Today's web applications run on multiple application servers and database systems.
Consider two application servers that share exactly the same source code in the basic sense. Requests from the user are ready to be received by one of these two servers according to the installation status.
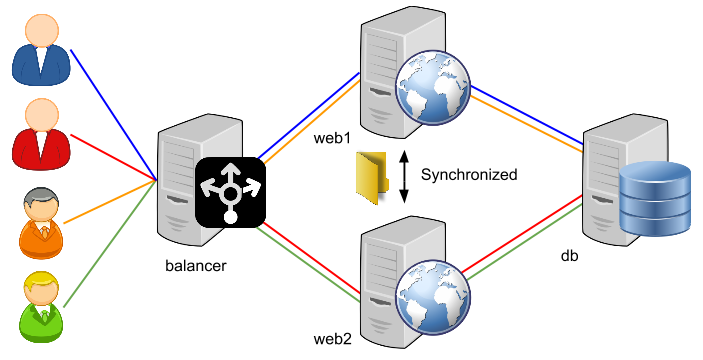
The load balancer mechanism, which handles HTTP requests in front of application servers, decides which request to transfer to which application server. This leads us to a big problem, including for mid-level system administrators and programmers. What is the actual IP address of the user?
The Diagram below is the graph that very clearly defines the word “load balancer”. Although, from the point of view of security experts, load balancers have very serious problems with time-based sql injection attacks, our topic in this article will be entirely about IP Spoofing.
Proxy and Real IP
Proxy literally means "Representative".
In other words, they are proxies responsible for managing the communication between the two systems. Looking at the image above, it can be seen that the proxy task load balancer is installed.
That is, there is only one system that talks to both the user and the application server. In terms of network traffic, web1 or web2 servers always talk to the load balancer's IP address. The same goes for users, of course.
Developer, Middle Tier, and XFF
Let's say there is a person developing this application. The business unit says, "All transactions, such as incorrect password attempts by users, will be recorded with their IP addresses."
The developer, who detects the user's IP address as soon as the HTTP request is met with the opportunity provided by the programming language used at the beginning, continues to use this data in the entire flow of the application.
Since their ip address will always be fixed during the development process (in corporate networks, user computers are allocated a static IP via MAC address), it will be normal for them to see the same address over and over in their own tests. After a while, this problem occurs in acceptance tests made by the business unit and the situation is reported to the software developer.

At this point, the person says, "Well, if somehow everyone has the same IP address... Let me write myself a controller in the development environment, dump the HTTP request forwarded to the application in raw form." says. he will say. Here comes the moment to meet X-Forwarded-For, perhaps for the first time, as he has experienced a very similar story before.
A header information called X-Forwarded-For comes to the application server and sees its own IP address, which it checks with ipconfig, not the load balancer it always sees in the logs. Then he says I can solve this problem with a code very similar to the one below.
Consider two application servers that share exactly the same source code in the basic sense. Requests from the user are ready to be received by one of these two servers according to the installation status.
The load balancer mechanism, which handles HTTP requests in front of application servers, decides which request to transfer to which application server. This leads us to a big problem, including for mid-level system administrators and programmers. What is the actual IP address of the user?
The Diagram below is the graph that very clearly defines the word “load balancer”. Although, from the point of view of security experts, load balancers have very serious problems with time-based sql injection attacks, our topic in this article will be entirely about IP Spoofing.

Proxy and Real IP
Proxy literally means "Representative".
In other words, they are proxies responsible for managing the communication between the two systems. Looking at the image above, it can be seen that the proxy task load balancer is installed.
That is, there is only one system that talks to both the user and the application server. In terms of network traffic, web1 or web2 servers always talk to the load balancer's IP address. The same goes for users, of course.
Developer, Middle Tier, and XFF
Let's say there is a person developing this application. The business unit says, "All transactions, such as incorrect password attempts by users, will be recorded with their IP addresses."
The developer, who detects the user's IP address as soon as the HTTP request is met with the opportunity provided by the programming language used at the beginning, continues to use this data in the entire flow of the application.
Since their ip address will always be fixed during the development process (in corporate networks, user computers are allocated a static IP via MAC address), it will be normal for them to see the same address over and over in their own tests. After a while, this problem occurs in acceptance tests made by the business unit and the situation is reported to the software developer.

At this point, the person says, "Well, if somehow everyone has the same IP address... Let me write myself a controller in the development environment, dump the HTTP request forwarded to the application in raw form." says. he will say. Here comes the moment to meet X-Forwarded-For, perhaps for the first time, as he has experienced a very similar story before.
A header information called X-Forwarded-For comes to the application server and sees its own IP address, which it checks with ipconfig, not the load balancer it always sees in the logs. Then he says I can solve this problem with a code very similar to the one below.
Kod:
function get_ip_address() {[/COLOR][/SIZE][/CENTER][/COLOR][/SIZE][/CENTER][/COLOR][/SIZE][/CENTER][/COLOR][/SIZE][/CENTER]
[SIZE=4][COLOR=rgb(26, 188, 156)][CENTER][SIZE=4][COLOR=rgb(26, 188, 156)][CENTER][SIZE=4][COLOR=rgb(26, 188, 156)][CENTER][SIZE=4][COLOR=rgb(26, 188, 156)][CENTER] $ip_keys = array('HTTP_CLIENT_IP', 'HTTP_X_FORWARDED_FOR', 'HTTP_X_FORWARDED', 'HTTP_X_CLUSTER_CLIENT_IP', 'HTTP_FORWARDED_FOR', 'HTTP_FORWARDED', 'REMOTE_ADDR');
foreach ($ip_keys as $key) {
if (array_key_exists($key, $_SERVER) === true) {
foreach (explode(',', $_SERVER[$key]) as $ip) {
// trim for safety measures
$ip = trim($ip);
// attempt to validate IP
if (validate_ip($ip)) {
return $ip;
}
}
}
}
return isset($_SERVER['REMOTE_ADDR']) ? $_SERVER['REMOTE_ADDR'] : false;
}(Although I am very optimistic, the software will learn in another story that it is necessary to check if the incoming value is a valid IP address.)
Bu yaklaşım ile yazılımcının aslında farkında olmadan kabul ettiği bir varsayım ortaya çıkmaktadır.

X-Forwarded-Application is reliable to come to the server. If the user is already using a proxy, the IP address cannot be changed. Because IP spoofing cannot be done in HTTP protocol.(!)
For the software developer, our story ends here. However, it is useful to remember the sentence I said at the beginning, “In order for an application to work healthily and safely, these teams that work together in theory but work at extreme points in reality try to get along with each other. with vulnerabilities that have a common basis”. Let's consider the situation from the point of view of the person responsible for configuring the load balancer.
The system administrator, who is highly skilled in the field of networking, ponders the following sentences;
Maybe developers, X-Forwarded-For etc. They record information such as Everyone knows that no data in an HTTP request can be trusted. I will forward the incoming X-Forwarded-For. I don't want to cause any trouble.

Son düzenleme:






