB stick to upload a worm or virus in a matter of seconds. The goal might be to identify and open a security portal or find an exploit that can be targeted at a later date.
Business websites can offer the same type of openings, and experienced hackers can use a vulnerable website to execute an attack. Emails that appear to be official may be sent to specific individuals with higher network privileges who could be lured into clicking a link that downloads code to enable later attacks. This type of attack is called spear phishing.
Modern browser software is comprised of thousands of lines of code. New lines of code add new features as the software evolves. Sometimes new code, by chance or oversight (or lack thereof) breaks little-known features or works at-odds with security patches that have previously been effective. When a new feature or a new piece of software hits the market, its analyzed, dissected, and backward-engineered by countless individuals and interested parties around the world.


What is Spyware?
Spyware is a term used to describe a program designed to gather information about a user's activity secretly. Spyware programs are often used to track users' habits to target them with advertisements better. Spyware is usually installed on a user's machine without their knowledge after clicking a link (intentionally or unintentionally) that redirects the user to a malicious website.
How Spyware Works?
Once the spyware is installed on the user's computer, it monitors all the user's activities, collects all relevant information such as the user's surfing habits, and transmits it to a third party over the Internet. It's often seen that spyware changes important system settings to remain undetected for as long as possible. Also, the browser's settings are adjusted so often that each time the browser is opened the user is redirected to a specific website. Other possibilities of spyware are display of banner ads, analysis of mail traffic and much more. Because the spyware runs constantly in the background, it uses up valuable system resources of the infected computer.
How do I protect myself from spyware?
The best defense against spyware, as with most malware, starts with your behavior. Follow these basics of good cyber self-defense.
- Dont open emails from unknown senders.
- Dont download files unless they come from a trusted source.
- Mouse-over links before clicking on them and make sure youre being sent to the right webpage.
- Use a reputable cybersecurity program to counter advanced spyware. In particular, look for cybersecurity that includes real-time protection.
How do I know if I have spyware?
Unless something is noticeably different, the only method of detecting spyware on a computer, phone, or tablet would be to have an anti-spyware or anti-malware detection tool.


Malwarebytes Usage
First, download it from this link:
Download
You'll see this. Clicking on 'Agree and Install' will be enough to continue.

Then we need to wait a lil bit to install it.

Click 'Scan Now' after it's done.

Wait till it's done as well.

You can remove all malicious softwares from your computer after scanning is done.


Preventing Cyber Espionage
Cyber espionage has no longer been restricted to financial or government institutions, it has deepened its roots in telecommunication industry, companies, hotels etc. The motive of stealing information has changed to damaging the reputation and entire structure of an organization. In case of government and military operations, such cyber-espionage attacks can even result in terrorist attacks endangering the lives of innocent. There are many ways to prevent such attacks, but there is no guarantee that all the attacks would be eliminated. As the saying goes Prevention is better than cure, lets see some of the preventive measures that can be taken in order to a**** cyber espionage attacks:
- Defining security policies and assessing the existing ones enables organizations to be vulnerable against cyber attacks. The organizations should also strive to have a proactive response plan in case such an attack is detected.
- Security measures such as backups and updates should be followed up and audited on a regular basis.
- Knowledge is very important in todays digital era, organizations should educate and train their employees about security policies that minimizes the acts of cyber espionage. Best practices should be followed such as changing passwords at regular intervals, keeping classified information secured and using approved antivirus and malware protection.
As cyber espionage deepens its roots in todays globally connected environment, cybersecurity increases and evolves and the need for automation tools and techniques will become an integral part of an organizations cyber-espionage policies. Organizations should employ automation tools to correlate data, generate policies faster than attacks and implement strategies at a quicker pace to minimize the risk of cyber espionage.


Cyber Espionage Attack Examples
1. Gillette Industrial Espionage
In 1997, a man from Washington, Iowa was charged with wire fraud and theft of trade secrets from Gillette. Steven L. Davis, then 47-years-old, stole information concerning a new shaving system the had been developed by the company. He was a previous employee of Wright Industries Inc. who had been commissioned by Gillette to help design the fabricator equipment for the new shaving system. Davis pleaded guilty and was charged for his part in the espionage and faced a total of 15 years in prison and hundreds of thousands of dollars in fines.
2. GhostNet
Researchers in Canada announced in 2009 that they had been tracking a vast and sustained cyber attack they called Ghostnet for the past 10 months. Ghostnet was one of the largest hacks uncovered in terms of its geographic reach, infiltrating 1,295 computers in 103 countries, targeting computers belonging to foreign ministries and embassies and those linked with the Tibetan spiritual leader, the Dalai Lama.
While they traced Ghostnet mainly to computers in China, the researchers at Information Warfare Monitor made no direct link to the government and Beijing denied involvement.
Source: https://www.turkhackteam.org/sosyal-muhendislik/1917021-siber-espiyonaj-ve-kullanilan-teknikler.html
Translator: R4V3N
Moderatör tarafında düzenlendi:





