
Greetings to all of you friends. In our today's topic, we will solve the VulnUpload CTF machine called JIS, which is located on Vulnhub. Our goal is to access their content by finding 5 flags hidden in various places inside the machine. The ip addresses that will be used during the process may differ for everyone, the machine gives everyone a different ip address. Let's not forget to pay attention to this detail.
First, we collect information on the ip address given to us using our nmap tool.
Our Command;
nmap -p- -A 10.0.2.40
In this way, we scan all ports on the target system and get information about the target system.
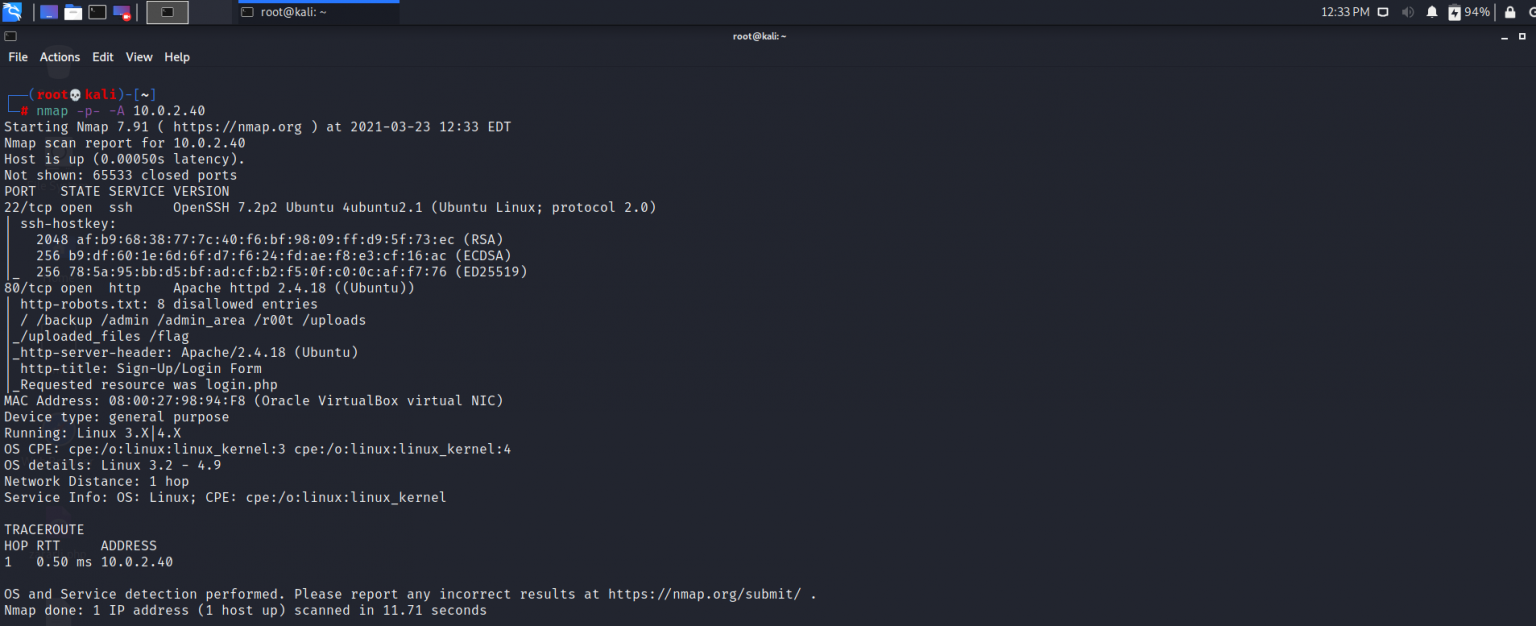
As it turned out, a website and an ssh port were left open. In that case, it is useful to check whether we can access different directories on the website with any of the tools such as dirb, dirbuster or gobuster, we are using the gobuster tool here.
Our Command;
gobuster dir -u 10.0.2.40 -w /usr/share/wordlists/dirb/big.txt
(dir: show directories, -u : destination website ip address, -w: wordlist to use during browsing)
we run the command.
Here we come across several directory addresses that we can try to access. First, go to the /flag directory
We see that he gave us our first flag under this series, now we have 4 flags left to find. Now it's /robots.we take a look at the txt directory and check if there are directories that may be useful to us.
/robots.when we examine the contents of the txt directory and the directories located here, we don't find much of a clue, except for the /admin_area directory. When we go to this directory, we are faced with a page as seen in the image below.
At first glance, although it may seem like nothing when we say our mouse right click View Page Source or view page source of the page when you examine the source code, as seen below, in front of us, the second flag comes with a username and a password for the user.
Now we have 3 flags left to get. Now we go to the login page of the site to use this username and password and enter this information correctly.
On the screen that appears, we are greeted by an option where we can upload files to the site, and we immediately download any php file that we can open a reverse connection by doing a search such as “php reverse shell” from the Internet. Then we open the downloaded file and edit the codes in the relevant part of the file so that our ip address and the port number we want to make the reverse connection are appropriate, if we upload and run the file without doing this, no connection will occur. That's why this part is important.
We have successfully uploaded our file. /robots.we go to the /uploaded_files directory that we discovered in the txt directory and access our file in the URL section as seen in the image below, but here we open a new terminal just before providing this access and start listening for the connection that will occur with the nc -nvlp 1234 command (port 1234 here should be the same as the port number that you type into the contents of the file)
As it can be seen, when we run the whoami command, we see that we have infiltrated the target system with the username “www-data”. Now let's go to the /var/www/html directory on the target system. When we went and viewed the contents of the directory, “he said.we see that there is a file called ”txt". Let's open this file.
cat is indian.when we read the contents of the file using the txt command, it is 3.we are also successfully obtaining the flag. Another file is flag.in order for us to read txt, we are informed that we need to know the password of a user named “technawi”.
when we go to the mysql directory that hosts the database files with the cd /etc/mysql command and do research in it, “credentials.a file named ”txt" attracts our attention, and when we read this file, it gives us both 4.it gives both the flag and the technawi user's password. Let's continue our processing.
Now ssh by opening a new terminal [email protected] we establish an ssh connection with the command and we can log in as a technawi user by typing the password we obtained in the password section.
Finally, we go back to the /var/www/html directory and select flag, which is probably the file where the last flag is located.we are reading the contents of the txt file. As a result of this, here is the 5th. and the last flag. Now that we have this flag, there is no more flag left for us to find.
In this way, we have successfully solved our CTF machine and completed our subject. Thank you for reading.
Source : Vulnhub | JIS:VulnUpload CTF WriteUp
Thanks...










