
First of all, hello everyone. As TurkHackTeam Blue Team, our primary goal is to close the lack of Turkish Resources. At the same time, we decided to translate the Turkish resources prepared with the support of our Director @Pentester into English.
Today's topic is the solution of the 2nd part of the Hunter Lab on CyberDefenders.



Let's Start
Case Overview: The SOC team got an alert regarding some illegal port scanning activity coming from an employee's system. The employee was not authorized to do any port scanning or any offensive hacking activity within the network. The employee claimed that he had no idea about that, and it is probably a malware acting on his behalf. The IR team managed to respond immediately and take a full forensic image of the user's system to perform some investigations.
There is a theory that the user intentionally installed illegal applications to do port scanning and maybe other things. He was probably planning for something bigger, far beyond a port scanning!
It all began when the user asked for a salary raise that was rejected. After that, his behavior was abnormal and different. The suspect is believed to have weak technical skills, and there might be an outsider helping him!
Your objective is to analyze the image and to either confirm or deny this theory.

Tools Used
FTK Imager
Stellar Repair for Outlook
WinPrefetchView
PECmd
ShellBagsExplorer

16-)What is the Gmail address of the suspect employee ?
With the Stellar Repair for Outlook tool, we extract the backup.pst file under the Hunter/Documents/Outlook Files directory for examination.
We open our backup file with the tool. We enter the Important tab from the tabs under Gmail and it gives us the Gmail address of the suspect.
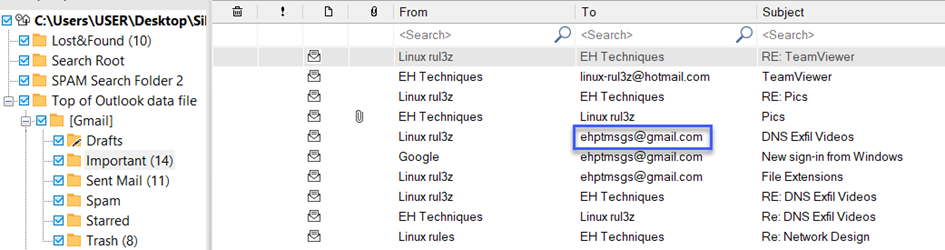
Answer: ehptmsgs @gmail.com

17-) It looks like the suspect user deleted an important diagram after his conversation with the external attacker. What is the file name of the deleted diagram?
Since the question asks for the deleted file, we are going to the Trash tab under Gmail.
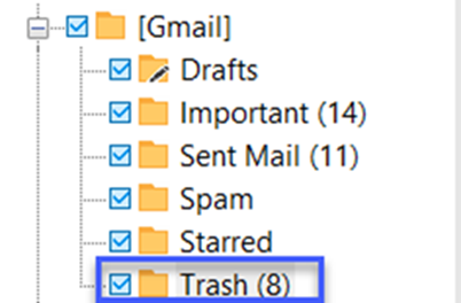

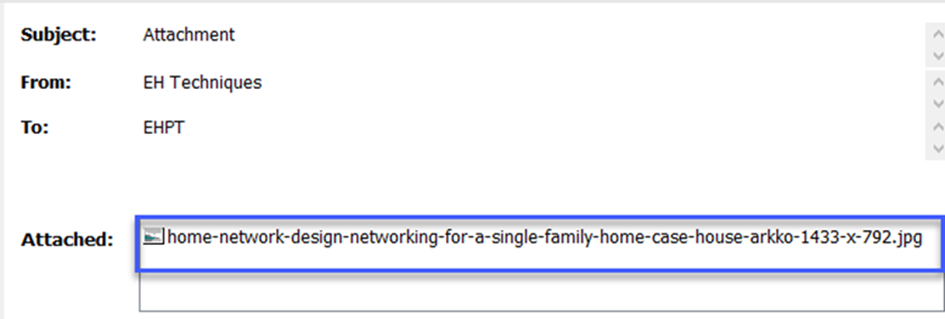
When we examine 4 e-mails with attachments out of in the 8 e-mails, we find our answer in this e-mail sent on June 21, 2016 at 15.19.
Answer: home-network-design-networking-for-a-single-family-home-case-house-arkko-1433-x-792.jpg

18 -) The user Documents directory contained a PDF file discussing data exfiltration techniques. What is the name of the file?
Starting from the question, the first thing we need to do is think about the word PDF. In other words, if we start from the word PDF, we need to search on documents, documentation directories or files.
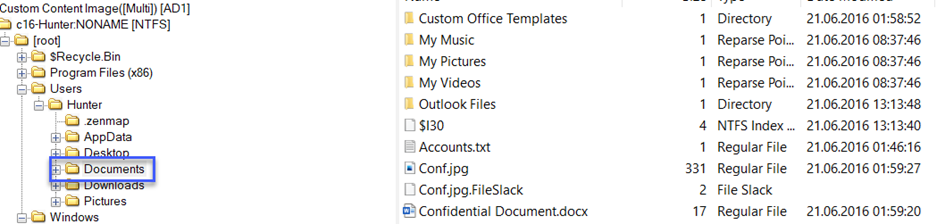

We see 5 pdf files. If we export all of them (export files) and examine them, we are left between 4 important files.
a-) defcon-16-ricks pdfi related to DNS Data Exfiltration
b-) When we open the how_do_threat_actors_steal_your_data pdf, we are greeted by the Data Exfiltration header, and when we write the answer, we are greeted with a false flag.
We're looking at our other pdf.
c-) When we open the mwri-detecting-deterring-both pdf, Data Exfiltration title welcomes us:
But this is false flag too. Then let’s looking our other file.
d-) When we open our Ryan_VanAntwerp_thesis pdf, the following title welcomes us:
Exfiltration Techniques: An examination and emulation
When we write this, it accepts our flag as correct.
Answer: Ryan_VanAntwerp_thesis.pdf

19-)What was the name of the Disk Encryption application Installed on the victim system?
I primarily look at the Program Files (x86) directory because the question uses the word installed. Then I display 3 directories under the Jetico directory. These are Shared – Shared64 and BCWipe. The BCWipe directory catches my attention and I look into it (BCWipe is designed to surgically delete certain data files without damaging the hard drive. At the same time, BCWipe allows you to permanently delete files so that they can never be recovered or deleted).
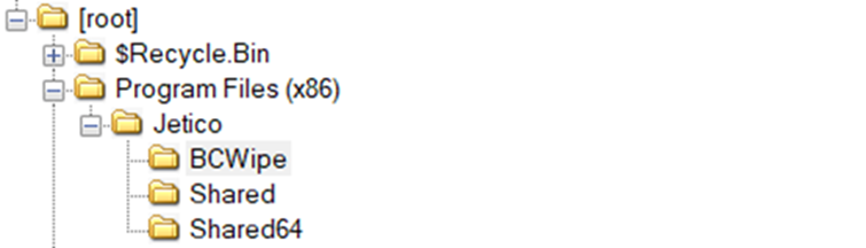

Answer: Crypto Swap

20-) What are the serial numbers of the two identified USB storage?
The directory/location where we will see the connected USB devices in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\USB
But since we will do the analysis through the Registry Explorer tool, the required directory is:
It is SYSTEM > ControlSet001 > Enum > USBTOR.
Two USB names appear under the directory, the first of which is:
Disk&Ven_Imation&Prod_Nano_Pro&Rev_PMAP
The second is:
It is Disk&Ven_Lexar&Prod_JumpDrive&Rev_1100. Our answer appears after entering this directory.
Answer: 07B20C03C80830A9,AAI6UXDKZDV8E9OU

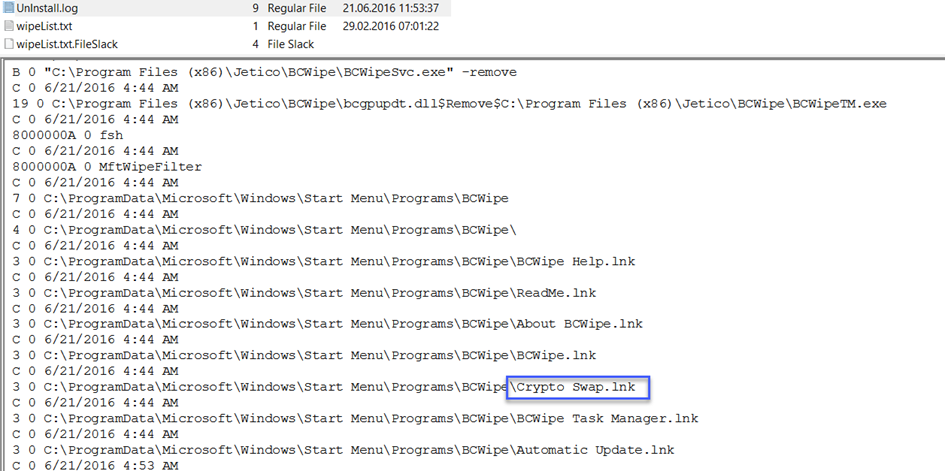
21-)One of the installed applications is a file shredder. What is the name of the application?
I mentioned it here when answering question 19. File shredder is an application that deletes files and processes them. The answer to that question is BCWipe, but it does not accept the answer as BCWipe. So let's do some research to learn about this tool:
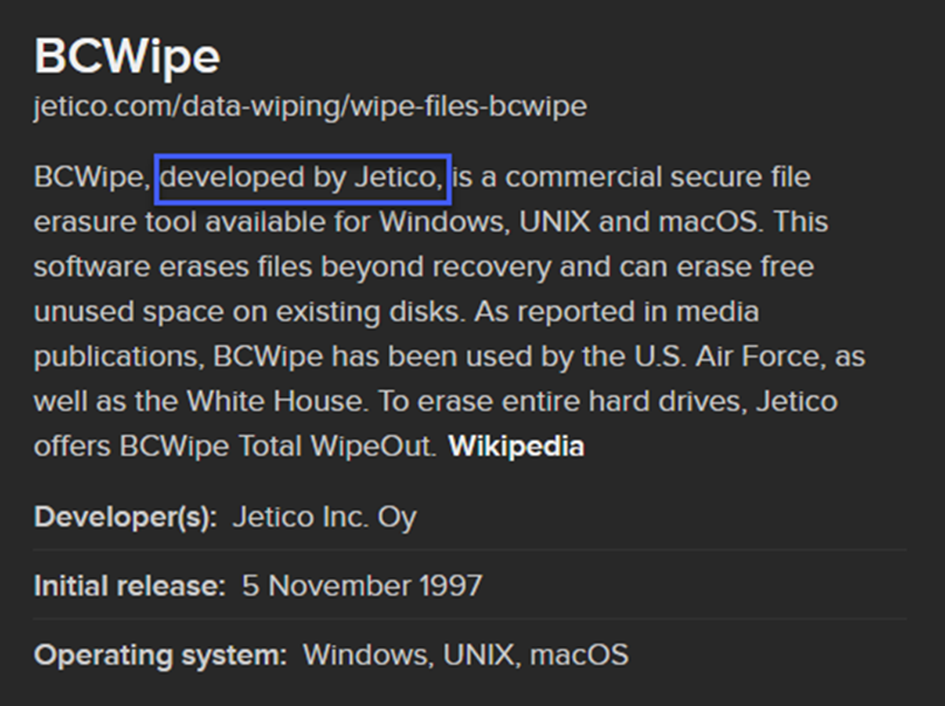
It tells us that the developer of this app is Jetico.
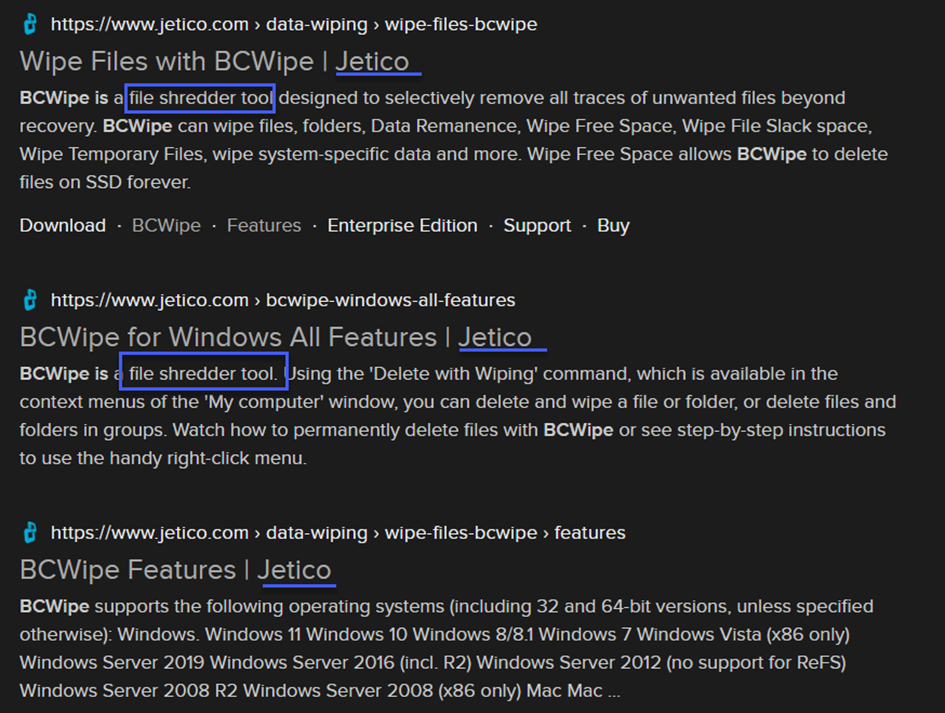
In this screenshot, we verify that the BCWipe tool is a file shredder tool.
At the same time, the BCWipe tool is located in the Jetico directory, so let's change our answer from BCWipe to Jetico BCWipe.
Answer: Jetico BCWipe

22-) How many prefetch files were discovered on the system?
NOTE: These are the temporary files stored in the System folder name as a prefetch. Prefetch is a memory management feature. Logs of frequently running applications on your machine are stored in the prefetch folder. Log is encrypted in Hash Format so no one can easily decrypt application data. These files can be used to extract the timestamp and other resources consumed when the file was executed. Prefetch data is stored in C:\Windows\Prefetch by default.
Let's export the Prefetch file under the Windows directory and view this file with the WinPrefetchView tool.
NOTE2:
From the Options > Advanced Options (F9) tab, the Prefetch Folder section will automatically remain selected as the default storage directory of our computer as C:\Windows\Prefetch. So change this (let's not forget to choose the directory of the Prefetch file we are exporting).
Then, when we open our Prefetch file, we select all the files with the Ctrl + a combination, but the ones with .pf extensions are what we need, as the tool supports/opens only files with .pf extension.
What I want to say here is that there are 229 files in FTK Imager (including .pf, .bin, .db file extensions). I explained it because it asked us about the prefetch file extensions discovered in the question.
While examining the Prefetch file we exported, we select all the files by pressing Ctrl + a again and it tells us that there are 186 files. When we write it in the answer section, it tells us the wrong flag. Let's continue our review now. By clicking on the filename column, we put it in alphabetical order, but it still does not work. Afterwards, File Size, that is, the file sizes, attracts my attention and when I filter, a sorting occurs, especially the files with a size of 0.
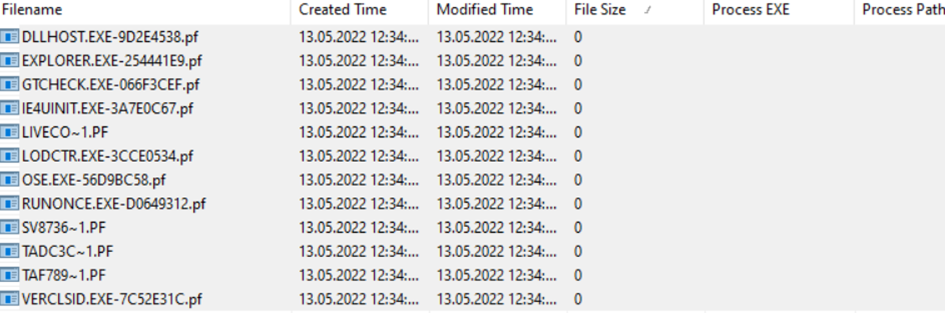
In the screenshot, we see that the file size of 12 prefetch files is 0, and when we extract 12 files with 0 file size from our 186 files, we reach our answer.
Answer: 174

23-) How many times was the file shredder application executed?
Now let's think a bit here and continue to review the tool. While we did it without filtering in the previous question, let's take a look at all the columns, where can we filter?
Two more columns stand out, the first is Run Counter and the second is Process EXE. The first is the run counter. The second is exe processes. So if we can find the file we want here, we will reach our answer. What was shredder application now? BCWipe.
Then let's find the BCWipe(.exe) file in the Process EXE column. Or, instead of searching for it one by one, let's filter the Process Exe column since the letter B will be at the top, let's see what the result will be:
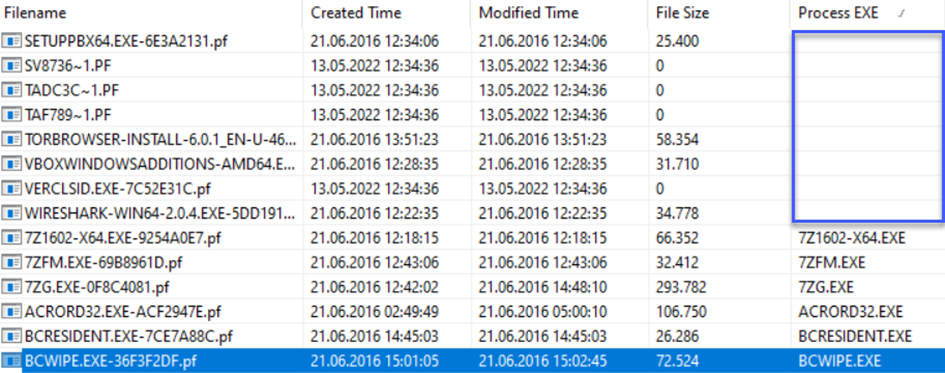

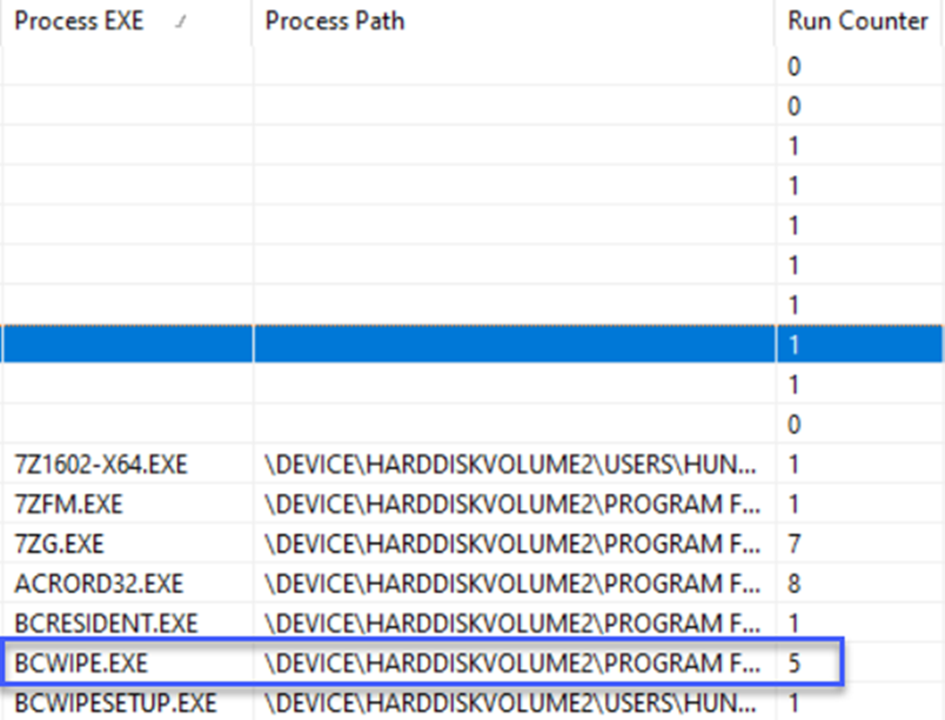
After the files with a size of 0, we display the output and the number of executions as 5 on the 6th line.
Answer: 5

24-) Using prefetch, determine when was the last time ZENMAP.EXE-56B17C4C.pf was executed?
Since in the previous question there was already a sorting by the Process EXE column, let's go directly to the bottom because of the letter Z.
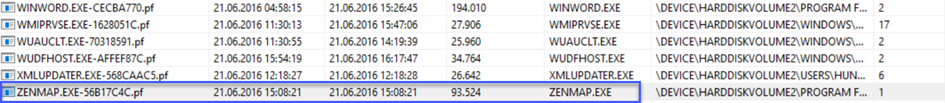
Last working time
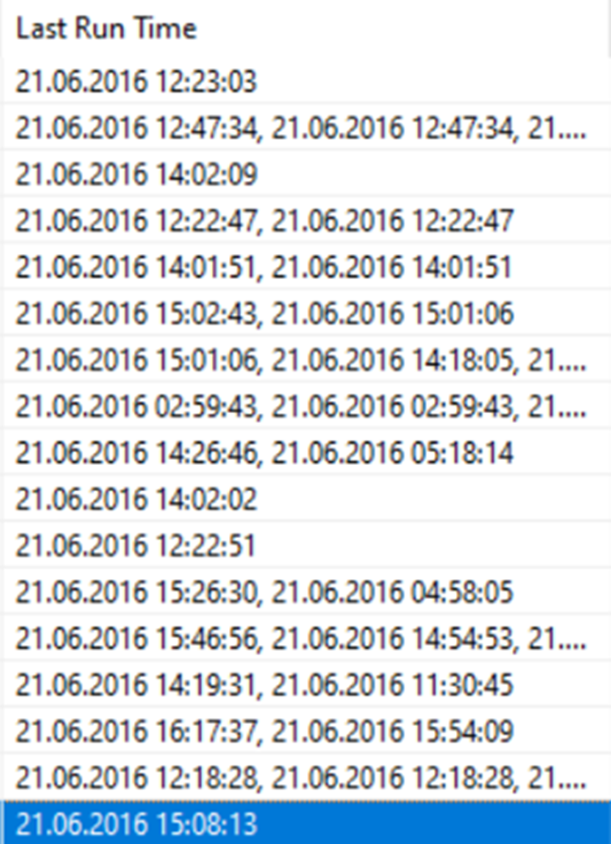
This is how we view it
In other words, we display the last run time of the zenmap.exe executable as 21.06.2016 15:08:13 via the tool. When we write this directly in the answer part, it does not accept it, then we look at it and it is not in the form of day-month-year, which we say as a habit, but in the form of month-day-year, and it asks for the time between :. So we need to use / between dates and : between hours. Let's use the PECmd prefetch parser by changing the tool, and open our ZENMAP.EXE file.
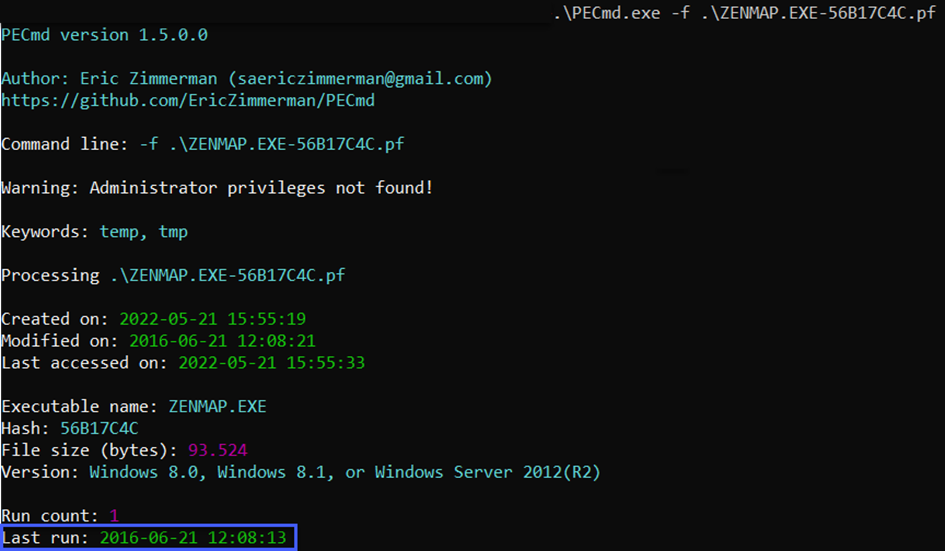
Answer: 06/21/2016 12:08:13 PM

25-) A JAR file for an offensive traffic manipulation tool was executed. What is the absolute path of the file?
When we use a hint in this question:
There are a lot of lnk files. We encounter the sentence “You may need a tool to help find them all with one click”. We are looking for a directory where we can search for lnk files, and then when we go to the Users/Hunter/AppData/Roaming/Microsoft/Windows/Recent directory, we can view all the lnk files.
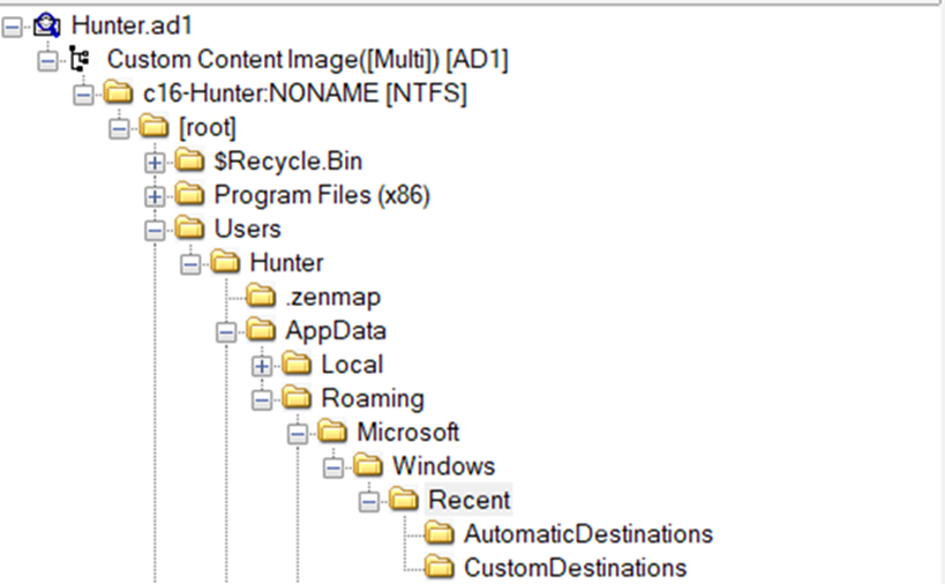
There are 52 files in the directory and we take a quick look at it. He already gave us as a separate clue that the answer in question format ends with .jar. To find the file that ends with .jar.lnk, we examine our directory from the end, and when we go up:
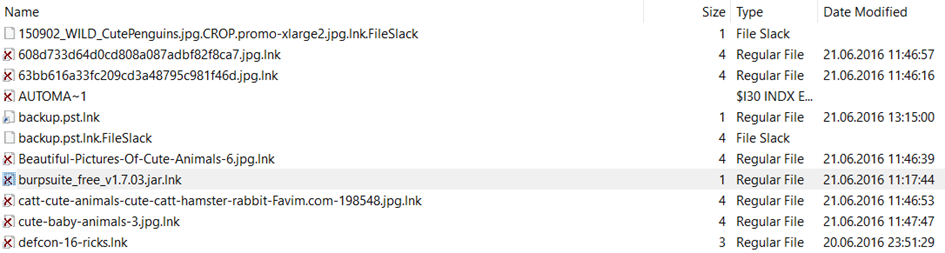
We got the burpsuite_free_v1.7.03.jar file but that's not the answer. It is asking for the absoulte path of the file. Let's go immediately to the local user's Downloads directory:
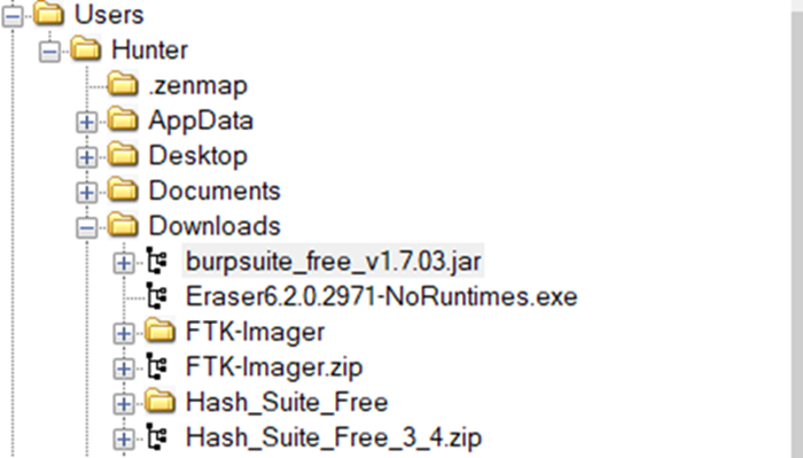
Bingo, we found our file in the Downloads directory. Now let's extract the absolute path.
Answer: C:\Users\Hunter\Downloads\burpsuite_free_v1.7.03.jar

26-) The suspect employee tried to exfiltrate data by sending it as an email attachment. What is the name of the suspected attachment?
In other words, the analysis of the e-mail he requested from us, for this we need to examine the backup.pst (A PST file is an Outlook Personal Information Store file) file under the Hunter/Documents/Outlook Files directory. Let's export our file with Export Files and analyze our outlook file with .pst extension with Stellar Repair for Outlook tool.
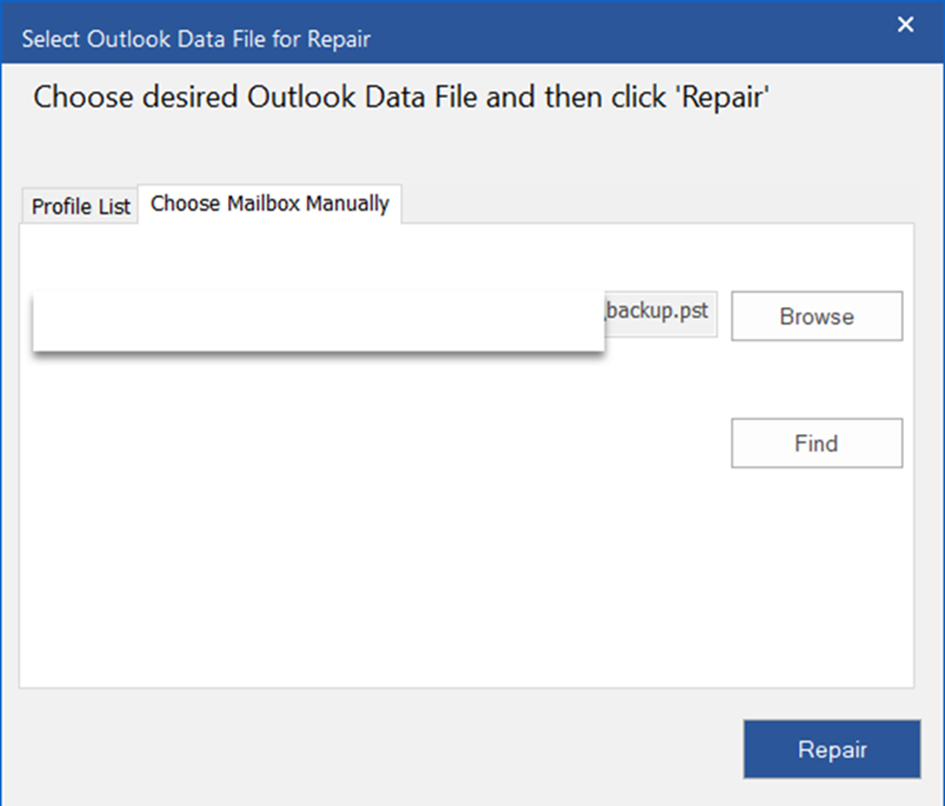
We select the backup.pst file.
Then, based on the question, we can understand that the place we need to examine is Sent Mail. When we enter the tab, we are greeted with the following screen:
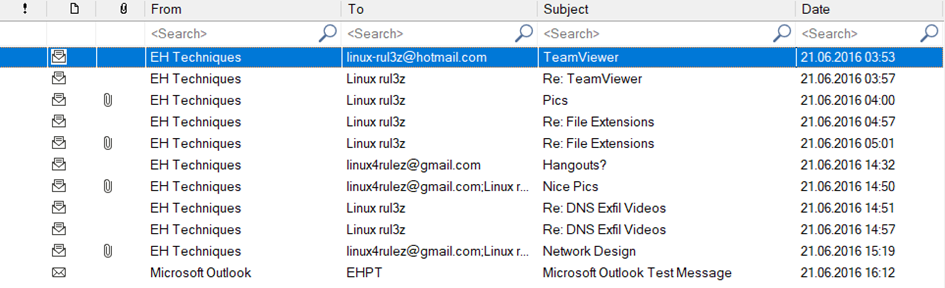
When we examine the e-mails here;
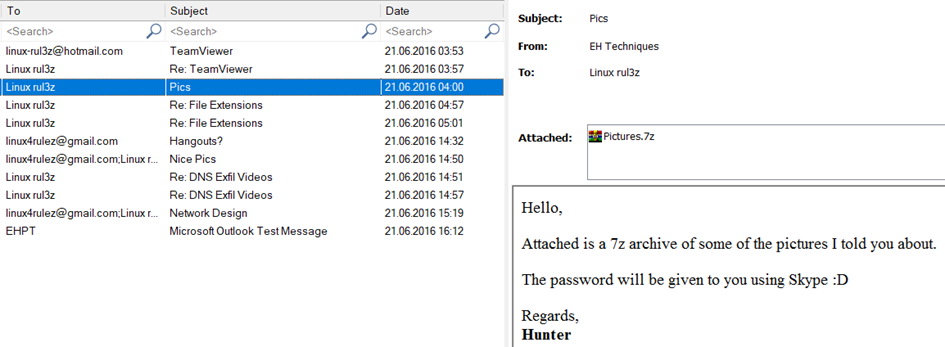
We reach our answer from the attachment and the content of the message in the 3rd e-mail.
NOTE: We also notice here that the attempted leaked files were archived under the misleading name Pictures and our extension 7z (7Z is the file extension used for an archived file created using 7-Zip, a free, open source file compression tool. similar to archived formats, but uses a higher compression ratio as well as AES-256 encryption. Also, the 7-Zip tool is the archiving tool of choice for malware analysis.)
Answer: Pictures.7z
NOTE: If you continue to deal with analyzes and you are asked to deal with attachments in a tab with a lot of mails, there is something that I think will help you. I want to show through the picture.

