Translator Note: Before getting started I want to tell you about this translation; there was too many HTML tags in the original text, I used ctrl+F combination to find words . So this was a tough process. Also there will be no swedish version of this one. Thanks. Btw, correct me if I translated something wrong because (no offence) there were many grammatical mistakes in the original text as well
Hi Dear TurkHack Team Members, in this tutorial well have a look to password attacks. Let us begin now;
We will handle the subject under 3 titles;
1-) Cewl
2-) Hashcat
3-) John
Now let us begin,
Lets create a wordlist using Cewl Tool;
Wordlist are text documénts used in password attacks. These text documénts used in various password brute force attacks may break the password by chance. Let's take a look at how to create a site-specific wordlist with cewl.
Processes;
We open the terminal and ;
When we run this command, we will see a screen like this;
Here it opens the help menu. Here it shows how to use our tool and what we can do with various parameters. You can read it if you want to.
NOTE: This program is a simple program. When creating a wordlist for a site, do not try it on very high quality sites, the program may crash.
Step 2;
Open the terminal;
NOTE: You can write this as root/Desktop. You determine the name of your directories yourself.
Step 3;
A txt file will appear on the desktop, this process may take a long time, for information. You can implement this wordlist in a brute force attack. The working principle of this program is as follows: It generates passwords according to the words commonly used on the site.
Hashcat ( Password Attack )
Hashcat is a tool that performs a password attack. Now let's get to the use of this tool. First of all we need a password to use this tool, Ill explain;
Step 1;
https://wmaraci.com/md5-sha1-sifre-olusturucu
We go to this address (Site is turkish but its easy to understand and use). md5 so, creating a password. You will create a password from here. For example, I am doing baysiberbela79 here ;
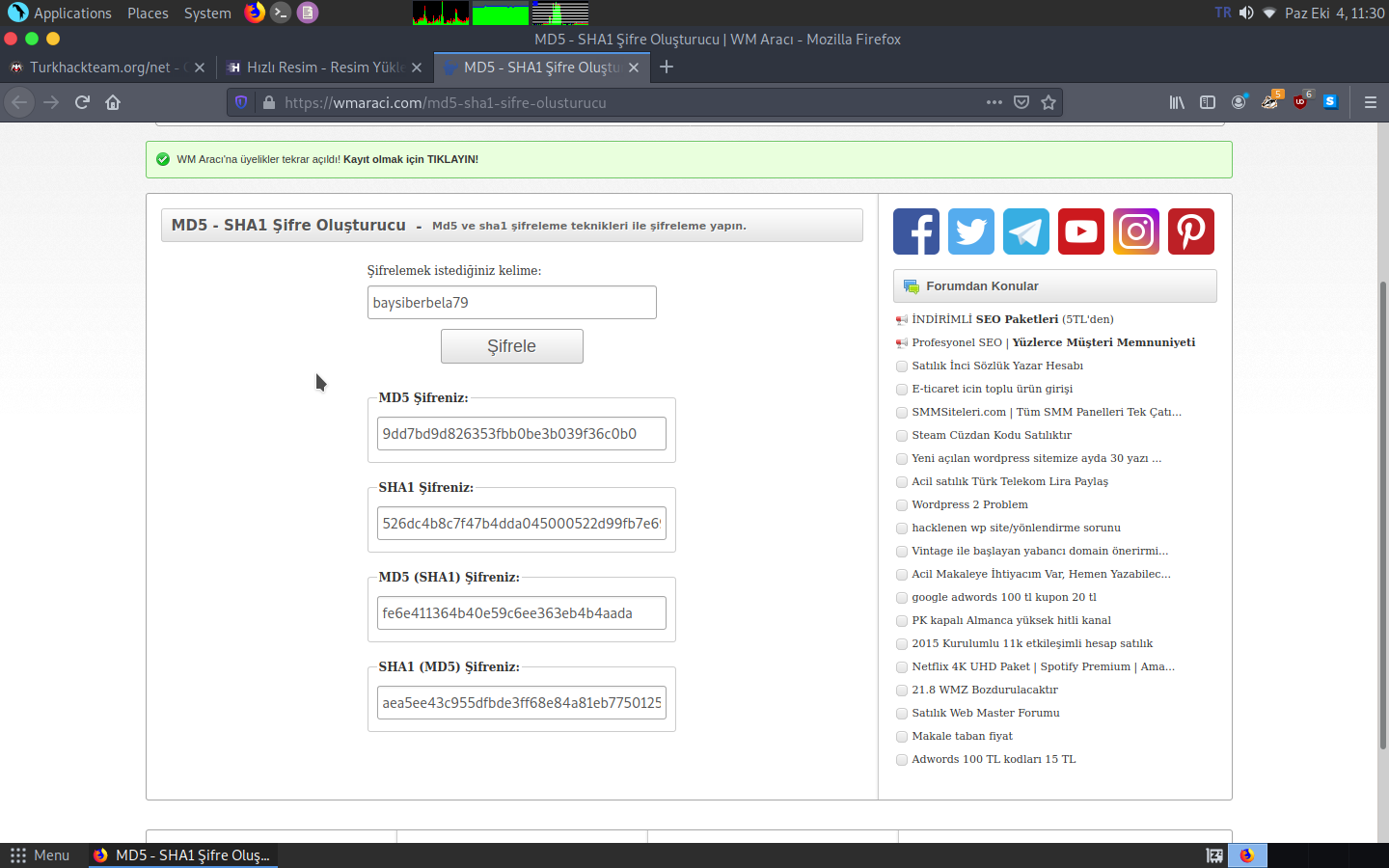
Now it gave us md5 passwords, as you can see here.
Step 2;
Copy your MD5 Password. Then we move on to the terminal;
We switch to the desktop by using this command. Later;
We create a txt documént with this command which means create gedit, keep this in mind.
We paste our password into this txt file that comes to our desktop.
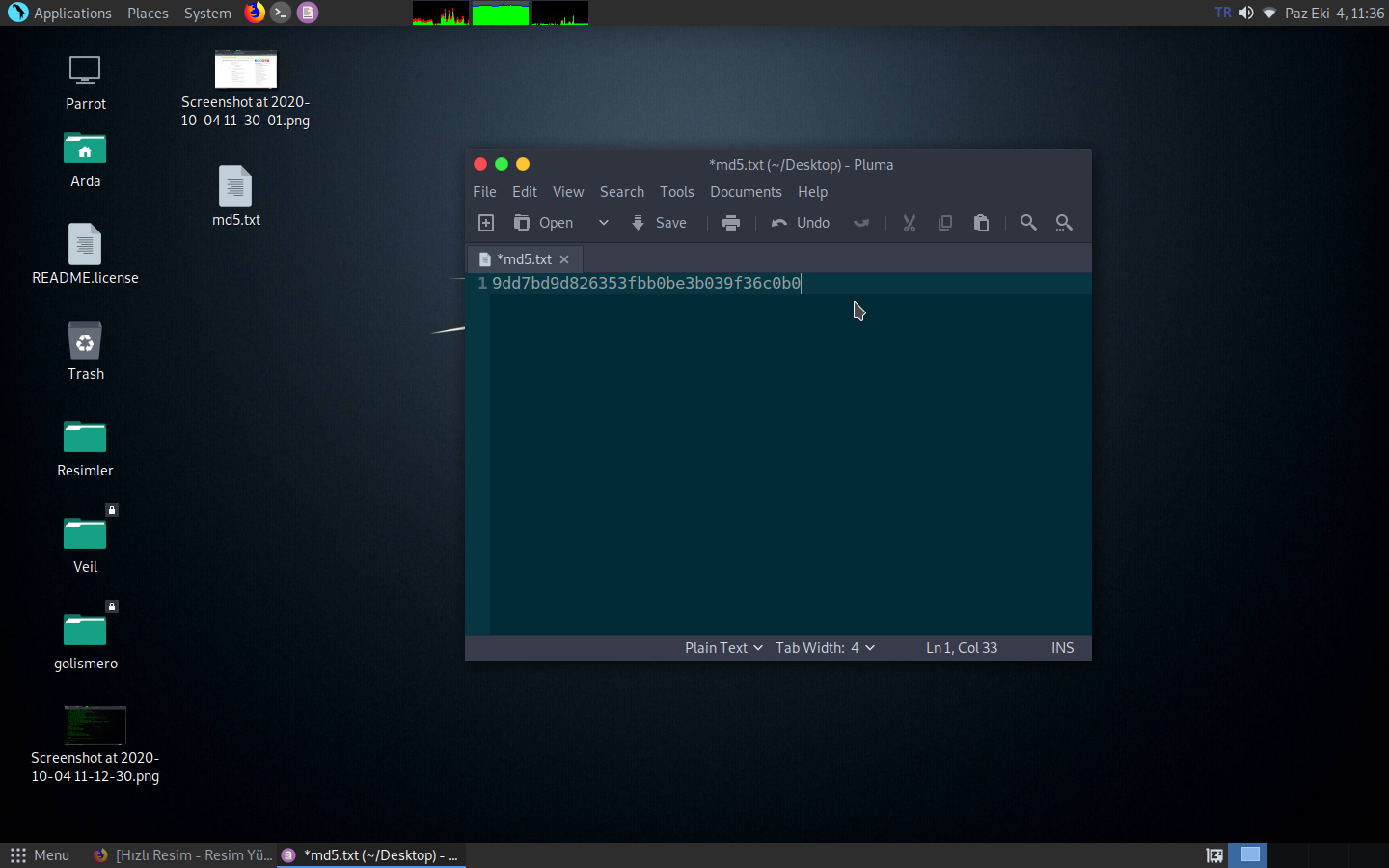
And let's create a wordlist;
Wordlist will also appear on the desktop. If you cannot create it with gedit, you can manually create txt documént on your desktop just like in windows.
Write something in the wordlist;
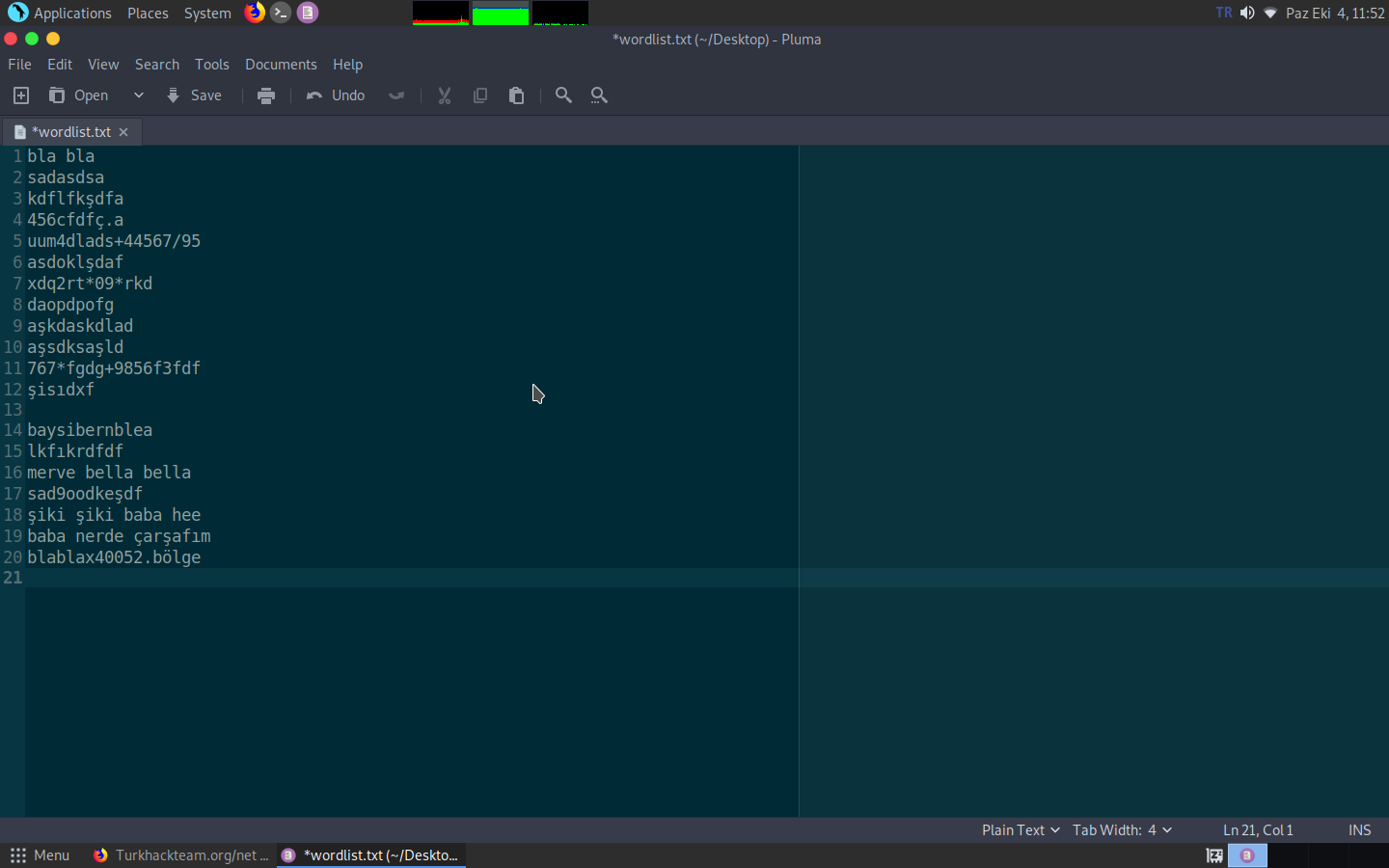
I wrote something here. Then let's start our tool
Step 3;
You write these to the terminal, now Ill mention about something important.
Note: This tool is a very strong tool. So there is a possibility whether it will work according to your processor or not. We can solve this problem using the -- force command.
If you get an error;
We can solve this problem with this command. This force command runs the tool in a slightier way.
It currently performs a brute force attack. It wont find the password, because we did not write that password into the wordlist, nor did we put anything like it, it would have found it if we did.
John The Ripper Tool
Now, let's explain password attacks through this tool. Now, to run this tool, we click to applications and find the john attache there. We click on the John tool from Password Attacks and run it. If you are not root, it will ask you for a password, enter it as toor or enter whatever you have set your password as.
We will see a screen like this;
Here again a menu gives information about how to use this tool. Various parameters are available here. The John tool is a more useful tool than the Hashcat tool.
Step 1;
Now lets open the terminal;
We write the command to the terminal and press enter.
Now when we run this, it gives an error because we cracked this password before. I created a new documént and an MD5 password named baysiberbela79.
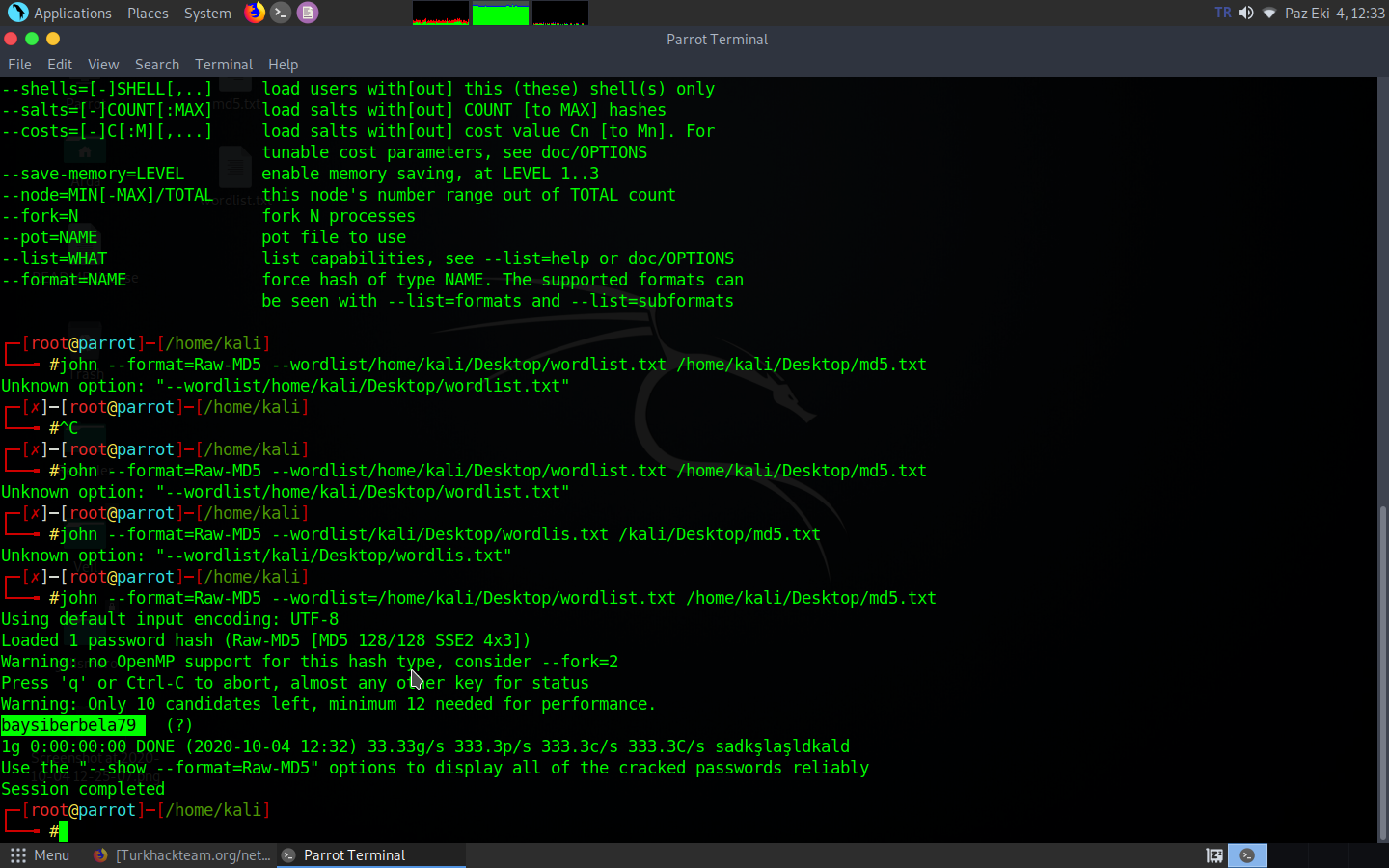
As you can see he found the password here. I put baysiberbela79 in my wordlist and in this case it found the password.
The tutorial ends here, I hope it will be a useful topic. Have a good day, everyone.
Source: https://www.turkhackteam.org/siber-guvenlik/1944606-sifre-saldirilarina-giris-yapalim-cewl-haschat-john.html
Translator: Dolyetyus
Original Author: baysiberbela
1-) Cewl
2-) Hashcat
3-) John
Now let us begin,
Lets create a wordlist using Cewl Tool;
Wordlist are text documénts used in password attacks. These text documénts used in various password brute force attacks may break the password by chance. Let's take a look at how to create a site-specific wordlist with cewl.
Processes;
We open the terminal and ;
Kod:
cewl --helpWhen we run this command, we will see a screen like this;

Here it opens the help menu. Here it shows how to use our tool and what we can do with various parameters. You can read it if you want to.
NOTE: This program is a simple program. When creating a wordlist for a site, do not try it on very high quality sites, the program may crash.
Step 2;
Open the terminal;
Kod:
cewl targetsite.com -w /kali/Desktop/wordlist.txtNOTE: You can write this as root/Desktop. You determine the name of your directories yourself.
Step 3;
A txt file will appear on the desktop, this process may take a long time, for information. You can implement this wordlist in a brute force attack. The working principle of this program is as follows: It generates passwords according to the words commonly used on the site.
Hashcat ( Password Attack )
Hashcat is a tool that performs a password attack. Now let's get to the use of this tool. First of all we need a password to use this tool, Ill explain;
Step 1;
https://wmaraci.com/md5-sha1-sifre-olusturucu
We go to this address (Site is turkish but its easy to understand and use). md5 so, creating a password. You will create a password from here. For example, I am doing baysiberbela79 here ;

Now it gave us md5 passwords, as you can see here.
Step 2;
Copy your MD5 Password. Then we move on to the terminal;
Kod:
cd DesktopWe switch to the desktop by using this command. Later;
Kod:
gedit md5.txtWe create a txt documént with this command which means create gedit, keep this in mind.
We paste our password into this txt file that comes to our desktop.

And let's create a wordlist;
Kod:
cd Desktop
Kod:
gedit wordlist.txtWordlist will also appear on the desktop. If you cannot create it with gedit, you can manually create txt documént on your desktop just like in windows.
Write something in the wordlist;

I wrote something here. Then let's start our tool
Step 3;
Kod:
hashcat -m 0 /root/Desktop/md5.txt /root/Desktop/wordlist.txtYou write these to the terminal, now Ill mention about something important.
Note: This tool is a very strong tool. So there is a possibility whether it will work according to your processor or not. We can solve this problem using the -- force command.
If you get an error;
Kod:
hashcat -a 3 -m 0 /root/Desktop/md5.txt /root/Desktop/wordlist.txt --forceWe can solve this problem with this command. This force command runs the tool in a slightier way.
It currently performs a brute force attack. It wont find the password, because we did not write that password into the wordlist, nor did we put anything like it, it would have found it if we did.
John The Ripper Tool
Now, let's explain password attacks through this tool. Now, to run this tool, we click to applications and find the john attache there. We click on the John tool from Password Attacks and run it. If you are not root, it will ask you for a password, enter it as toor or enter whatever you have set your password as.
We will see a screen like this;

Here again a menu gives information about how to use this tool. Various parameters are available here. The John tool is a more useful tool than the Hashcat tool.
Step 1;
Now lets open the terminal;
Kod:
john --format=Raw-MD5 --wordlist=/root/Desktop/wordlist.txt /root/Desktop/md5.txtWe write the command to the terminal and press enter.
Now when we run this, it gives an error because we cracked this password before. I created a new documént and an MD5 password named baysiberbela79.

As you can see he found the password here. I put baysiberbela79 in my wordlist and in this case it found the password.
The tutorial ends here, I hope it will be a useful topic. Have a good day, everyone.
Source: https://www.turkhackteam.org/siber-guvenlik/1944606-sifre-saldirilarina-giris-yapalim-cewl-haschat-john.html
Translator: Dolyetyus
Original Author: baysiberbela
Son düzenleme:







