What is Kamerka-GUI?
The main purpose of the Kamerka-GUI Ultimate Internet of Things/Industrial Control Systems reconnaissance tool is to map attack surfaces, in terms of Industrial Control Devices, for any country.
The tool was developed by Wojciech.
The tool was originally designed to identify nearby surveillance cameras that could be accessed from the internet, but two years ago its developer expanded its features and now can be used to find a wide variety of systems, including printers, ICS and IoT devices.
Users who wanna use Kamerka over its GUI must install it on a server. This can be done on a local server by installing Celery task queue application for Python3, Django, Redis, and Python web applications.
No specific configuration edits are required for Kamerka to work properly. The tool also uses the Whois XML API, Shodan API ($59) or BinaryEdge, Flickr and Google Maps API to browse the web and manage the collected data.
We have 3 Python commands to run Kamerka on a local server, the application works on port 8000 and can be used in a web browser on localhost.
Researchers believe that tool can be extremely useful for the state and government to identify critical infrastructure that could be exposed to malicious attacks.
Wojciech says he will continue to improve Kamerka. I see a lot of possibilities for further development more queries, integration with Nmap and PLCscan, offensive capabilities, more social media sources or automated separation of critical infrastructure from other devices, he explained.
We can also view the results on a map and use the Google Street View API to view buildings hosting target devices.
Installation
We need to copy the github link first:
https://github.com/woj-ciech/Kamerka-GUI
Then open terminal and go to desktop, to do that:
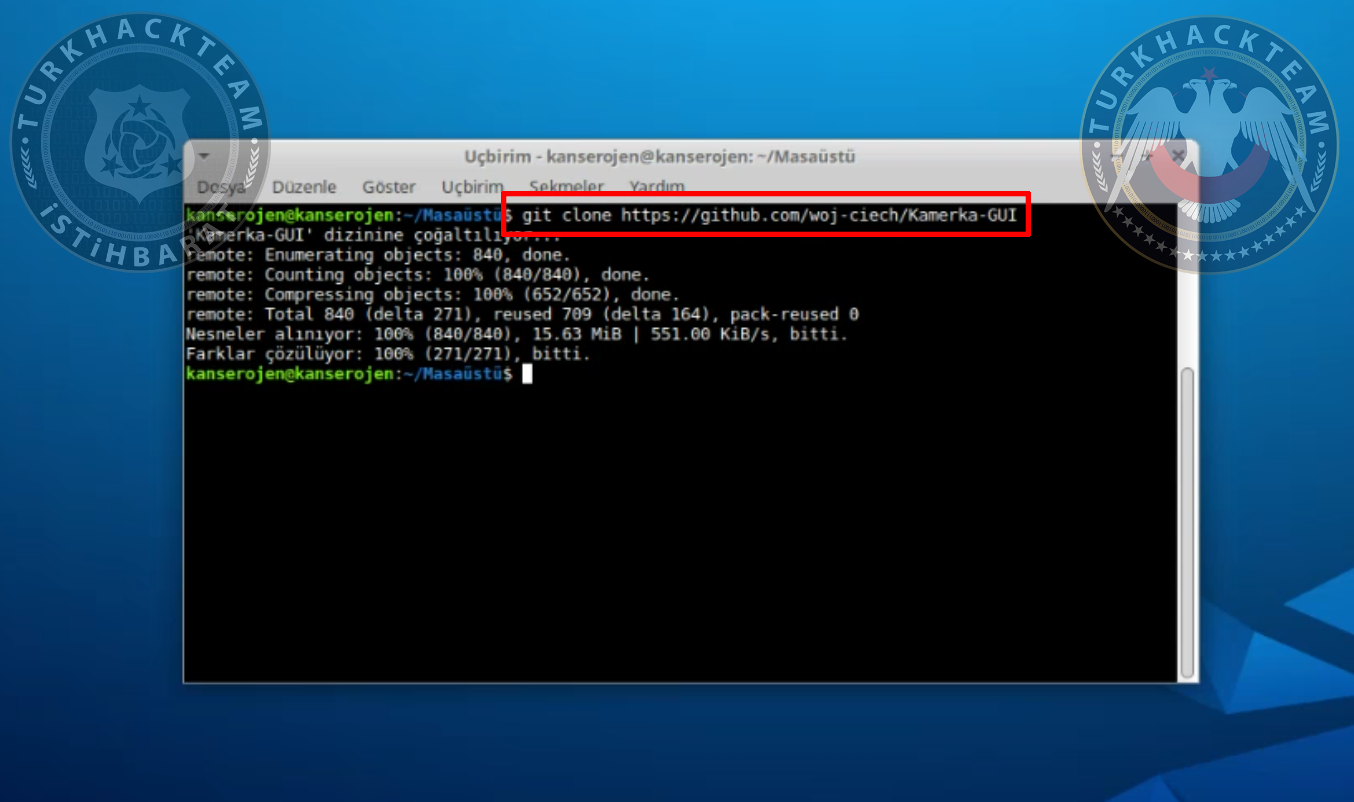
We can download the tool here, type:
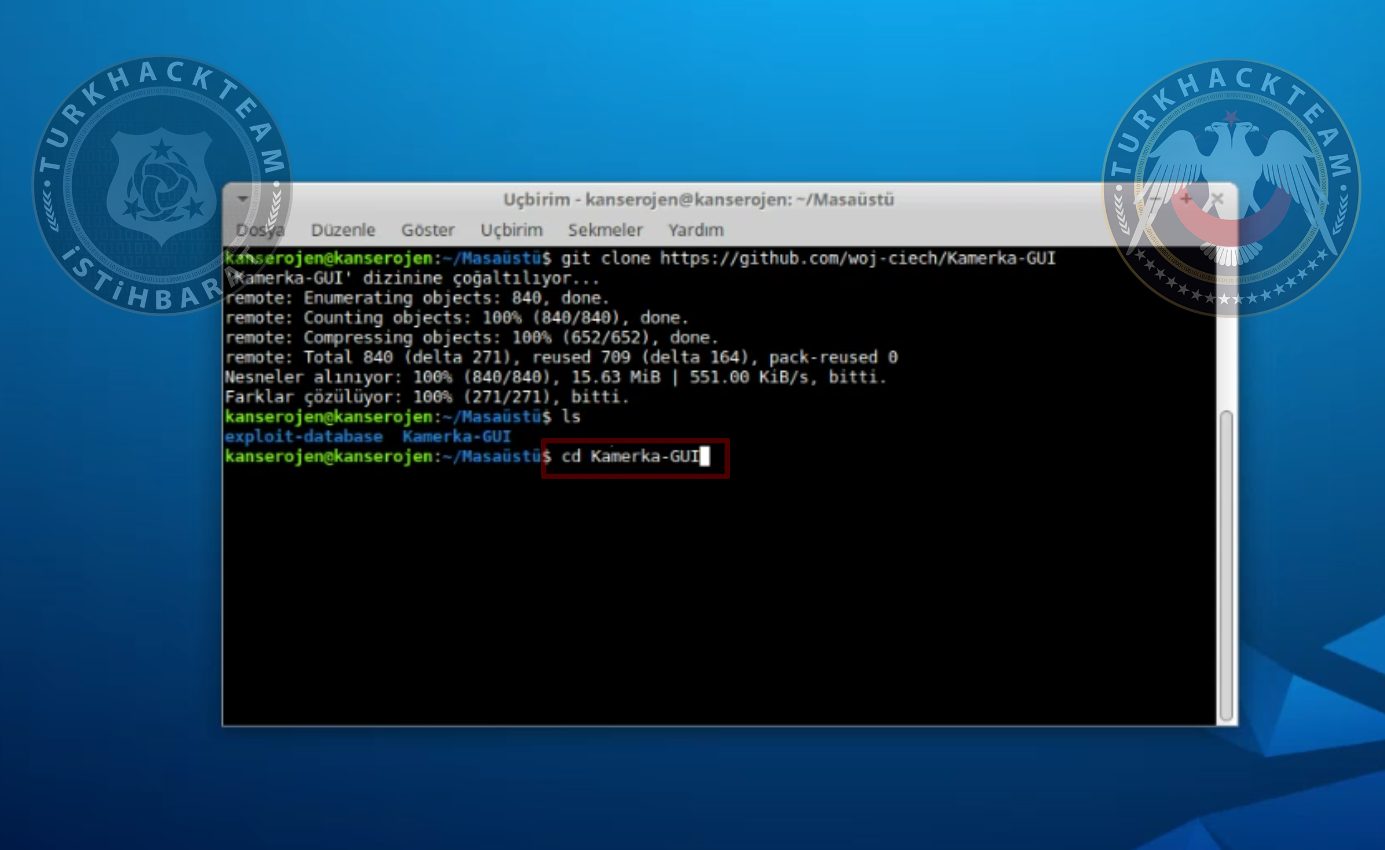
Go to that folder after it's downloaded.
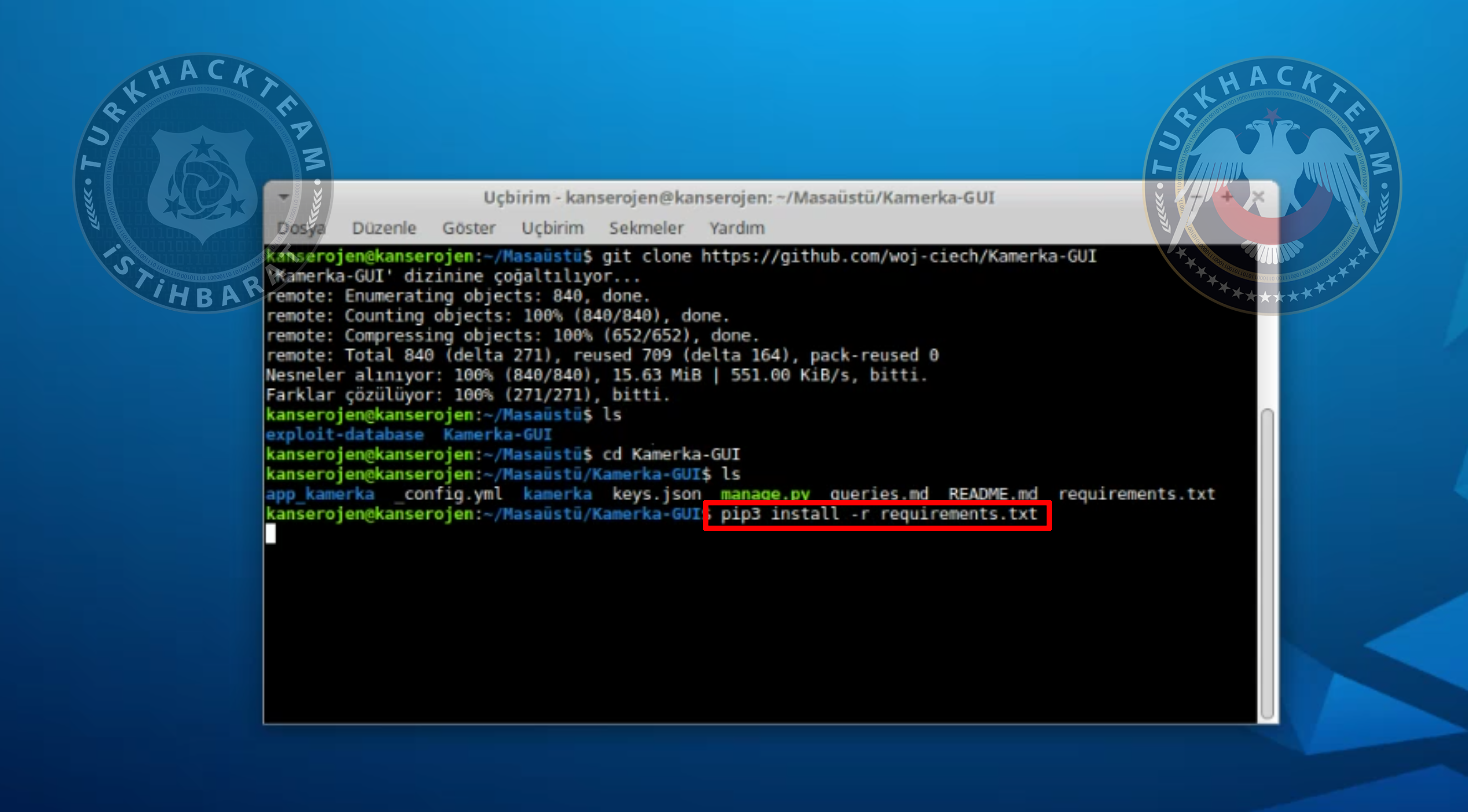
Now we need to install requirements.txt file.
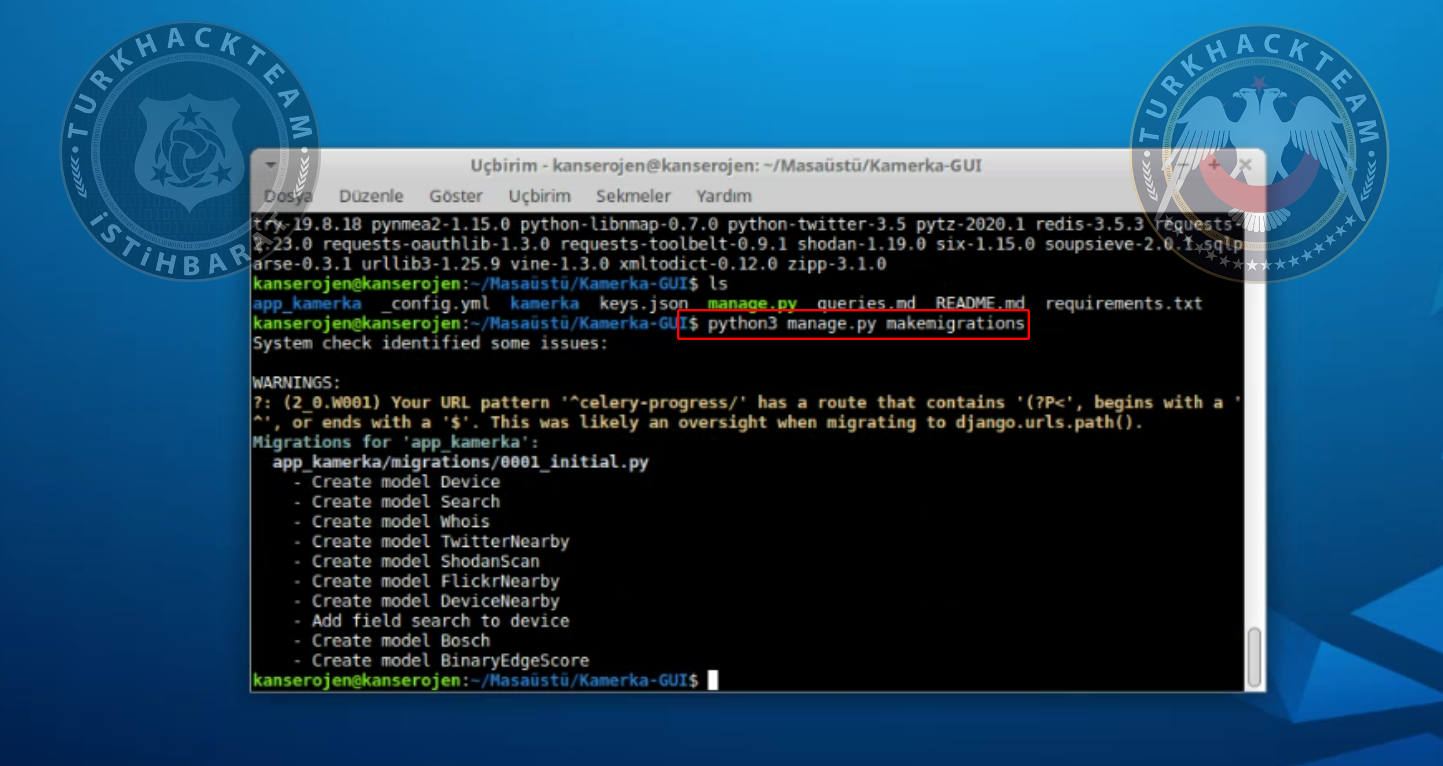
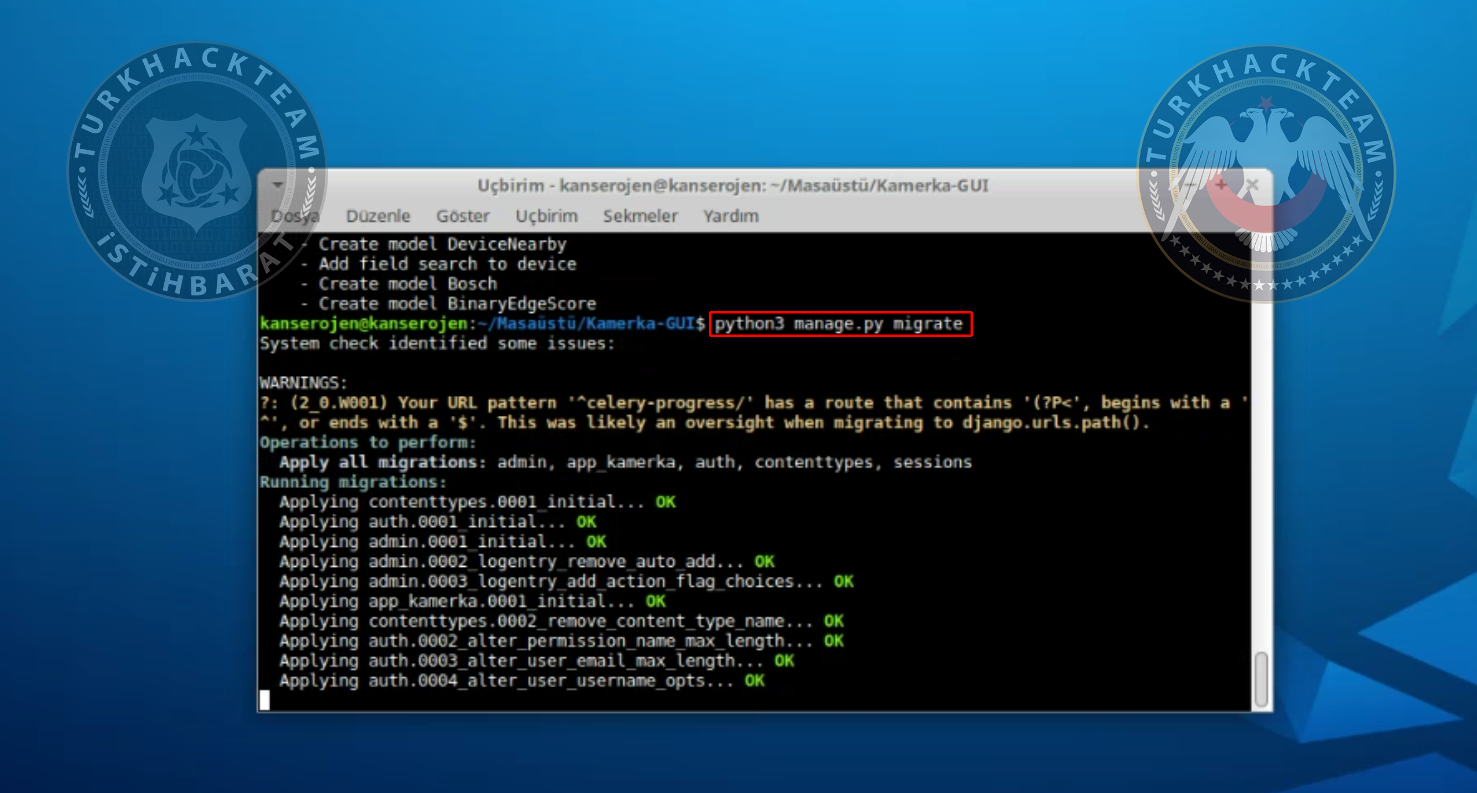
Type the following command to run the tool:
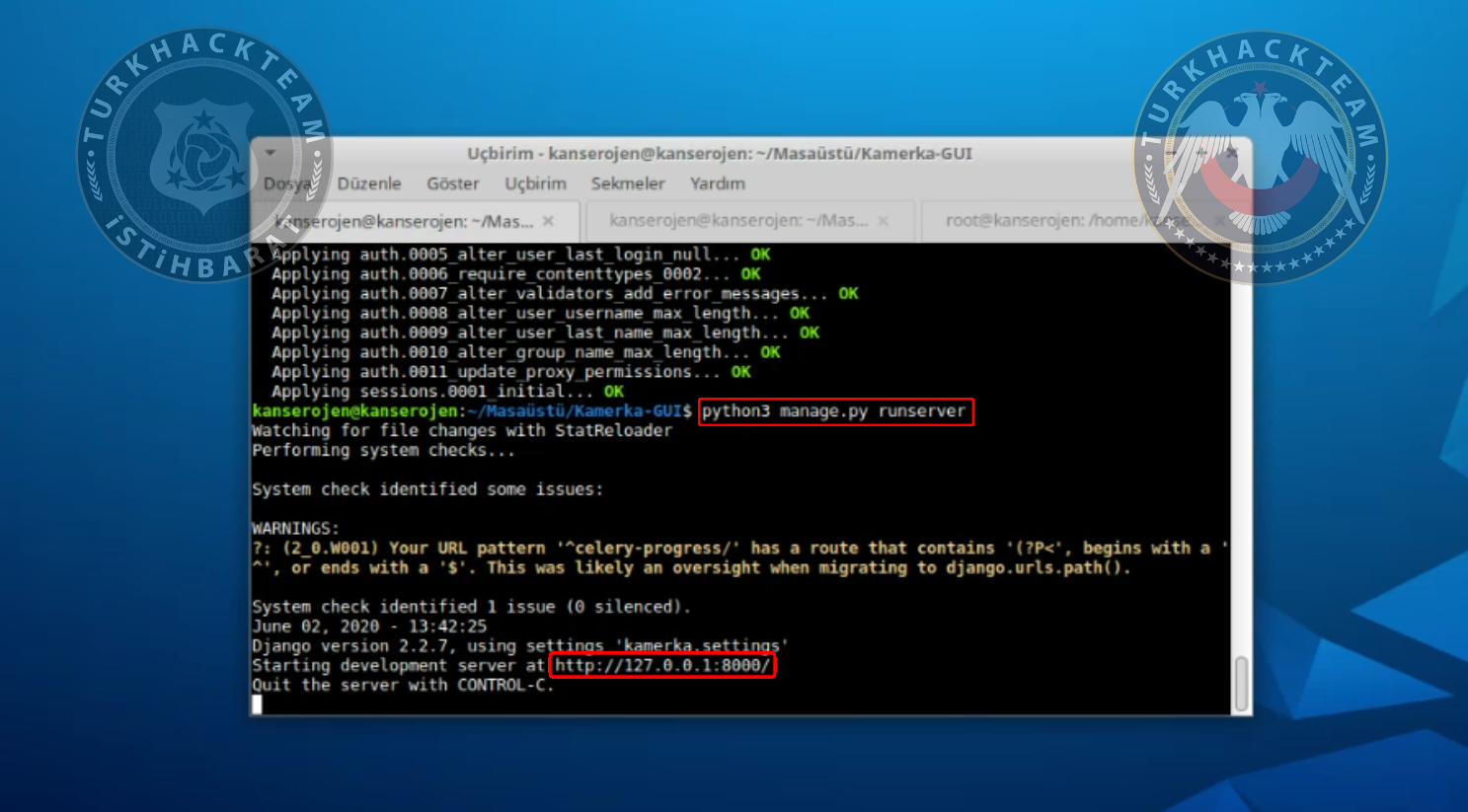
Now our tool is installed on 127.0.0.1:8000
Open a new tab in terminal.
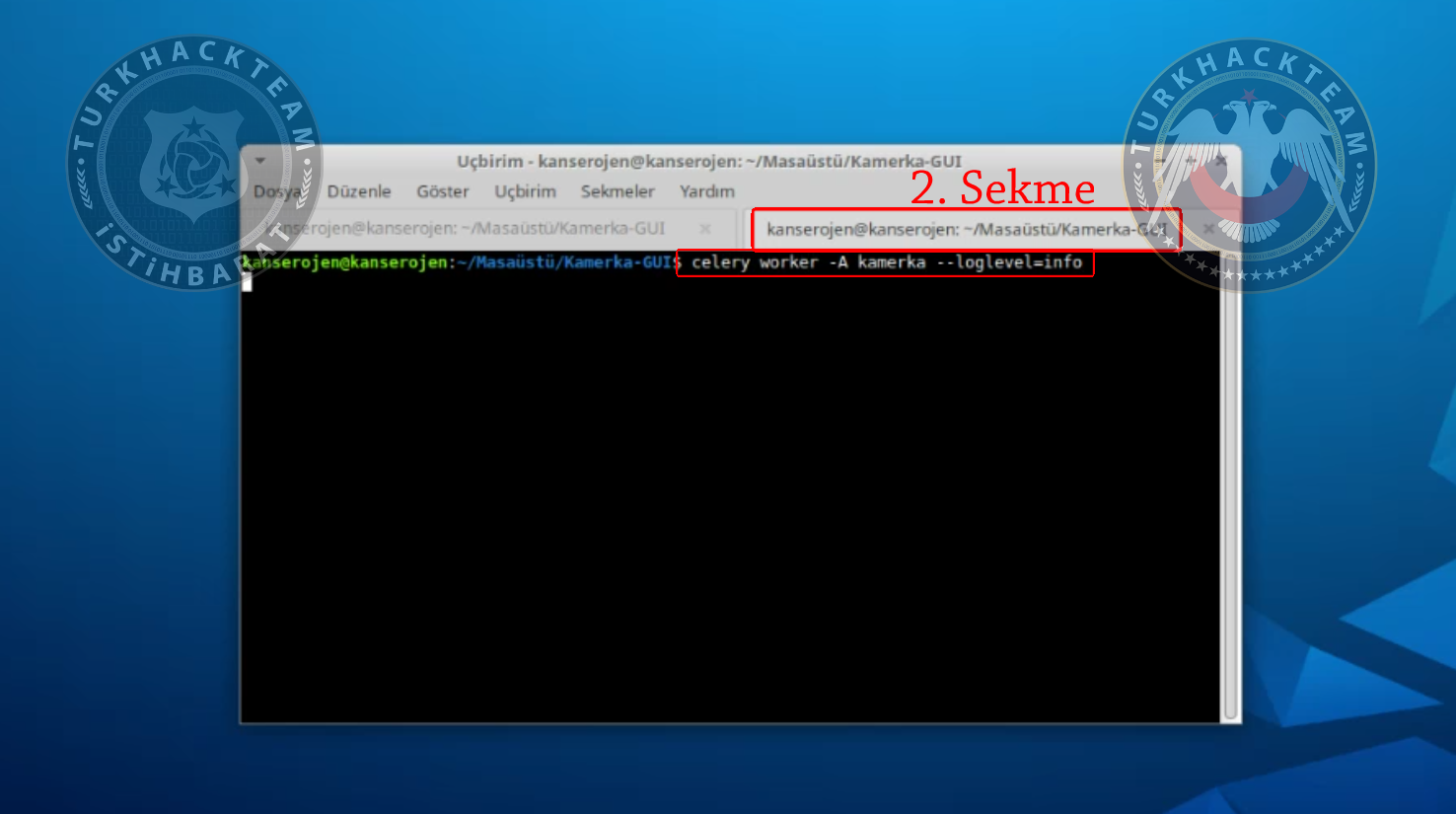
We need to type a command to forward APIs.
Now install redis package.
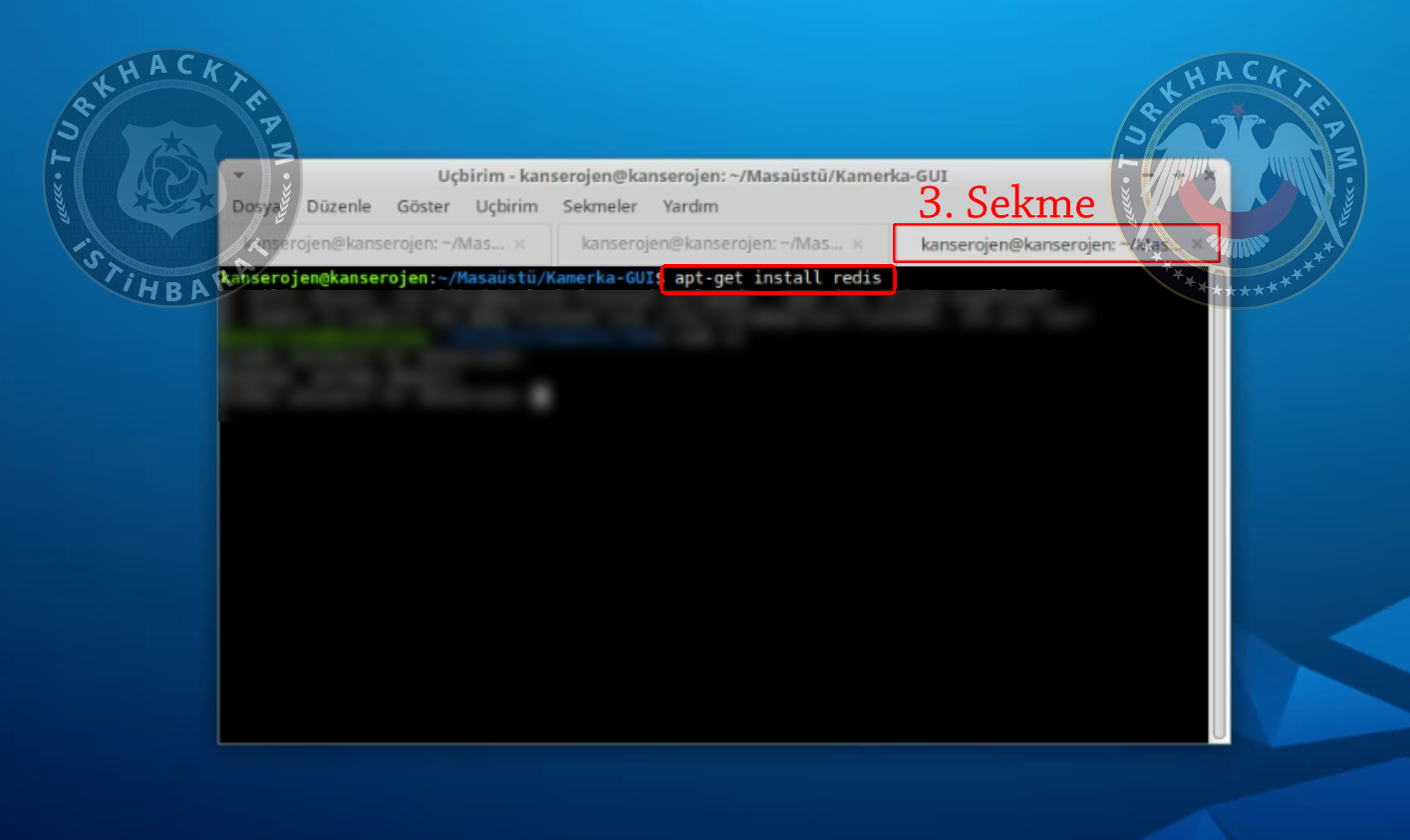
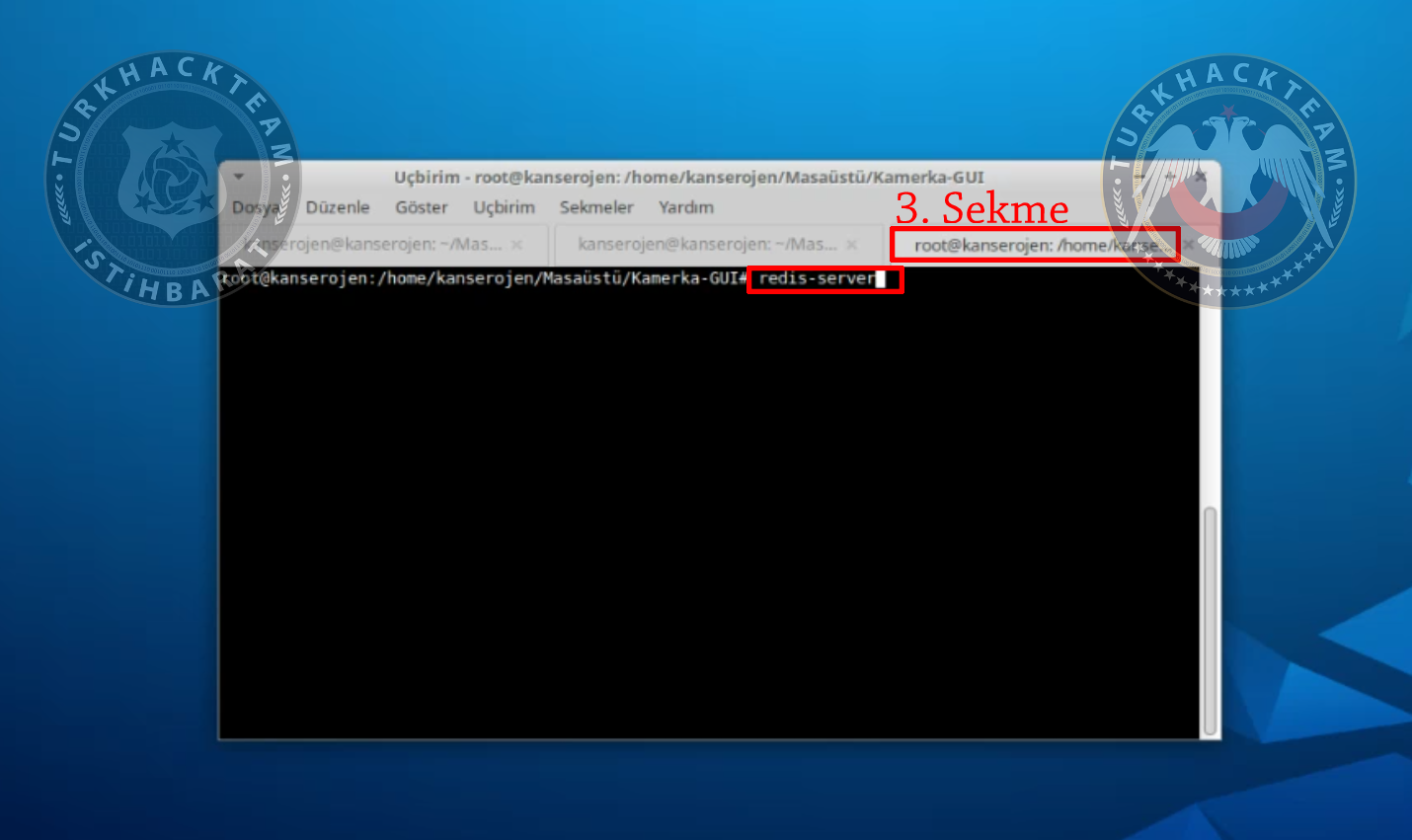
Lastly, open 3rd tab in terminal and type
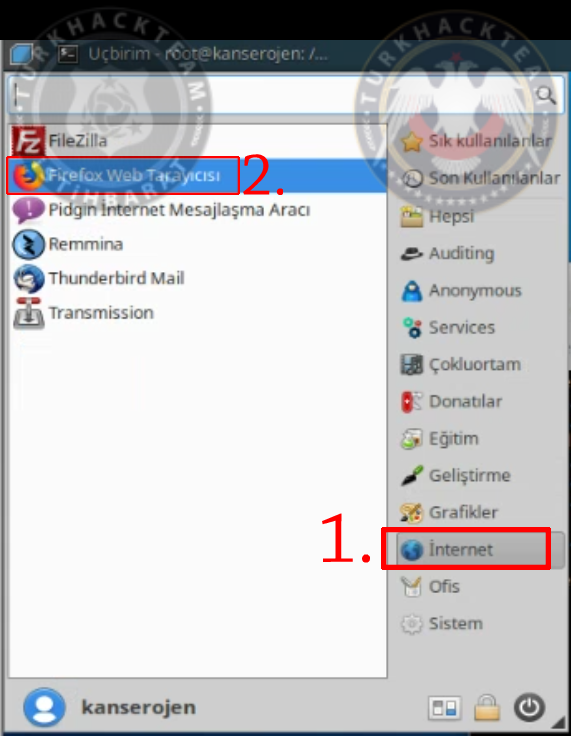
Then open your browser, finally.
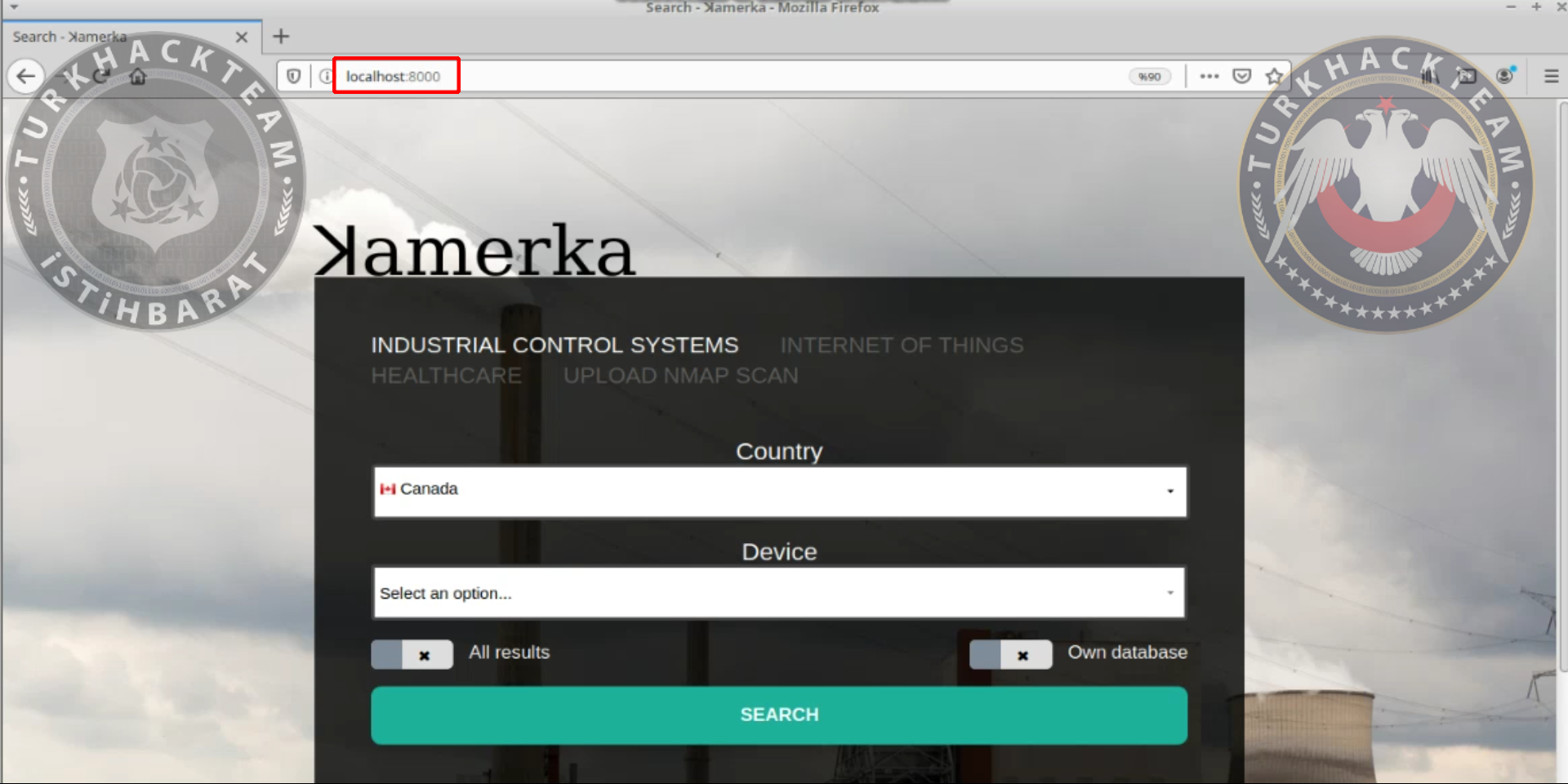
Go to 127.0.0.1:8000 and you'll see Kamerka tool.
Here's a video for you guys:
https://www.youtube.com/watch?v=IPMXe6eeu-A
Summary
While in its initial version Kamerka scanned only for security cameras -- hence the Kamerka name -- the tool has received several updates in the past year. Current versions can scan and identify.
- Internet-connected security cameras
- Internet-connected printers
- Internet-connected ICS/SCADA industrial equipment
- Systems and sensors that work on top of the MQTT protocol
- Devices that broadcast an RTSP-based live video stream
- Tweets, Instagram posts, and Flicker images that contain geolocati0n details
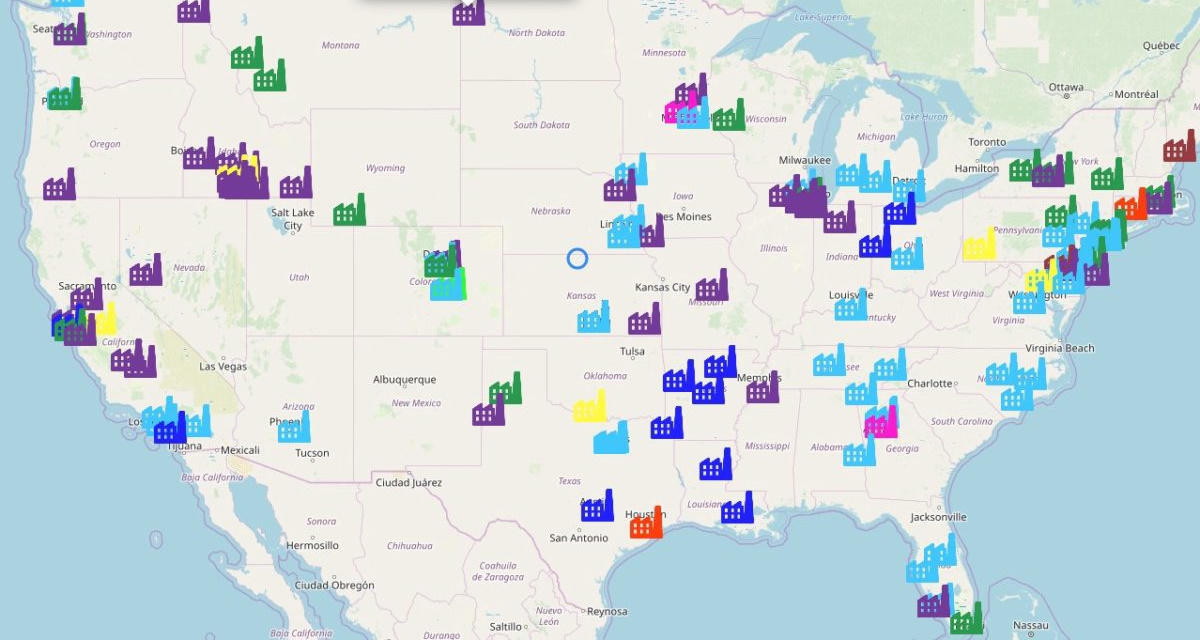
Kamerka gathers this information, collects it in an Elasticsearch database, and then plots it on a Google Map. For each device plotted on the map, users can click and see a tooltip with exposed ports and various other métadata.
Here's an example:
The main purpose of the Kamerka-GUI Ultimate Internet of Things/Industrial Control Systems reconnaissance tool is to map attack surfaces, in terms of Industrial Control Devices, for any country.
The tool was developed by Wojciech.
The tool was originally designed to identify nearby surveillance cameras that could be accessed from the internet, but two years ago its developer expanded its features and now can be used to find a wide variety of systems, including printers, ICS and IoT devices.
Users who wanna use Kamerka over its GUI must install it on a server. This can be done on a local server by installing Celery task queue application for Python3, Django, Redis, and Python web applications.
No specific configuration edits are required for Kamerka to work properly. The tool also uses the Whois XML API, Shodan API ($59) or BinaryEdge, Flickr and Google Maps API to browse the web and manage the collected data.
We have 3 Python commands to run Kamerka on a local server, the application works on port 8000 and can be used in a web browser on localhost.
Researchers believe that tool can be extremely useful for the state and government to identify critical infrastructure that could be exposed to malicious attacks.
Wojciech says he will continue to improve Kamerka. I see a lot of possibilities for further development more queries, integration with Nmap and PLCscan, offensive capabilities, more social media sources or automated separation of critical infrastructure from other devices, he explained.
We can also view the results on a map and use the Google Street View API to view buildings hosting target devices.
Installation
We need to copy the github link first:
https://github.com/woj-ciech/Kamerka-GUI
Then open terminal and go to desktop, to do that:
Kod:
cd DesktopWe can download the tool here, type:
Kod:
git clone https://github.com/woj-ciech/Kamerka-GUI
Go to that folder after it's downloaded.
Kod:
cd Kamerka-GUI
Now we need to install requirements.txt file.
Kod:
pip3 install -r requirements.txt
Type the following command to run the tool:
Kod:
python3 manage.py makemigrations
Kod:
python3 manage.py migrate
Kod:
python3 manage.py runserver
Now our tool is installed on 127.0.0.1:8000
Open a new tab in terminal.

We need to type a command to forward APIs.
Kod:
celery worker -A kamerka --loglevel=info
Now install redis package.

Lastly, open 3rd tab in terminal and type
Kod:
redis-server
Then open your browser, finally.

Go to 127.0.0.1:8000 and you'll see Kamerka tool.

Here's a video for you guys:
https://www.youtube.com/watch?v=IPMXe6eeu-A
Summary
While in its initial version Kamerka scanned only for security cameras -- hence the Kamerka name -- the tool has received several updates in the past year. Current versions can scan and identify.
- Internet-connected security cameras
- Internet-connected printers
- Internet-connected ICS/SCADA industrial equipment
- Systems and sensors that work on top of the MQTT protocol
- Devices that broadcast an RTSP-based live video stream
- Tweets, Instagram posts, and Flicker images that contain geolocati0n details
Kamerka gathers this information, collects it in an Elasticsearch database, and then plots it on a Google Map. For each device plotted on the map, users can click and see a tooltip with exposed ports and various other métadata.
Here's an example:

Source: https://www.turkhackteam.org/sosyal-muhendislik/1922026-osint-araci-kamerka-gui.html
Translator: R4V3N
Moderatör tarafında düzenlendi:





