- 7 Tem 2013
- 8,198
- 670
In computer and information security, the opposite parties are hackers and their attacks. Attempts made to the computer system for the purpose of hacking the system, causing vulnerability, directly or indirectly damaging the individual, damaging the system, disrupting/stopping/destroying operations are called an attack. Attackers can try many different methods to achieve the goal.

Knowing the variety of attacks and examining it correctly is the first requirement for security.

Man in the middle attack (MITM)
In the Man in the middle attack, the attacker intervenes and steals the information he wants. The target person enters the website and the information entered into the website is prepared by the attacker, so the attacker has achieved his goal.

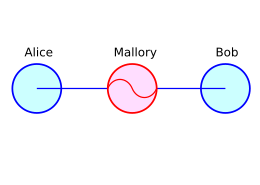

MITM attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones.
The attacker needs to decode 2 network connection which hasn't been encrypted yet.
In the first method, the client actually logs into the website on the server, but when it sends a request, the data is transmitted to the attacker in the middle of the network.
In the second method, the client (target) reaches the copy of the same page prepared by the attacker without accessing the real website. It sends information to the attacker while logging in.

For a successful MITM attack, the target should be delivered to the proxy server rather than the real server.
For this, the following scenarios are used:
1. LOCAL AREA NETWORK:
1.1. ARP poisoning
1.2. DNS spoofing
1.3. STP mangling
2. FROM LOCAL TO REMOTE:
2.1. ARP poisoning
2.2. DNS spoofing
2.3. DHCP spoofing
2.4. ICMP redirection
2.5. IRDP spoofing route mangling
3. REMOTE:
3.1. DNS poisoning
3.2. Traffic tunneling
3.3. Route mangling
Source: https://www.turkhackteam.org/siber-...ki-adam-saldirisi-man-middle-attack-mitm.html
Çevirmen/Translator Gauloran

Knowing the variety of attacks and examining it correctly is the first requirement for security.

Man in the middle attack (MITM)
In the Man in the middle attack, the attacker intervenes and steals the information he wants. The target person enters the website and the information entered into the website is prepared by the attacker, so the attacker has achieved his goal.



MITM attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones.
The attacker needs to decode 2 network connection which hasn't been encrypted yet.
In the first method, the client actually logs into the website on the server, but when it sends a request, the data is transmitted to the attacker in the middle of the network.
In the second method, the client (target) reaches the copy of the same page prepared by the attacker without accessing the real website. It sends information to the attacker while logging in.

For a successful MITM attack, the target should be delivered to the proxy server rather than the real server.
For this, the following scenarios are used:
1. LOCAL AREA NETWORK:
1.1. ARP poisoning
1.2. DNS spoofing
1.3. STP mangling
2. FROM LOCAL TO REMOTE:
2.1. ARP poisoning
2.2. DNS spoofing
2.3. DHCP spoofing
2.4. ICMP redirection
2.5. IRDP spoofing route mangling
3. REMOTE:
3.1. DNS poisoning
3.2. Traffic tunneling
3.3. Route mangling
Source: https://www.turkhackteam.org/siber-...ki-adam-saldirisi-man-middle-attack-mitm.html
Çevirmen/Translator Gauloran