These signs also show that a file attachment has been added in an e-mail by the sender or incoming person, different from just the text. In other words, as I mentioned above, if you are going to search through an attachment, we click on the column and filter through attachments and first of all, we see the attached mails.

As you can see, the screenshot is that there are 4 attached mails and I want these 4 mails to be shown to me first.

27-) Shellbags shows that the employee created a folder to include all the data he will exfiltrate. What is the full path of that folder?
Here, first of all, I would like to touch on what Shellbags are and under which directory they are located.
What is Shellbag?
Shell bags help monitor the views, sizes, and positions of a folder window when viewed through Windows Explorer; this includes network folders and removable devices.
Why are Shellbags Important for Forensic?
The location, appearance, or size of a particular folder window is of little importance to forensic investigators. But while these features aren't all that valuable, Windows creates a series of additional structures as it stores these features in the registry, giving the investigator detailed information about the folder, the suspect's browsing history, and details about any folder. This means that all directory migrations are tracked and protected in the registry. A Shellbags entry is created for each newly discovered folder.
We can find these details under reg hive as NTUSER.dat and UsrClass.dat (hives is the name given to the main part of the registry that contains registry keys, registry subkeys and registry values. All keys considered hive start with "HKEY" and located at the root or at the top of the hierarchy in the registry.) Some common registry hives in Windows are:
HKEY_CLASSES_ROOT
HKEY_CURRENT_USER
HKEY_LOCAL_MACHINE
HKEY_USERS
HKEY_CURRENT_CONFIG
Shellbags are located in NTuser.dat hive for Windows XP, UserClass.dat for Win7 and above, under HKCU (HKEY Current User).
Since the machine of the file we are performing the forensics of is Win7 or higher, the file we need to find is UserClass.dat.
Under the directory Users/Hunter/AppData/Local/Microsoft/Windows

We see our UsrClass.dat file. Then we can export the Windows directory, which is the directory of our UsrClass.dat file, and open it via the tool.
Then, when we open our UsrClass.dat hive with the ShellBags Explorer Tool
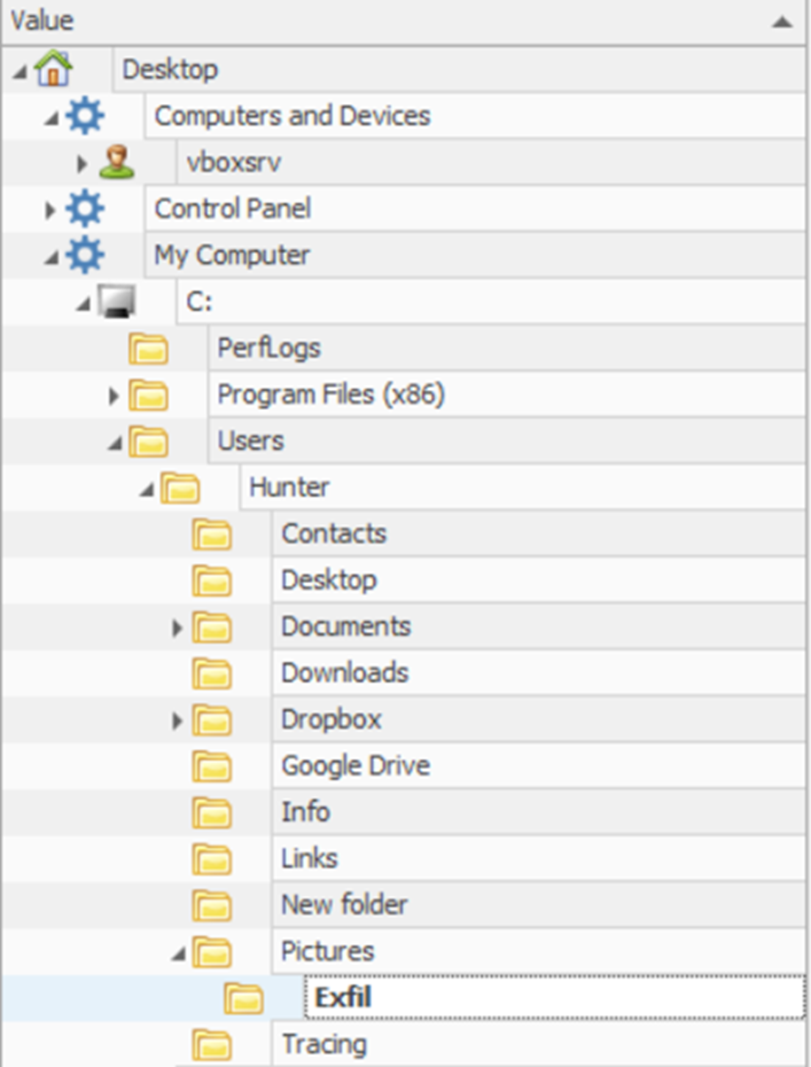
We reach the Exfil file under the Pictures directory.
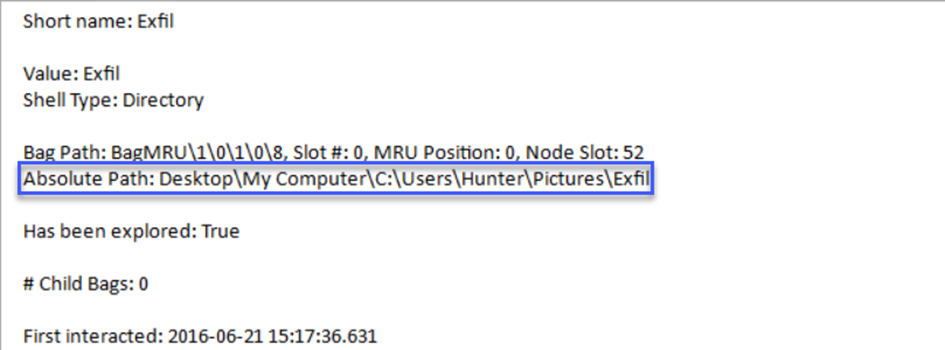
When we come to FTK and look at the same directory,
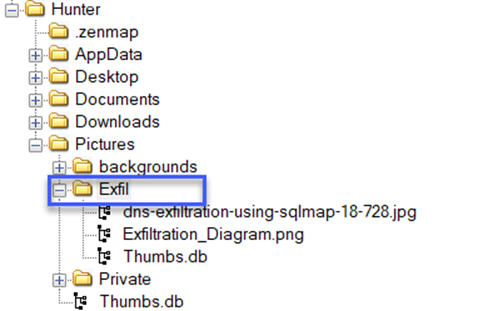
We can view the file and its contents.
Answer: C:\Users\Hunter\Pictures\Exfil

28 -) The user deleted two JPG files from the system and moved them to $Recycle-Bin. What is the file name that has the resolution of 1920x1200?
Let's go to the moved directory now.
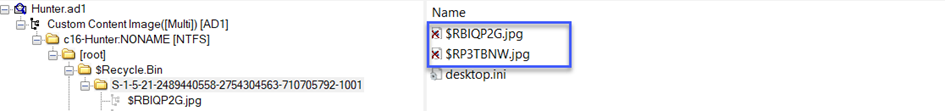
We are displaying 2 .jpg image files, let's take a look at them.
The first picture is blank as you can see. So let's look at the second picture.
The second picture is distorted as you can see. Let's think about what we can do. While I was researching Outlook questions, My Music-Pictures-Videos directories under Hunter/Documents had caught my attention. Let's take a look at Pictures then.

Yes, we couldn't get a result here because our directory is empty. We came back empty-handed, but a .jpg file caught my attention under the /Documents directory, let's take a look at it.
This is the same image in our $Recycle.Bin directory but with a different name. Then, starting from here, the option that we can find the same corrupted file with a different name appears. So let's keep looking again.
After looking carefully for a while, I remembered that there was the Pictures directory and there were too many pictures in it from the previous question.
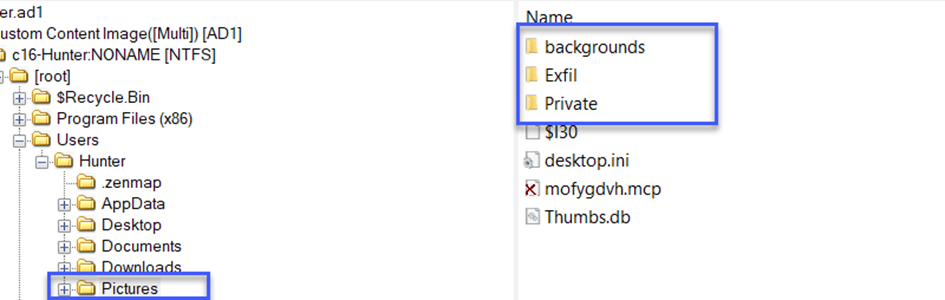
Now let's take a look at the 3 directories on this right side.
First, I enter the backgrounds:






There are many images, but none of them are related to the broken image I'm looking for.
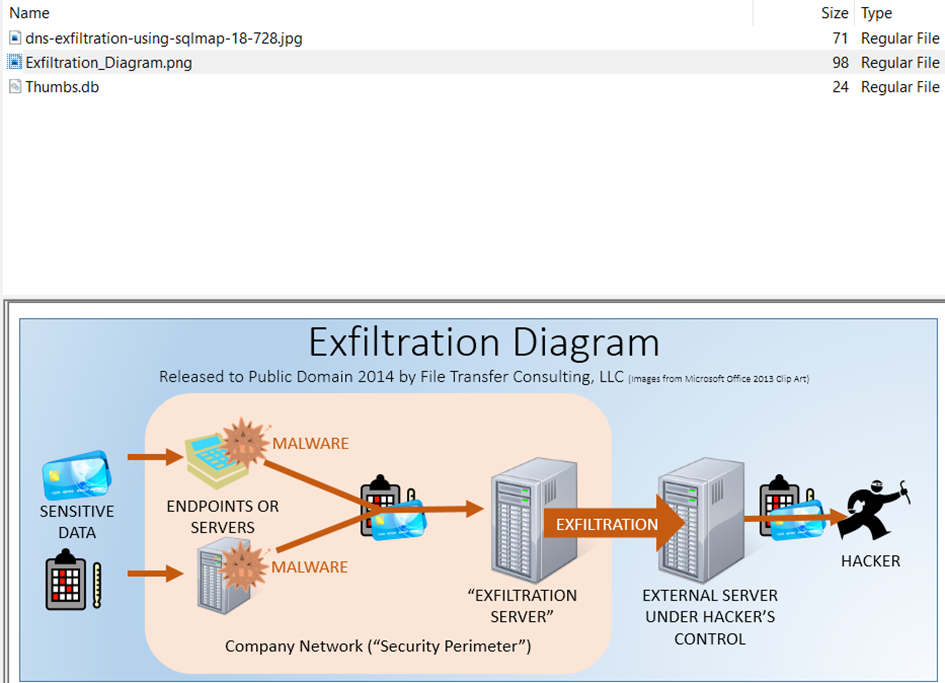
Then I come to the Exfil file, I have already looked at the pictures here, one is Exfiltration_Diagram.png in the answer to Question 27 above and the other is:

I couldn't come to a conclusion from here either, we only have one directory left, the room Private.
When I go into the directory, pictures of cats in the form of Cat, kitties-cats, slide-cat, big-eyes appear, but more importantly, we see our .jpg image file with 1920x1200 extension.
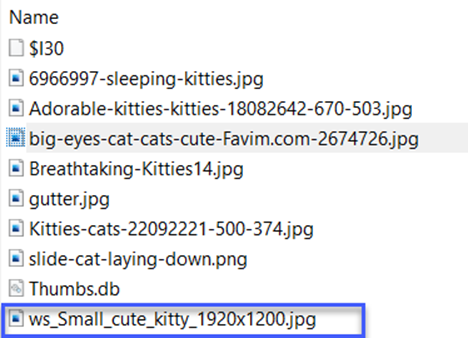
When we get inside:
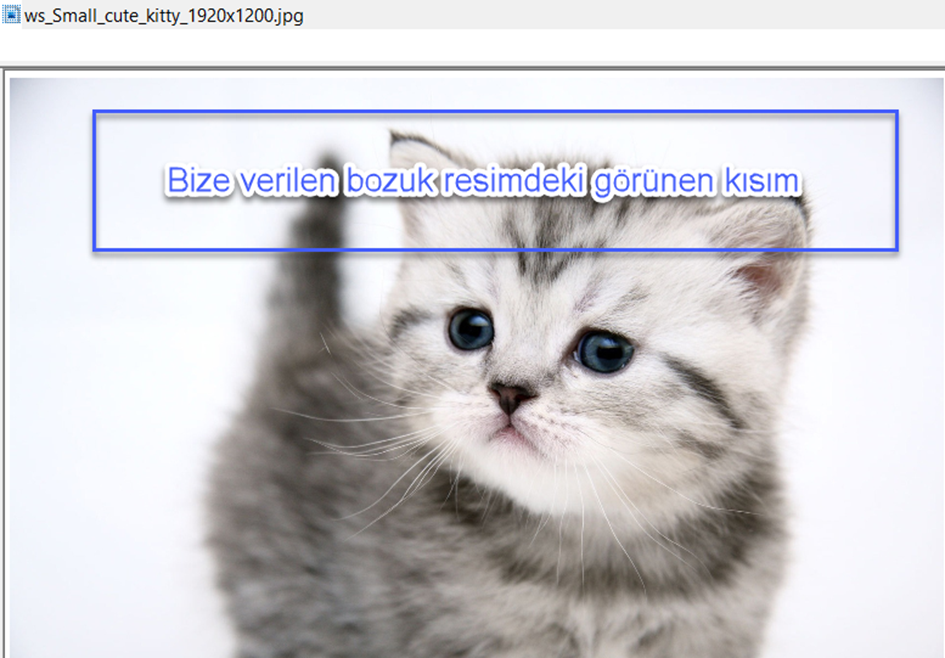
Here we get our answer.
Answer: ws_Small_cute_kitty_1920x1200.jpg

