
The THT Cyber Star Hacking Training Kit contains training materials related to web security and hacking, prepared by professional individuals. These trainings have been voluntarily prepared by the Anka Red Team, a part of the Turkhackteam Attack Teams.
This training kit is a perfect fit for individuals aspiring to become hackers and those seeking free hacking education.
With these hacking tutorials, you can acquire knowledge at the basic/intermediate levels, and the rest is up to your imagination.

★ Active & Passive Information Gathering from Websites ★
★ Hacking Attack Scenarios ★
★ Basic/Intermediate Pentest Techniques with Kali Linux ★
★ Using Burp Suite ★
★ Ports and Open Port Vulnerabilities ★
★ Detecting and Using GitHub Hacking Tools ★
★ What is an Exploit? How to Use It? ★
★ What is SQL Injection? How to Exploit It? ★
★ What is XSS Injection? How to Exploit It? ★
★ How to Deploy a Shell? Using Web Shells ★
★ What is File Upload Arbitrary Vulnerability? How to Exploit It? ★
★ CTF Solution Examples ★

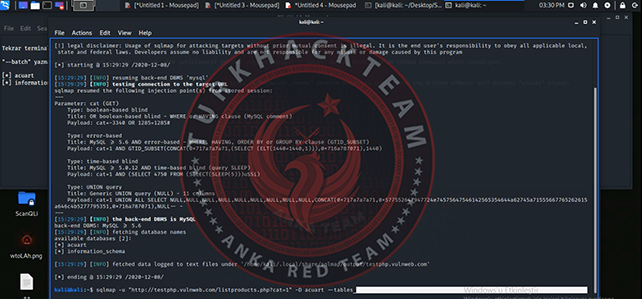


Active & Passive Information Collection from Websites
In this training, detailed definitions of concepts and terms related to active and passive information gathering are provided, using the Kali Linux operating system. Practical demonstrations of these definitions are given through various tools to maximize the effectiveness of the training. By the end of this training, you will have a comprehensive understanding of active and passive information gathering, and you will be able to easily apply the theoretical and practical knowledge you have acquired.
Hacking Attack Scenarios
The content of this training emphasizes the importance of conducting accurate assessments and focusing on potential vulnerabilities before penetrating a target. While Attack Scenarios can vary infinitely depending on the situation, this training primarily focuses on enabling you to make more critical moves in your approach to your target, based on lessons learned from our experiences. Additionally, an example tool is presented within the training to expedite your work and expand your target range. The ultimate goal of this training is for individuals to gain the ability to view the penetration process from a different perspective, speeding it up from the first to the last step.
Basic/Intermediate Pentest Techniques with Kali Linux
This training simplifies the theoretical explanation of how basic pentesting on websites can be performed using the tools available in the Kali Linux operating system. The explanation is supported with visuals and turned into practical application. By the end of this training, you will have a fundamental understanding of the tools used in pentesting processes on the Kali Linux operating system, what they are used for, and how to use them.
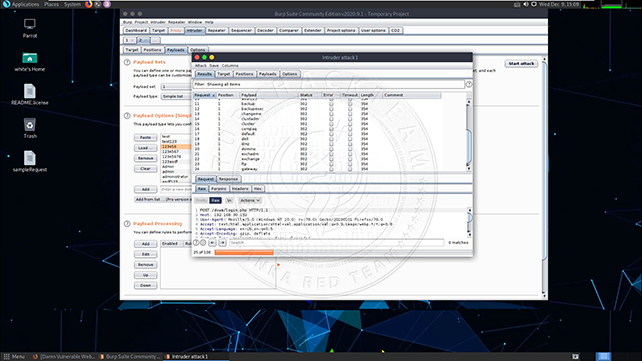
Using Burp Suite
This training covers the Burp Suite software. Burp Suite offers various features like a proxy, repeater, intruder, which are essential for web vulnerability scanning and various attack scenarios. If you are conducting web-based examinations, it is crucial to be proficient in using Burp and similar applications to the best of your ability. Hopefully, this serves as a good starting point for you.
Ports and Open Port Vulnerabilities
This training explains basic-level ports and how they work. By the end of this training, you will have knowledge about the fundamental ports and vulnerabilities of websites and understand the functioning logic of ports.
Detection and Use of GitHub Hacking Tools
This training explains the fundamental concept and functioning of the GitHub network. The aim is to facilitate the procurement of projects according to their needs. GitHub's rich content repository speeds up the process in hacking scenarios. A compiled link to popular projects is provided in the training. The goal of individuals taking this training is to create the most stable hacking tool repositories for themselves in the long run. It also aims to enable individuals to acquire and use tools according to the attack scenario.
What is Exploit? How to use?
This training covers Remote and 0day exploits. It demonstrates step-by-step attack scenarios, including attacks on certain ports via Metasploitable2. Nmap is used for reconnaissance, and the logic of its operation is explained. The training also explains terms such as exploit, auxiliary, post, payload, encoder within Metasploit and demonstrates their usage with examples. Finally, the use of searchsploit for filtering results is discussed. The training content includes gaining access to two ports, and various recommendations are provided for expediting the reconnaissance stage before penetration.
What is SQL Injection? How to Evaluate?
SQL Injection is one of the most serious vulnerabilities in web applications. Especially with the rise in popularity of frameworks and ORM (Object Relational Mapping), it is seen less frequently today compared to the past, but you can still encounter SQL Injection vulnerabilities anywhere. By the end of this training, you will have a complete understanding of SQL Injection hacking logic.
What is XSS Injection? How to Evaluate
This training covers the basics of XSS Injection, how it can be exploited, and provides scenario examples. By the end of this training, you will learn how to exploit XSS and the actions that can be taken against it.
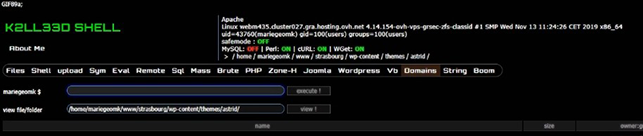
How to Throw Shell? Using Web Shell
In this training, the benefits of web shells, the operations they can perform, and their general logic are discussed. Shells provide unauthorized access and can lead to root access on target sites and servers. Different shells have unique features. The training covers the functions of the shell used and discusses both its positive and negative aspects. While shells may not always maintain their relevance, the training focuses on shells that have remained up-to-date.
What is File Upload Arbitrary Vulnerability? How to use?
The File Upload vulnerability may seem simple, but considering the impact it can have on a system, it should not be underestimated. This training explains how to exploit this vulnerability, covering concepts like file upload, exploit usage, exploit reading capability, and hacking sites with file uploads, among other topics.
CTF Solution Examples
In this training, two VulnHub machines are set up initially. After configuring network settings and discovering machines on the local network, security vulnerabilities are exploited. The first machine is exploited using a security vulnerability in the WordPress system, leading to privilege escalation and gaining root access. On the second machine, a vulnerability in the web application is used to gain SSH access. The training includes identifying machines on the network, conducting reconnaissance on target machines, and pushing the limits by evaluating various findings. All these steps will provide you with valuable insights, and by the end of this training, you will have gained a valuable skillset for pentesting scenarios.


The necessary URL and QR Code for download are below.
SM Accounts to Follow
https://twitter.com/AnkaRedTeam
https://twitter.com/THT_Resmi
Login • Instagram
Tweet to RT and Fav
Our only expectation in return for this extensive Hacking Training Kit, which we have prepared voluntarily and offer for free, is your support on social media.
Turkhackteam Cyber Star Hacking Training Kit Download Link [Click Here]
QR Code
Rar Pass : turkhackteam.org@ankaredteam_cyberstar+
Gofile Pass : thtcsl02

We didn't wait for history to write us; we wrote history ourselves.
Source : @Veteran 7 https://www.turkhackteam.org/konula...r-egitim-seti-turkiyede-ilk-ucretsiz.1960243/
Son düzenleme:






