Hello everyone, in this topic I'll tell you about what is DoS/DDoS, what are it's types. Let's begin.

# Thread Content #
# What is DoS/DDoS?
# What are the most used DoS/DDoS types in our time.

What is DoS/DDoS ?
DoS:Known as Denial of Service attack, is the attack type done by a single person or a computertek. This Denial of Service attack happens via sending packets that exceed the bandwidth of the target machine. Shortly, it's sending as much requests as the system can't respond to. Because the system can't respond to these datas it'll be denied of service. It's easy to prevent this attack.
DDoS: The attack type that does the same task as DoS, the only thing that separetes it from DoS is, that it's done by two or more computers in real time. Datas will be sent to the target system as in DoS. Because these datas come from a lot of places, not all of them will be responded and Denial of Service attack will occur. It's difficult to prevent this attack.
These attacks vary according to internet speed. For example let's compare a 100MB internet to a 1000MB.
If bandwidth is targeted in DoS/DDoS attacks, there is no way to prevent these attacks. We can give this an example like this. Let the limit of a bus be 75. If you fill all of these 75 places, there won't be another passenger. DoS/DDoS attacks are same as this. After exceeding a capacity, naturally it'll be denied of services.

What are the most used DoS/DDoS types in our day?
DoS/DDoS attacks that we most meet in our day are these;
SYN Flood
HTTP Flood
UDP Flood
DNS Flood
Let's inspect these attack types.

SYN Flood
SYN Flood, occurs via sending SYN packets to the target system that exceed the capacity. SYN Flood, is an attack done to the system's open port. It happens via sending more packets than the target system can handle. When the attack happens, usually the target uses the IP cheat called SPOOF. In this attack, the target system's capacity is important.
Here is an SYN Flood Example
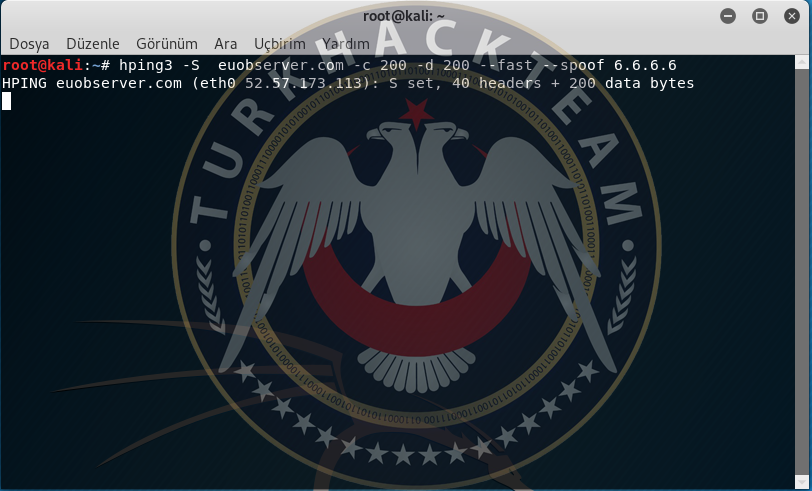
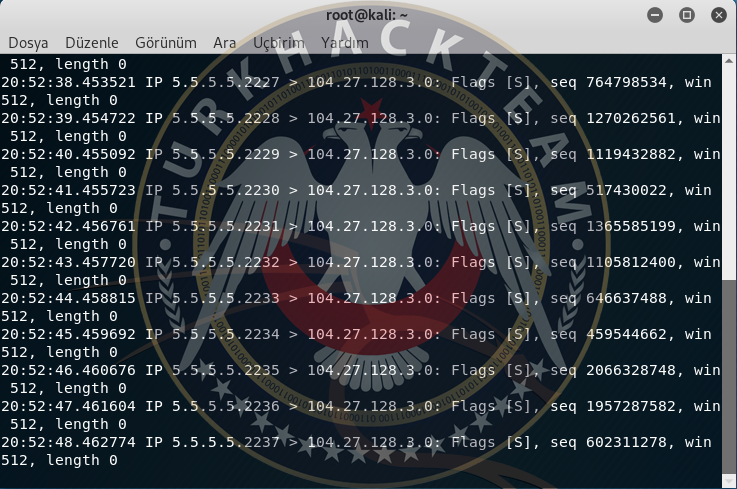
The Video Instruction of the Attack
Attack video
HTTP Flood
HTTP Flood, is an attack done with HTTP protocol. The target does web stream by using 80 port, does secure stream by using 443 port. If any one of these is happening, then the port number will be open dependantly on that process.
The system's endurance test is tested via doing HTPP flood attack. In the result, HTTP service will be affected. The purpose of this attack test is, trying and reporting how many people can the target give a healthy usage.

# Thread Content #
# What is DoS/DDoS?
# What are the most used DoS/DDoS types in our time.

What is DoS/DDoS ?
DoS:Known as Denial of Service attack, is the attack type done by a single person or a computertek. This Denial of Service attack happens via sending packets that exceed the bandwidth of the target machine. Shortly, it's sending as much requests as the system can't respond to. Because the system can't respond to these datas it'll be denied of service. It's easy to prevent this attack.
DDoS: The attack type that does the same task as DoS, the only thing that separetes it from DoS is, that it's done by two or more computers in real time. Datas will be sent to the target system as in DoS. Because these datas come from a lot of places, not all of them will be responded and Denial of Service attack will occur. It's difficult to prevent this attack.
These attacks vary according to internet speed. For example let's compare a 100MB internet to a 1000MB.
- In SYN Flood while 100MB Internet sends 200.000 packets a second, 1000MB internet will send 2.000.000 packet a second.
- In UDP Flood, while 100MB Internet sends 400.000 packets in a second, 1000MB internet will send 4.000.000 packets in a second.
- In HTTP Flood,while 100MB Internet sends, 32.000 packets in a second, 1000MB Internet will send 320.000 packets in a second.
If bandwidth is targeted in DoS/DDoS attacks, there is no way to prevent these attacks. We can give this an example like this. Let the limit of a bus be 75. If you fill all of these 75 places, there won't be another passenger. DoS/DDoS attacks are same as this. After exceeding a capacity, naturally it'll be denied of services.

What are the most used DoS/DDoS types in our day?
DoS/DDoS attacks that we most meet in our day are these;
SYN Flood
HTTP Flood
UDP Flood
DNS Flood
Let's inspect these attack types.

SYN Flood
SYN Flood, occurs via sending SYN packets to the target system that exceed the capacity. SYN Flood, is an attack done to the system's open port. It happens via sending more packets than the target system can handle. When the attack happens, usually the target uses the IP cheat called SPOOF. In this attack, the target system's capacity is important.
Here is an SYN Flood Example


The Video Instruction of the Attack
Attack video
HTTP Flood
HTTP Flood, is an attack done with HTTP protocol. The target does web stream by using 80 port, does secure stream by using 443 port. If any one of these is happening, then the port number will be open dependantly on that process.
The system's endurance test is tested via doing HTPP flood attack. In the result, HTTP service will be affected. The purpose of this attack test is, trying and reporting how many people can the target give a healthy usage.
Here is an HTTP Flood Example


UDP Flood
UDP Flood, is an attack done by targeting UDP protocols. Because the UDP protocols can't do source check, the solution to UDP flood attacks that come to system cannot be found. In this attack type, the most efficient attack is done to the DNS protocol. In this attack, as I mentioned above, IP Cheat (SPOOF) can be used. Because the system won't be able to block IP address. Through Spoof process, packets are sent from every IP address. Slowdown or delay is seen when querying these coming packet informations.
Here is an UDP Flood Example

DNS Flood
This attack type is done via sending DNS requests until the DNS servers crash. Spoof is also used in this attack type. Usually in this attack, the coming attacks are shown as if their IPs were coming from a government site. When faced against attacks that are happening as if their DNS servers' are coming from IP addresses it can be really difficult to block it. The event that is known false is supposing that every attack against UDP 53 port is DNS flood.
Here is a DNS Flood Example




UDP Flood
UDP Flood, is an attack done by targeting UDP protocols. Because the UDP protocols can't do source check, the solution to UDP flood attacks that come to system cannot be found. In this attack type, the most efficient attack is done to the DNS protocol. In this attack, as I mentioned above, IP Cheat (SPOOF) can be used. Because the system won't be able to block IP address. Through Spoof process, packets are sent from every IP address. Slowdown or delay is seen when querying these coming packet informations.
Here is an UDP Flood Example

DNS Flood
This attack type is done via sending DNS requests until the DNS servers crash. Spoof is also used in this attack type. Usually in this attack, the coming attacks are shown as if their IPs were coming from a government site. When faced against attacks that are happening as if their DNS servers' are coming from IP addresses it can be really difficult to block it. The event that is known false is supposing that every attack against UDP 53 port is DNS flood.
Here is a DNS Flood Example


---------------------
Source : https://www.turkhackteam.org/siber-...dir-en-cok-kullanilan-cesitleri-nelerdir.html
Translator : Vilge234
Translator : Vilge234
Moderatör tarafında düzenlendi:





