
Types of threat intelligence
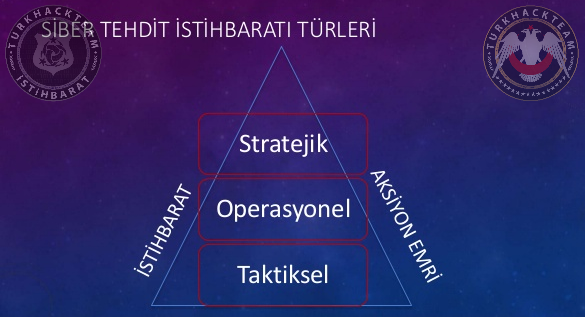
We can distinguish the three main categories of threat intelligence:
Strategic: strategic threat intelligence is a high-level analysis usually reserved for non-technical audiences, such as board members. Strategic threat intelligence is a high-level analysis usually reserved for non-technical audiences, such as stakeholders or board members.
Tactical: tactical threat intelligence focuses on the near future and helps teams determine whether current security programs will succeed in detecting and reducing risks.
Operational: operational threat intelligence helps IT defenders understand the purpose of specific cyber attacks by detailing relevant factors such as the purpose, timing and complexity of the responsible group.

Detecting Data Breaches

Don't make changes: the first rule is not to change anything in suspicious systems, because this could potentially falsify evidence and in some cases make things worse.
Gather evidence: you need to preserve evidence and collect forensic data to get all the details from a trespasser, both for Incident Analysis and ultimately for post-incident actions. These data, log files, memory, and disk information, network streams, instances of the malware or list of running processes, logged users, or may include active network connections.
Log everything: at each stage, it's important that you take a step back and note down every action. Validation, correlation: and rotation actions are often repeated; You can use your notes so that you don't miss something important. These laptops can also serve as a resource to support timelines and find areas that need improvement.
Verify with peers: once you have a basic understanding of what's going on, it can be useful to verify the findings with your peers. This can be through threat intelligence resources , industry information sharing and analysis centers (ISACs), or National Computer Security Incident Response Teams (CSIRTS).
Get to know your team: keep in mind that reports from people within the organization can also count as indicators. Internal reports can be invaluable sources of information for detecting abnormal behavior or situations, as well as necessary communication after the incident.
Internal reporting: in addition to regular reporting of observed events to stakeholders, you should also report to them critical ongoing events that have (or may have) an impact on the business.
Reporting may include a high-level analysis of the attack, including::
Whether targeted;
Whether previously observed;
Whether industry peers observed a similar attack;
What damage it has done so far;
What damages it may cause in the future; and
The purpose of the attack.
Your stakeholders will also be interested in hearing what mitigation actions are being carried out, whether they are effective, and what actions you anticipate in the future.

Source: https://www.turkhackteam.org/sosyal-muhendislik/1901048-tehdit-istihbarati-turleri.html
Translator: theblackestday





