So Twitter exploded earlier with calls of a remote code execution WinRAR vulnerability leaving half a BILLION users open for some hardcore exploitation.
I got interested (obviously..as thats what I do here) and went to read about it, I have to call pretty sketchy, non-technical reporting from the The Register for once, it seems like it was written by an intern.
 To summarise the news
shocker, executing an executable leads to code execution yah really, no shit?
To summarise the news
shocker, executing an executable leads to code execution yah really, no shit?
The fact that it allows you to download a file from the SFX (Self Extracting RAR files basically) panel and execute that, thats a little shady, but youve already executed the .exe self unpacking file..so if its from a dubious source, you kinda deserve whatever happens from there on in.
You can watch the PoC of the exploit here.
Im honestly surprised all the major sites are reporting on this like its a big thing. Did anyone stop and actually read whats happening here?
Im not really surprised this has no CVE, and honestly dont really expect it to get one. Might WinRAR fix this hole? Probably not, as its how SFX works. Why go to such trouble when you could bind malware directly to the SFX archive and have that execute.
Is it serious?
I got interested (obviously..as thats what I do here) and went to read about it, I have to call pretty sketchy, non-technical reporting from the The Register for once, it seems like it was written by an intern.

The fact that it allows you to download a file from the SFX (Self Extracting RAR files basically) panel and execute that, thats a little shady, but youve already executed the .exe self unpacking file..so if its from a dubious source, you kinda deserve whatever happens from there on in.
Half a billion users are at risk from a public zero day remote code execution exploit affecting all versions of the popular WinRAR compression software.
A proof-of-concept exploit has been published. Its creator reckons it works on all versions of WinRAR, making it very likely that it will be used by criminals in phishing attacks. WinRAR has been a popular shareware unzipping tool for Windows users over the last two decades. It is plugged heavily thanks to many reviews by software download sites like CNET and Softpedia.
Iranian researcher Mohammad Reza Espargham reported the hole to the Full Disclosure security mailing list.
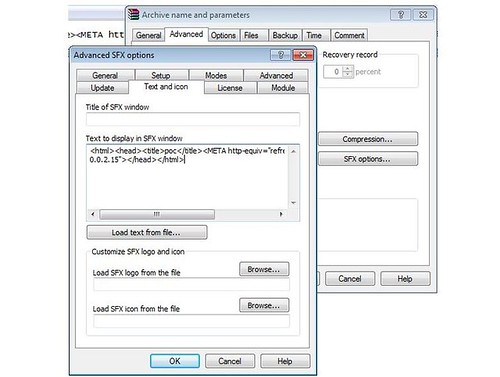
The vulnerability allows unauthorised remote attackers to execute system specific code to compromise a target system, Espargham says. The issue is located in the text and icon function of the text to display in SFX window module.
Remote attackers are able to generate [their] own compressed archives with malicious payloads to execute system specific codes for compromise.
A proof-of-concept exploit has been published. Its creator reckons it works on all versions of WinRAR, making it very likely that it will be used by criminals in phishing attacks. WinRAR has been a popular shareware unzipping tool for Windows users over the last two decades. It is plugged heavily thanks to many reviews by software download sites like CNET and Softpedia.
Iranian researcher Mohammad Reza Espargham reported the hole to the Full Disclosure security mailing list.
The vulnerability allows unauthorised remote attackers to execute system specific code to compromise a target system, Espargham says. The issue is located in the text and icon function of the text to display in SFX window module.
Remote attackers are able to generate [their] own compressed archives with malicious payloads to execute system specific codes for compromise.
Now if this trick worked when opening a .rar file with WinRAR, Id say that could be a serious problem. But only for SFX (self extracting executable archive) files not an issue really.You can watch the PoC of the exploit here.
Im honestly surprised all the major sites are reporting on this like its a big thing. Did anyone stop and actually read whats happening here?
Espargham puts the severity score at 9.2 since it requires a low competency to exploit and requires that users only open the file. Torrent files for games and applications would be a nice attack vector given attacks could be made stealthy.
The vulnerability has not yet received a CVE number by which major bugs are tracked and scored. Users could be owned if the decompress malicious SFX files. Attackers can write HTML code to WinRARs window that will run on a target machine when the archive is opened.
MalwareBytes researcher Pieter Arntz says the proof of concept needs subtle tweaking out of the tin for it to work properly. The proof-of-concept requires some trivial changes before I got it to work, Arntz says, but that might have been down to a Perl version conflict.
And honestly, why is anyone still using WinRAR since 7zip came out? Theres no excuse at all.The vulnerability has not yet received a CVE number by which major bugs are tracked and scored. Users could be owned if the decompress malicious SFX files. Attackers can write HTML code to WinRARs window that will run on a target machine when the archive is opened.
MalwareBytes researcher Pieter Arntz says the proof of concept needs subtle tweaking out of the tin for it to work properly. The proof-of-concept requires some trivial changes before I got it to work, Arntz says, but that might have been down to a Perl version conflict.
Im not really surprised this has no CVE, and honestly dont really expect it to get one. Might WinRAR fix this hole? Probably not, as its how SFX works. Why go to such trouble when you could bind malware directly to the SFX archive and have that execute.
Is it serious?



