- 10 Eyl 2015
- 689
- 0
Hello, multicolored-hat hackers!
Today I am going to show you how to use the wordlists that come preinstalled with Kali Linux to crack those annoying hashes that contain our passwords. I'm sure that at some point in all of your lives, you have attempted to crack a password by trying multiple words or numbers that may be the owners password. What you may not know is that this method of hacking has a name: Dictionary attack. This article from OTW contains some information as to what a dictionary attack is and what other methods exist for password cracking. This type of hacking is done with wordlists which, as the name states: list words. These words are common passwords that can be personalized for the target to increase the chance of getting it right. On hacking forums and such, you'll find people telling you to download wordlists from the internet to use in a dictionary attack. However, if you use Kali Linux (if you don't, you should really look into it if you plan on becoming a hacker), there are some wordlists that can be found in the Linux distribution. Of course, this isn't meant to discourage you from downloading other wordlists from the Internet, for all you know a wordlist on the internet contains your magic word. Still, working through the provided wordlists will at least help you rule some out. So let's get to it!
Step 1: Get Your Hashes
If you're a newbie, you may be wondering: what's a hash? A hash is a password that has gone through a certain algorithm that encrypts the password behind a multitude of numbers and letters so that it can be stored but not seen by users. While there are many types of algorithms with different outcomes including MD5, SHA-1, SQL, etc., for the purpose of this How-to and the script I provide to you, we will be using and MD5 hash. This hash can be obtained multiple ways but, I got mine through a blind SQL Injection attack. This article from Th3 skY f0x explains what I did well. Once going through a websites database, you may find something like this:
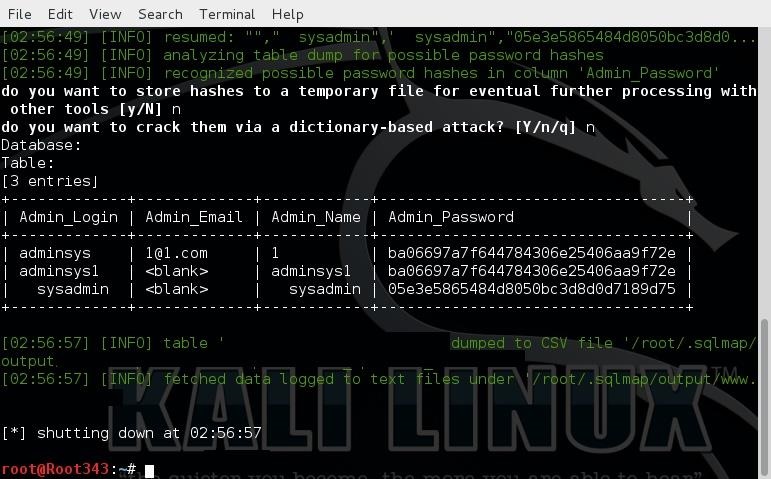
By using your common sense, you will see that there is a column under the name 'Admin_Password'. Again, using your common sense, you'll find that under it are a bunch of random letters and numbers and you'll think, "Hey, Papa Root343 prepared me for this! Then you'll say 'those look like hashes!'" Now identify that hash type by going to your terminal and typing:
hash-identifier
You should receive a prompt, that asks you for the hash. Copy the hash from the database and paste it into this prompt. The program should tell you the most probable hash type the input was.
Step 2: Find Where to Put the Hash Once You've Cracked It
In order to not waste our time, we must make sure that once we've cracked this hash, that there is somewhere to put in the password. Assuming that place is a website, this perl script from Tartou2 will find the admin panel of that website if there is one. Just copy and paste the raw data from the paste bin if you don't feel like downloading it. Once you have it on your Kali desktop or wherever you put it, make sure to give it a .pl extension and that it has permission to run. You can ensure this by typing:
chmod 755 "Whatever you named the script.sh"
Then, just start the script and give it any information it asks you for. If nothing is found, the hash might have been set up as a decoy and is useless. Find another target or look for a different hash and come back.
Step 3: Crack That Hash
Now that you have a target and a hash, we must crack it to reveal its contents. A good offline, and non-CPU or GPU intensive program that cracks hashes is Hashcat, which of course, can be found in Kali Linux. This program allows you to input both a hash list (containing the hashes) and a wordlist (containing the possible passwords), then compares the hashed forms of the words in the wordlist to the hashes in the hash list to see if there are any matches. The important part is the wordlist. If you have a good wordlist, the chances of you finding the match increases. Going back to the Kali installed wordlist, I have created a BASH script that uses hashcat and automates this process with all the wordlists found in Kali; a process that would normally take really long. This script, dubbed The Hash Slinging Slasher (pretty cool name right? I know it is), can be found here. Like the other script, make sure it has permission to run by tyoing in the same command as before with the proper name, but MAKE SURE YOU GIVE THIS SCRIPT A .sh EXTENSION, NOT A .pl ONE! All I ask is that you tell me what you think about the script and that you don't copy and paste it after changing the name and call it your own creation. Start it like this:
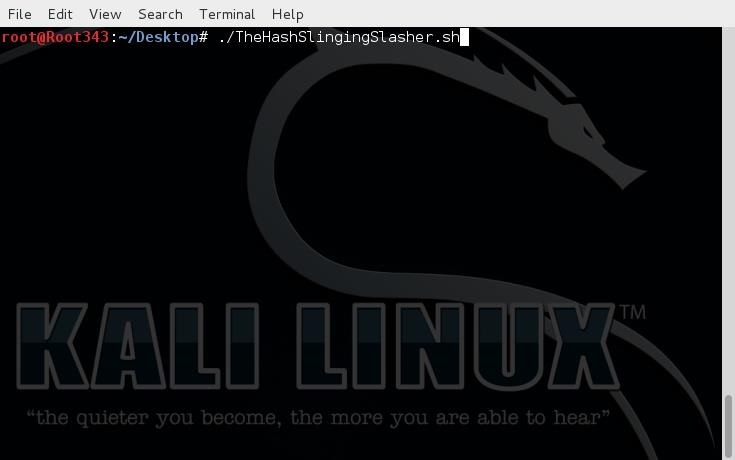
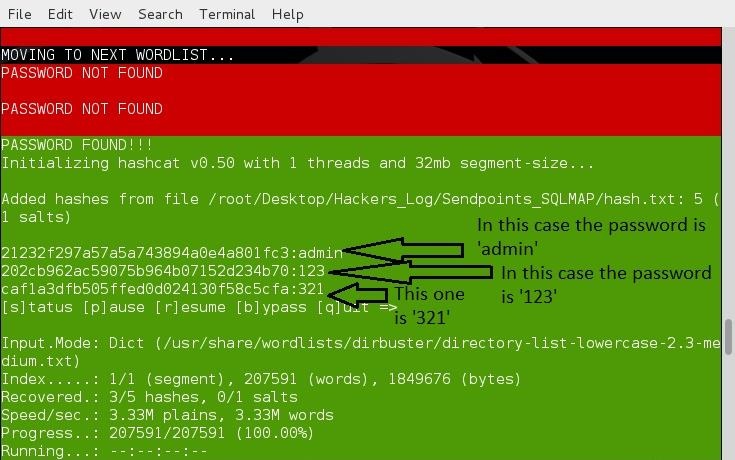
Copy and paste your hash into a text file and then find its ********. By ******** I mean 'root/Desktop/hash.txt' or however and wherever you saved it. For the moment, the script can only try to crack 5 MD5 hashes at a time, so if you try to run more than 5 hashes at a time or try to crack a SHA-1 hash, THE SCRIPT WILL NOT WORK. After putting in the ******** of the hash file, the script will do the rest. Just look for the green highlight and you will see the password. Once the program is done, look for this:
Step 4: Punch That Password In
There! You're all set. Go put that password in along with the username that was stated in the database (See Step 1 ) and you should be in.
Source: How to Crack MD5 Hashes with All of Kali Linux's Default Wordlists « Null Byte
Today I am going to show you how to use the wordlists that come preinstalled with Kali Linux to crack those annoying hashes that contain our passwords. I'm sure that at some point in all of your lives, you have attempted to crack a password by trying multiple words or numbers that may be the owners password. What you may not know is that this method of hacking has a name: Dictionary attack. This article from OTW contains some information as to what a dictionary attack is and what other methods exist for password cracking. This type of hacking is done with wordlists which, as the name states: list words. These words are common passwords that can be personalized for the target to increase the chance of getting it right. On hacking forums and such, you'll find people telling you to download wordlists from the internet to use in a dictionary attack. However, if you use Kali Linux (if you don't, you should really look into it if you plan on becoming a hacker), there are some wordlists that can be found in the Linux distribution. Of course, this isn't meant to discourage you from downloading other wordlists from the Internet, for all you know a wordlist on the internet contains your magic word. Still, working through the provided wordlists will at least help you rule some out. So let's get to it!
Step 1: Get Your Hashes
If you're a newbie, you may be wondering: what's a hash? A hash is a password that has gone through a certain algorithm that encrypts the password behind a multitude of numbers and letters so that it can be stored but not seen by users. While there are many types of algorithms with different outcomes including MD5, SHA-1, SQL, etc., for the purpose of this How-to and the script I provide to you, we will be using and MD5 hash. This hash can be obtained multiple ways but, I got mine through a blind SQL Injection attack. This article from Th3 skY f0x explains what I did well. Once going through a websites database, you may find something like this:

By using your common sense, you will see that there is a column under the name 'Admin_Password'. Again, using your common sense, you'll find that under it are a bunch of random letters and numbers and you'll think, "Hey, Papa Root343 prepared me for this! Then you'll say 'those look like hashes!'" Now identify that hash type by going to your terminal and typing:
hash-identifier
You should receive a prompt, that asks you for the hash. Copy the hash from the database and paste it into this prompt. The program should tell you the most probable hash type the input was.
Step 2: Find Where to Put the Hash Once You've Cracked It
In order to not waste our time, we must make sure that once we've cracked this hash, that there is somewhere to put in the password. Assuming that place is a website, this perl script from Tartou2 will find the admin panel of that website if there is one. Just copy and paste the raw data from the paste bin if you don't feel like downloading it. Once you have it on your Kali desktop or wherever you put it, make sure to give it a .pl extension and that it has permission to run. You can ensure this by typing:
chmod 755 "Whatever you named the script.sh"
Then, just start the script and give it any information it asks you for. If nothing is found, the hash might have been set up as a decoy and is useless. Find another target or look for a different hash and come back.
Step 3: Crack That Hash
Now that you have a target and a hash, we must crack it to reveal its contents. A good offline, and non-CPU or GPU intensive program that cracks hashes is Hashcat, which of course, can be found in Kali Linux. This program allows you to input both a hash list (containing the hashes) and a wordlist (containing the possible passwords), then compares the hashed forms of the words in the wordlist to the hashes in the hash list to see if there are any matches. The important part is the wordlist. If you have a good wordlist, the chances of you finding the match increases. Going back to the Kali installed wordlist, I have created a BASH script that uses hashcat and automates this process with all the wordlists found in Kali; a process that would normally take really long. This script, dubbed The Hash Slinging Slasher (pretty cool name right? I know it is), can be found here. Like the other script, make sure it has permission to run by tyoing in the same command as before with the proper name, but MAKE SURE YOU GIVE THIS SCRIPT A .sh EXTENSION, NOT A .pl ONE! All I ask is that you tell me what you think about the script and that you don't copy and paste it after changing the name and call it your own creation. Start it like this:

Copy and paste your hash into a text file and then find its ********. By ******** I mean 'root/Desktop/hash.txt' or however and wherever you saved it. For the moment, the script can only try to crack 5 MD5 hashes at a time, so if you try to run more than 5 hashes at a time or try to crack a SHA-1 hash, THE SCRIPT WILL NOT WORK. After putting in the ******** of the hash file, the script will do the rest. Just look for the green highlight and you will see the password. Once the program is done, look for this:

Step 4: Punch That Password In
There! You're all set. Go put that password in along with the username that was stated in the database (See Step 1 ) and you should be in.
Source: How to Crack MD5 Hashes with All of Kali Linux's Default Wordlists « Null Byte






