Hi.
Step 1 Fire Up Kali & Open Hashcat
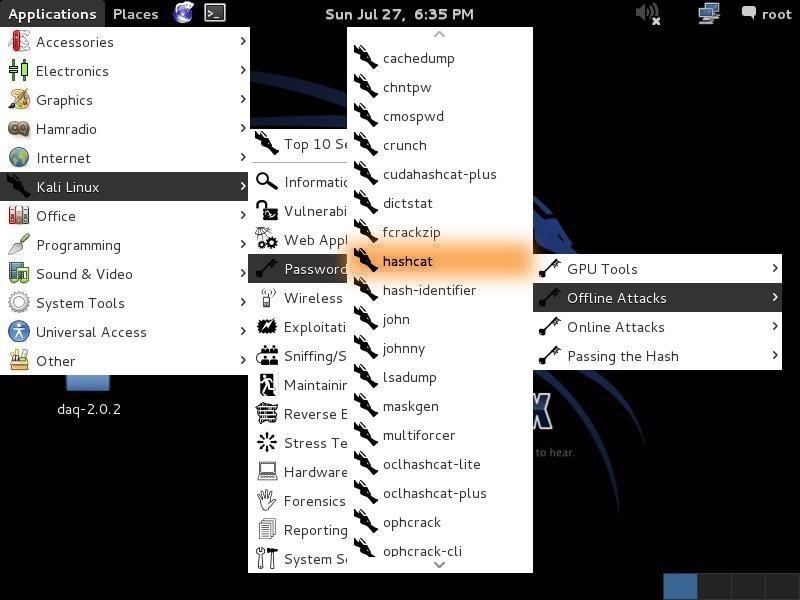
Let's start by firing up Kali and opening hashcat. Go to Applications -> Kali Linux -> Password Attacks -> Offline Attacks -> hashcat, as seen below.
When we click on the hashcat menu item, it opens the help screen.
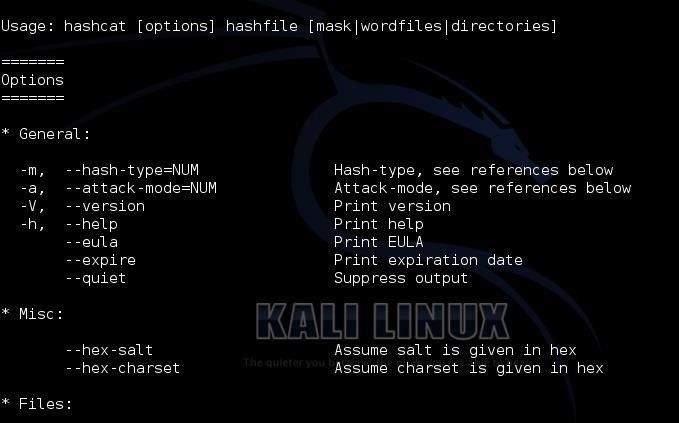
At the top of the screen, you can see the basic hashcat syntax:
We can see some of the options for hashcat displayed below the basic syntax. Some of the most important of these are -m (the hashtype) and -a (attack mode). In general, we will need to use both of these options in most password cracking attempts with hashcat.
Step 2 More Extensive Options
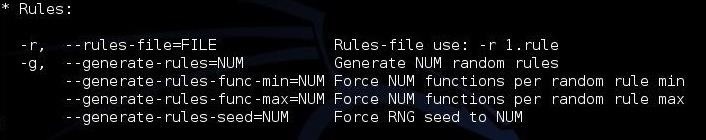
If we scan a bit further down this hashcat help screen, we can see more options. The first two below are some of the key options that hashcat enables.
First, hashcat enables rules that allow us to apply specifically designed rules to use on our wordlist file. These rules can take our wordlist file and apply capitalization rules, special characters, word combinations, appended and prepended numbers, and so on. Each of these will help us to break passwords that have been made more complex to a**** dictionary attacks.
The next stanza shows us custom character sets. This enables us to set the character set that we want to use to crack the passwords. If we know the company's or institution's password policy, we can choose a subset of all characters to meet their policy and speed up our cracking. For instance, if a company allows an all-numeric character set, choose to crack the hashes with just numbers. These types of passwords are VERY easy to crack.
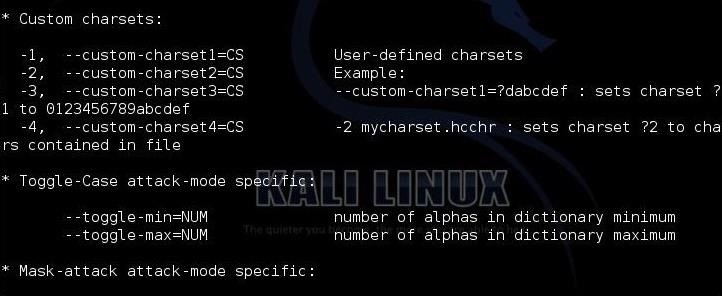

The next screen includes some of the more obscure options, including the output file type, the debug mode and the built-in character sets.
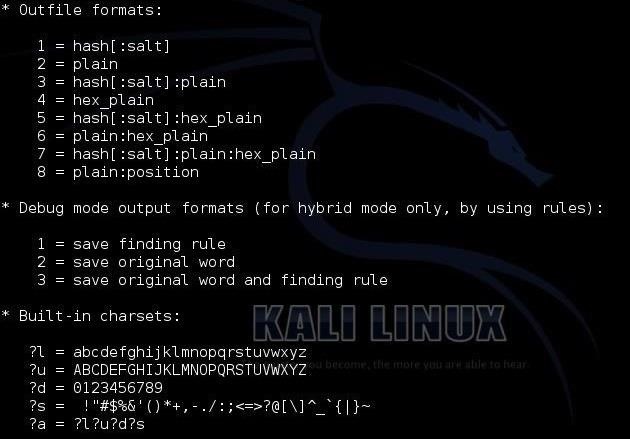
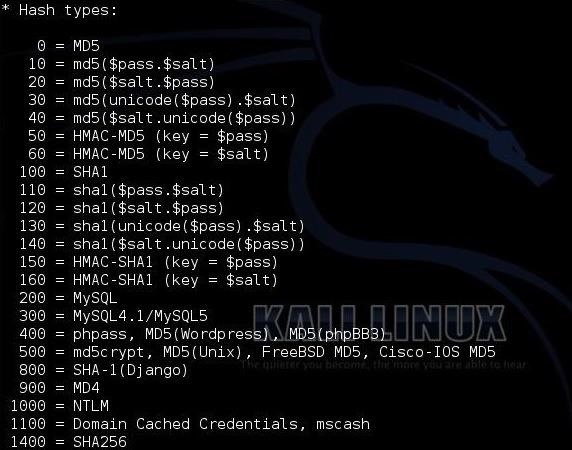
Finally, we have to chose the type of hash we are trying to crack. Hashcat gives us numerous options. When we get ready to crack the hash, we need to designate in our command what type of hash we are working with by giving hashcat the number associated with the hash type. Here we can see a list of some of the hash types hashcat can work with.
Step 3 Choose Your Wordlist
In this tutorial, we will be using a simple dictionary attack on some Linux hashes. To do so, we need a wordlist to work from. There are literally thousands of wordlists available on the web, but Kali has numerous wordlists built right in, so let's try using one of those.
To find the built in wordlists in Kali, we can type:

When we do, we can see that there are dozens of wordlists available
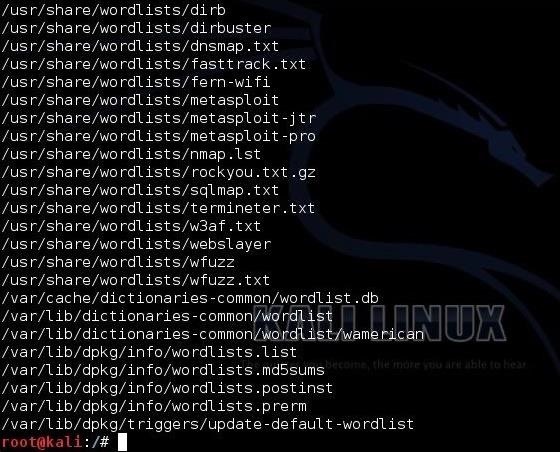
I will be using the wordlist built for sqlmap, which has over one million words and hybrid words.
Step 4 Grab the Hashes
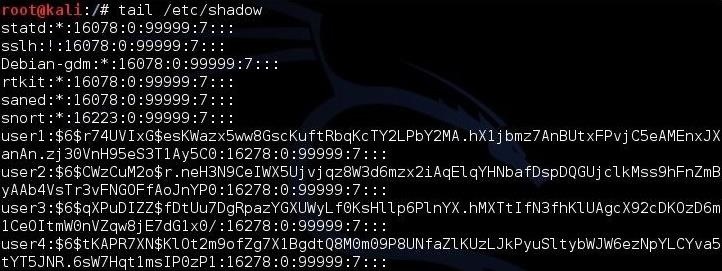
In the next step, we need to grab the hashes on our Kali system. If we are logged in as root, we can see and grab the hashes. In Linux, the hashes are stored in the /etc/shadow file, so if we type:
We can see the shadow file with the hashes, as below.
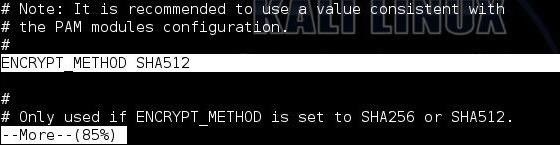
Next, we need to know what type of hashing the system is using. In Linux, we go to the /etc/login.defs to view what encryption type the system is using. We open that file by typing:
When we navigate about 85% down the file, we can see that Kali is using SHA512 encryption. This is important, as we will need to tell hashcat this information when we are ready to crack the hashes.
Crack the Hashes!
Now, that we know the basics of hashcat, where the hashes are located and the type of encryption, we are ready to begin cracking the hashes.
Let's first put those hashes into a separate file we will name hash.lst.
To make sure that they were copied over, let's check by typing:
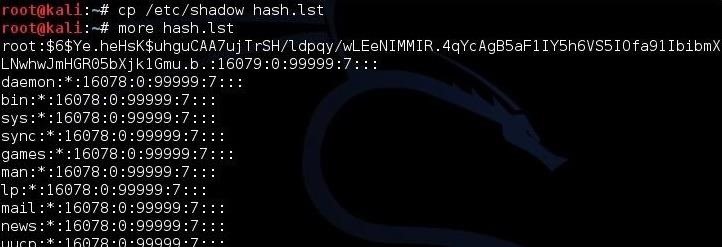
To prepare this file for cracking, we need to remove all of the information in this file, except the hashes. The /etc/shadow file includes the username, then the salted hash, and then information about the applicable user policy. We need to remove all that information leaving just the hash.
We can see that this file starts with the username, i.e., "user1", "user2", etc. Open this file in your favorite text editor (vim, vi, leafpad) and delete the username and the following colon. Then, go to the end of the line and remove the information after the hash that starts with a colon ). Now we will have a file with just the hashes and nothing else.
). Now we will have a file with just the hashes and nothing else.
In the final step, we can now start cracking the hashes. Here's the command I used.
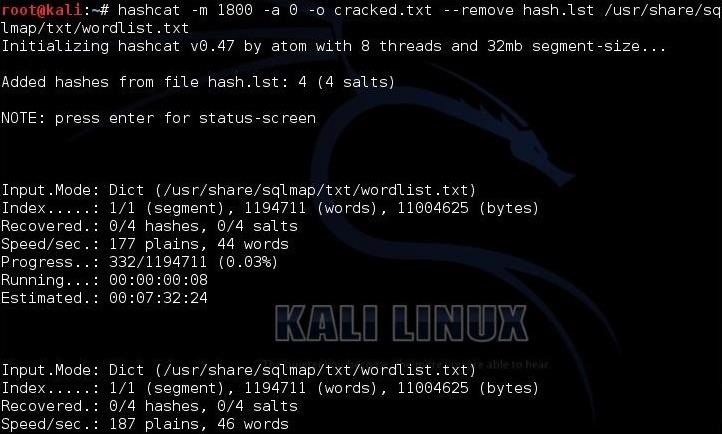
Once the cracking process starts, we can hit <enter> to get an update on the process. When hashcat has completed its work, you will see a screen like below where hashcat announces that it has recovered all my hashes after 9 :47:16 of work.
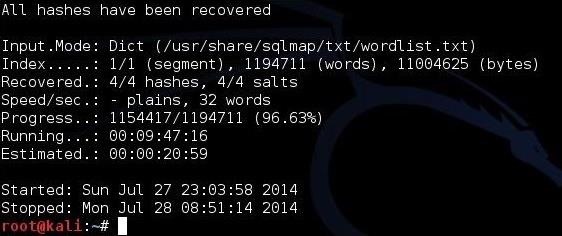
Now, we only need to open the cracked.txt file to view our cracked passwords!
Hashcat may be the world's best password cracking tool right now, so take some time to get to know it. It has many more features that we have not yet touched on, and a version that uses your GPU (oclhashcat) that can crack passwords many times faster than your CPU can!
Step 1 Fire Up Kali & Open Hashcat
Let's start by firing up Kali and opening hashcat. Go to Applications -> Kali Linux -> Password Attacks -> Offline Attacks -> hashcat, as seen below.

When we click on the hashcat menu item, it opens the help screen.

At the top of the screen, you can see the basic hashcat syntax:
Kod:
kali > hashcat options hashfile mask|wordfiles|directoriesWe can see some of the options for hashcat displayed below the basic syntax. Some of the most important of these are -m (the hashtype) and -a (attack mode). In general, we will need to use both of these options in most password cracking attempts with hashcat.
Step 2 More Extensive Options
If we scan a bit further down this hashcat help screen, we can see more options. The first two below are some of the key options that hashcat enables.
First, hashcat enables rules that allow us to apply specifically designed rules to use on our wordlist file. These rules can take our wordlist file and apply capitalization rules, special characters, word combinations, appended and prepended numbers, and so on. Each of these will help us to break passwords that have been made more complex to a**** dictionary attacks.

The next stanza shows us custom character sets. This enables us to set the character set that we want to use to crack the passwords. If we know the company's or institution's password policy, we can choose a subset of all characters to meet their policy and speed up our cracking. For instance, if a company allows an all-numeric character set, choose to crack the hashes with just numbers. These types of passwords are VERY easy to crack.


The next screen includes some of the more obscure options, including the output file type, the debug mode and the built-in character sets.

Finally, we have to chose the type of hash we are trying to crack. Hashcat gives us numerous options. When we get ready to crack the hash, we need to designate in our command what type of hash we are working with by giving hashcat the number associated with the hash type. Here we can see a list of some of the hash types hashcat can work with.

Step 3 Choose Your Wordlist
In this tutorial, we will be using a simple dictionary attack on some Linux hashes. To do so, we need a wordlist to work from. There are literally thousands of wordlists available on the web, but Kali has numerous wordlists built right in, so let's try using one of those.
To find the built in wordlists in Kali, we can type:
Kod:
kali > locate wordlist
When we do, we can see that there are dozens of wordlists available

I will be using the wordlist built for sqlmap, which has over one million words and hybrid words.
Step 4 Grab the Hashes
In the next step, we need to grab the hashes on our Kali system. If we are logged in as root, we can see and grab the hashes. In Linux, the hashes are stored in the /etc/shadow file, so if we type:
Kod:
kali > tail /etc/shadowWe can see the shadow file with the hashes, as below.

Next, we need to know what type of hashing the system is using. In Linux, we go to the /etc/login.defs to view what encryption type the system is using. We open that file by typing:
Kod:
kali > more /etc/login.defs
Crack the Hashes!
Now, that we know the basics of hashcat, where the hashes are located and the type of encryption, we are ready to begin cracking the hashes.
Let's first put those hashes into a separate file we will name hash.lst.
Kod:
kali > cp /etc/shadow hash.lstTo make sure that they were copied over, let's check by typing:
Kod:
more hash.lst
To prepare this file for cracking, we need to remove all of the information in this file, except the hashes. The /etc/shadow file includes the username, then the salted hash, and then information about the applicable user policy. We need to remove all that information leaving just the hash.
We can see that this file starts with the username, i.e., "user1", "user2", etc. Open this file in your favorite text editor (vim, vi, leafpad) and delete the username and the following colon. Then, go to the end of the line and remove the information after the hash that starts with a colon
In the final step, we can now start cracking the hashes. Here's the command I used.
Kod:
kali > hashcat -m 1800 -a 0 -o cracked.txt --remove hash.lst /usr/share/sqlmap/txt/wordlist.txt
Kod:
-m 1800 designates the type of hash we are cracking (SHA-512)
-a 0 designates a dictionary attack
-o cracked.txt is the output file for the cracked passwords
--remove tells hashcat to remove the hash after it has been cracked
hash.lst is our input file of hashes
/usr/share/sqlmap/txt/wordlist.txt is the absolute path to our wordlist for this dictionary attack
Once the cracking process starts, we can hit <enter> to get an update on the process. When hashcat has completed its work, you will see a screen like below where hashcat announces that it has recovered all my hashes after 9 :47:16 of work.

Now, we only need to open the cracked.txt file to view our cracked passwords!
Hashcat may be the world's best password cracking tool right now, so take some time to get to know it. It has many more features that we have not yet touched on, and a version that uses your GPU (oclhashcat) that can crack passwords many times faster than your CPU can!