29-) Provide the name of the directory where information about jump lists items (created automatically by the system) is stored?
The hint in the question tells us that we need to do some research, and as a result of our research, we learn the following information from some sources:
Jump lists are lists of recently opened items, such as files, folders, or websites, organized by the program you used to open them.
Jump Lists is a Windows 7 technology that takes you to documents, images, songs or websites that are entered every day. Jump Lists is a system-supplied menu that appears when a user right-clicks a program on the taskbar or Start menu. It is used to provide quick access to frequently used documents and to provide direct links to application functions.
What you see in a Jump Lists is entirely program dependent. For example, Jump List for Internet Explorer shows frequently viewed websites. And Jump Lists don't just show shortcuts to files. Sometimes they provide quick access to commands like composing new email messages or playing music. Jump Lists basically consist of two file types, *.automaticDestinations-ms files that are created by the operating system when the user performs certain actions such as opening files, using the Remote Desktop Connection tool. The CUSTOMDESTINATIONS-MS file contains a timestamp, application ID, and file path that Windows uses to open the pinned file when you select it from the Jump List. Jump Lists are stored in subfolders of the user's Recent folder, previously defined as storing LNK files (C:UsersAppDataRoamingMicrosoftWindowsRecent). Automatic Destinations are stored in the AutomaticDestinations subfolder and Custom Destinations are stored in the CustomDestinations subfolder. Addresses where Jump Lists are saved:
%APPDATA%\Microsoft\Windows\Recent\AutomaticDestinations
%APPDATA%\Microsoft\Windows\Recent\CustomDestinations
I had already noticed these 2 addresses while doing research in Question 25, and when I entered AutomaticDestinations, I remembered that the file extensions were *.automaticDestination-ms as stated above.
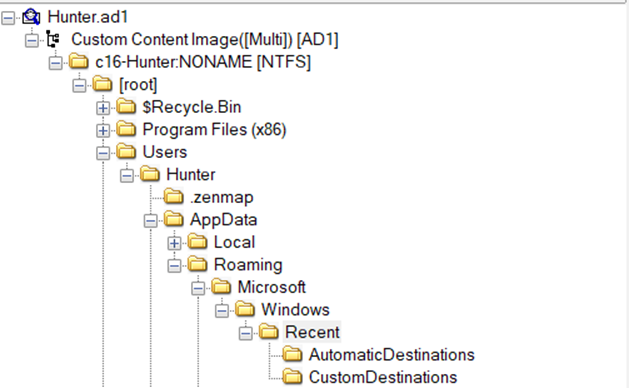
There were 52 files and 2 directories under the AppData/Roaming/Microsoft/Recent directory, as you can see:
AutomaticDestinations and CustomDestinations
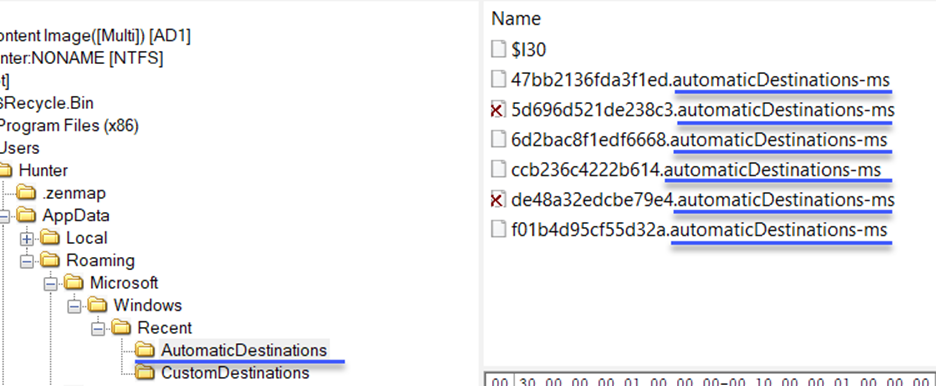
Answer: AutomaticDestinations

30-) Using JUMP LIST analysis, provide the full path of the application with the AppID of "aa28770954eaeaaa" used to bypass network security monitoring controls.
We will use the JumpListExplorer tool to answer the question. The Jump List with the AppID requested in the question exists in the Custom directory, not in the Auto directory. So let's get our file out.
Let's go to the tool and filter among the files we export:
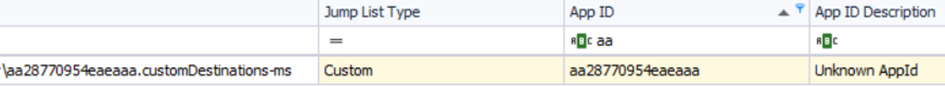

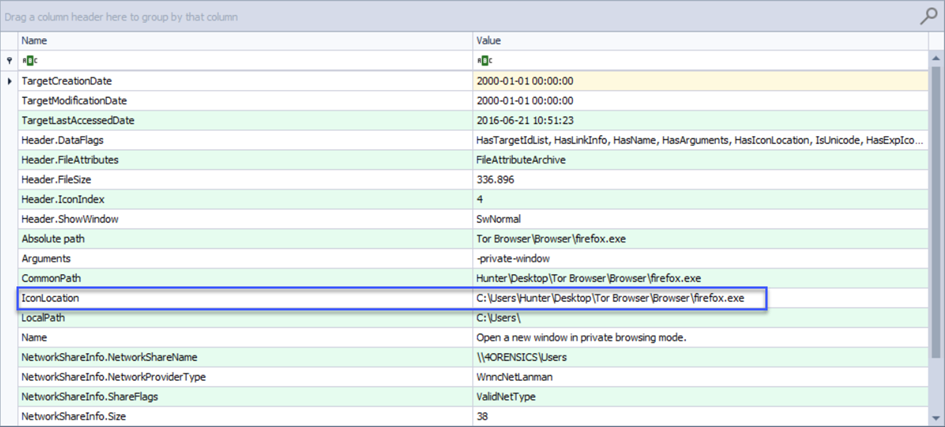
As you can see in the picture, our answer has emerged.
Answer: C:\Users\Hunter\Desktop\Tor Browser\Browser\firefox.exe
I have come to the end of my topic. If there is anything you are wondering about or I can help you, you can write.

Son düzenleme:








